Last year we announced a set of new functionalities aligned across Exabeam’s products to solve specific security challenges. These new Threat Detection, Investigation & Response (TDIR) use case packages provide a powerful, prescriptive solution to help security operations teams improve workflows from collection to detection, investigation and response using an outcome-based approach. The TDIR packages address the complete lifecycle of security operations (SecOps) workflows with end-to-end content that includes prescribed data sources, detection models, investigation checklists, and response playbooks to assist analysts with repeatedly delivering successful outcomes.
In this article:
- Why are prescriptive use cases necessary?
- Coverage for common threats
- What is lateral movement?
- How does Exabeam detect and respond to lateral movement?
- Deep dive: lateral movement
- Visibility and investigation
- Response
- Exabeam and lateral movement
Why are prescriptive use cases necessary?
According to Gartner, “The lack of sufficiently detailed goals and clearly defined use cases is one of the most common reasons for failed security analytics implementations. Industry analysts expected up to 80% of security analytics initiatives to fail without a use-case centric approach. We clearly saw in the market and with our customers that there was often ambiguity as to what specific problems their security teams were trying to solve. For instance “Insider threats” was a commonly desired “use case” that could refer to both internal employee monitoring and also threats with adversaries that sought to compromise employees to gain access to systems and networks internally.
Beyond issues with ambiguity, we also learned that existing solutions in the security market for use cases were also limited to mere detection. While other vendors touted hundreds of out of the box use cases, we found these largely did not solve the entire problem the customer was trying to solve. For example, if a customer was trying to address a lateral movement use case, they might use certain rules and models for threat detection, but be unable to answer “what’s next?” in terms of investigation and response processes.
Ultimately, problems with ambiguity and myopic focus on detection lead to subpar outcomes for security teams.
Coverage for common threats
The TDIR use case packages simplify analyst workflows by providing prescriptive content for Exabeam’s analytics and automation engines to run in order to protect against the top three categorical common threats:
- External threat use cases that include phishing, malware and ransomware.
- Compromised insider use cases that include privileged activity, account manipulation, privilege escalation, evasion, compromised credentials, lateral movement and data exfiltration.
- Malicious insider use cases that include privileged access abuse, account manipulation, audit tampering, physical access, data access abuse, data leak and destruction of data.
In this post, I’ll take a closer look at what this looks like for a specific use case in the compromised insider category: lateral movement.
What is lateral movement?
Lateral movement is when an attacker compromises or gains control of one asset within a network and then moves internally within the network (“east to west”) from that device to others.
Adversaries using lateral movement make their way systematically through a network to find sensitive data or high-value assets. After gaining initial access, attackers probe other assets for vulnerabilities to compromise other accounts, escalate privileges, and ultimately exfiltrate data or cause other damage.
Traditional security tools are unable to distinguish between lateral movement activity associated with compromised accounts and normal user behavior. This allows adversaries to remain undetected and extend dwell time for weeks or months while expanding the attack.
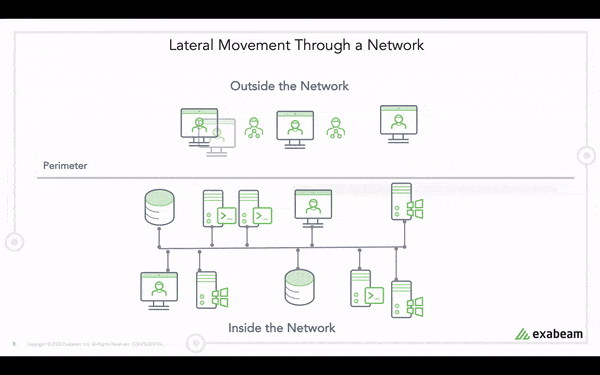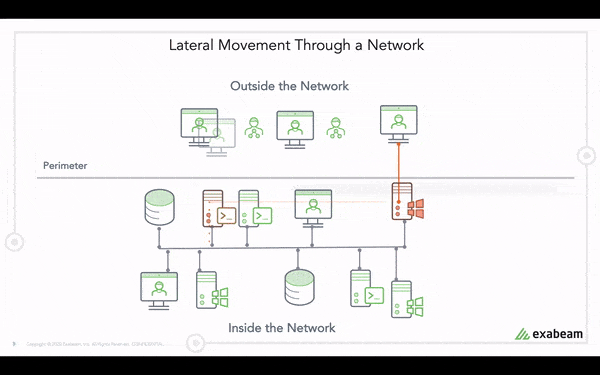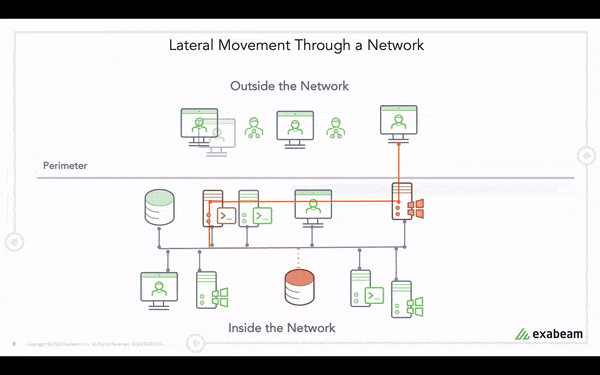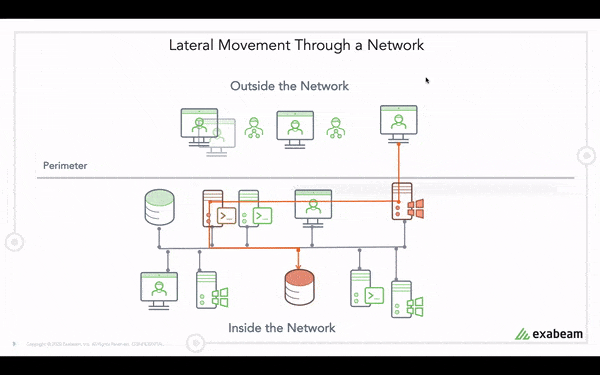
How does Exabeam detect and respond to lateral movement?
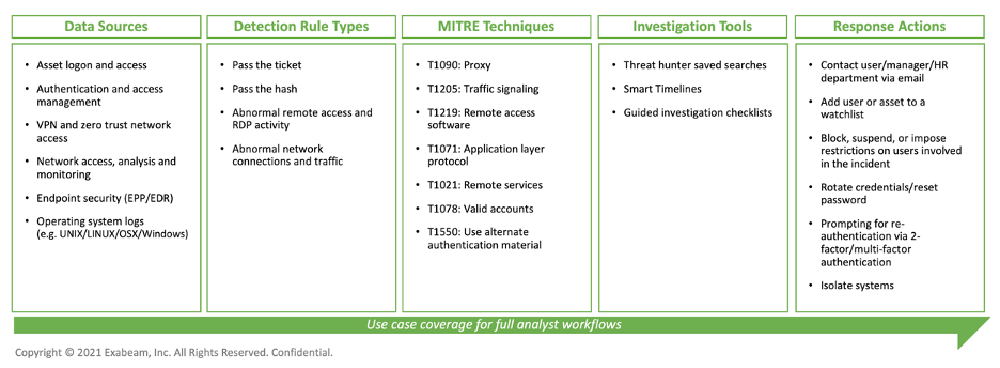
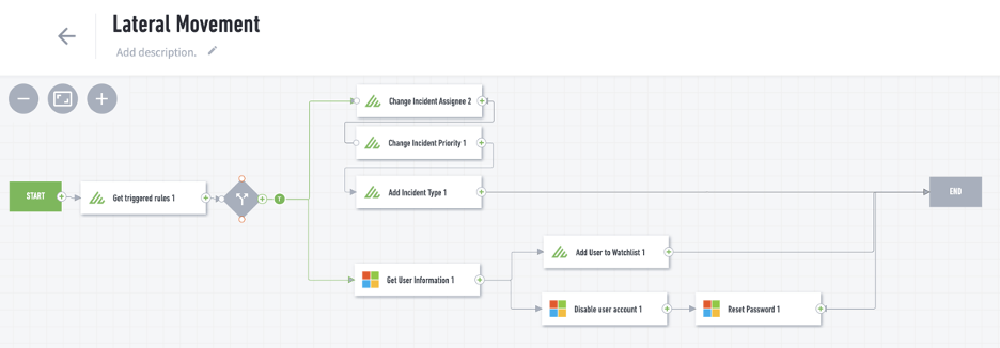
To provide coverage for lateral movement, Exabeam prescribes key data sources and content for collection, detection, investigation and response. Data sources such as asset logon and access or authentication activity help detect key techniques associated with lateral movement, like pass the ticket, pass the hash and more. Exabeam’s out-of-the-box detection rules and models for this use case are mapped to MITRE techniques, allowing teams to clearly understand their coverage. Investigation tools such as Threat Hunter, our Smart Timelines and lateral movement checklists improve overall investigation speed and quality, while recommended response actions, as shown below, can be automated in Incident Responder, decreasing mean time to respond (MTTR). This end-to-end content ensures security teams have all the components needed to consistently solve for the lateral movement use case across each stage of the analyst workflow.
Deep dive: lateral movement
Let’s walk through each stage of the analyst workflow to learn how Exabeam supports this use case. We’ll also share what this use case looks like in our platform with example user, Julietta Donaldson.
Collection and detection
A common challenge security teams face at this stage is that legacy security tools cannot distinguish lateral movement by adversaries using valid credentials from normal user activity. Exabeam ingests and analyzes key data sources to detect risky access and techniques like pass the hash, pass the ticket and more. Exabeam behavioral models put anomalous activity like first time or failed access to hosts and assets in the context of the historic behavior of that user, their peers and their organization to clearly identify adversarial behavior from normal activity.
Here, we’ve identified a lateral movement incident involving user Julietta Donaldson. Exabeam collects and correlates various logs, then associates them back to the responsible user and builds a timeline.
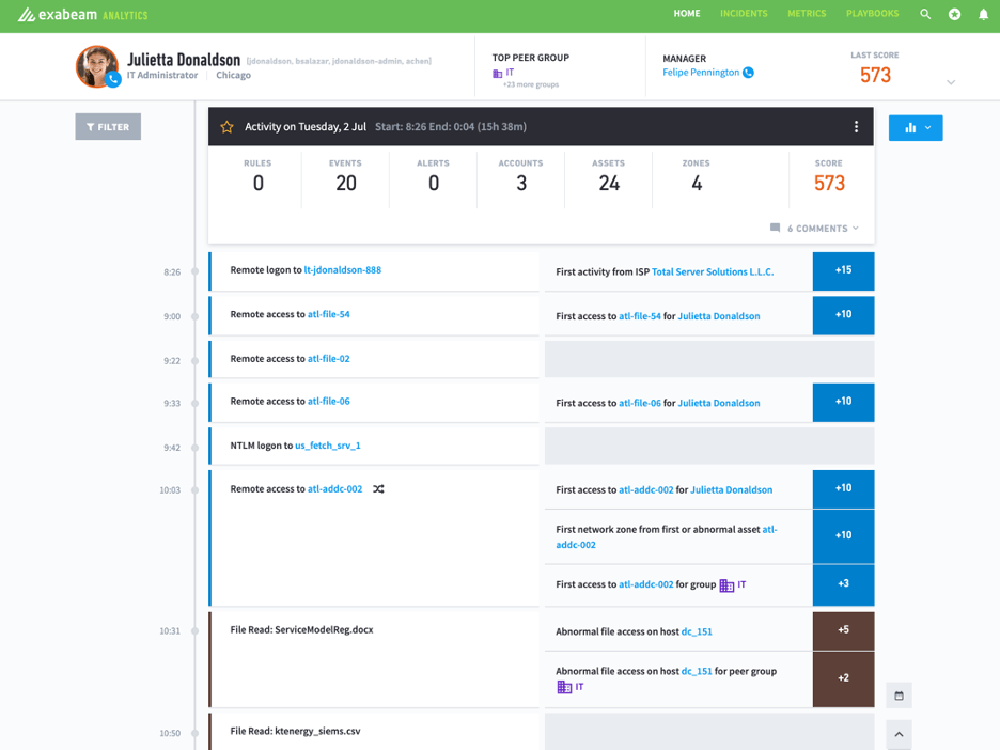
Once the data is ingested, it is enriched with context. Exabeam maps the user to the host, IP address, network zone and other relevant parameters. This is important to track the user as they move across the network.
Drilling down into the first event, we can see in greater detail the first indicator that Julietta may be compromised. Events and event details are parsed from data sources such as authentication, asset access and login data and more. In this event, we can see this is the first time Julietta has used a remote logon from this internet service provider (ISP), which is considered abnormal activity. We suspect she may be compromised, and start to investigate further.
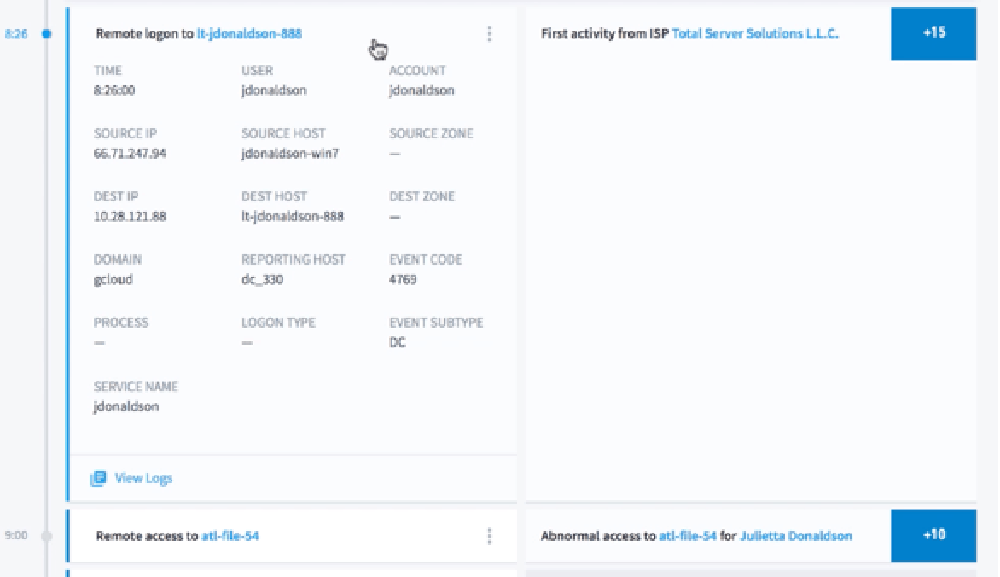
Next, Exabeam learns a user’s normal behavior through behavior modeling. These models can provide valuable context about normal behavior for analysts and help detect anomalies. Exabeam develops a baseline of normal user behavior, then detects things like first time or anomalous access activity for the user. A rule based on this model is then able to flag and assign a risk score to the abnormal behavior.
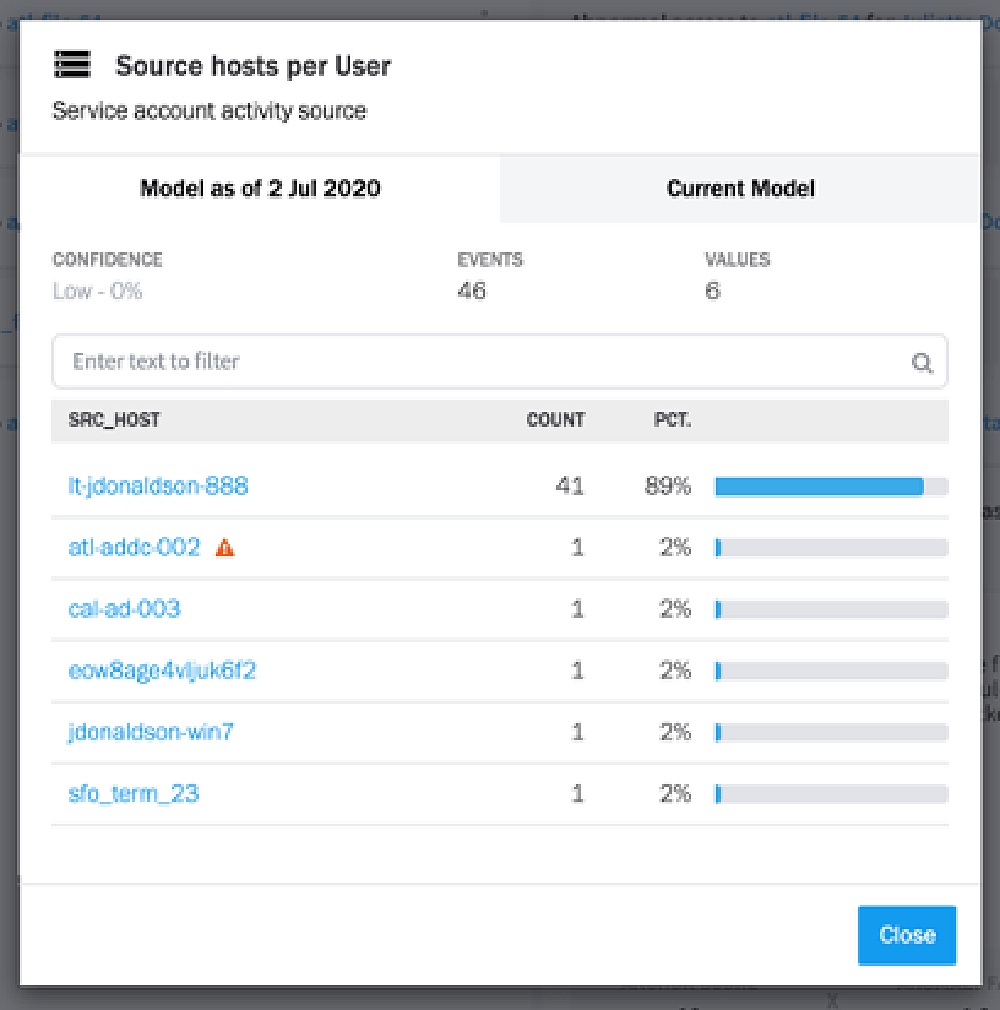
From this Data Insight Model, we can see Julietta normally logs onto host lt-jdonaldson-888. The alert on access to a new host, atl-addc-002 and the others below in the model indicate our adversary may be attempting to access other hosts, a classic sign of lateral movement.
Next, Exabeam tags anomalous events with MITRE ATT&CK tactic and technique labels where relevant. For example, this event is being tagged with the “Remote Services” technique which is associated with the lateral movement tactic. Analysts can also search for lateral movement based on anomalous behavior or MITRE ATT&CK tactics and techniques. This helps analysts find all the users and assets that are compromised in a lateral movement incident. As a result, organizations can strengthen security posture by using behavior analytics to detect lateral movement, including techniques described in the MITRE ATT&CK framework.
Exabeam detects seven MITRE techniques associated with lateral movement:
- T1090: Proxy
- T1205: Traffic signaling
- T1219: Remote access software
- T1071: Application layer protocol
- T1021: Remote services
- T1078: Valid accounts
- T1550: Use alternate authentication material
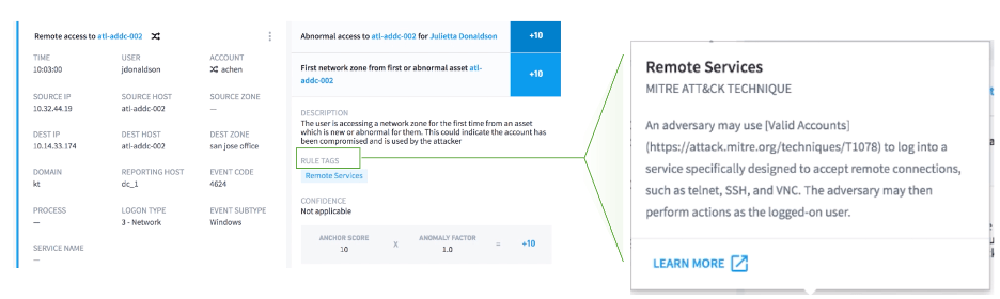
From this timeline, with events tagged with MITRE technique T1021: Remote Services, we can now see the adversary has used Julietta’s account to move laterally from her normal host, lt-jdonaldson-888, to host adtl-addc-002. Adversaries using lateral movement will often continue to move throughout the network, which we’ll see as we investigate further.
Visibility and investigation
Another common issue during the investigation portion of the workflow is that security teams are often unable to answer key investigation questions to ensure they do not risk missing parts of a lateral movement attack. Exabeam gives complete visibility into lateral movement attacks by providing a list of compromised users and assets. In addition to the Smart Timelines we showed earlier, analysts can investigate further with Exabeam Threat Hunter to find other compromised users or assets, or drill down in the timeline events to review the raw logs. Each step of the way, analysts can reference our lateral movement checklist to ensure their investigation is thorough and complete.
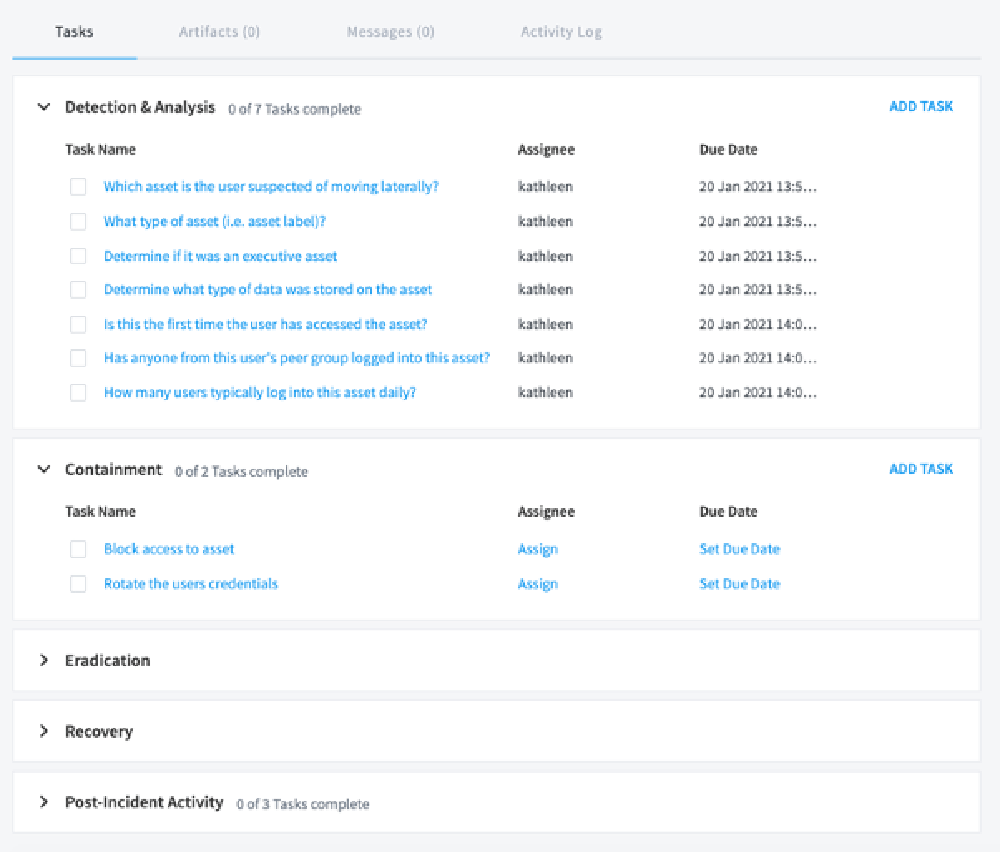
In Julietta’s timeline, we can further investigate and answer the questions “Which asset is the user suspected of moving laterally?” and “Is this the first time the user has accessed this asset?”. In the timeline event below, we see it is her first time accessing a specific server. Exabeam has determined that this is Julietta’s first time accessing the network zone that the server is located in.
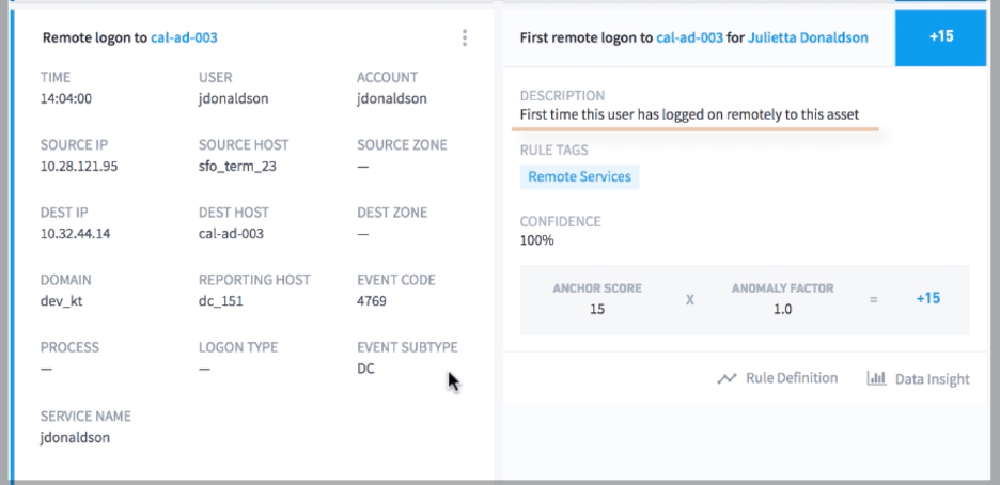
Here we see again the adversary has used Julietta’s account now to move laterally to another new host, cal-ad-003. By moving through the network, the adversary is able to access high-value assets, and ultimately perform privilege escalation or data exfiltration.
By automatically assembling this information in a timeline, Exabeam improves investigation quality and speed by enabling analysts to quickly answer key questions.
Response
The last challenge security teams face when responding to lateral movement investigations is that they can spend hours or days coordinating a response across multiple security tools. Exabeam playbooks orchestrate response to lateral movement incidents across your security stack. Out-of-the-box integrations and customizable actions enable security teams to automate playbooks to respond to lateral movement incidents, such as suspending a user or resetting a password.
Exabeam and lateral movement
I hope this post explained how Exabeam solves for the lateral movement use case, supporting the full analyst workflow, from detection through response. To summarize, Exabeam helps security teams:
- Strengthen their security posture by detecting lateral movement using behavior analytics, including techniques described in the MITRE ATT&CK framework.
- Improve investigation quality and speed by enabling analysts to quickly answer key questions that are relevant to lateral movement.
- Improve operational efficiency and decrease mean time to respond with security orchestration automation and response playbooks.
Learn more about lateral movement
Want to learn more about Exabeam’s use-case based solution for lateral movement? Read the solution brief.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













