In the wake of a data breach, is cyber attribution a fundamental step in incident response (IR) or merely a “nice to have”?
When a cyber breach occurs, it’s only natural to want to know who’s responsible. The process of identifying the perpetrators is known as cyber attribution. Depending on the tools and processes, it can be a long and arduous process, often taking months or even years of investigation to learn anything of value. However, does that mean it’s a waste of time?
Let’s examine the role that attribution plays in modern-day incident response and assess the amount of effort organizations should place on it.
What is cyber attribution?
Cyber attribution is the process by which security analysts collect evidence, build timelines, and try to piece together evidence in the wake of a cyber attack, so that they can identify who and what is responsible for the breach.
Within the context of an incident response, attribution attempts to address the ancillary questions surrounding the “who” and the “why” of an attack, as opposed to the more immediate concerns of “what”, “when”, “where” and “how”. As with any forensic process, answering these questions is not something that can be completed quickly and will usually require significant amounts of time and resources. Furthermore, in many cases, the process involves a significant amount of educated guesswork—and even analytical leaps—meaning results can often be subject to debate and difficult to back up with hard facts.
If it’s so difficult, why do it?
On the flip side, effective attribution can be a hugely valuable source of intelligence for cyber-breach victims. In a world where many perpetrators go to great lengths to cover their tracks, any information gained through the attribution can bring organizations and law enforcement one step closer to catching those responsible. Taking the time to learn from both successful and thwarted breaches can also play an important role in future incident response planning activities—possibly the finest learning tool available to responders. Just as historic battles are researched, as should incidents. The security industry has a saying, “There’s gold in your prior incidents.” Without attribution, that gold might not be found, potentially leaving organizations open to the same attacks over and over again.
What are the ingredients required for effective attribution?
The first requirement is extensive knowledge and unencumbered visibility into the IT environment, including the solutions used by the adversary, such as free cloud services. For many organizations, this is the biggest stumbling block of all. Without this insight, anyone attempting to carry out the long task of attribution is virtually guaranteed to fail because they simply won’t know what signs to look for; nor will they have the expertise to thread it into a cohesive timeline. Key indicators will be missed, leaving the investigation floundering from the start. It takes time and effort to understand an environment fully, and if organizations aren’t prepared to invest in finding effective solutions, any attempts at attribution will be largely pointless.
The second key ingredient for effective attribution is knowledge of potential adversaries. This includes who they might be, why they might attack, and what they might potentially leave behind. While predicting the future is never easy, laying the groundwork ahead of time means that in the event of an attack, the organization won’t need to start from scratch.
Finally, significant time and resources are required for your attribution efforts to be successful. Attribution is not a fast process, and the larger the investigation, the longer it can take. In particularly serious incidents, external law enforcement may need to get involved, extending the investigation time scale and adding further layers of communication to the whole process. The messages here are: Don’t expect results overnight. Use caution: Adversaries with enough resources will work to include “false flags” to trick investigators. Why? Misdirection consumes additional resources and can lead to false attribution, which is technically and politically beneficial to the perpetrator. This was seen in 2018 with the Olympic Destroyer malware used in the PyeongChang Olympics attack which ended up being a deliberate attempt to plant a false attribution flag, and the attack was initially, falsely attributed to the North Koreans.
Using next-gen SIEM for Attribution
SIEM tools that provide automated incident response with detailed timelines are a best practice to more quickly and accurately identify perpetrators, so investigators can understand the evidence and build a case.
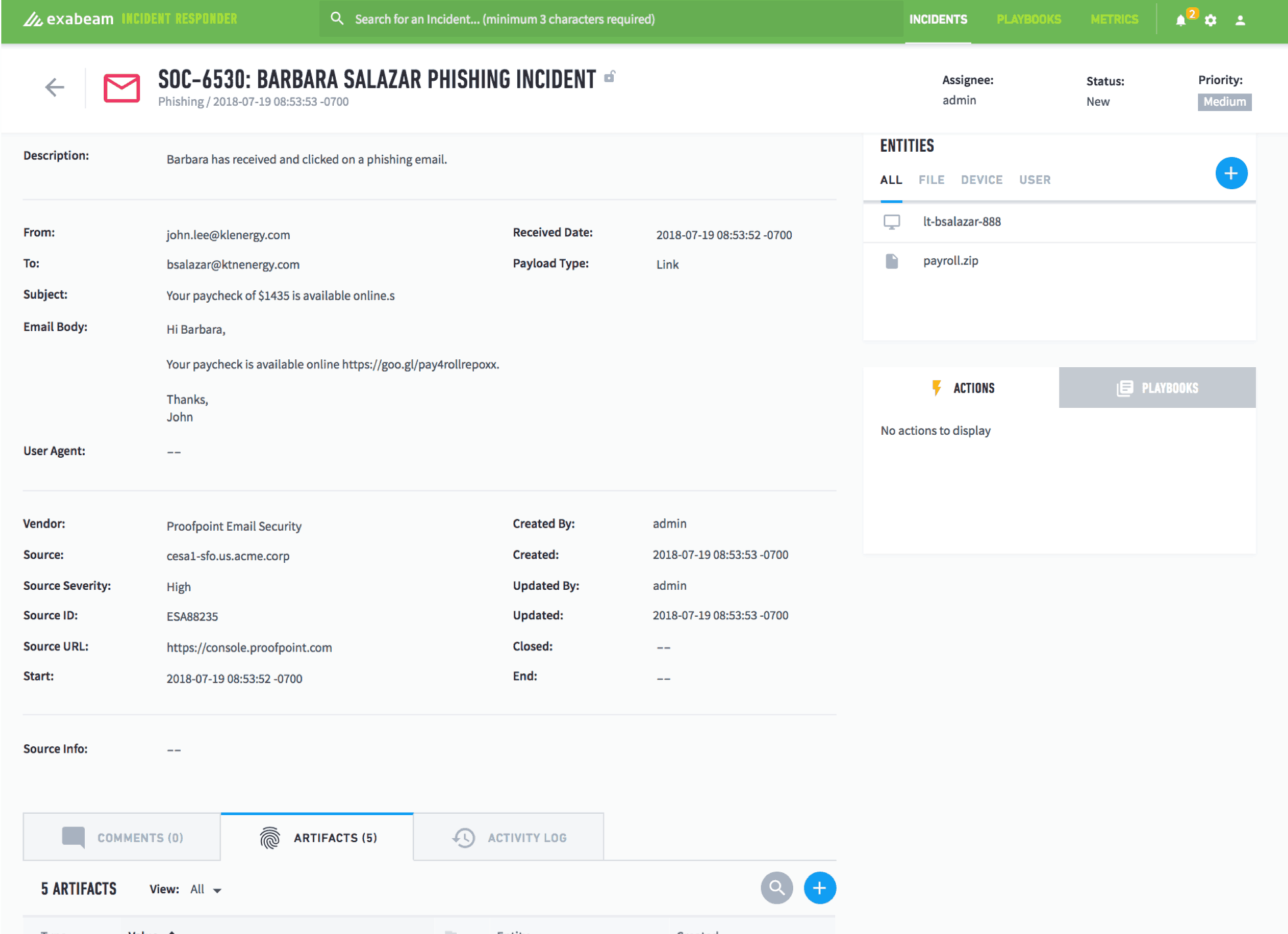
Figure 1: An incident created after the user received and clicked on a phishing email, with the artifacts and evidence collected.
As part of gathering evidence during the attribution process, security analysts also need accurate timelines listing the risky behaviors, so they can pinpoint the events that led to the incident.
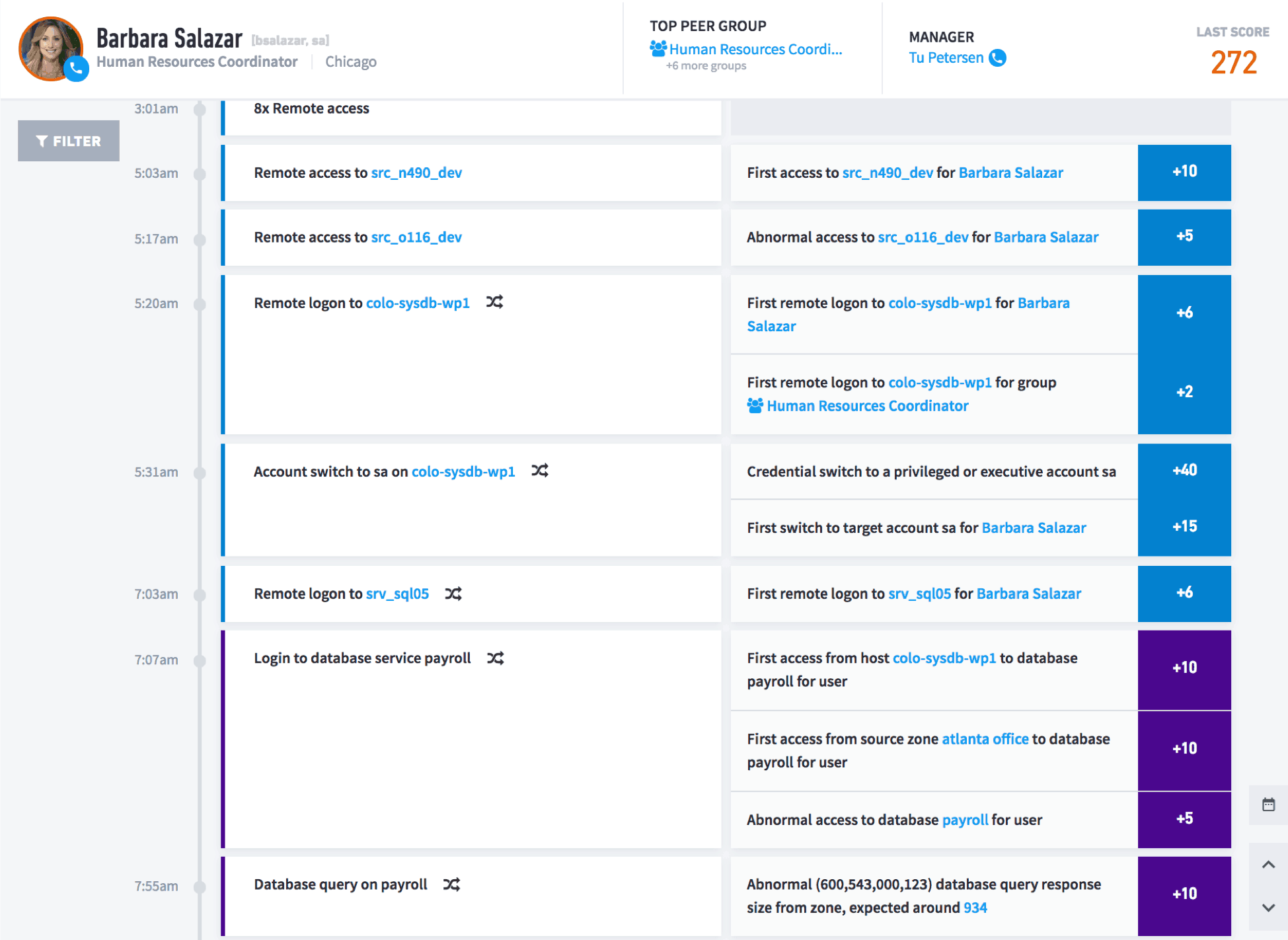
Figure 2: A detailed user timeline showing anomalous behavior with links to the evidential artifacts of the incident.
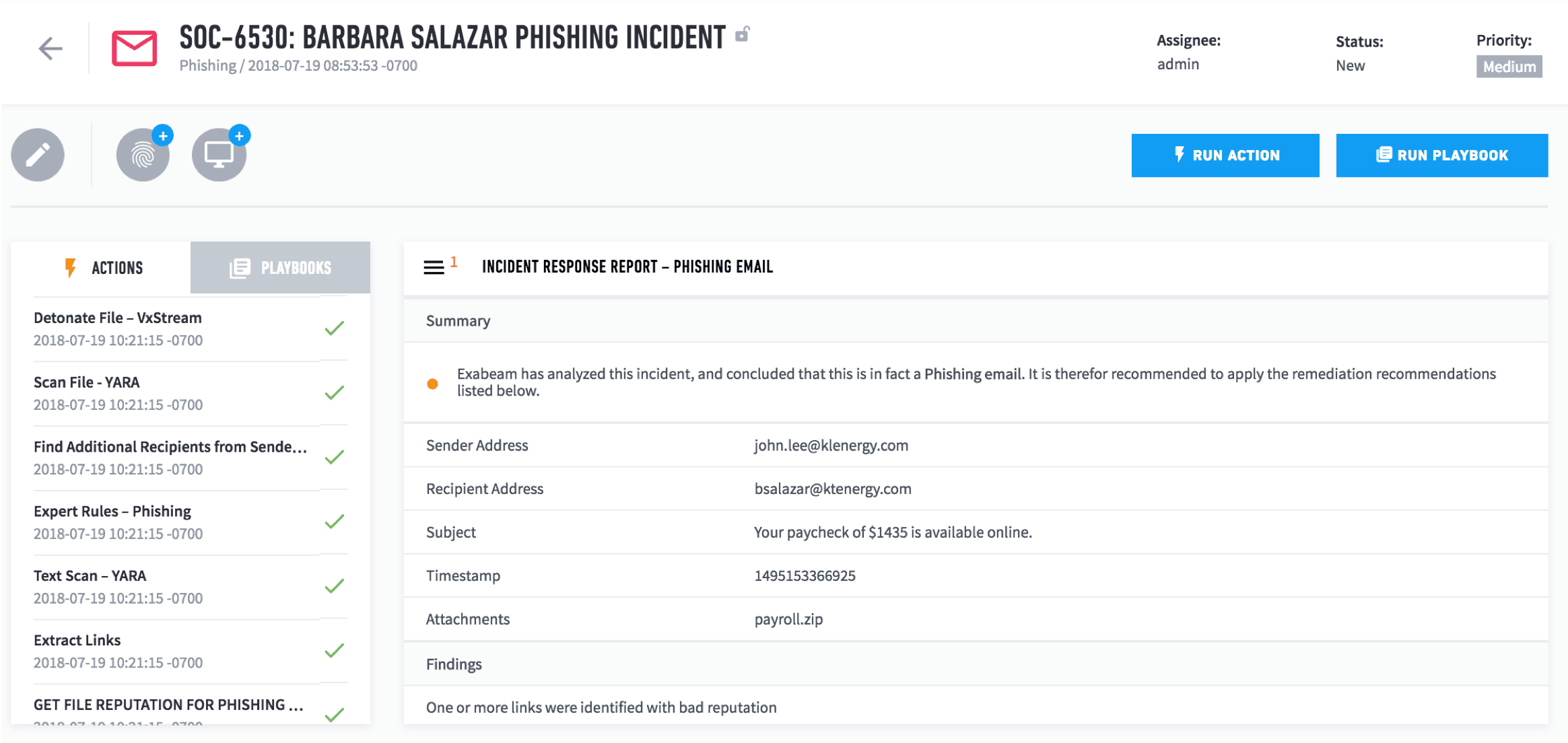
Figure 3: An automated response playbook collecting evidence on the incident, extracting links, getting email reputation for phishing email verification, and detonating files.
What does success look like?
The chances may be remote that an organizations will track down their attackers. Success, at some level, might require the assistance of outside experts and law enforcement. View this as a concurrent task to incident response and recovery. Success can take many forms. It may highlight new types of attacks, expose vulnerabilities in existing security, or provide information on where the attackers may be geographically, including their prior engagements and their motives. While this may not lead to a day in court, it may inform future security planning and investment, and help to educate the entire organization.
Building cyber attribution capabilities into your incident response plan
While some organizations may not be able to attribute attacks to certain threats, cyber attribution capabilities can be part of your incidence response plan (IRP) when using the right tools. There are also companies that outsource their IR practices, including attribution.
As a general rule, the larger the organization, the more important attribution will be. For government bodies and organizations involved in highly sensitive fields, such as matters of national security, it can be absolutely critical to know who is behind an attack. A recent example is the NotPetya cyber attack, which has now been attributed to Russia following a lengthy investigation by the U.S. government. For the vast majority of organizations, the time and cost of a comprehensive attribution investigation usually outweighs the benefits. Having said that, there is always something to be learned from prior incidents, if an organization has the time and the resources to properly research the breach.
The importance of attribution boils down to the organization involved and whether or not it has the ability to see an investigation through. Due to the time consuming nature of investigations, it will never be the first thing to do in the event of a breach. As the dust settles and questions are asked about “who” and “why”, attribution may be the only way to find meaningful answers. Just don’t expect results quickly—and use caution!
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













