What a year 2022 has been. Early in the year, many organizations went on a hiring spree and now the recent economic downturn has led to an uptick in companies downsizing. With businesses in many sectors struggling, some organizations have started this process and others are starting to think about it.
Regrettably, the role of the CISO needs to be included in this process. Past history has shown that downsizing increases the organizational risk companies face from impacted employees and the data and IP they have access to. In the 2022 Cost of Insider Threats Global Report, Ponemon Institute estimated that the average cost of an insider-related incident was $15.4M. With this in mind, CISOs need to educate their organizations on the risk of insider threats all the way to the board level to get buy-in for the programs and necessary budget to address these threats.
In this article:
- The challenge of detecting insider threats
- How Exabeam helps triage, detect, investigate, and resolve insider threats
- Data leak activity to watch for
- Benefits of using Exabeam for insider threats
The challenge of detecting insider threats
Credential-based attacks are on the rise, but when it comes to insider threats, employees are already logged in. An insider with malicious intent can exfiltrate data that can cause damage to the organization for personal gain or to adversely affect the organization’s reputation. Because of their access and knowledge of the organization’s most valuable assets, attacks involving malicious insiders are harder to identify and remediate than those that originate from outside the organization. To minimize harm to an organization, insider threat teams need a reliable method to monitor, detect, investigate, respond, and report on behaviors that identify malicious insider activity.
To detect data leak threats, many organizations rely on data loss prevention (DLP) tools, but detection from these tools depends primarily on static rules. Also, static correlation rules can be too broadly or narrowly defined, and result in alert noise with low fidelity or miss instances of a data leak altogether. Additionally, malicious insiders may know the organization’s security thresholds (for example, how much outbound data transfer would trigger an alert); this can allow them to remain under the radar to avoid detection. Understanding user behavior is critical to identifying insider threats and reducing the risk associated with incidents. Context — understanding what is normal behavior, even as normal keeps changing — enables organizations to recognize anomalous behaviors that might be indicative of malicious activity.
Let me share with you a story of a large, global manufacturing company. The CISO and SOC team initially started working on a SOC modernization project, but then the organization announced a corporate restructuring which was going to impact several hundred employees. Those employees were aware of the pending layoff and still employed, so the SOC needed to monitor their activity. Their incumbent legacy SIEM and existing tools couldn’t detect anomalous activity of users or assets. In this example, there was a possibility that internal employees could exfiltrate data and digital assets without being detected. The CISO spent a lot of time educating their board that compromised credentials aren’t the only way in — insider threats posed a very high risk.
How Exabeam helps triage, detect, investigate, and resolve insider threats
Malicious insiders are one of the hardest threats to identify. Unlike external attacks, these insiders hide in plain sight and use valid credentials. Legacy tools that rely on signatures and rules alone cannot defend against insiders. They can’t detect when user or asset behavior drifts from normal. Behavioral analytics and the context they deliver, combined with automation, are often your only defense.
New-Scale SIEM™ from Exabeam is designed to ingest data from thousands of sources, storing it in a cost-effective and highly scalable cloud-native data lake, and enabling accessible search of that data for investigation. Monitoring insider threat activities starts with Exabeam analyzing behavior for all users, groups, and assets to baseline normal behavior. After establishing the baseline of normal behavior and analyzing the activities, Exabeam sets a risk score for each activity — anything that is a deviation from normal gets a higher risk score — such as if the user emailed a huge amount of data outside the company, inserted removable storage into a laptop, or printed more than usual. If during a session, a risk score reaches a pre-set threshold, that user is flagged as notable and added to the notable user watchlist.
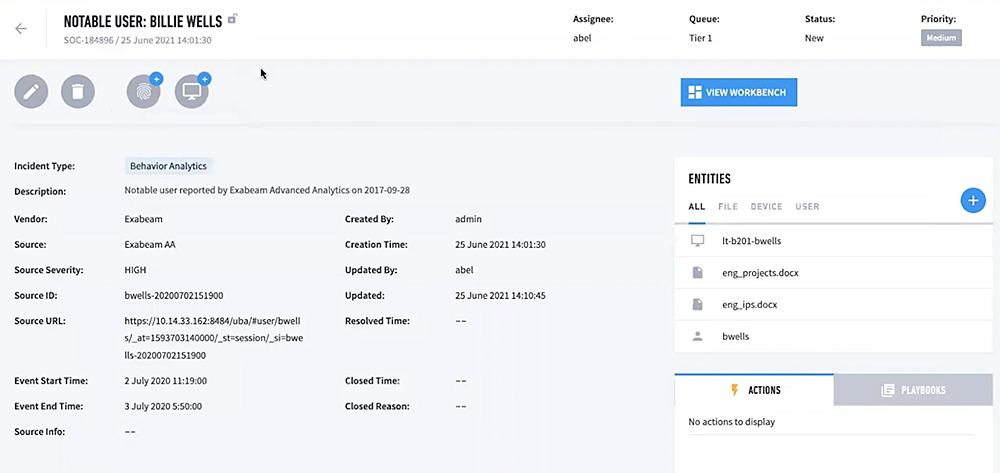
Every action that the user takes increases the risk score. To illustrate every attack story, Exabeam automatically reconstructs activities within Smart Timelines™ that show full event flows and actions to inform the next right action. This helps detect lateral movement by organizing incidents to follow attack activity, credential use, or permission changes within the environment. The results security teams gain: they find and stop the threats other tools miss, they uplevel their security team speed and performance, and they stay ahead of their adversaries. Smart Timelines help these teams dive deeper, faster, into user activity and investigations.
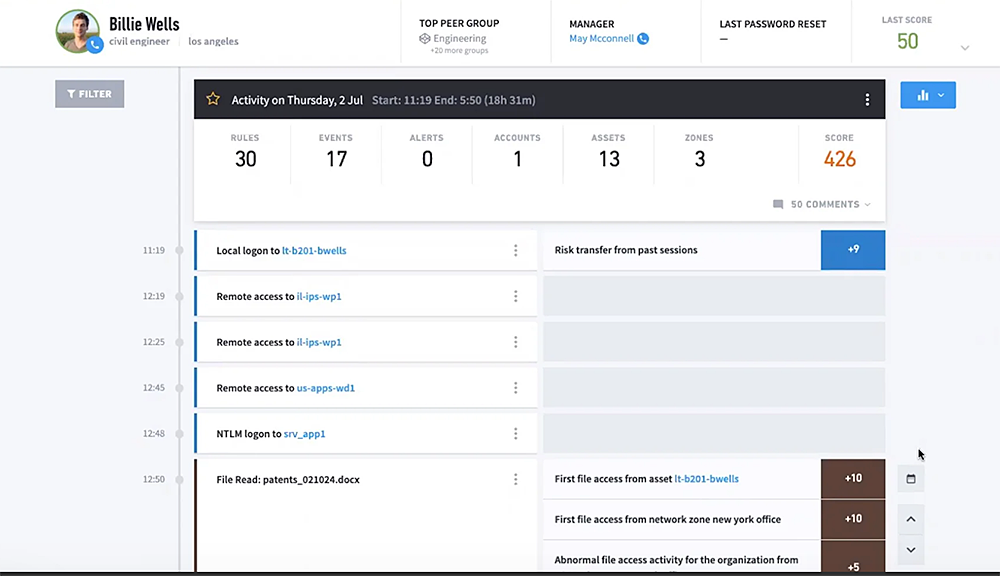
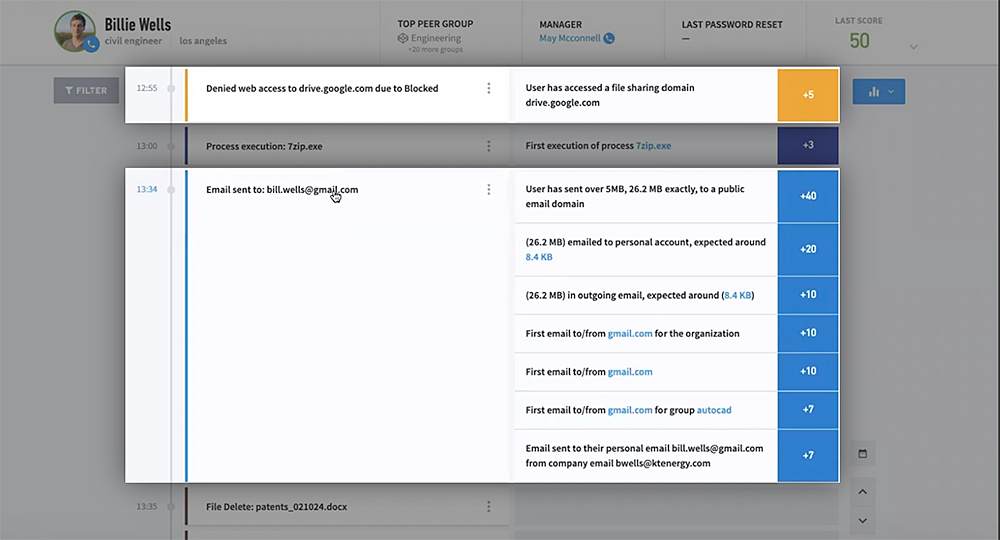
Data leaks can closely resemble normal activity, making them challenging to detect. Exabeam combines DLP alerts with authentication, access, and contextual data sources into a timeline of all a user’s activity. With a complete picture of a user’s activity, analysts can determine if the insider is acting with malicious intent and spend their time investigating actual risks.
Data leak activity to watch for
Key data sources
- Web security and monitoring
- Print activity
- Data loss prevention
- Email security and management
- File monitoring
- Database activity monitoring
- Endpoint security (EPP/EDR)
Key detection rule types
- Data leak
- Data leak via email
- Data leak via printer
- Data leak via a removable device
- Data leak via web
MITRE ATT&CK® tactic, technique and procedure (TTP) coverage
- TA0010: Exfiltration
- T1567: Exfiltration over web service
- T1052: Exfiltration over physical medium
Benefits of using Exabeam for insider threats
Your intellectual property and data are your organization’s most valuable currency. Whether or not your organization is experiencing layoffs or potentially downsizing, insider threats represent a viable threat and organizations with the strongest cybersecurity practices have insider threat programs in place to minimize risk.
Exabeam can uniquely help:
- Increase your team’s operational efficiency by using behavior analytics to increase DLP alert fidelity and prioritize response efforts
- Improve investigation quality and speed by enabling analysts to quickly answer key questions like, “Are they a flagged user?”, “What data was leaked?” or “Why is that person accessing that server for the first time in six months?” without performing advanced search queriesEnhance analyst productivity and decrease mean-time-to-respond (MTTR) with security orchestration automation and response (SOAR)-powered playbooks
Find additional resources here to help you further understand insider threats and how best to prepare your organization against these threats.
You can also speak to one of our experts, watch a demo, or see an interactive walkthrough of the malicious Insiders use case.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!