Many security organizations discover the costs of using a legacy security and information event management (SIEM) tool are like the one-two punches of a prizefighter. The purchase cost hit you upfront before seeing any value at all. The second costs hit you later after deployment as you start ingesting log data. But, defenders of enterprise security don’t have to go down fighting a red balance sheet and wrath of the CFO. A new Ponemon survey commissioned by Exabeam found that 90% of its customers say this modern security management solution is highly effective at reducing the operational costs associated with using a SIEM for detection and investigation. And unlike legacy SIEMs, Exabeam users say this value occurs both upfront and after deployment.
A key takeaway from this research is that Exabeam’s value is quickly realized. Specifically, 92 percent of Exabeam respondents were able to see its value within a week after deployment versus 53 percent of users of other SIEM solutions (see Figure 8 below). This is nearly twice as many as respondents whose organization uses other SIEM solutions. Similarly, Exabeam users are far less likely to require professional services – either for deployment or for specialized assistance after implementation of the SIEM.
Effectiveness in minimizing the costs of using a SIEM – 90%
Controlling the ongoing operational costs of a SIEM should be an important priority for organizations. From a business perspective, the odds of fulfilling budget projections will rise if unnecessary spending is kept under control. The sprawling requirements of IT are a good reason to choose security products that avoid the razor blade syndrome. This is where the cost of the security product (a shaving razor) is quickly eclipsed by the ongoing cost of operations (buying razor blades). Obviously, one cannot eliminate all operational costs. The discerning choice of a SIEM, however, can certainly limit post-purchase spending on the solution.
Using a 10-point scale (1 = “worst” and 10 = “best”), Ponemon asked randomly chosen SIEM users to rank the effectiveness of their organization in minimizing the costs associated with using the tool to detect and investigate cyberattacks. Twenty percent ranked Exabeam SIEM as 7 or 8, and 70% ranked a value of 9 or 10 – a total of 90% ranking in these top two categories of effectiveness. By contrast, only 49% of users of other SIEM solutions ranked their organizations’ effectiveness in minimizing costs in the top two categories. The margin of successfully minimizing costs by organizations using Exabeam SIEM was nearly two-to-one!
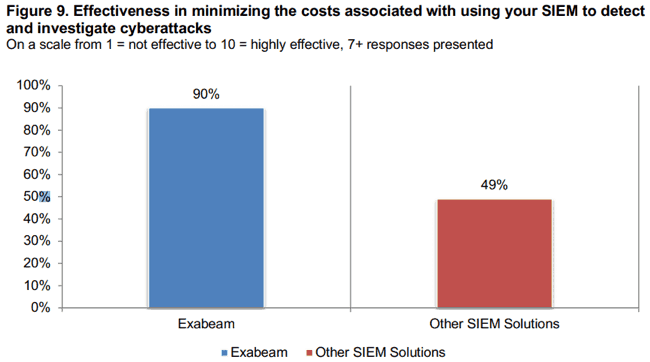
Figure 9: Ninety percent of Exabeam users say their organization was able to minimize costs associated with using the SIEM to detect and investigate cyberattacks.
A specific cost issue for legacy SIEMs is having to pay for log source license upgrades to accommodate growth in log data. Ponemon discovered this occurs for half of legacy SIEM users; and 46% of legacy users say the license model prevents them from getting log data needed for security. This obstacle hampers the fundamental requirement for a SIEM to ingest as much data as possible in order to be fully capable of helping analysts detect, investigate and remediate issues. Exabeam users report dramatically lower occurrence of these issues at 29% and 12%, respectively.
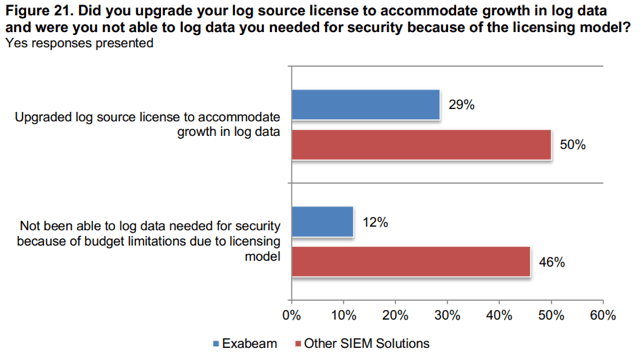
Figure 21: Half of legacy SIEM users say the cost of source license upgrades and 46% of legacy users say the license model prevents them from getting log data they need. Exabeam users report a significantly lower occurrence of these issues.
Enabling feature: predictable pricing. Legacy SIEM pricing models tied to the volume of data being collected lead to cost increases that are inevitable, unpredictable, and – more often than not – substantial. Exabeam approaches pricing differently. It uses a flat, user-based model that removes uncertainty and eliminates the need to cut another check every time a new data source is added to the mix. Exabeam makes it easy and affordable to collect data from each and every source the security team thinks is worthwhile – and eliminate cash flow surprises for your organization’s CFO.
Realized value within days or a week – 92%
Buyer’s remorse occurs when it’s hard to tell if the thing you bought is delivering any value. This annoying outcome is all too common with technology purchases. As vendors demonstrate products or initiate a proof-of-concept project, you may recall some pre-sales specialists saying something like, “It takes a while to get used to, but then _________(fill in the promise)________.”
To understand whether those promises were fulfilled, Ponemon asked: How long did it take your organization to realize value from their SIEM solution? For Exabeam users, 52% said they realized value in less than a week. Another 40% said value was realized within a week. No chance of buyer’s remorse for 92% of Exabeam users! For users of other SIEM solutions, rankings were respectively 28% and 25% so just over half recognized value within a week. Again, nearly a two-to-one margin in favor of Exabeam SIEM.
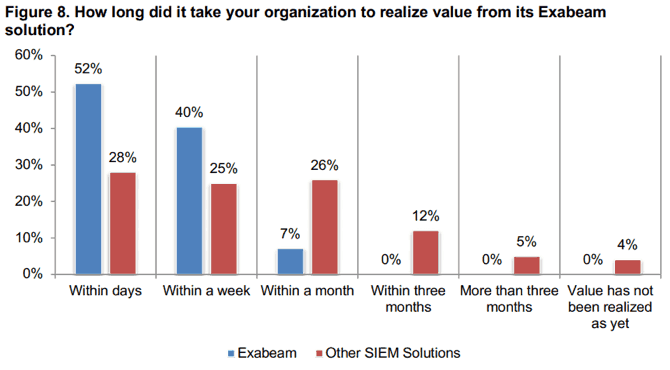
Figure 8: Fifty-two percent of Exabeam users say they realized value from their SIEM solution within days.
Enabling feature: use case models. Knowing how to start using a new SIEM makes all the difference in realizing value right out of the gate. Exabeam provides hundreds of use case rules and models to help you accelerate the set-up phase of deployment. Our models are easily modified for specific requirements of your organization’s various use cases. Example use cases include protecting against insider threats; identifying compromised credentials; detecting account creation and management; augmenting endpoint analytics; monitoring high-risk employees; and prioritizing security alerts. When you flip the switch and go live with Exabeam, you’ll know what to expect and will see the value of results right away.
Did not use professional services for deployment – 79%
SIEM operators are quite familiar with a business strategy used by many solution providers that includes strong encouragement to purchase professional services. Indeed, the integration of numerous third-party tools and data sources can be complex, intimidating and beyond the capabilities of internal staffers to carry out on their own. Such a perception often rises at the beginning of a SIEM purchase and on through deployment when everything seems new and un-doable without expert professional services on tap. But the reality is that lengthy service engagements are not necessarily applicable to every SIEM.
Consider the issue of SIEM deployment. Ponemon asked: Did your organization purchase any professional services to help with the SIEM deployment? Just 21% of Exabeam users responded “yes”; 79% required no extra help to deploy the SIEM. By contrast, twice as many users of other SIEM solutions had to hire professional services for deployment. Which is another way of saying that deployment of Exabeam SIEM is not as complex or intimidating or beyond the capabilities of internal staffers as it is with deploying other SIEM solutions.
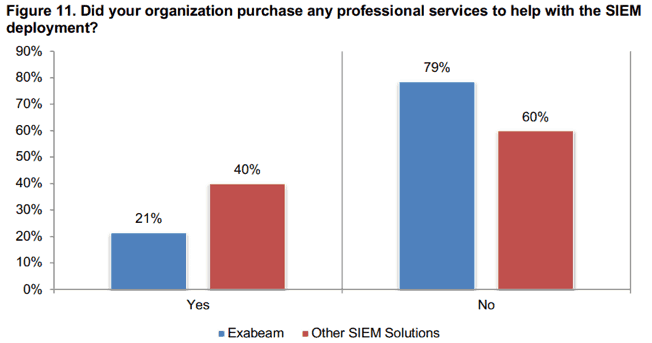
Figure 11: Just 21% of Exabeam users purchased professional services to help with SIEM deployment and 79% required no extra help to deploy the SIEM.
Enabling feature: 8-step model for SIEM migration. As a mature industry segment, SIEM deployments (especially for larger organizations) are often a migration from using a legacy product to something new. Exabeam leads the industry with its highly-usable process flow, Eight Steps to Migrate Your SIEM. The steps are
- Determine SIEM priorities
- Select use cases
- Scope data collection sources
- Configure log sources
- Prepare SIEM content
- Define operational processes
- Establish benchmark criteria
- Evaluate next steps
Exabeam clearly describes the process of modernizing your SIEM so your security team can understand how to execute the steps without having to always hire external professional services people for help with deployment.
Did not use professional services after deployment – 55%
The oft-needed requirement to hire professional services after SIEM deployment is the razor blade issue discussed above. Budget requests for post-deployment professional services often entail help with implementing a new use case, tuning a SIEM, help with incident response and under-the-hood assistance with tricky integrations. You may have signed some of these purchase orders in your own organizations. While providing extra help, professional services supplement the capabilities of the organization at the cost of continued cash outflows.
The Ponemon survey asked respondents to report their experiences in post-deployment categories mentioned above. Despite these reasonable scenarios, 55% of Exabeam users did not purchase any additional professional services after deployment. By contrast, just 29% of people using other SIEM solutions reported no purchases of additional services. Again, almost a two-to-one margin of success for Exabeam SIEM users on this issue.
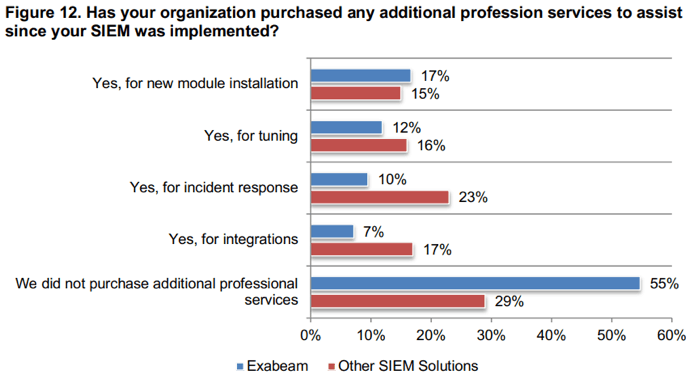
Figure 12: More than half of Exabeam users did not purchase any additional professional services after deployment, while just 29% of people using other SIEM solutions reported no purchases of additional services.
Enabling feature: Exabeam prebuilt integrations. With legacy SIEMs, a frequent post-deployment call for hiring professional services comes when an organization needs to integrate a broader set of tools for increasingly complex enterprise security requirements. Often this requires adding new data sources for ingestion into the SIEM to augment analytics and detection. Exabeam Security Management Platform eases the requirement for ongoing professional services by providing prebuilt integrations with more than 200 data sources. The integrations streamline the process of aligning essential log data from security and IT devices and solutions for supporting each respective use case.
Conclusion
Reducing operational costs and recognizing value quickly are reasonable expectations as you consider selecting a SIEM for your organization. Based on survey responses in the Ponemon study they are more commonly achieved by Exabeam users than they are for users of other SIEMs. Most of the value and savings metrics tilt in Exabeam SIEM’s favor by a margin of almost two-to-one. To learn more about these and other insights related by users on the value proposition of a SIEM, we invite you to read the full report, Exabeam SIEM Productivity Report.
Additional resources
Ponemon Study Reveals Analysts Tasks Take 50% Less Time When Using Exabeam
Ponemon Study Reports 95% of Exabeam SIEM Users Rank It as Highly Effective for Security
Attend our webinar on Tuesday, October 22: How to Increase SOC Analyst Productivity and Security Effectiveness
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













