External Threats
Defend against phishing, malware, ransomware, and more.
Trusted by organizations
around the world





















Ready to respond
Phishing, malware, and ransomware attackers are a daily occurrence for many organizations.
While defense against these attacks are improving, the diversity and evolving nature of these attacks means prevention is not a given. SOC teams must be ready to respond to an active attack anytime.
- Phishing
- Malware
- Ransomware
Exabeam automatically detects phishing attacks and provides a full list of compromised users and assets for investigation.
Phishing checklist guides analysts to answer key investigation questions and prescribes a comprehensive list of response actions.
The Phishing Playbook automates key workflows, such as leveraging threat intelligence to check the reputation of links or attachments in emails.
Exabeam automatically detects abnormal behavior associated with malware, such as processes executed or anomalous file activity.
Smart Timelines and malware checklists help analysts investigate threats by answering questions like “Has this malware been found on other machines?”
The Malware Playbook automates key workflows, like detonating a file in a sandbox.
Exabeam detects techniques consistently seen across all ransomware attacks, providing visibility into assets with vulnerabilities or misconfigurations that attackers may exploit.
Analysts can quickly investigate and respond to any threats with incident timelines, a guided checklist, and automated playbooks to ensure they intervene in the early stages of a ransomware attack and prevent payday.
pre-built log parsers
As it is ingested, data is parsed using over 10,000 pre-built log parsers and enriched using context sources from open source and commercial threat intelligence feeds.
events per second
Rapid log ingestion processing at a sustained rate of over 2M EPS
vendor integrations
Collect data from more than 665 different product integrations across 332 different vendors.
Explore the many ways Exabeam can work for you
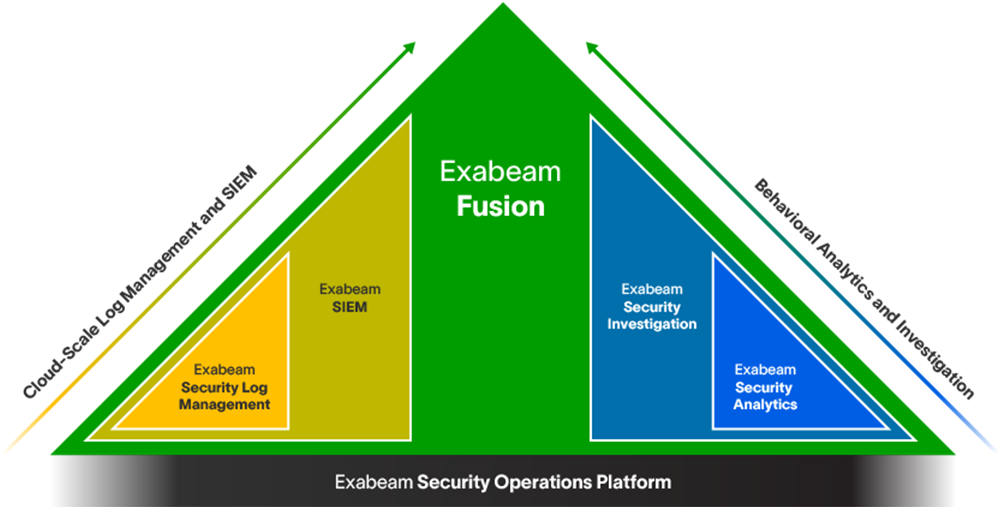
Whether you replace a legacy SIEM, or complement an ineffective SIEM solution by adding UEBA, automation, and TDIR content on top, the modular Exabeam Security Operations Platform can help you achieve security operations success.
- Get started: Exabeam Security Log Management
- SIEM replacement: Exabeam SIEM and Exabeam Fusion
- SIEM augmentation: Exabeam Security Analytics and Exabeam Security Investigation
Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision