Although there’s so much at stake with this year’s U.S. presidential election, security weaknesses throughout the election process, including the voting system still exist exposing the election to cyber threats. This infographic shows the key areas of vulnerabilities in the election process and where disruptions can occur.
Campaigns: an easy target
Cash-strapped campaigns are soft targets as they may lack the funds to staff a full-time cybersecurity team to protect campaign systems. Campaign teams are staffed by large groups of volunteers, many of whom use their own devices that may already be infected with malware or be targeted for social engineering attacks. Additionally, the fast pace and demands placed on campaigns, means there’s little time for proper onboarding and training on security protocols for the volunteers.
Nation-states pose an additional and perhaps greater threat to campaigns. In 2008, Chinese threat actors successfully infiltrated both the Obama and McCain campaigns stealing large quantities of information. The group then subsequently attacked the Romney campaign in 2012. In 2016, Russian threat actors stole and leaked tens of thousands of emails and documents from the Democratic National Committee (DNC). These sophisticated state actors often choose rudimentary methods of attacks. This was the case when John Podesta, the chairman of Hillary Clinton’s campaign, fell for a phishing email urging him to reset his password. Upon doing so, the Russians were able to access all of Podesta’s emails, including sensitive campaign information. Russians also used malware to steal the credentials of other DNC staffers and in some cases, were successful at escalating privileges to gain access to critical DNC servers.

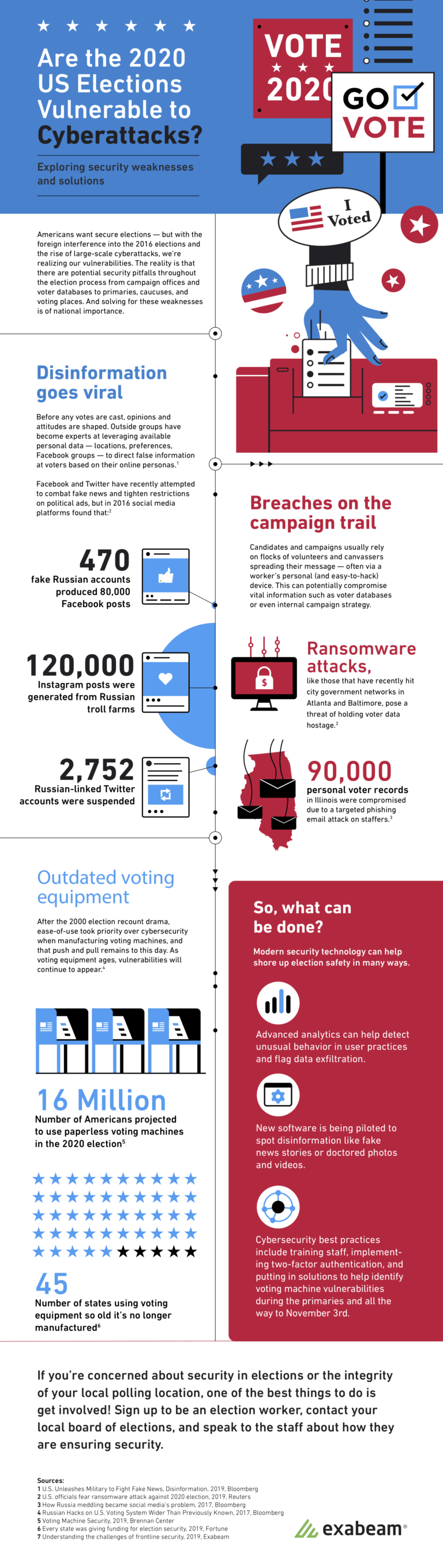
Fake accounts created with stolen credentials accounted for 80,000 Facebook posts in the 2016 election.
Disinformation: fake news proliferates
Attacks against campaigns can result in disinformation. A recent NPR poll found that 57 percent of those surveyed believe that disinformation is difficult to recognize. Cyber attacks can also have an impact on campaign funding through the creation of false donor sites or in the case of Phil Bredesen’s senate campaign, threat actors breached a consultant’s email and tricked the campaign into paying them false invoices for media buys.
Voting machines: multiple threat vectors
Voting machines are an essential component of the election, however, they also provide the vehicle for threat actors to potentially disrupt the 2020 presidential election. Currently, 45 states are using machines that are so old, they’re no longer being manufactured and more importantly, these machines are running older versions of Windows with known vulnerabilities. Additionally, some of these machines include a modem that allows elections officials to get preliminary results, exposing the systems to internet threats.
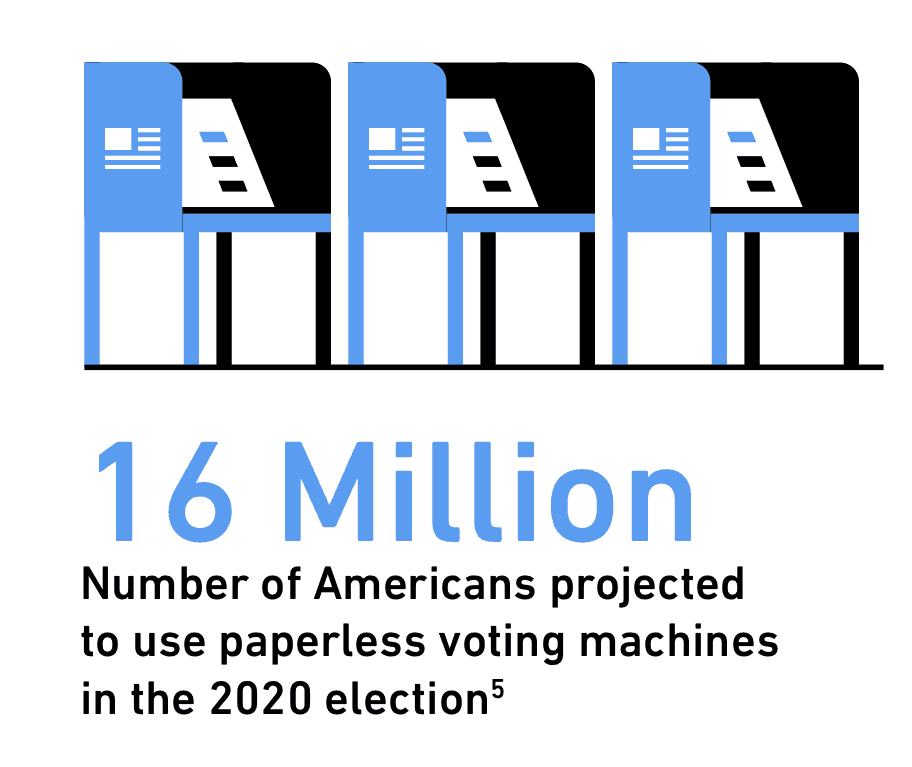
An estimated 16 million voters will use paperless voting machines in the 2020 US election.
Voter data: highly prized by threat actors
While some threat actors are motivated by disrupting campaigns for political or national reasons, a significant number are motivated by money. Whether by exploiting vulnerable machines or unsuspecting campaign volunteers, the goal of some actors is to gain access to voter information. Ransomware attacks give adversaries a method to extract payment for voter information. And in a recent shift in ransomware goals, threat actors can also sell user data (voter information) including driver licenses on the dark web.
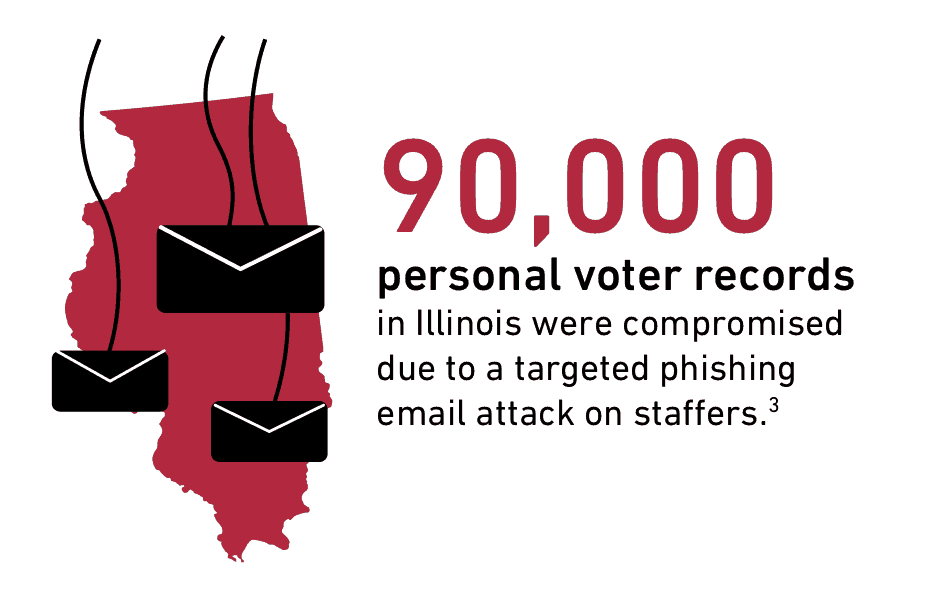
Phishing attacks target campaign staffers’ emails to gain access to voter records.
Preventive measures
Steps are being taken on several fronts to address election cybersecurity threats. The Belfer Center for Science and International Affairs at Harvard Kennedy School has published a cybersecurity campaign playbook for campaigns of any political affiliation with actionable information to protect campaign information. The playbook provides useful information such as security best practices for campaign volunteers.
New software and tools are now available to help voters and campaigns spot disinformation. For example, BotSlayer is an open-source software tool that lets anyone identify and stop fake twitter accounts promoted disinformation.
While Congressional funds are available for states to use to replace outdated, vulnerable machines these funds are not enough to cover the vast number of machines that need to be replaced. As a result, some organizations are developing open-source voting machines, including VotingWorks to provide election officials more secure machines at a lower price.
Measures are also being taken to protect the voter registration database and systems from ransomware. The Cybersecurity Infrastructure Security Agency (CISA), in particular, is developing educational material as well as looking to provide penetration testing and vulnerability scans that will be available to state and county governments.
Behavioral analytics technology can also help thwart cyberattacks. For example, by establishing an early baseline of campaign user activity, devices, and networks with user and entity behavior analytics solutions, cybersecurity teams can detect anomalies in campaign staffers’ practices. These anomalies can indicate data exfiltration that may be taking place as a result of a compromised staffer account or exploited vulnerability.
You, too, can be part of the solution by helping other voters become aware of the threats and solutions to protect our election process shown in our infographic below. Look out for the next post in our series covering vulnerabilities in the election process.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!