We’ve talked about the rise of the XDR market and why that came to be in our first post of the Exabeam XDR blog series. In this post, we’ll discuss why a use case-based approach is key to an effective XDR platform. This approach is meant to be prescriptive and step-by-step, focused on successful outcomes that can be repeated at scale, by any organization.
A legacy approach to SOC maturity
SOCs were historically tasked with assembling a toolset and supporting processes that can help them detect, investigate, and respond to those threats. To do this, most SOCs adhere to a process that looks like the following chart in Figure 1.
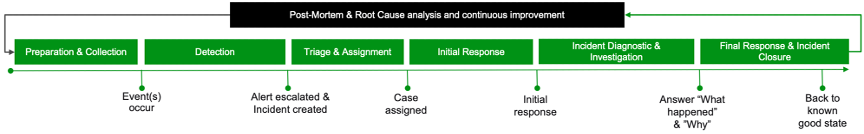
When SOCs look to mature their capabilities, they typically look to do so via automation, in a “left-to-right” fashion. It starts with trying to bring in all possible data to their SIEM “just in case” so they don’t miss anything that might be security relevant. With (hopefully the right set but usually too much) data in place, attention is turned to automating detection for as many security threats as possible. With the detection mechanisms in place, alerts begin to pile up — both from security products and from the SIEM itself. To handle this glut of alerts, tier-1 triage workflows are automated. This process of left-to-right automation progresses until it ultimately reaches response and case closure.
This legacy model of optimizing a SOC tries to automate each phase in the workflow one at a time, but for all threat types at the same time. Unfortunately, not all threats are the same. They have different relevance, different priorities, require different data, have different detection methods, different investigation needs, and resolution requires different people, processes, and tools. Not only does a left-to-right approach require a huge amount of heavy lifting and customization, but it’s simply not an efficient way to mature a SOC.
Maturing “top-to-bottom” with threat-centric use cases
Instead of trying to automate all threats at one stage of the SOC workflow, then moving left-to-right, a more efficient path to SOC maturity is to automate the collection and detection through the resolution of a single threat type before moving on to the next. Start with simple yet prevalent use cases and as you automate them, move on to more complicated threats. Conceptually this maturity path is closer to working “top-to-bottom”, as illustrated in Figure 2 below.
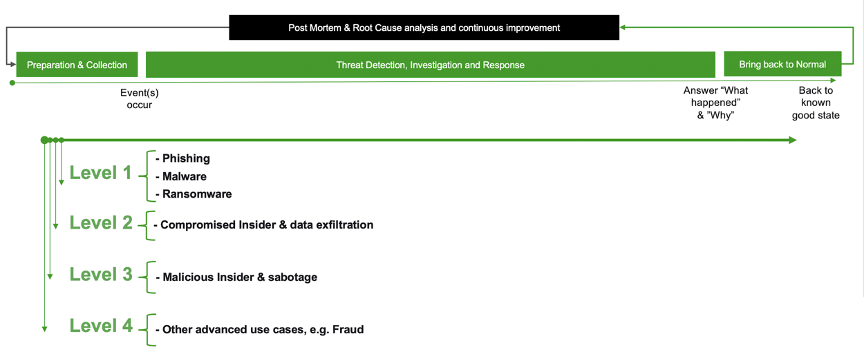
In order to easily facilitate the automation of threat detection, investigation, and response (TDIR) processes, vendors need to offer prescriptive guidance and workflows for handling specific threats and tailor their products to deliver successful outcomes for specific threat types. Figure 3 below shows some of the ways vendors can tailor their products with features, processes, and content to focus on threat-centric use cases across the entire TDIR lifecycle.
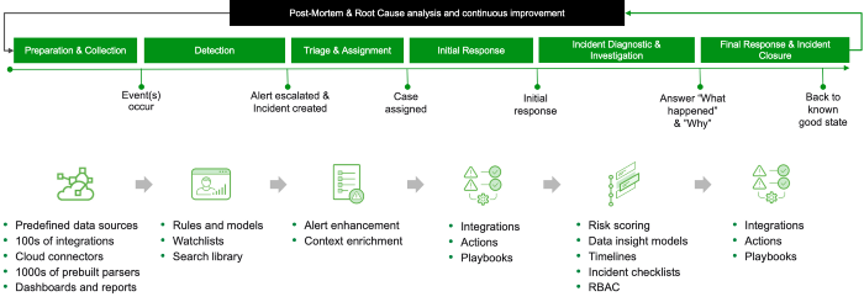
Additionally, customers should not be forced to build functional detection, triage, investigation and response content using the “bag of legos” vendors provide them. Instead, vendors should provide prepackaged content at each step of the TDIR process which is directly related to a specific use case. As shown in figure 1, each use case is limited in scope to the specific data sources, detection types, investigation steps, response actions that address a specific threat, in this example, lateral movement. The use case content includes everything you need to solve a particular type of threat for repeatable, successful outcomes every time and at scale.
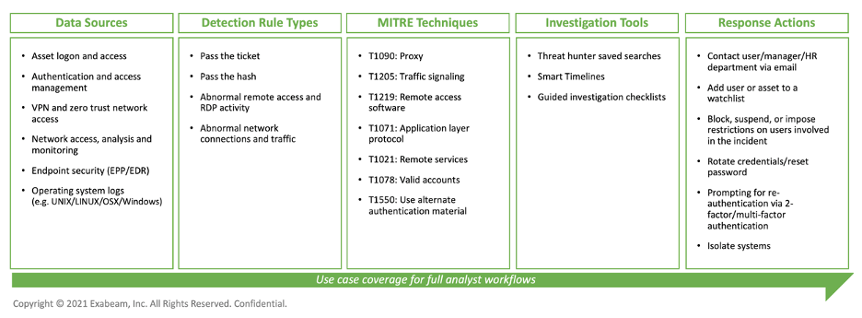
Effective XDRs must include prescriptive, threat-centric workflows
XDRs should be able to offer a closed-loop solution that encompasses the entire security operations workflows of threats. XDRs are supposed to be turnkey solutions with immediate time to value and minimum/no configuration, regardless of the expertise level of the SOC — so instead of tuning, SOCs should be able to use XDRs to address immediate concerns from start to finish. By this, we mean focusing on one use case and expanding from thereafter each one is addressed. Without this capability, XDRs will not be able to fulfill their value prop: turn-key TDIR that works immediately, without customization.
Want to learn more? To find out more about the state of the XDR market, read our earlier post.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












