Exabeam’s research report details the latest insider threat, plus how to detect and combat it
Exabeam’s newly released research looks inside the hidden world of cryptocurrency mining by malicious insiders. Imagine a trusted and privileged insider, a system administrator for example, who has wide access to your network mining cryptocurrency. The activity is undetected and in addition to draining valuable resources increases the attack surface on your network.
The report also provides recommendations on what your organization can do to protect your business from such crypto mining.
A brief primer on crypto mining
There are two ways you can obtain cryptocurrencies: They can be purchased using actual fiat currency through a digital transaction on a cryptocurrency exchange. Or, they can be received as newly minted cryptocurrency coins awarded to miners per the blockchain software protocol.
In the latter case, miners are rewarded in cryptocurrency coins by validating transactions on a distributed blockchain ledger. Such validation is necessary to ensure a cryptocurrency transaction occurs only once, as well as to prevent attempts to change any transaction in the digital ledger (the blockchain).
Validation involves computing a cryptographic hash of all the transactions in a block (a collection of transactions), coupled with performing a computational task. Once verified, cryptocurrency transactions are extremely resilient to tampering, as manipulating any transaction affects the entire block. And altering any block affects the entire blockchain. This makes a transaction a permanent part of the distributed blockchain ledger.
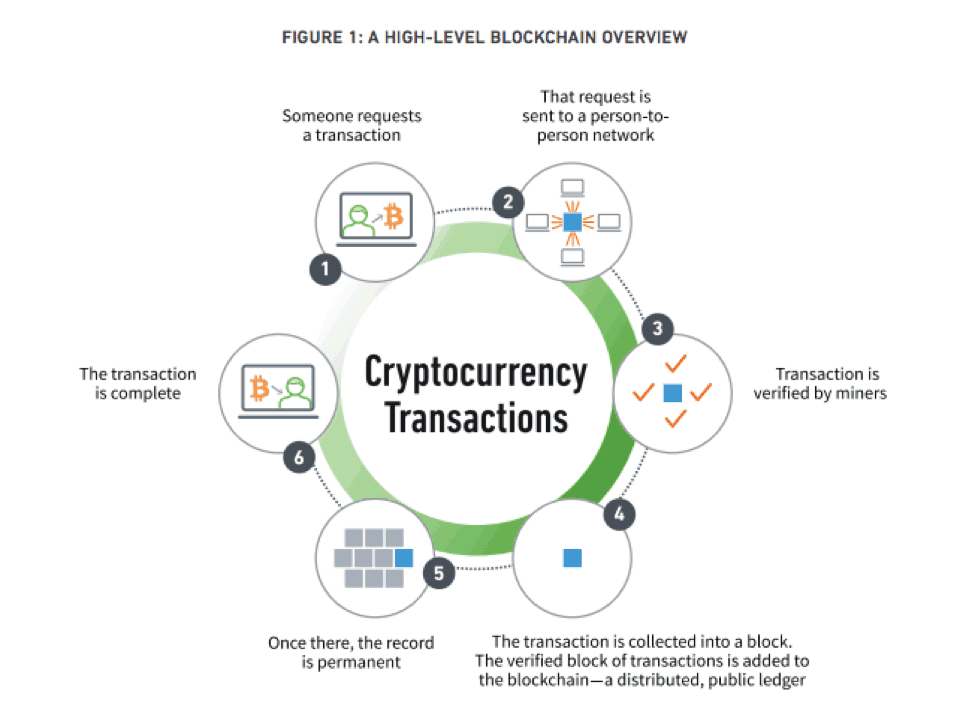
This sounds complicated, and it is. In fact, miners must produce millions of guesses while performing the additional task related to validating a transaction block. And that requires enormous computing power. The urgency to get it done further adds to the compute power needed: they must work quickly because the first miner to get the correct answers wins the reward.
A persistent and deeply hidden insider threat
This new form of insider threat poses the question: what happens if the people you trust abuse their privileges to silently mine cryptocurency? At the time of this writing, a single Bitcoin trades for approximately USD$5,000, which makes mining it potentially very profitable. A single block yields a reward of 12.5 Bitcoin, or about $50,000.
This may sound like easy money, but miners face a major hurdle to turning a profit. The cost of the computing power, including electricity, needed to make all those guesses and validate transactions to receive coins is steep.
Attracted by the potential for big profits, unscrupulous insiders have devised schemes to hijack IT resources of their organizations (and individual users’ machines), using them for illicit cryptocurrency mining. After all, it’s easier to make a profit when you have both free infrastructure and electricity.
For example, system administrators or operational security staff could secretly tap the power of a corporate data center or recruit a small amount of computing power from a number of users’ systems. Or a hacker might compromise a privileged user and perform the same activities from outside your organization after stealing credentials.
The report cites a number of notable cases that have made the news, such as:
- A US Federal Reserve communications analyst was discovered covertly operating cryptomining for more than two years.
- A National Science Foundation researcher was described as using supercomputers at two universities to mine between $8,000–$10,000 in Bitcoin per month.
Termed shadow mining, such secret cryptomining not only consumes resources and drives up utility bills, but also affects the security of an organization’s entire IT infrastructure.
The Risks and Impact of Shadow Mining
For a shadow mining operator to be successful, they must deploy mining applications, or miners, across many systems. And the miner apps must remain undetected. Successful, shadow mining depends on security systems being deliberately misconfigured.
Since all software contains weak points, installing additional internet-connected applications increases any computer’s attack surface. This makes the enterprise less secure by multiplying attack surfaces, while making affected computers less reliable by introducing software that consumes additional resources.
To make matters worse, countless forum posts, how-to guides, and step-by-step videos inform even the layperson about crypto mining techniques—and methods used for automating it. The barrier to entry has been lowered to the point that almost anyone can get started.
Since shadow mining is conducted by trusted insiders, it can be difficult to detect. And it can go on for years before it’s discovered.
Our research shows the many ways shadow mining is done. The scripts used to enable shadow mining leave a telltale trail. And by using host and network data as input data sources, heuristic and statistical methods can be used to detect it.
To learn more about those results and recommendations about how to protect your organization, download the full report.
Want to learn more about Insider Threats?
Have a look at these articles:
- What Is an Insider Threat? Understand the Problem and Discover 4 Defensive Strategies
- Fighting Insider Threats with Data Science
- Insider Threat Indicators: Finding the Enemy Within
- How to Find Malicious Insiders: Tackling Insider Threats Using Behavioral Indicators
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












