Government
Change the game with improved visibility, rapid insights and easier response.
Trusted by organizations
around the world





















Easily achieve all OMB-21-31 levels
Exabeam helps agencies or departments achieve maturity OMB-21-31 Level EL3 (Event Logging Tier 3). We present comprehensive, detailed guidance for logging, orchestration, automation, response, user behavior monitoring, access, and incident visibility. Deploying a behavior analysis solution should be an ongoing practice, with departments and agencies continuously monitoring activity and adjusting normal behavior baselines as needed.
Through our distribution partner Carahsoft and network of authorized resellers, Exabeam is available on GSA (47QSWA18D008F), CDM, and SEWP (NNG15SC03B/NNG15SC27B) contracts.
Too many threats, too little time
Critical infrastructure, state, local and federal agencies are under constant attack. Whether it’s nation state sponsored, for-profit, or insider threats, securing these vital environments demands innovative tools that enable smarter detection, faster investigations and easier response.
Read more on the Exabeam Blog:
Control cybersecurity risk
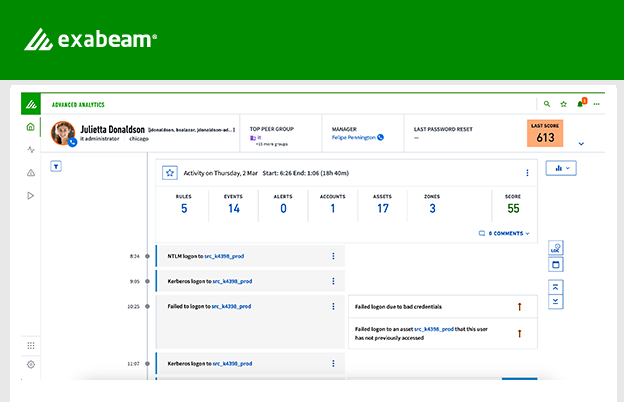
Exabeam accurately detects high-risk, anomalous activity on a network, in SWIFT transactions, and across cloud instances.
By analyzing user behavior, security teams are directed in real-time to instances of a potentially malicious employee activity, or indicators of compromise where an attacker using stolen credentials is already within your network.
Deliver a better customer experience to drive retention
Complete visibility of threats is needed to ensure systems and applications remain online for teams and customers. Exabeam integrates with 500+ products so detection models, alerts, and searches are performed against a dataset that reflects an organization’s complete environment to protect the organization as it continues to modernize its networks.
Addressing the skills shortage
To address the cybersecurity skills shortage, technology must do more for security teams. Through natural language querying, context enhanced parsing, and data presentation, Exabeam improves analyst investigation efficiency and effectiveness. Automation—from collection to response—cuts the time spent on security tasks by 51%.
behavioral models
To baseline normal user behavior and detect anomalous behavior.
pre-built parsers
As it is ingested, data is parsed using over 9,500 pre-built log parsers and enriched using context sources from open source and commercial threat intelligence feeds.
events per second
Rapid log ingestion processing at a sustained rate of over 2M EPS.
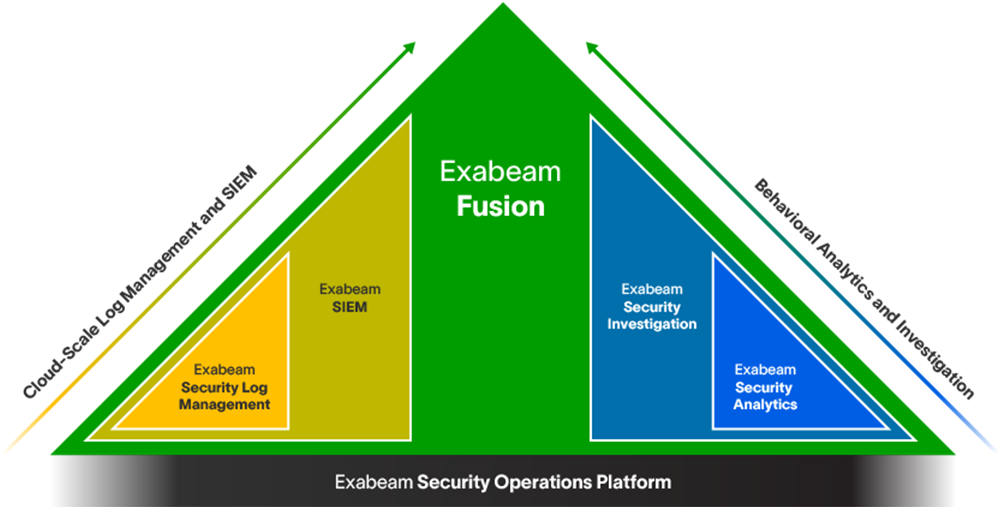
Explore the many ways Exabeam can work for you
Whether you replace a legacy SIEM, or complement an ineffective SIEM solution by adding UEBA, automation, and TDIR content on top, the modular Exabeam Security Operations Platform can help you achieve security operations success.
- Get started: Exabeam Security Log Management
- SIEM replacement: Exabeam SIEM and Exabeam Fusion
- SIEM augmentation: Exabeam Security Analytics and Exabeam Security Investigation
Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision