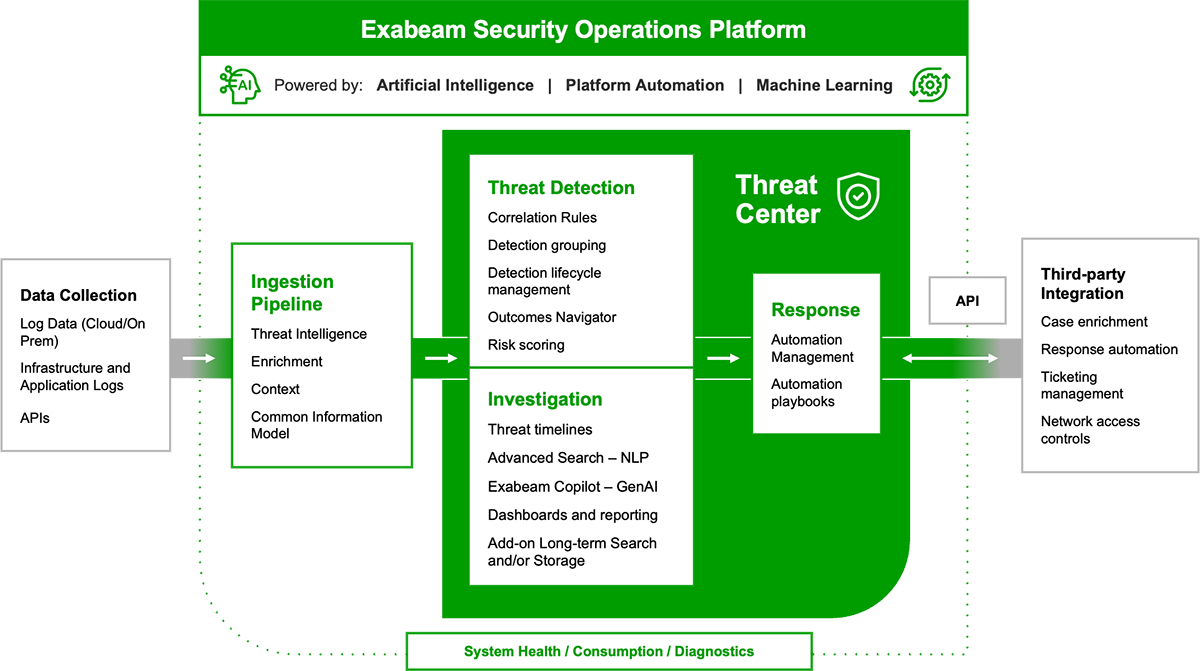
The AI-Driven Exabeam Security Operations Platform
Exabeam gives security operations teams a holistic view of incidents for faster, more complete response with the industry’s most advanced and powerful cloud-native platform for SIEM, UEBA, and SOAR to deliver world-class TDIR.
Detect. Defend. Defeat.™
Security operations teams are struggling with the limitations of legacy SIEM. Product innovation hasn’t kept pace with the growth of data, the sophistication of attacks, or the shift to the cloud. Legacy SIEM tools are too complex, point security solutions fail to provide a complete picture of a threat, and both bury analysts in alerts, resulting in slow, ineffective, manual investigations.
Addressing these gaps requires a modern AI-driven platform engineered for threat detection, investigation, and response (TDIR), prioritizing thoughtful usability and broader insights, purpose-built for security, and leveraging the speed, scale, and efficiency of the cloud.
Choose the right solution for you
Whether you replace a legacy SIEM, or complement an ineffective SIEM solution by adding UEBA, SOAR, and TDIR content, the modular Exabeam Security Operations Platform can help you achieve security operations success.
- SIEM replacement: Exabeam Fusion
- SIEM augmentation: Exabeam Security Investigation
vendor integrations
Collect data from more than 680 different product integrations across 350+ different vendors.
pre-built compliance dashboards
Build a dashboard in a minute from 14 different pre-built chart types as if you were using a leading BI tool.
MITRE ATT&CK® categories
Coverage for all ATT&CK categories, including 199 techniques and 379 sub-techniques.
The AI-Driven Exabeam Security Operations Platform
The AI-driven Exabeam Security Operations platform applies AI and automation to security operations workflows to deliver the industry’s most effective offerings for threat detection, investigation and response (TDIR).
Exabeam Security Log Management
Exabeam Security Log Management is the industry’s most advanced cloud-native solution in support of security use cases. The product represents the entry point to ingest, parse, store, and search security data in one place, providing a lightning fast, modern search and dashboarding experience. Exabeam Security Log Management delivers affordable log management at scale without advanced programming, query-building skills, or lengthy deployment cycles.
Exabeam SIEM
Exabeam extends the cloud-scale capabilities of Exabeam Security Log Management with additional features for threat, detection, investigation, and response (TDIR). Exabeam SIEM includes Alert and Case Management, over 190 pre-built correlations, integrated threat intelligence, and powerful dashboarding capabilities. The solution delivers analysts new speed, processing at over 2M events per second (EPS) sustained.
Exabeam Fusion
Exabeam Fusion represents the industry’s most powerful and advanced product for TDIR. Fusion unites the combined capabilities of the cloud-native Exabeam Security Operations Platform: efficient data storage, seamless data ingestion, context enrichment, lightning-fast query performance, powerful behavioral analytics, use case content, and SOAR automation.
Exabeam Security Analytics
Exabeam Security Analytics was designed to upgrade an organization’s defenses and detect sophisticated and credential-based attacks. As the only UEBA product that can run on top of a third-party SIEM or data lake, Exabeam Security Analytics ingests, parses, and normalizes data using a Common Information Model (CIM). Exabeam Security Analytics UEBA baselines normal behavior for users and devices to highlight anomalies and assigns a risk score to each notable event.
Exabeam Security Investigation
As the only product in the market that runs on top of a third-party SIEM or data lake, Exabeam Security Investigation combines content, workflows, automation, and UEBA to augment ineffective SIEM products with outcomes-focused TDIR capabilities. Exabeam Security Investigation helps teams standardize around TDIR best practices.
Put Your Security Skills to the Test
Challenge yourself and compete with peers in a formidable game of Exabeam CTF. You’ll get a firsthand view into the power of Exabeam behavioral analytics, threat hunting, and automation and their ability to transform your team’s TDIR capabilities.

“Using Exabeam reminded me of how surprisingly fast the platform updates. There is an almost daily improvement on desired functions, and with Exabeam, it all keeps getting better.”
Keisuke Kawakami
Infrastructure System Division | MTI Ltd.

Trusted by organizations
around the world





















What else can Exabeam do for you?
At Exabeam, we deliver persona-based workflows, purpose-built for security. With support resources, professional services, training opportunities, and business partnerships, Exabeam can usher your organization through deployment and beyond.
Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.

DATA SHEET
The Exabeam Security Operations Platform
Whether you replace a legacy product with a New-Scale SIEM, or complement an ineffective SIEM solution by adding the industry’s most powerful user and entity behavior analytics (UEBA) and automation to it, the Exabeam Security Operations Platform can help you achieve security operations success.

EBOOK
The Ultimate Guide to Behavioral Analytics
The UEBA software market was valued at $373.37 million in 2020, and is projected to reach $5469.49 million ($5.48 billion) by 2028, growing at a CAGR of 40.5% from 2021 to 2028, according to Verified Market Research. Read this guide to help better understand UEBA and how it can be adopted to improve your overall security posture with faster, easier, and more accurate threat detection, investigation, and response (TDIR).
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision










