Most security organizations today face the same set of problems—too many alerts, not enough trained analysts, and actual threats likely going unnoticed. There is no doubt that modern security operation centers (SOCs) are experiencing an ever-increasing amount of noise potentially masking an ever-increasing number of threats from multiple vectors. Increasingly, many organizations are trying to solve these problems through automation. These organizations know that they need automation due to the fact they can’t find and hire the right talent fast enough to keep up with demand, nor would throwing a large number of staff at innumerable repetitive tasks fix the problem. When most organizations look for automation solutions, they immediately turn to a security orchestration and automated response (SOAR) solution, which uses application programming interfaces (APIs) to automate response and remediation through playbooks. Implementing a SOAR solution is a huge undertaking that requires strategic planning and time to execute. The good news is there are other ways to quickly reap the benefits of automation before embarking on a total SOAR solution.
Are you ready for SOAR?
Another question to ask is do you need it now? Likely “yes” but a significant amount of planning is required for a correct implementation. Here are a few thoughts you might want to consider before going from zero to SOAR in one big step:
- Don’t try to automate your current alert overload. Let’s say you already have a security information management (SIM) solution in place, and your staff is currently ignoring the tens of thousands of alerts it is generating every day. If you are already ignoring those alerts, why include them in your automation? You may need to consider why you feel that letting machines operate on “garbage” alerts will create a better yield, something better than a “garbage” response.
- Don’t try to automate playbooks you don’t have. Many organizations don’t have manual playbooks. It’s not always practical to start automating playbooks when you don’t yet know how you want to standardize incident response and remediation.
- Focus on small, visible wins. Automation costs money. You need to show your team and your managers that you are succeeding in your automation efforts. Don’t attempt to go from zero to total automation in one step. Rather than try to build a huge playbook with lots of complex actions to provide a total, end-to-end solution, consider starting with a playbook with just one or two actions. Go for quick and visible wins and build on your successes.
- Don’t settle for endpoint-only remediation. Often, playbooks are designed to focus remediation on the endpoint. For example, a playbook may remediate a malware discovery by simply deleting the malware. But what else did that malware do? Where did it originate? Is it still active elsewhere in the network? If your playbook just deletes the evidence, then you have drastically reduced your chance of discovering other potential victims.
If a full-blown SOAR solution is not the best way to implement security automation, how can you start to automate your operation? The rest of this article focuses on the automation that Exabeam provides that can help you get started on automating repetitive tasks.
Don’t start automation without seeing the full picture
Threat detection is based on analyzing log events. Think of each log event as a piece of a jigsaw puzzle. You need to be able to put the pieces (events) together correctly in order to see the picture they make (Figure1).
Figure 1: Where to begin?
Grouping events in a data lake or SIEM
Most organizations use a security log event data lake or SIEM solution. These solutions typically can group together various events, for example, one group of firewall events, one group of Active Directory events, one group of alert events (Figure 2).
Figure 2: Log events are grouped much like the pieces of a jigsaw puzzle.
This grouping is a first step, and a reasonable question is, “What is the next logical step in my quest to automate my operation?”
Logs don’t provide a complete picture
In most cases, logs don’t contain all of the data needed to detect and reconstruct an attack, especially in cases involving lateral movement. So analysts must swivel from log to log, attempting to recreate the data; otherwise, they risk missing critical parts of an attack. For example, Figure 3 shows information available across six different logs, none of which contain all of the needed information: user name, IP address, and device name.
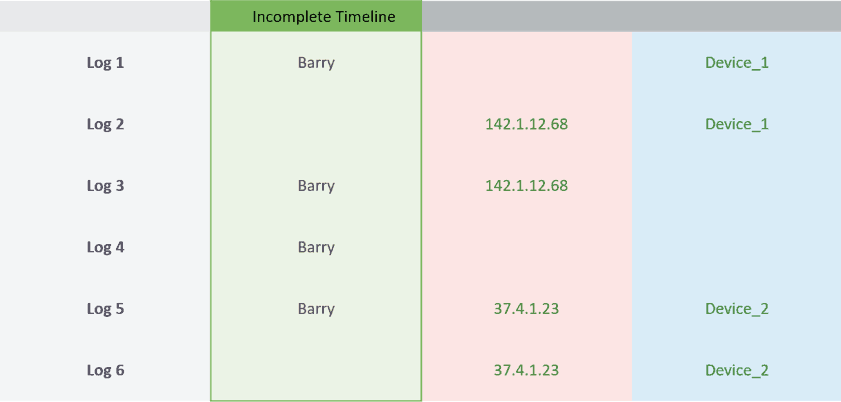
Figure 3. Missing critical data, incomplete log entries frustrate attempts to piece together an attack.
Level 1 automation: Smart Timelines
Exabeam’s exclusive Smart Timelines use automated host-to-IP-to-user mapping to stitch together log data in real-time. The result is a complete picture that encompasses your entire network taken from millions of log entries across thousands of users and machines with constantly-changing IP addresses. The result from this level of automation is similar to getting the frame of our hypothetical jigsaw puzzle worked out (Figure 4).
Figure 4: Level 1 automation in Smart Timelines provides a solid framework for detecting threats.
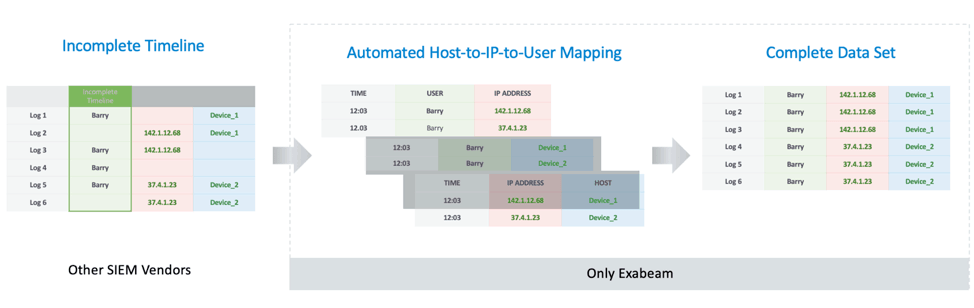
Figure 5: Logs don’t contain the data needed to recreate an attack resulting in incomplete timelines. With Exabeam’s automated host-to-IP-to-user mapping, Smart Timelines stitches together log data in real time to fill in the gaps.
Level 2 automation: Context enrichment
Exabeam brings behavioral analytics and machine learning into the picture to provide the next level of automation. By examining relationships of assets and patterns of usage, Advanced Analytics fills in more pieces of the puzzle.
Behavioral analytics adds context related to:
- Identity
- Peer groups
- Asset and user relationships
- Threat intelligence
Machine learning creates new context, including:
- Asset types
- Asset ownership
- Account types
- Peer groups
- Domain Generation Algorithm (DGA) detection
- Account associations
- Daily activity patterns and changes
Granular information such as the following for each category can enrich context and help create a full picture for incident investigation and threat hunting:
- Asset types
- Workstation versus server
- Static versus dynamic IP
- Prefix suffix
- Subnet
- Logged in users
- Account Types
- User versus service
- Domain generation algorithm detection
- Account associations
- Daily activity change
Level 3 automation: answering the expensive questions
Context enrichment answers the expensive questions that humans cannot discover from examining raw events. For example, it’s important to understand who owns an asset in an organization and not have to rely on a static configuration management database. Knowing which asset belongs your CEO can drive better decision-making during SOAR and running automated playbooks. Another situation would be to automate response if a user’s credentials have been compromised. In this situation knowing other credentials the user has used can help analysts determine if other users may also be compromised. The initial alert for malware that started the investigation will only report which user was infected and not all possible users the malware could have obtained. Questions to ask when investigating an incident include:
- Has this user ever logged in through VPN?
- Yes, Barbara has VPNed in before
- Has this user ever connected from this IP address or geolocation?
- No, Barbara has never VPNed in from this IP or Geo
- Has this user ever connected from (or to) this asset?
- No, Barbara has never VPNed in from this asset CC559 nor has anyone else in the organization
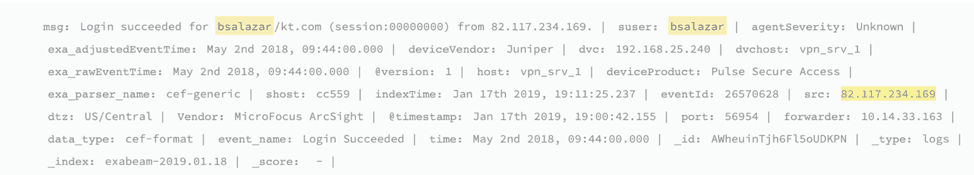
Figure 6: Raw events don’t tell the whole story. Has this user logged in via VPN? Has the user connected from this IP/Geo? Has this user connected from this asset before?
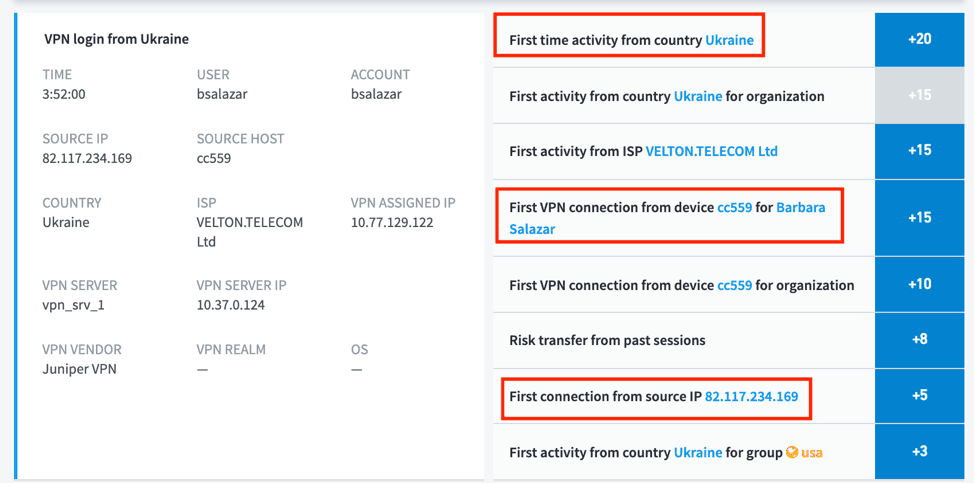
Figure 7: Advanced Analytics automatically answers the expensive questions.
Figure 8: Level 3 automation, context enrichment, fills in many missing puzzle pieces.
Level 4 automation: SOAR
With your logs consolidated and organized into a coherent resource, and with your log data enriched, analyzed, and scored, you can start to plan a full SOAR implementation. Rather than using your own technical resources to try to make sense out of a mass of unorganized log data, you can build on Exabeam’s solid foundation of underlying automation to further orchestrate and automate your threat responses.
For example, a malware playbook with analytics can:
- Show you where the malware came from, what it did, where it spread, and whose credentials were compromised.
- Remediate access to malicious domains
Figure 9 shows the three-hour timeline that led up to a successful malware attack, including the exact times, events, and resources involved. Much more detail can be revealed by clicking any of the light blue text to drill down to lower levels. And importantly, the events are described in language that can make even your entry-level analysts effective in mitigating threats.
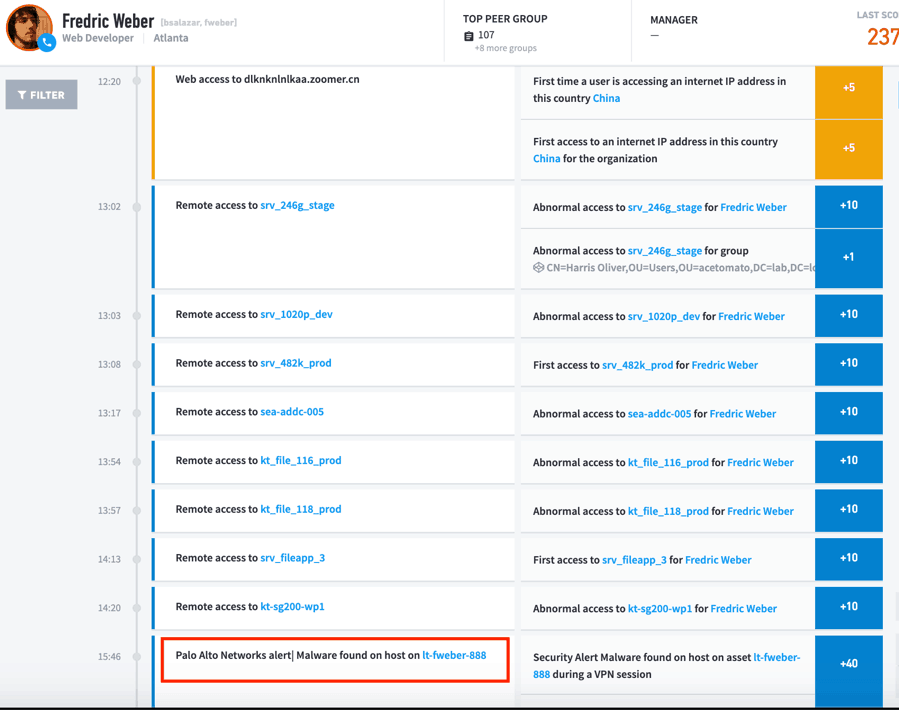
Figure 9: Example of a successful malware attack detected by a malware playbook.
Conclusion
When you are ready to head down the path toward automating your SOC, take a step back and examine what you are trying to accomplish. In many cases, trying to jump the gap from no automation to a complete SOAR solution in one step is overly ambitious. Instead, consider the advantages of starting small and building on your successes until you have a complete solution that meets your needs. Exabeam’s out-of-the-box capabilities provide several levels of automation without any technical involvement from your organization.
For information on how Exabeam can help you automate your operation, see:
- Smart Timelines: Nine Benefits for Detecting and Investigating Security Incidents
- SIEM Threat Detection – Rules or Models?
Exabeam Security Research Team (ESRT) Mission Statement:
The ESRT strives to provide unique insight into how we look at the world of cyberthreats and risk by highlighting the common patterns that different threats and threat actors use, and why we need to reorient our detections and priorities to tactics, techniques, and procedures (TTPs) vs. indicators of compromise (IOCs).
We aim to share a newer ideology of investigating threats by answering the following questions: “who, what, and how”.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












