Recently PetitPotam, a new POC tool created by researcher Gilles Lionel (@topotam77), was published on GitHub.
PetitPotam forces Windows hosts to authenticate to other machines. With this tool, an attacker can trigger NTLM authentication from the domain controller against a listener computer and then launch an NTLM relay attack.
This technique is mainly used to seize control of the entire domain by chaining it to an exploit targeting Windows Active Directory Certificate Services (AD CS). In addition, this technique may be used for other attacks like NTLMv1 downgrade and relaying machine accounts on computers where this machine account is a local admin (SCCM, exchange server, are often in this situation for example).
The technique primarily takes advantage of the MS-EFSRPC EfsRpcOpenFileRaw function.
What is an MS-EFSRPC EfsRpcOpenFileRaw function?
MS-EFSRPC is a Remote Procedure Call (RPC) interface that is used to perform maintenance and management operations on encrypted data that is stored remotely and accessed over a network. It is used in Windows to manage files that reside on remote file servers and are encrypted using the Encrypting File System (EFS). EFS allows the NTFS file system to encrypt files on disk in a manner that is transparent to the user.
The EfsRpcOpenFileRaw method is used to open an encrypted object on the server for backup or restore.
Using this function forces the targeted computer to initiate an authentication procedure and share its authentication details via NTLM
Who is vulnerable to it?
PetitPotam can affect Windows Server 2008 to 2019. Most of the time this technique is used to relay SMB authentication to an HTTP certificate enrollment server allowing full take over of the domain controller.
Most vulnerable teams are the ones who are using the Active Directory Certificate Services (AD CS) with any of the following services:
- Certificate Authority Web Enrollment
- Certificate Enrollment Web Service
Mitigation
The only way to mitigate this technique is to disable NTLM authentication or enable protections, such as SMB signing, LDAP signing, and channel binding.
The NTLM relay attack according to Microsoft can be mitigated in the same way as other NTLM relay attacks.
Microsoft’s suggestions for mitigations include:
- Enabling EPA and disabling HTTP on AD CS servers.
- Disabling NTLM authentication where possible. The following mitigations are listed in order from more secure to less secure:
- Disable NTLM authentication on your Windows domain controller.
- Disable NTLM on any AD CS Servers in your domain using the group policy Network security: Restrict NTLM: Incoming NTLM traffic.
- Disable NTLM for Internet Information Services (IIS) on AD CS Servers in your domain running the “Certificate Authority Web Enrollment” or “Certificate Enrollment Web Service” services.
PetitPotam detection by Exabeam
Detection case 1
If there is an abnormal source IP that checks if it has the access right to write and read data from one of the named pipes lsarpc/efsrpc/lsass/samr/netlogon in the IPC$ share, apply the following:
- Event Code – 5145
- ShareName – \\*\IPC$
- AccessMask – 0x3
- RelativeTargetName – “lsarpc” OR “efsrpc” or “lsass” OR “samr” or “netlogon”
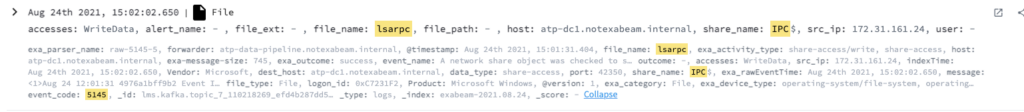
Detection case 2
The first time an source IP checks if it has the access right to write and read data from one of the named pipes lsarpc/efsrpc/lsass/samr/netlogon in the IPC$ share, apply the following:
- Event Code – 5145
- ShareName – \\*\IPC$
- AccessMask – 0x3
- RelativeTargetName – “lsarpc” OR “efsrpc” or “lsass” OR “samr” or “netlogon”
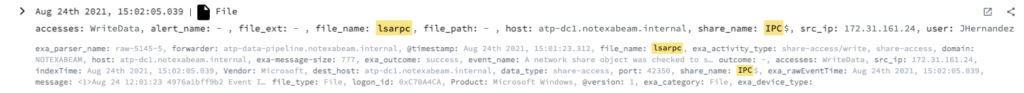
Detection case 3
When an anonymous user checks if they have the access rights to write and read data from one of the named pipes lsarpc/efsrpc/lsass/samr/netlogon in the IPC$ share, apply the following:
- Event Code – 5145
- ShareName – \\*\IPC$
- User – Anonymous Logon
- AccessMask – 0x3
- RelativeTargetName – “lsarpc” OR “efsrpc” or “lsass” OR “samr” or “netlogon”
Conclusion
PetitPotam is a technique that could have a dramatic impact on a company’s operations if it is used by the attackers. We recommend monitoring for attempts to access pipes named lsarpc/efsrpc/lsass/samr/netlogon. By using this technique with an exploit targeting Windows AD CS, an adversary could seize control of the entire domain. Organizations can thwart attacks through early detection by monitoring for unusual access.
References
- https://github.com/topotam/PetitPotam
- https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-efsr/08796ba8-01c8-4872-9221-1000ec2eff31
- https://www.bleepingcomputer.com/news/microsoft/windows-petitpotam-attacks-can-be-blocked-using-new-method/
Exabeam Security Research Team (ESRT) Mission Statement:
The ESRT strives to provide unique insight into how we look at the world of cyberthreats and risk by highlighting the common patterns that different threats and threat actors use, and why we need to reorient our detections and priorities to tactics, techniques, and procedures (TTPs) vs. indicators of compromise (IOCs).
We aim to share a newer ideology of investigating threats by answering the following questions: “who, what, and how”.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












