To successfully conduct an investigation, it’s important to understand the context in which that incident took place. When we as security analysts start our investigation, we don’t look at a single alert or log and expect to understand the entire picture of what happened. Instead, we assess different indicators of compromise (IoCs) or the tactics, techniques, and procedures (TTPs) of an attack to determine the context in which that alert is firing. This gives us a true understanding of the alert or incident under investigation.
Once we understand the factors around the incident, we can make informed decisions to properly remediate and contain the incident within our environment. To put this in perspective, I’ll compare a phishing and a malware investigation and show you how understanding the context will give you accurate information to make decisions during the investigative process.
Analyzing user behavior to investigate a phishing attack
Let’s first go through a phishing investigation using Exabeam Smart Timelines. As you can see below, we received two Palo Alto Networks alerts at 14:27 and 16:44 for user Barbara Salazar (bsalazar). The first thing I notice about these two alerts is that the user goes out to what looks to be a malicious link and then downloads a piece of malware. This information makes sense but doesn’t answer the question, how did this user get the malicious link in the first place?
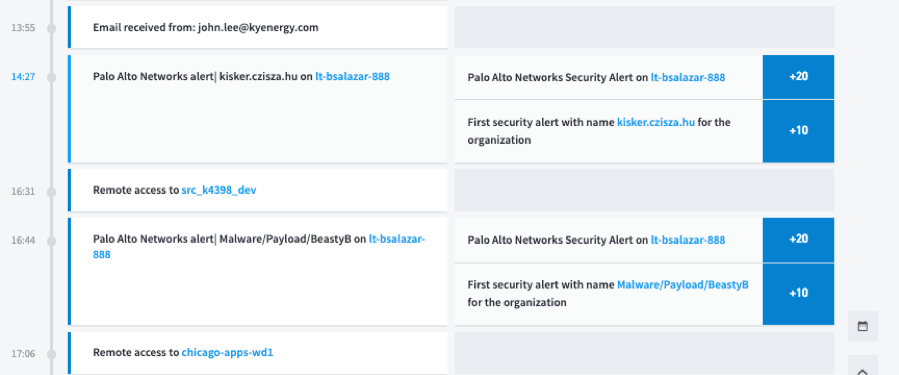
Figure 1: Exabeam Smart Timelines shows two alerts when a user clicks on a malicious link and downloads malware.
If we take a look at the event at 13:55 which precedes the Palo Alto Networks alert by approximately 30 minutes we see that bsalazar received a suspicious looking email. A few red flags stand out indicating this is a phishing email. First, the sender domain is kyenergy[.]com and the recipient are at ktenergy[.]com. Secondly, why is a user from a completely different domain sending a user within my environment payroll information? This shows the two Palo Alto Networks alerts may be a result of the user being subject to a phishing attack.
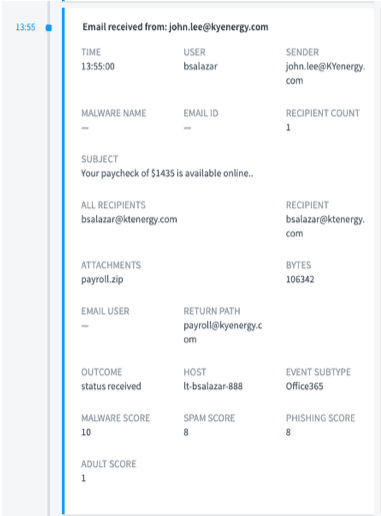
Figure 2: Investigating an event before the alert shows that user bsalazar received a phishing email.
The next step is to investigate the contents of this email with malware and email analysis tools to determine its validity. Using Exabeam’s playbooks, I submitted this email for analysis and received a report confirming my suspicions. Several screenshots of the automated analysis are shown below:

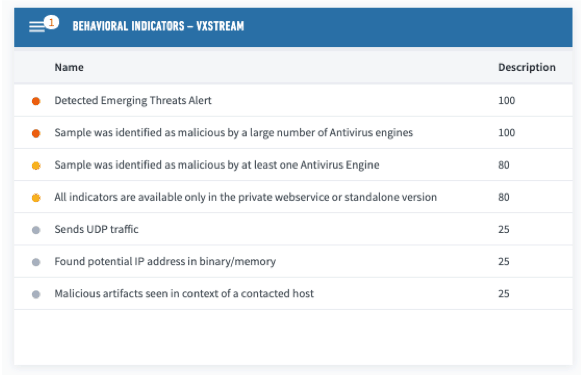
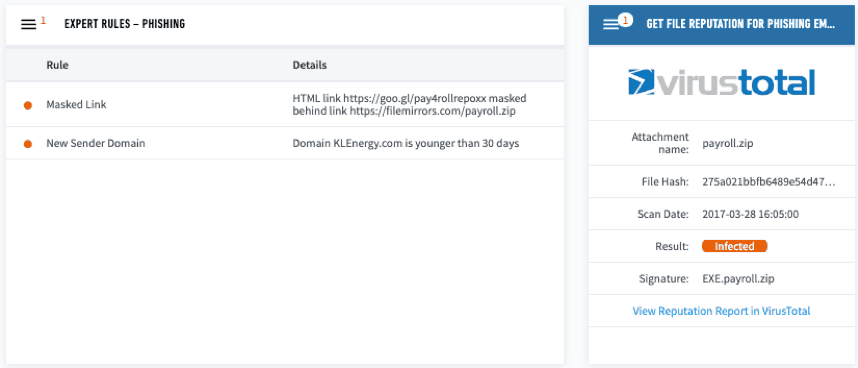
Figure 3: Running the contents of the suspicious email through automated malware and email analysis tools resulted in a number of detailed malicious indicators.
Using Exabeam Smart Timelines and playbook automation we were able to see the context behind the two Palo Alto Networks alerts and can determine that bsalazar’s user ID was infected by a phishing email which set off the alerts.
Understanding the context of the alerts allows us to take additional remedial actions like looking through the email logs and determining if anyone else in the organization received a similar email. If we just considered the Palo Alto Networks alerts by themselves, it would have been difficult to scope out this incident properly because we didn’t understand the attack vector that led to this investigation.
Analyzing entity activity to investigate a malware attack
Now let’s compare the phishing investigation to a malware investigation. They’re similar because both have malware associated with them, but the actions taken before and after the malware execution is different. This changes how we would investigate and remediate the situation.
In the report below we see that a Palo Alto Networks alert fired for the user Frederick Weber (fweber) on the system lt-fweber-888 at 17:46. In order to properly understand this alert, we need to determine the context in which this alert is firing to validate whether it is a true or false positive.
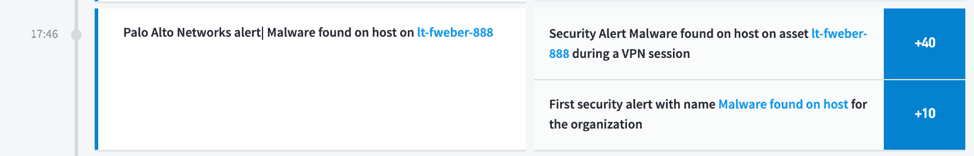
Figure 4: Without context it is difficult to determine if malware security alerts are true or false positives.
If we take a look at the user fweber’s Smart Timeline within Exabeam we see that this user went to the domain ‘dlknknlnlkaa[.]zoomer[.]cn’ at 14:20 which is associated with an IP address located in China. The URI string for the query against the zoomer domain is pulling the file barbarian.jar. At 14:21 this user runs the file barbarian.jar from the temp directory. All this activity happened approximately three hours before the Palo Alto Networks alert.
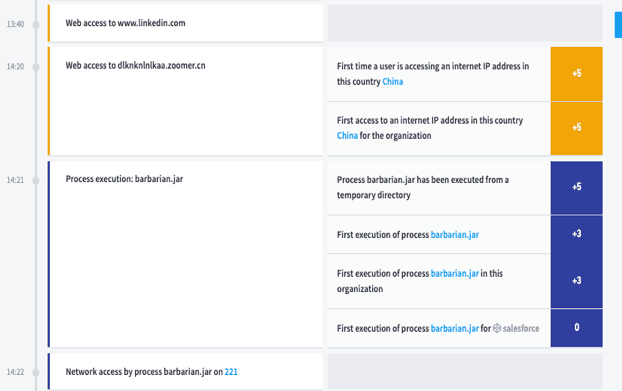

If we continue to investigate this user’s timeline, we see him remotely access eight different systems from 15:02 to 16:20. Exabeam analytics and data modeling shows that this user typically doesn’t access these systems, this is a strong indication that someone is moving laterally through the organization. Then at 17:46 we see the Palo Alto Networks alert from before.
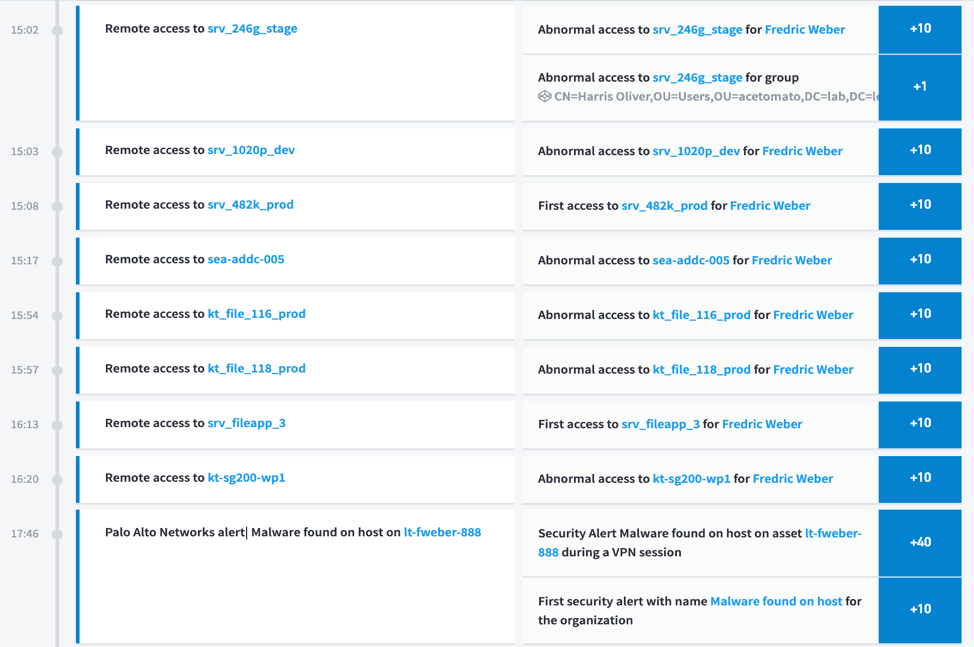
Figure 6: Details of unusual entity behavior is shown chronologically on the Exabeam Smart Timelines dashboard.
Putting all of this information together helps us understand when this user and his machine were initially compromised, what it did on his machine, and how this user’s account was used to move laterally throughout the environment.
Now that we have built a solid understanding of this alert in the context of this user’s timeline, we can start performing additional investigative tasks and plan proper remediation actions. The following are suggested action items and investigative tasks that we would perform based on our understanding of this alert through the investigation of the user fweber’s smart timeline:
- Investigate the entity timelines of all eight systems accessed by this user. (An entity timeline is based on entity behavior instead of a user.)
- Investigate the entity timeline of fweber’s system lt-fweber-888.
- Review proxy logs to see who else went out to the zoomer domain and if anyone else is accessing IP addresses located in China.
- Search through endpoint logs to determine if the file barbarian.jar is being used anywhere else.
Conclusion
By comparing these two investigations we can see that understanding the context around an alert often matters more than the alert itself. The context allows you to understand what is actually going on in your environment. In turn, this helps us as analysts to properly scope, investigate, and remediate an incident within our respective environments.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













