Ransomware’s Weakness: How to Turn Ransomware’s Achilles’ Heel Into the Defender’s Golden Hour
By Gorka Sadowski and Barry Shteiman, Exabeam
Ransomware has an Achilles’ heel, yet few organizations are paying attention to the canary in the coal mine. Understanding normal versus abnormal behavior sheds light on the presence of ransomware performing reconnaissance before it strikes. This represents a great opportunity for defenders to get an early heads-up. In this post we’ll examine how organizations can leverage this knowledge.
Ransomware is unfortunately here to stay. It took off in 2013 with the CryptoLocker variant, along with cryptocurrency becoming the de facto payment form. Back then, the attacker asked for a payment of $300 to decrypt the files. How things have changed…today no organization is immune to ransomware attacks, not even hospitals. They used to be spared by attackers who would offer them decryption keys for free. However, over the past two months, several small regional hospitals in France have been hit with a ransom of $50K. This latest Acer attack with an unprecedented $50M ransom is raising some eyebrows and will likely perpetuate, and even exacerbate, a bad cycle of more organizations hit with larger ransoms.
As described in Exabeam’s research paper, “Anatomy of a Ransomware Attack”, there is a fundamental difference between typical malware and typical ransomware. Malware wants to be silent, hidden and linger, whereas ransomware wants to strike as fast as possible, with most phases in the attack lasting only minutes. For reference, the phases of a ransomware kill chain are as follows:

- Distribution campaign – attackers use techniques like social engineering and weaponized websites to trick or force users to download a dropper which kicks off the infection
- Malicious code infection – the dropper downloads an executable which installs the ransomware itself
- Malicious payload staging – the ransomware sets up, embeds itself in a system, and establishes persistency to exist beyond a reboot
- Scanning – the ransomware searches for content to encrypt, both on the local computer and the network accessible resources
- Encryption – the discovered files are encrypted
- Payday – a ransom note is generated, shown to the victim, and the hacker waits to collect on the ransom
There are only a few phases where an organization can disrupt an active ransomware. This is described in the table below.
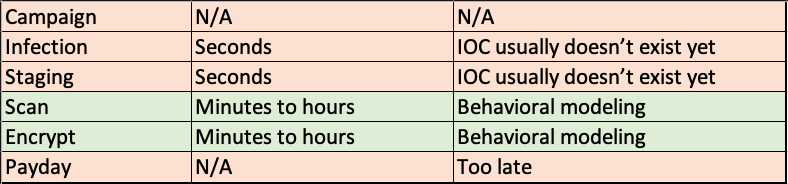
With ransomware, time is of the essence and as stated in the table above, it’s clear that not all stages of attack can be disrupted.
Detecting the ransomware during the early phases of the attack such as “Infection” and “Staging” would require an indicator of compromise (IOC), however those IOCs usually only exist after attacks have been effective and reported back to security vendors at least once. Worse, the most effective ransomware attacks use zero-day or freshly released vulnerabilities – e.g., seven days between the publication of the Microsoft Exchange HAFNIUM vulnerability and the weaponization of that vulnerability for a new attack campaign.
The “Encrypt” phase is also interesting for the defender. Endpoint security vendors can efficiently disrupt the ransomware at this stage, but only for known ransomware strains for which the EDR/AV vendors have developed deterministic signatures. For new ransomware, EDR/AV vendors usually err on the side of caution. Disrupting zero-day ransomware would typically require endpoint security vendors to also disrupt regular users from normal endpoint operations, such as preventing any suspicious process to open, save and/or delete any file.
From our research, the defender’s Golden Hour is when the ransomware is out in the open, during a spread on the network at the “Scan” phase. At that time it’s scanning the network for files and locations to encrypt, verifying the endpoint’s capabilities to encrypt the files and to delete the cleartext versions of these files, as well as checking for the endpoint’s ability to communicate to a command-and-control center. This behavior is primed to be detected with user and entity behavior analytics (UEBA) tools that use advanced analytics’ behavioral modeling, that can understand what is normal versus abnormal, and that can surface relevant insights in a user-intuitive way. This behavior cannot be detected using simple correlation rules because it
1) would require too many rules, and
2) it would generate too many false positives.
Conclusion
Ransomware is here to stay, and organizations large and small need to revisit their risk management priorities for this attack vector. The defender’s window of opportunity is small and requires advanced analytics to try and detect the expected new ransomware and its variants. This can be done by analyzing the behavior of the ransomware executable and the way it interacts with the host and the network. So while it’s almost impossible to write effective correlation rules for unknown behaviors, it’s exactly where UEBA does its trick by detecting the behavioral deviation and thus spotting malicious activity without the need for signatures.
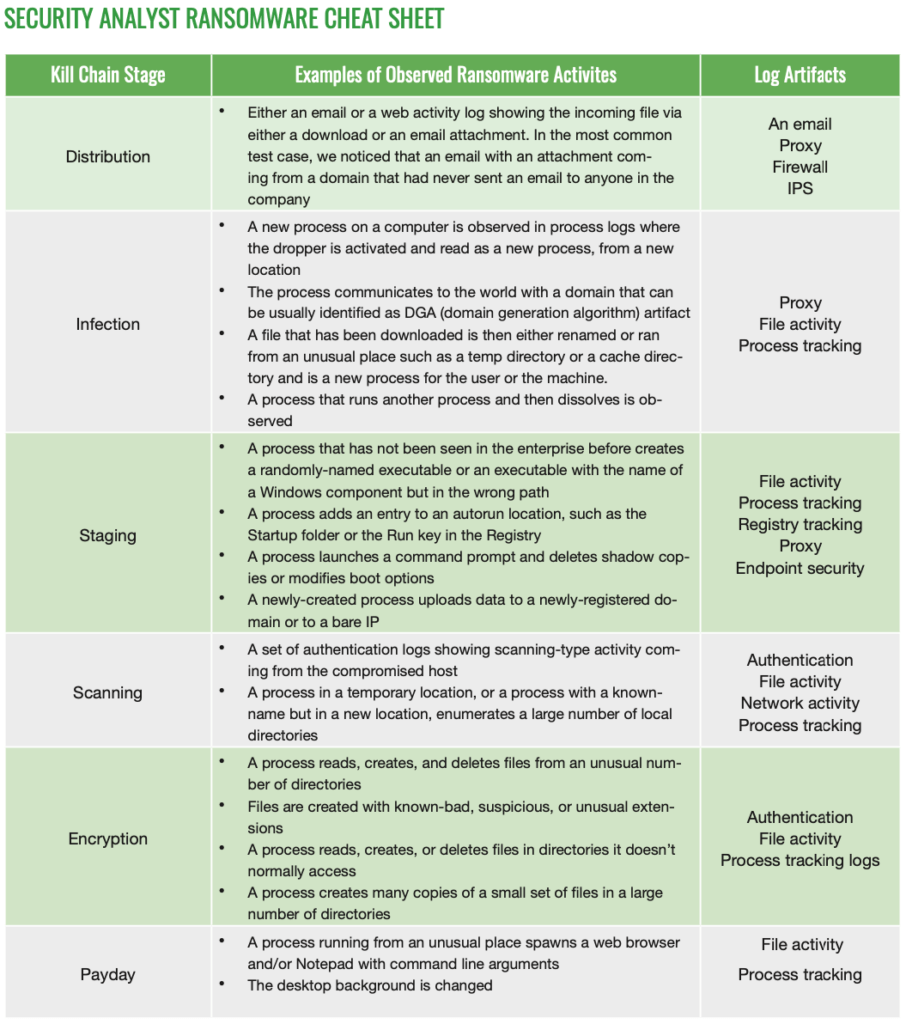
For more information, please refer to “The Anatomy of a Ransomware Attack” and refer to the cheat sheet below to ensure you are collecting the proper logs.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











