Solutions Overview
From industry-specific requirements to outcome-focused use case coverage, Exabeam delivers teams a faster, easier way to protect their organizations.
Use Case Solutions
Exabeam delivers threat-focused security content that enables security teams to deliver faster, more accurate outcomes.
Compliance
Standard reports and detection models enabling always-on compliance adherence.
Compromised Insiders
Once-trusted insiders who are now a threat, either by accident or intentionally.
Malicious Insiders
Detect trusted insiders gone rogue before they cause long-lasting damage.
External Threats
Secondary line of defense against phishing, malware, and ransomware attacks.
Industry-specific Solutions
Exabeam enables security teams to protect their organization’s sensitive data, users, and assets while meeting industry-specific requirements.
Government
Increase threat visibility, detection, and response across your diverse asset and user base from a single platform.
Learn MoreHealthcare
Maintain continuous threat visibility ensuring patient data stays secure, all while meeting compliance requirements.
Learn MoreThe Exabeam Resource Library
Learn everything about the Exabeam platform and beyond. Expand your knowledge on information security with our collection of whitepapers, podcasts, webinars and more.
REPORT
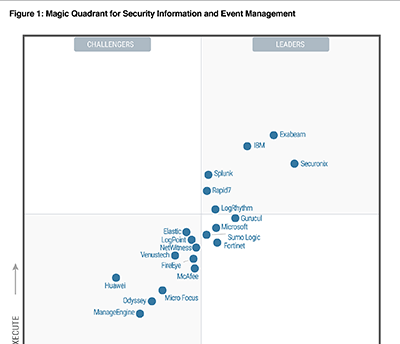
2022 Gartner Magic Quadrant for SIEM
Gartner named Exabeam a leader in the Magic Quadrant for SIEM for the third consecutive year.
Read the Report
WHITE PAPER
SIEM and XDR: A Comparison Guide
Learn how SIEM and open XDR are best suited for different situations. In this comparison guide, we dive into the strengths and differences of SIEM and XDR.
Read the White Paper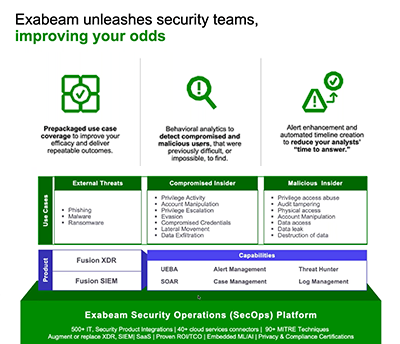
WEBINAR
Top Three Reasons to Replace Your Existing SIEM
SIEMs don’t have to be the bane of your existence, now is the time to take your SOC to the next level.
Watch the WebinarSee the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision






