The Web Browser: A Critical Source for Digital Forensic and Cybersecurity Investigations

Whatever your browser preference—Chrome, Firefox, Safari, Internet Explorer, or Edge—your browser is more than how you access applications and websites. It’s also a potential cache of many things personal and professional, from your driving habits, work hours, bank accounts, and job projects, to a record of the websites and restaurants you frequent—as well as a place to find your stored passwords. Some would say with its level of access, the browser is not only a roadmap of your personal and professional life, it’s a window into your thoughts.
Law enforcement investigators have long been aware of the power of the browser to provide important information and have zealously included it in their criminal investigations. Back in 2009, a California investment banker who claims he thought he hit a deer was sentenced to three years in prison—partly because his ensuing Google search terms included “hit-and-run”. In 2017, a post-doctoral associate at a research university in Cambridge, Massachusetts, was arrested and charged with insider trading. It was alleged that he traded on confidential corporate information that he obtained from his spouse, a lawyer at an international law firm. His web searches allegedly included an article entitled, “Want to Commit Insider Trading? Here’s How Not to Do It.”
Browser Features Make Life Easier by Retaining a Plethora of User Information
Web browsers store an incredible amount of important and sensitive information about an individual’s personal and professional activities. Features like remembering recently-viewed web pages, recording web form data, saving passwords, sending geolocation information, and syncing browser history across devices are all designed to make life easier. As a result, not only can this information be exploited by cyber criminals (as I discussed in my blog, How Criminals Can Build a “Web Dossier” from Your Browser), investigating the abundance of information stored in a person’s browser is an important part of a security team’s incident playbook and law enforcement’s criminal investigations.
For cybersecurity analysts, a browser investigation can be a critical step in their incident response playbooks. It typically occurs after a user has crossed a predefined risk threshold (becoming “a notable user”), or after a system has been flagged as suspicious or potentially compromised. In a criminal investigation, it’s done after the confiscation of a suspect’s laptops and phones. Khairullozhori Matanov, a friend of the Boston bomber, was charged with four counts of obstruction of justice for clearing his browser.
As security analysts face an increasing number of alerts with a limited amount of time and resources to respond, the ability to perform browser investigations efficiently is becoming more important. Due to the prevalence of HTTPS and other privacy measures, it is difficult for investigators to examine web activities by looking at network traffic alone. Any deep-dive investigation should involve looking at the browser artifacts on endpoints (like laptops or cell phones). Pulling every bit of information possible out of a user’s browsing history can be key to reconstructing a user’s activities.
Exabeam’s Survey of Digital Forensics and Incident Response Professionals
In April 2018, Exabeam conducted a survey of digital forensics and incident response (DFIR) professionals to better understand what they are experiencing during their web browser investigations in the field. Among other things, we were interested in what web browsers they encountered during their cases, how many devices they examined a month, and how long each review took.
While there are dozens of web browsers on the market, three of them dominated the results. It’s not surprising that Chrome, which is available on every platform and is the most popular web browser in the world, took the top spot, while Internet Explorer (IE) and Firefox took second and third places, respectively. The distribution of browsers can be dependent on the host operating system, while Chrome and Firefox can run on most systems, and Safari is only on Apple devices, and IE and Edge are only on Microsoft Windows. The discrepancies in the survey responses between IE and Edge are also interesting, since both browsers are present on Windows 10. Either investigators are still looking at a lot of Windows 7 devices, or they may be missing Edge on Windows 10 in their investigations.

Figure 1 – The browsers DFIR professionals see during their investigations, with Google Chrome holding the top spot.
We found that 66 percent of investigators examined five to 20 devices per month, while only eight percent looked at 40 devices or more. Investigators looked at browser history as a part of their investigation in about two-thirds of cases.

Figure 2 – Most investigators examine five to ten devices per month, both for general investigations and for cases involving browser history.
The survey results of DFIR analysts also shows that almost 85 percent of subjects have multiple devices (including computers and mobiles). As a result, investigating record syncing between devices is increasingly important, as well as ensuring that investigators have access to all of a person’s devices. While investigative targets, such as in the Boston Bomber case, can easily clear their history from their computer, they may forget that their data may have been synced on one of their other devices, like their cell phone. And as people acquire more devices, security teams and law enforcement may become even busier during their investigations as they process more evidence.
So, how much time does the investigator need to actually review the web activities from each device? This survey question doesn’t include machine processing time; we wanted to measure the time investigators typically spend reviewing processed browser data.
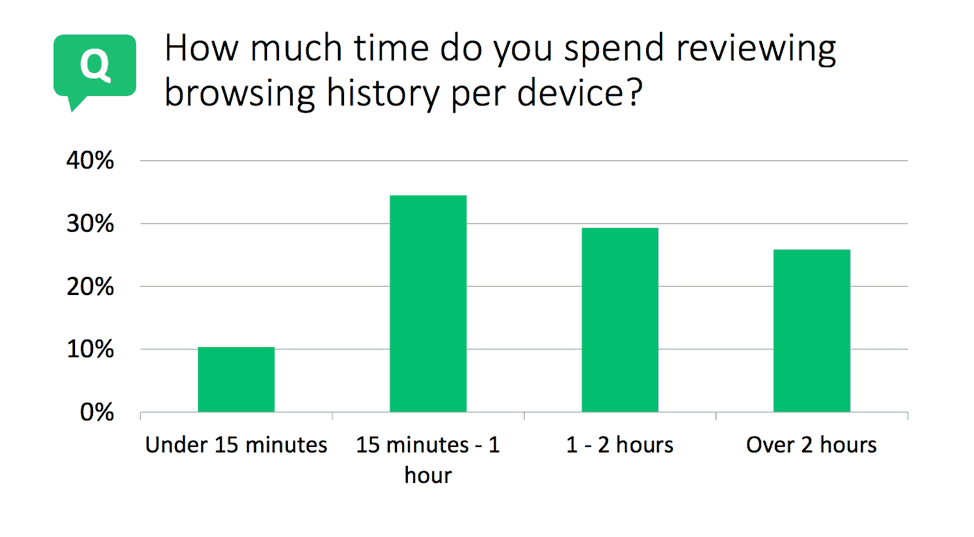
Figure 3 – Nearly 35% of investigators spend between 15 minutes to an hour reviewing the browser activity on each device.
The results showed that web investigations take a significant amount of time. Most investigations took over an hour, which can add up when you consider the number of devices that must be examined during an organizational breach or a criminal investigation. In addition, reviewing images can be a very long (and unnerving) process. This highlights the need for using tools and automation during an analysis. Automatically parsing actions from the web history into easy-to-read reports or including threat intel integrations to ease the use of indicators of compromise can speed up the process.
Synopsis: An Exabeam Tool Designed to Help with Browser Investigations
Exabeam’s open source tool called Synopsis is designed to aid investigators reviewing browser history files by providing a high-level summary of key information. Many questions are common across different types of investigations, and Synopsis helps analysts get the answers they need quickly. With the Synopsis dashboard, analysts can view an overview of data from the device in question, spot trends and outliers, and extract information such as:
- Search engine queries
- Accounts on websites
- Autofill data (information typed into web forms)
- Historical geolocation
- Activity per domain
- Activity trends based on the time and day of the week
You can see Synopsis in action in this BBC Click piece on GDPR.

Figure 4 – Synopsis extracts information from browser history files and displays it as cards in a dashboard.
Resources to Aid in Your Browser Investigations
The Exabeam survey shows us that DFIR professionals spend a significant amount of time on their web browser investigations, suggesting that making browser investigations quicker and more efficient is very needed—Synopsis is designed to help.
You can click here to download Synopsis on GitHub.
How to Investigate Insider Threats Using Web Browser Forensics
Blog: How Criminals Can Build a “Web Dossier” from Your Browser
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!










