New-Scale SIEM™ Features
The powerful combination of cloud-scale security log management, powerful behavioral analytics, and an automated investigation experience.
Detect. Defend. Defeat.™
Security operations teams are struggling with the limitations of legacy SIEM. Product innovation hasn’t kept pace with the growth of data, the sophistication of attacks, or the shift to the cloud. The legacy tools are too complex, fail to provide a complete picture of a threat, and bury analysts with alerts resulting in slow, ineffective, manual investigations, creating a SIEM effectiveness gap.
To address this gap you need a SIEM platform built from the ground up for security leveraging the speed, performance, and efficiency of the cloud. The Exabeam Security Operations Platform provides complete coverage.
Cloud-scale security log management
Cloud-scale log management to ingest, parse, store, and search log data with powerful dashboarding and correlation.
Collectors
The Exabeam Security Operations Platform provides extensive data collection capabilities and coverage through a single interface to securely configure, manage, and monitor the transport of data.
Log Stream
Rapid log ingestion processing more than 1M events per second sustained, using a Common Information Model and parsing at ingest. A central console enables you to visualize, create, deploy, and monitor parsers within a unified ingestion pipeline for all Exabeam functions.
Search
Simplified search experience with faster query and instant results over petabytes and years of data; search hot and cold data at the same speed.
Reporting and Dashboards
Print, export, or view dashboard data with pre-built compliance reports, customized reports, and dashboards with 14 different chart types.
Correlation Rule Builder
Compare incoming events with predefined relationships between entities to identify and escalate anomalies. A single interface lets you write, test, publish, and monitor up to 1,000 custom correlation rules for your most critical business entities and assets.
Powerful behavioral analytics
A majority of the breaches involving credential theft or misuse often appear as anomalous activity on an endpoint, server, or application. Exabeam offers industry-leading user and entity behavior analytics (UEBA) that baselines normal behavior of users and devices with histograms to detect, prioritize, and respond to anomalies based on risk. The more than 1,800 rules and behavior models automatically detect potential security threats such as credential-based attacks, insider threats, and ransomware activity by identifying high risk or anomalous user and entity activity.
Advanced Analytics
Advanced Analytics offers UEBA with more than 1,800 rules, including cloud infrastructure security, and more than 750 behavioral model histograms that automatically baseline normal behavior to detect, prioritize, and respond based on risk.
Exabeam Smart Timelines™
Exabeam automatically baselines normal activity for all users and entities, presenting all notable events chronologically within a Smart Timeline. The timeline conveys the complete history of an incident highlighting the risk associated with each event and saving an analyst from writing hundreds of queries.
Dynamic Alert Prioritization
Machine learning automates the prioritization of third-party alerts, and infuses them with UEBA context to dynamically identify, prioritize, and escalate alerts requiring the most attention.
Automated investigation experience
Today’s cybersecurity teams are buried in a sea of noise, manually investigating alerts only to end up with inconclusive outcomes. Exabeam offers an automated experience across the entire TDIR workflow. Built-in timelines reconstruct the chain of events across all log sources, enriched with relevant context as well as scripted response actions, allowing analysts to quickly see and act on meaningful alerts. This recaptures two-thirds of the time an analyst spends on detection, triage, and investigation.
Smart Timelines™
Exabeam baselines normal activity for all users and entities, and presents all notable events visually and chronologically within an automated Smart Timeline.
Alert and Case Management
Centralize incidents sourced from Exabeam or third-party products for an analyst with manual review or automate the alert triage workflow.
Dynamic Alert Prioritization
Machine learning automates third-party alert prioritization, infusing third-party security alerts with UEBA context to dynamically identify, prioritize, and escalate alerts requiring the most attention.
Outcomes Navigator
Outcomes Navigator maps the feeds that come into Exabeam products against the most common security use cases and suggests ways to improve coverage.
Incident Responder
Optional add-on to orchestrate and automate repeated workflows to 100 third-party products with 576 actions and operations, from semi- to fully automated activity.
Action Editor
An intuitive, self-service interface guides administrators to build custom response actions or set up integrations with third-party IT and security tools.
MITRE ATT&CK® Coverage
The Exabeam Security Operations Platform uses the MITRE ATT&CK framework as a critical lens to help improve the visibility of your security posture.
Context Enrichment
Context enrichment provides powerful benefits across several areas of the platform. Exabeam supports enrichment using three methods: threat intelligence, geolocation, and user-host-IP mapping.
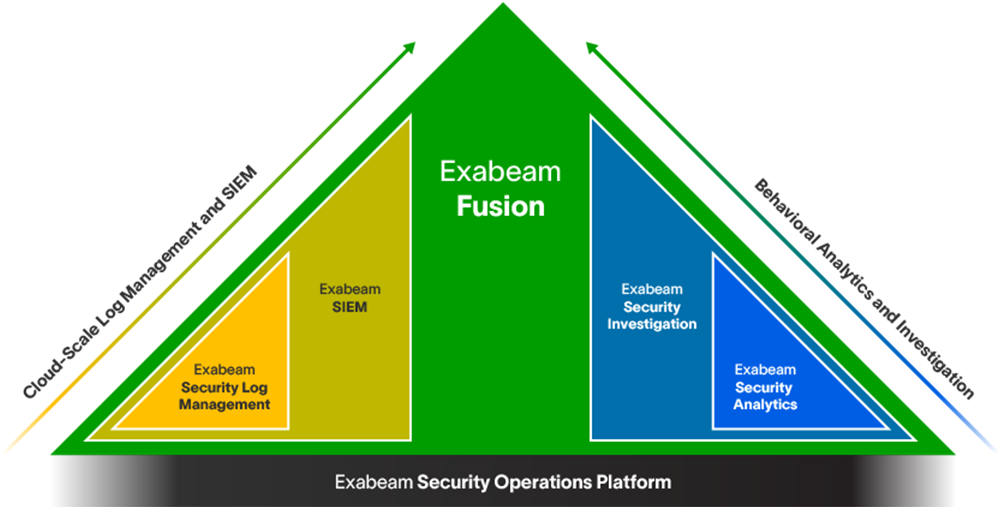
The Exabeam Security Operations Platform
The Exabeam Security Operations Platform provides the industry’s most complete cloud-native product offerings for complete threat detection, investigation, and response (TDIR) coverage.
Compliance and Certifications
Exabeam achieved ISO 27001 and SOC 2 Type II certification, is registered and certified with Privacy Shield, has appropriate technical and organizational measures in place for GDPR, and has resources available to help you address commitments to your own customers and their personal data.
Context Enrichment
Context enrichment provides powerful benefits across several areas of the platform. Exabeam supports enrichment using three methods: threat intelligence, geolocation, and user-host-IP mapping.
Integrations
Exabeam enbales data collection with 200+ on-premises products, 30+ cloud-delivered security products, 10+ SaaS productivity applications, and 20+ cloud infrastructure products. Our 7,937 pre-built parsers support 549 products. We support 100 third-party SOAR integrations with 576 response actions.
Log Stream
Delivers rapid log ingestion processing at a sustained rate of more than 1M EPS. A central console enables you to visualize, create, deploy, and monitor parsers within a unified ingestion pipeline for all Exabeam products and features. As it is ingested, data is parsed using 7,937 pre-built log parsers and enriched using context sources from open source and commercial threat intelligence feeds.
MITRE ATT&CK® Coverage
The Exabeam Security Operations Platform uses the MITRE ATT&CK framework as a critical lens to help improve the visibility of your security posture.
Outcomes Navigator
Support measurable, continuous improvement focusing on outcomes by recommending information, event stream, and parsing configuration changes to close any gaps.
Correlation Rule Builder
Write, test, publish, and monitor hundreds of custom correlation rules for your most critical business entities and assets, including defining higher criticality via Threat Intelligence Service-sourced activity.
Reporting and Dashboards
Print, export, or view dashboard data with pre-built compliance reports, customized reports, and dashboards with 14 different chart types.
Service Health and Consumption
High-level and detailed views of the health and data consumption performance of your cloud-delivered service. Visualize service health and data consumption while monitoring connections and sources.
Threat Intelligence
Add context enrichment to events ingested from multiple commercial and open source threat intelligence feeds — then aggregate, scrub, and rank them, using proprietary machine learning algorithms.
pre-built parsers
As it is ingested, data is parsed using over 9,500 pre-built log parsers and enriched using context sources from open source and commercial threat intelligence feeds.
events per second
Rapid log ingestion processing at a sustained rate of over 2M EPS
anomaly rules
Over 1,800 anomaly rules, including cloud infrastructure security, with over 795 behavioral models that automatically baseline normal behavior of users and devices.
What else can Exabeam do for you?
At Exabeam, our goal is to help you achieve your business outcomes. Leverage our breadth of experience, resources, and tools to help your security team meet their business goals through deployment and beyond. This goal is our key focus for customers and partners alike.
Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.

DATA SHEET
The Exabeam Security Operations Platform
Whether you replace a legacy product with a New-Scale SIEM, or complement an ineffective SIEM solution by adding the industry’s most powerful user and entity behavior analytics (UEBA) and automation to it, the Exabeam Security Operations Platform can help you achieve security operations success.

REPORT
Introducing Exabeam Fusion: The Industry’s Most Powerful and Advanced Cloud-native SIEM
Security Operations success requires a new approach: New-Scale SIEM™. Exabeam Fusion, our most comprehensive offering, introduces New-Scale SIEM™ and represents the industry’s most powerful and advanced cloud-native SIEM.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision









