Zero-days Like HAFNIUM Attacks on Exchange Servers Are the New Norm: Why UEBA Matters More Than Ever

By Marc Capellupo and Abel Morales
In early January, Volexity noticed anomalous activity occurring in their network. It turned out to be a zero-day vulnerability in Microsoft Exchange that allowed attackers to remotely read the contents of users’ mailboxes – confirmed by Microsoft on March 2, 2021. After monitoring this activity, further vulnerabilities were found that then allowed attackers to compromise the entire Exchange server, allowing further pivots deeper into the network. The first exploit enabled the others and the attack was able to build from the first point of entry. Due to the vulnerability requiring no authentication and being remotely exploitable, these vulnerabilities received High, even Critical, ratings. Adding to the severity of the vulnerabilities, Exchange servers often sit between the internet and internal networks and when compromised, can be a bridge for attackers to access and reach deeper into these networks. A great timeline of events for this attack is here – but the specific post-exploitation techniques, reverse shells, dumping credentials from memory, pivoting between accounts, are consistent across this and similar APT campaigns, regardless of how the initial access was obtained.
Organizations can continue to expect the discovery and exploitation of new celebrity vulnerabilities that provide adversaries with access to internal networks. Zero-days and compromises like the SolarWinds supply chain attack from late last year will continue to affect organizations and governments at scale. The adversaries for these two different attacks leveraged similar tactics, techniques, and procedures (TTPs) with a goal to compromise privileged credentials, move laterally, and exfiltrate data. However, organizations find it challenging to identify an adversary in their network. Attacks bypassing protection mechanisms make detection a critical priority.
Attacks leverage undetected activity to move laterally across networks
The pattern across these large-scale attacks is simple: malicious actors gain a foothold into networks through social engineering or a zero-day vulnerability, bypassing the best laid defenses. From one point of entry, the attacker can move across an internal network and access sensitive information, perform surveillance, or other malicious activities. Attackers used lateral movement in HAFNIUM attacks, using internal systems and processes that are hard to detect and often can be mistaken as normal since the processes are part of the operating system (and are also often used as part of normal IT operations).
Defenders require a detection strategy that is an indicator of compromise (IOC) agnostic. Meaning the TTPs to move across internal environments are all the same regardless of how the compromise or point of entry first occurred. Although the pattern and general techniques are the same, every attack is unique in what internal systems, processes, and services are used to continue this movement across sensitive data and resources. Defenders traditionally leverage IOCs to identify evidence of an adversary in an organization’s network, however, attackers dynamically change these indicators by adjusting payloads and exploiting different processes. The question is will attackers use WMIC to execute malicious payloads this time or will it be like HAFNIUM and they use Microsoft Exchange Server’s Unified Messaging service inappropriately?
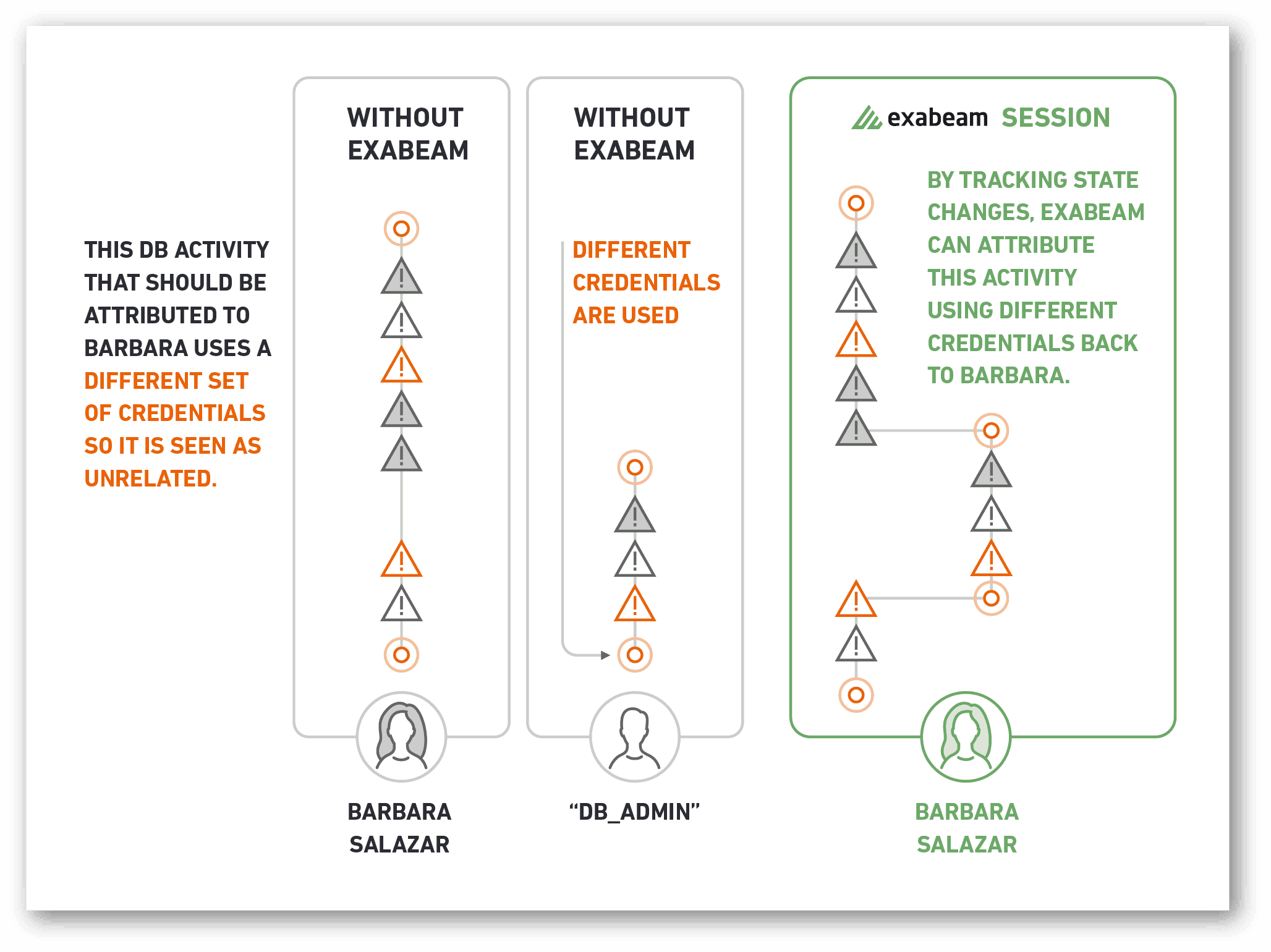
Working with customer and prospect security teams, we understand how difficult it is once a breach has happened. It’s similar to finding mice inside your home; You can patch the way they came in but it does nothing to remove the ones already inside. And just because you stopped seeing evidence of their previous activity doesn’t mean that they didn’t move to another part of the house. This becomes even more challenging at scale. Once an entry point is detected, it is difficult to find abnormal activity on valid accounts numbering in the thousands, even tens of thousands. The MITRE ATT&CK framework provides guidance to detect valid account misuse by identifying “abnormal” behavior – but how do organizations highlight abnormal without first defining “normal” behavior?
This is why we recommend a UEBA component to all security programs and tools. Traditional tools and SIEMs do not baseline “normal” and will only fire off alerts based on static correlation rules. With behavioral analytics, what is “normal” activity for an account, user, device, entity, and other endpoint is baselined and risky activity can be found at-scale, regardless of the specific process or system that is performing the activity. When machine intelligence is applied to detecting compromises, organizations are no longer behind the curve looking for IOCs that are unique with each attack. Security teams can focus on developing mitigation and security processes to address lateral movement proactively versus chasing after the next zero-day and adding static detection rules to find them in their networks. Breaches may seem inevitable, but they follow similar patterns and modern tools with UEBA can help security teams be more proactive rather than reactive to incidents.
Exabeam customers can access a content pack containing a full list of existing and new detection coverage for this threat, including TTPs and CVEs, through the Exabeam Community portal. Please note this is an early availability release and detection quality may vary depending on the customer environment. We’ll provide updates to the Community article as we learn more.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











