I love the topic of security automation and have been fortunate to be in the field for many years. As an example, I was part of the original Gartner team that coined and defined Security Orchestration, Automation, and Response (SOAR) back in November 2017.
I’m very happy to see that five years later, there is still a strong interest in this topic. I recently participated in a Twitter thread, in one of those occasions where Twitter fulfills its promise of being a public forum where people can openly collaborate in positive ways. When the right people are participating, one idea leads to another, and discussions land in an interesting place. This is one of these situations. Special thanks to Anton Chuvakin, Christopher Hoff and many others for taking part in a thread that sparked the inspiration to write this blog.
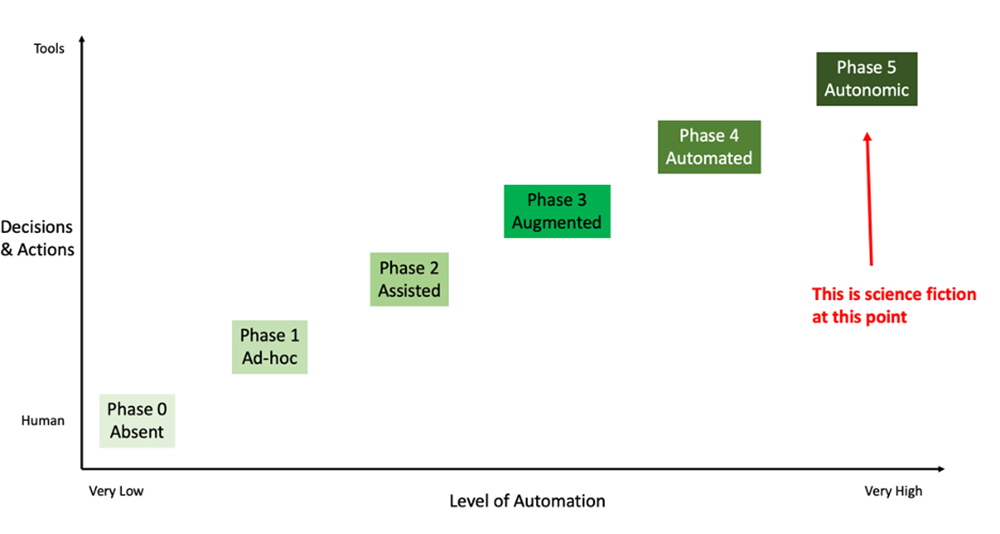
Automation has great potential to alleviate many issues in cybersecurity such as lack of qualified expertise and resources, too many alerts to deal with, and numbing approaches to solving boring problems. However, automation is not a binary proposition — yes, I have automation or no, I don’t have automation — but rather a phased journey that organizations need to embark on, similar to a crawl, walk, run approach. This journey is usually composed of five different phases. Although we have observed variations of the first three phases in full production in organizations, some thought forward organizations are now succeeding while aiming for the fourth level. The fifth level, however, well … that is pure science fiction at this point in time.
Let’s dive deeper. This blog briefly discusses organizations’ automation journey and each of the phases in this maturity model.
Like any worthwhile investment, automation is not free. It requires:
- Careful thinking and planning
- Thoroughly documented processes
- An initial setup of the automation
- A never-ending ongoing phase of continuous improvement and modifications to accommodate the expected environment and process changes
- Tools, and bi-directional integrations between tools
Some of the initial questions in the thinking and planning phase include:
- What will we automate (the entire SOC, some alerts only, investigation timelines, etc.) — what is the scope of the automation
- When will we invoke automated resolution — what are the trigger points for the automation
- Who will decide that automated resolution needs to be performed — specifically, will the decisions be made by humans, or by the tools
- How will processes be automated — specifically, will automation be done via static playbooks or other means
- What are the feedback loops and continuous improvement processes — what is the lifecycle of the automation
- What is the ownership and operating structure — what is the responsible, accountable, consulted, informed (RACI) matrix
Answering the thinking and planning questions is already a serious undertaking, and that is before anything is automated!!
To Automate Or To Not Automate
Automation makes most sense when the environment is fairly stable, a few situations happen over and over again, and problems are always solved the same way. The automation opportunity is to solve once and use technology to repeat many. In this case, there is usually a clear return on investment (ROI) to engage in an automation journey.
On the other hand, when the environment or the processes change frequently, every situation is unique, solution workflows are riddled with exceptions, or the answer to “How do we solve this” is “It really depends” then automation may not make as much sense. And again, as long as the processes have not been properly documented, the organization is not yet ready to automate.
The Five Phases in the Automation Journey
It would be ill-advised for organizations to adopt security automation using a “big bang” approach, but rather they should be wise to embark on an iterative automation journey carefully and intentionally. This allows everyone to get some early wins, learn lessons along the way, iterate in a virtuous circle, maximize ROI, and improve success rates.
Phase 0 — Absent
Organizations start with no automation. Everything is manual. It is usually best to solve problems “by hand” a few times before a repeatable solution emerges.
Phase 1 — Ad-hoc
Organizations will explicitly document some processes or some steps and automate them opportunistically. Automation will be applied to those elements that are particularly predictable, deterministic, and valuable. This happens usually when organizations perceive and understand the potential of automation.
Phase 2 — Assisted
Organizations are now committed to automation and use tools to augment humans’ efficiency in solving problems. This usually means that discrete steps are performed predominantly by tools, and humans are out of the loop for these few steps.
Phase 3 — Augmented
Organizations use tools extensively to perform actions, however decisions are still made by humans.
Phase 4 — Automated
Organizations use tools to make decisions and to carry on the actions associated with these decisions. Humans are there only to make sure that the whole automation machinery is performing as per expectations, and get involved in tweaking, improving and fine-tuning the operations of the automation.
Phase 5 — Autonomic
Tools are running the show, and humans may not even be aware that decisions are being made, or that actions are undertaken, until the tools report back. Even the fine-tuning and tweaking is done by the tools for the tools. Things seem to work “automagically”. This scenario is pure science fiction at this point.
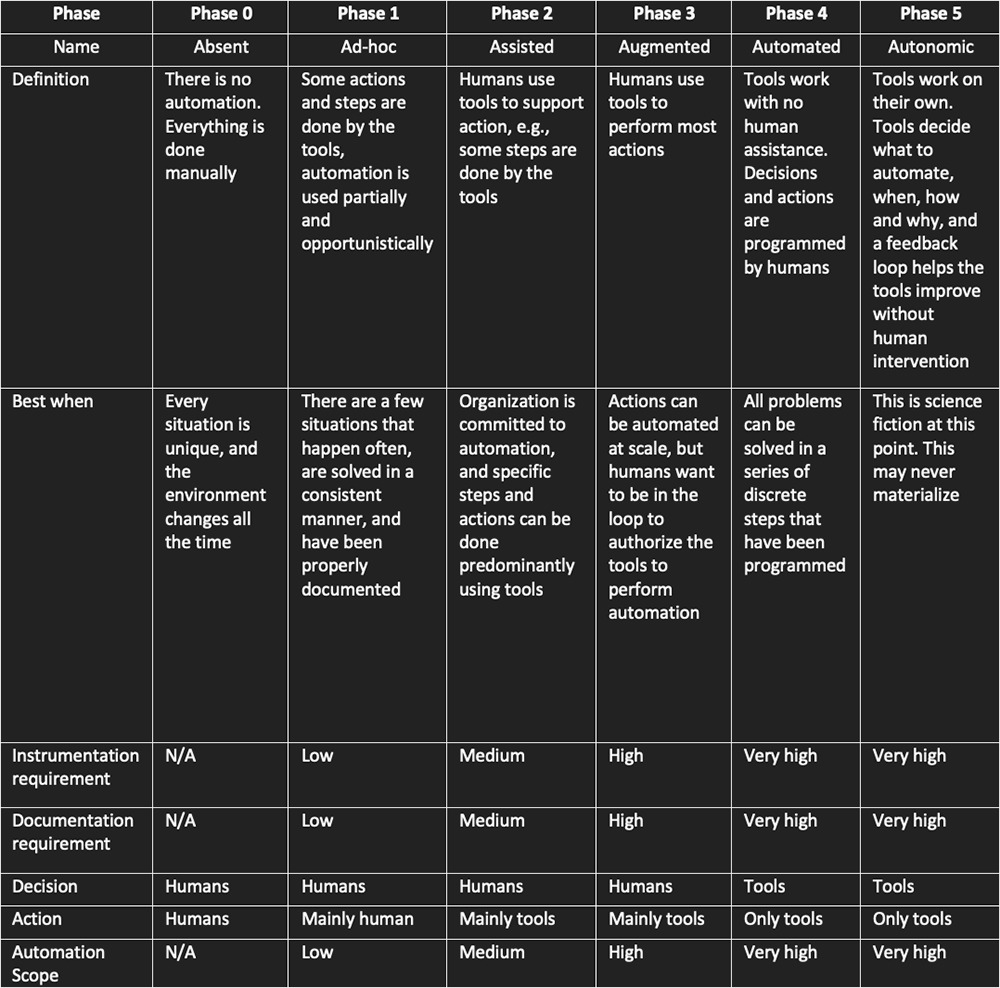
Characteristics of the Automation Phases
Main characteristics of the five phases of the automation journey are described in the following table.
Conclusion
Security automation is a topic that is top of mind for all security professionals, and rightfully so.
While organizations should not underestimate the difficulty of setting up robust automation, the rewards are often well worth it — as long as organizations understand that the journey to more automation needs to be done carefully and intentionally, using a phased approach. And although early deployments and other experimentations are very encouraging, we are actually still in the early days of this discipline despite the marketing from all vendors.
I love the topic of cybersecurity automation. If you would like to discuss automation for your security operations center, contact me anytime by Private DM on Twitter at @gorkasadowski. I look forward to hearing from you and your automation journey!!
Learn more about Security Automation
With employees working remotely and accessing resources and services across public, private, and hybrid clouds through several devices and networks, the attack surface for malicious actors continues to grow.
SOC teams can harden their security posture by combining security and IT operations solutions to defend against these attacks. But balancing the deluge of alerts and staffing adequately can become a challenge as the SOC needs to also continually add to their stack as new threats emerge. This guide helps SOC managers determine where to leverage automation in their workflows to significantly reduce resourcing and budget constraints while ensuring the best security for their organization.

Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!