Keeping track of cyber threats isn’t easy. As soon as experts identify one, three or four more emerge for them to research and communicate. That’s where the MITRE ATT&CK® knowledge base comes into play. Through its federally-funded research and development centers, MITRE works to keep the public safe across all possible industries and disciplines. Those disciplines include technology and cybersecurity. This post looks at how MITRE has helped identify common techniques used in modern-day attacks and how you can use the knowledge base in your security strategy.
Understanding MITRE ATT&CK
Launched in 2013, the MITRE ATT&CK database catalogs all identified tactics, techniques and procedures (TTPs). The database is available and free to anyone who wants to access it, and it’s routinely used by cybersecurity professionals across all types of organizations for education and research purposes.
But staying abreast of so many TTPs can be overwhelming. Security analysts are overwhelmed by thousands of alerts, leaving little time for monitoring a database. Additionally TTPs are the most difficult threats to detect as shown by the “pyramid of pain”.
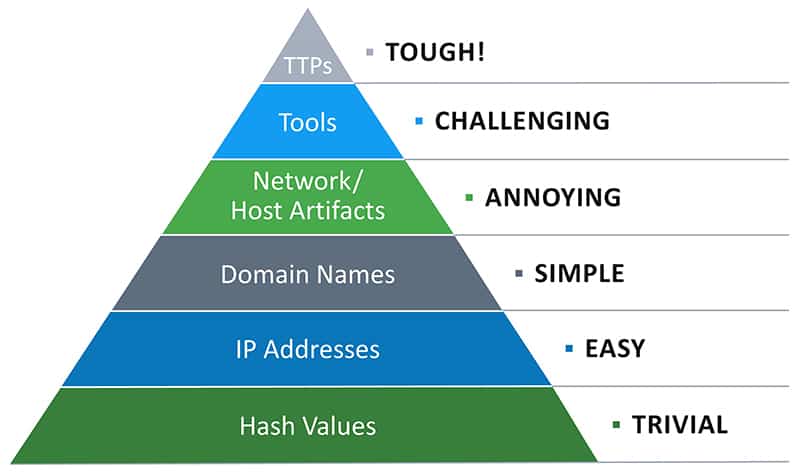
Figure 1: The “pyramid of pain” shows the level of effort required to detect different types of threat indicators.
This is where technology helps by doing the heavy lifting in automating threat detection and helping keep systems safe far better than an analyst can do manually. Here are some ways the right solution can ensure you’re getting the full benefits of MITRE’s research.
Combining MITRE ATT&CK with analytics
MITRE’s research identifies commonly-used techniques, but in most instances, you’re missing the context of the threat. A denied login could be a hacker trying to gain access, but it could also be an employee who simply forgot his password. The solution you use must be able to look at both the incident and the context to separate malicious intent from innocent mistakes.
The key to success when working within the MITRE ATT&CK framework is behavioral analytics. Behavioral analytics technology monitors systems to determine baseline behavior and in doing so, can more easily identify when an activity is outside of what’s normal. When systems administrators receive an alert, they’ll have the full picture so that they can better determine what they need to do to prevent further damage.
Exabeam and MITRE ATT&CK
Exabeam uses user and entity behavior analytics (UEBA) to ensure that the information analysts receive is complete and as useful as possible. Once a behavioral baseline is established, threats can be more accurately identified, which means you’ll be alerted not only when something is suspicious, but when the event is so unusual, it merits further attention.
To provide this accuracy, Exabeam’s technology uses an incident timeline called Smart Timeline™, which offers administrators more than some vague alert. You get a detailed list of events that help you see exactly what was happening when the anomaly occurred. Included in that timeline is risk scoring, along with whether an event within the timeline has been identified as a MITRE ATT&CK technique.
When you see an event identified as part of the MITRE ATT&CK framework, you can read more on its label, including the TTPs for that particular event. The label is tagged with MITRE ATT&CK TTPs that takes you straight to the MITRE ATT&CK knowledge base so that you can read further details on the particular technique and tactic that was used.
Using Exabeam for investigations
Investigating incidents is an important part of protecting your organization’s network. Exabeam makes it easy with Smart Timelines and Threat Hunter. Analysts can search by MITRE ATT&CK’s TTPs within the Threat Hunter tool, allowing them to search for anomalous events with techniques or tactics that adversaries might have used as defined in the MITRE ATT&CK framework. You can input a few key search terms and get results that you can then expand for more details.
When you search using Threat Hunter, you’ll also get the full Smart Timeline on the threat you’ve searched. This includes reasons, risk scores and contextual events to help you learn more about what’s happening on your network. As you continue to use Exabeam and take advantage of the data available from MITRE ATT&CK, you’ll find that you’re gaining information that you can put toward strengthening your organization moving forward.
In our whitepaper, “Unlocking Effective Threat Detection and Investigation with Analytics & TTPs,” we detail the MITRE ATT&CK framework and how TTPs relate to your systems. Click here to read our whitepaper and learn more about how Exabeam uses MITRE ATT&CK to protect your devices and network infrastructure.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













