Both IoT and industrial IoT devices span across our daily lives. Beyond our laptops and smartphones, internet connectivity now includes a wide range of everyday objects and industrial assets, which until fairly recently, weren’t internet-enabled at all. From the Amazon Echo in our homes, to wineries monitoring environmental conditions, to sensors that help you find a parking space—there are now more internet connected devices than humans. In 2017, eight billion connected devices were recorded, claims a recent Gartner study. And the total number of IoT devices are expected to grow to 45 billion by 2023.
On the energy front, many in the renewables industry are saying the future of solar is IoT, where asset management can be a challenge. IoT can resolve common challenges associated with complex energy grids and make it far easier to manage panels and energy output.
In the Amazon jungle, small, IoT-controlled planes are detecting illegal logging and mining in 550 square miles of Peru. And now beekeepers are combating honeybee colony collapse disorder with cellphone alerts when a major change in beehive weight occurs.
IoT attacks are growing
While IoT continually evolves and grows, so do the number of cyberattacks. From 2016 – 2017, the number of IoT attacks has increased from about 6,000 to 50,000. This is a 600% rise in a single year. Meanwhile, the risk of a potentially life-threatening infrastructure attack—such as power grids, gas lines, and hospitals—becomes all the more likely.
According to New York Times reports from intelligence officials and technology companies, this year state-sponsored Russian hackers appear far more interested in disrupting the US electricity grid than the upcoming midterm elections.
What are the unique cybersecurity risks of IoT?
Like all attacks, IoT incidents are unpredictable and can potentially cause tremendous damage. In the Mirai botnet DDoS attack, for example, users hadn’t changed the default passwords of hundreds of thousands of older webcams, DVRs, and routers—an all too common reality. Armed with malicious code, hackers targeted out-of-date Linux kernel versions in the devices, then flooded Dyn, Inc.’s servers—one of the largest DNS providers—with traffic. Systems overloaded and failed, taking down numerous websites, including Etsy, GitHub, Netflix, Shopify, SoundCloud, Spotify, Twitter, and even the site of renowned security expert Brian Krebs.
The challenge of securing IoT
The cybersecurity challenge of securing IoT is complex and extensive due to the fact that IoT devices are deployed over a wide attack surface and contain numerous threat vectors such as authentication and authorization, software, device threats, network threats, and OS level vulnerabilities.
In addition, despite the initiative in developing and deploying innovative IoT use cases, a general lack of standards remains. Organizations often aren’t implementing needed security governance, policies, and compliance. Compounding the problem, many IoT devices aren’t part of a rigorous patch or upgrade routine, leaving them open to security vulnerabilities.
Strategies used for IoT attacks include:
- Identity compromise: The weakest link in the IoT connected device chain is the actual device. For example, hackers might be able to find a device vulnerability and alter the identity of the device to gain access to a network. By infecting one device and gaining access to the network, a malicious actor can begin a large-scale breach.
- Device vulnerability: Much of the embedded firmware running connected devices is insecure and contain vulnerabilities, leaving critical systems at risk.
- Unprotected patches and upgrades: The biggest security challenge with IoT such as connected medical devices or home improvement systems is the inability to easily upgrade or patch them.
- “Man-in-the-middle” attacks: Because IoT devices might be released with security vulnerabilities and poorly configured or unencrypted Wi-Fi networks, devices are prone to man-in-the-middle attacks. Scenarios include attackers secretly relaying and altering the communication between an attacker and a victim, where the victim believes they’re directly communicating over a private connection. In fact, the entire communication can be controlled and altered by the attacker.
Strategies for protecting IoT
The first step in securing IoT devices is to view them as assets or entities that are open to attacks in multiple ways. It’s essential to understand IoT device baseline behavior to be able to identify deviations from established patterns. This enables you to pinpoint rogue activities, such as insider threats for obtaining compromised credentials, accessing sensitive data, and lateral movement within the network.
Because IoT is a hyper-connected, and hyper-distributed collection of resources, there are many behaviors that need to be monitored to keep connected IoT devices in check. It’s necessary to understand the pattern of network communication by analyzing network activities such as bytes transmitted per device, direction of traffic, type of data flow, type of devices being connected, the source of data from devices, and the protocols and services used for data transmission.
Profiling the authorized person(s) who accesses each IoT device provides important data on its valid use and overall health. For example, user behavior analytics can baseline management and maintenance tasks assigned to personnel, so anomalous activities immediately stand out.
In addition, if a “credentialed identity” connects through an IoT device to a database server for the first time, being able to identify such activity in real-time can stop an intruder in their tracks.
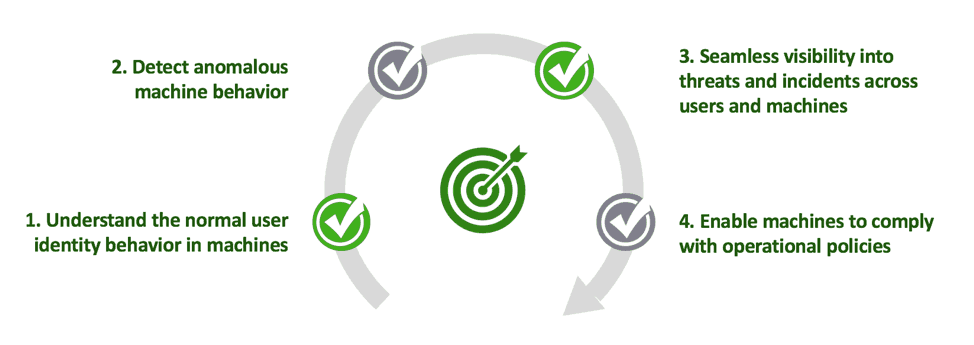
Figure 1 – The stages in the cycle of anomalous behavior identification for effective IoT device management
Go to our Exabeam Community for more information on using Entity Analytics for IoT Cybersecurity and read our next upcoming IoT blog, Preventing Attacks on Your IoT Infrastructure.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












