How reliant is your business on credentials to keep your network safe? Are you like the 29% of organizations, according to a Thales Report study, who still view passwords as one of the more effective security tools? If so, this is your wake-up call — and hopefully, it will be far less painful than the one Fortinet recently received.
Just this past week, Fortinet learned a hacker posted a list of one-line exploits to steal VPN credentials from close to 50,000 Fortinet VPN devices. The list of vulnerable targets included over four dozen prominent global banks and government agencies.
What does the Fortinet debacle teach us? Credentials aren’t an effective line of defense today. Your employees can impress each other with their creative passwords, but breaches happen, credentials are stolen, and then the real problems begin. Once inside via a legitimate credential, it becomes tough to identify an impersonator looking to wreak havoc in your network
This article will discuss why credentialing doesn’t work, what does, and who you can partner with for the solution. Are you ready? Let’s get started.
Why credentials don’t work
Credentials mean very little from a security standpoint today. If you’re not disturbed by the ease with which the nearly 50,000 Fortinet VPN devices were compromised and credentials exposed, you may want to think again. In this case, the exploitable bug was discovered in 2018 — just hanging around unpatched as an easy target for threat actors. How many more of these vulnerabilities are out there waiting to be exploited?
We humans are creatures of habit and convenience. These traits have served us well throughout our evolution — but not so much when it comes to passwords. Most people favor simpler, shorter passwords and, worse yet, habitually reuse them. A 2019 Google survey discovered 52% of respondents use the same password for multiple accounts, and 13% use the same password for all accounts. The fact is people reuse passwords, well, because we are people.
Credentials often rely on encryption, which provides some resistance to attackers but is by no means bulletproof. Chances are, given enough time, this defense can be cracked. In most cases encryption can be broken — it just comes down to a matter of time.
Maybe most dangerous of all is the level of trust in passwords considering what hangs in the balance — only the access to entire devices, systems and networks. Stealing one password can provide a front door key, allowing invaders undetected access to your entire organization.
What works instead of credentials
It’s understood relying on credentials isn’t an effective strategy to safeguard devices, systems, and networks today. So, what is? Glad you asked — as some better options do exist.
Multi-factor authentication (MFA)
MFA, the practice of employing multiple means of authentication, is gaining traction and popularity. Currently, only 11% of Microsoft’s own enterprise accounts have MFA, but that number seems poised to grow. MFA uses easy, lightweight options (codes, tokens, biometrics) to challenge users rather than automatically locking them out and unnecessarily hindering productivity. MFA isn’t perfect as it usually involves a password, but having multiple non-password barriers makes unauthorized access more difficult.
Password managers
As we’ve discussed, humans aren’t great password managers. Today, many executives enjoy using one credential to access a password manager tool that creates and manages many complex passwords for them. With many already suffering from password fatigue, employing a password manager is proving to be a convenient option for reducing overload while improving security.
Know the normal
A stolen password works just as effectively for an attacker as it does for an employee. So, how can your organization know who is behind an accessing credential? It starts by understanding the normal behavior patterns of your employees. Massive amounts of event data must be examined and analyzed to establish a standard baseline for time, location and nature of the action. With a normalcy profile in hand, your organization can now engage computer analytics to help identify abnormal patterns.
As stolen credentials have become an unfortunate inevitability today, the importance of identifying abnormal activity is growing. Teams that can rapidly pinpoint malicious invasions have a leg up in the race for a solution. As defenders, we can learn what normal behavior in our environment looks like. With a little extra investment in analytics, we can expand our knowledge of normal exponentially. This knowledge denies attackers the opportunity to operate without being seen and increases the chance that defenders stop an attack before it causes serious loss.
Knowing the normal requires fast processing and analysis of vast amounts of information — far more than can be handled manually. Regrettably, most organizations don’t have the staffing or tools required to implement this effective strategy.
Detecting compromised credentials with Exabeam
Fortunately, there is a solution that makes the speedy identification of abnormalities possible for any security team. Exabeam Advanced Analytics, part of the Exabeam Security Management Platform, performs user and entity behavior analytics (UEBA) for threat detection. It thoroughly examines each login for specifics and sets filters for abnormalities in dozens of categories such as VPN session start time, VPN country access, and amount of data transferred. This advanced security resource quickly and automatically baselines normal user behavior, tracks normal and abnormal behavior, and detects access-based threats while assigning dynamic risk scores.
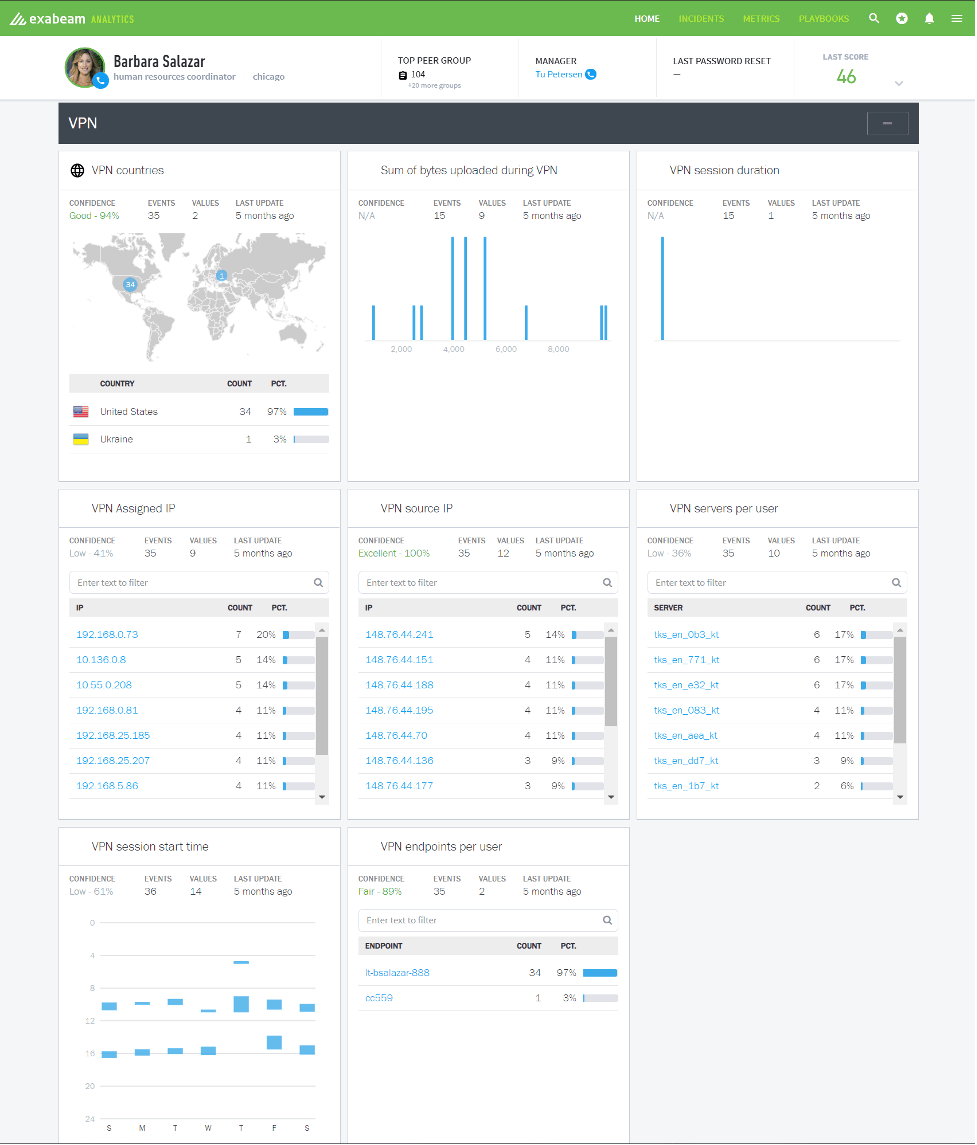
Figure 1: In this scenario, eight models track VPN usage for one user. These same eight perspectives of normal behavior are tracked for every user in the organization.
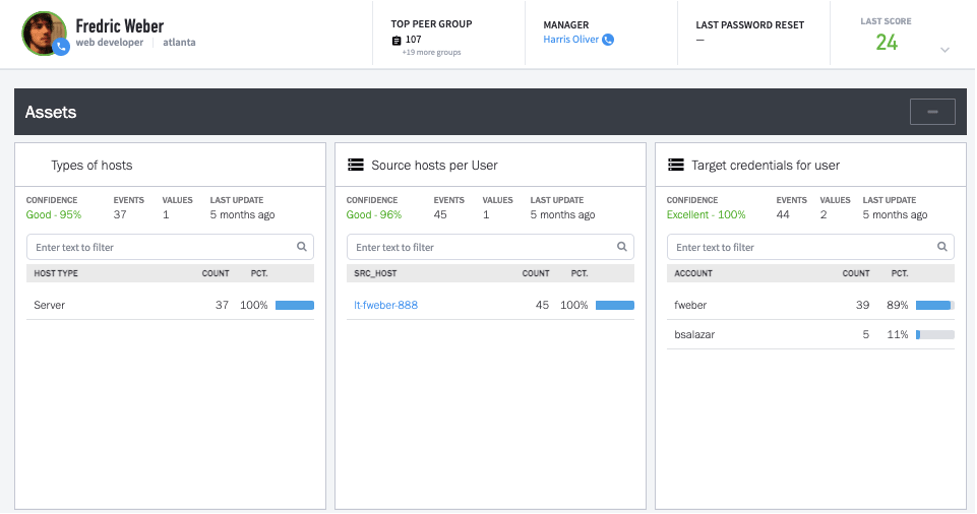
Figure 2: Here are three perspectives on computer usage for one user. Notice that Freddie has used another user’s login indicating that he knows another user’s password.
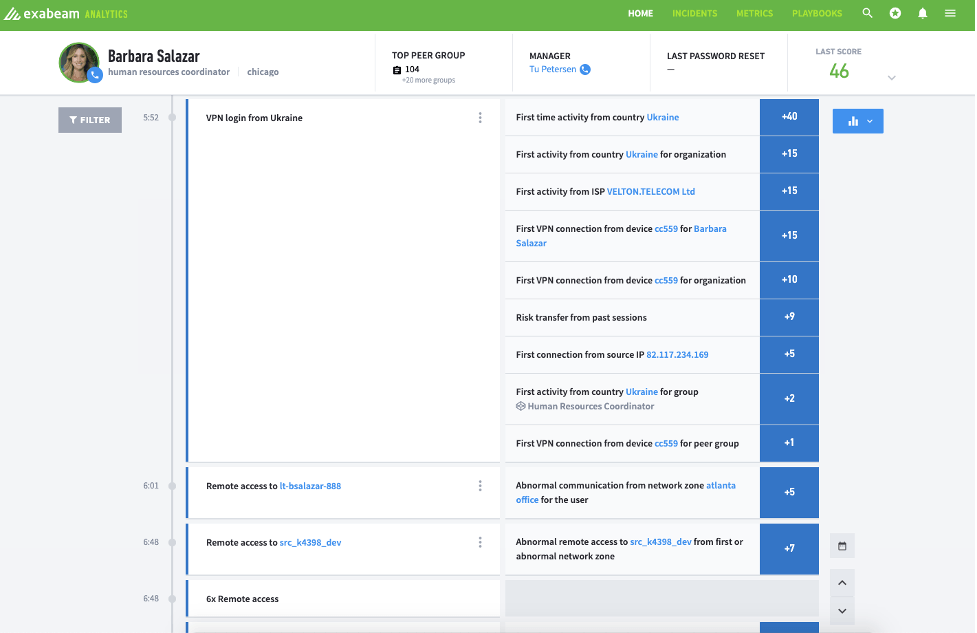
Figure 3: This view shows one user’s activity starting with an extremely risky VPN session from another country, using a device that had never connected to the corporate VPN before.
With Advanced Analytics you can get an in-depth and complete view of anomalous user behavior that will help you focus your investigation on the most critical security event.
As the Fortinet example teaches us, it’s a recipe for disaster to rely heavily on credentials to keep your devices, systems and networks safe today. When credentials become compromised, Advanced Analytics is your go-to solution for quick identification of the abnormal behavior frequently exhibited by unauthorized users. Without this critical knowledge, rooting out the imposters and securing your enterprise can become a guessing game — one that’s too important for your team to lose.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












