Shadow Mining and Cryptojacking: Two Commonly Undetected Security Threats [survey]

Security threats often hide in full sight. That’s according to a new survey of 150 cybersecurity professionals polled at the Cloud and Cybersecurity Expo 2019 in London. The survey asked respondents to identify challenges their businesses are facing and the results indicate that many were not aware nor prepared for these threats.
As cryptocurrency continues to grow in popularity, incidents of shadow mining and cryptojacking have risen as well. Shadow mining refers to the use of resources within the organization for mining cryptocurrency. That means the organization is compromised by an insider threat. Cryptojacking is defined as the secret use of a computing device to mine cryptocurrency.
In both cases, corporate IT resources are used to mine cryptocurrencies, which taxes networks and slows down devices, affecting productivity. The survey found that nearly half of respondents lack the tools necessary to prevent illicit cryptocurrency activity off of their own network.
The scope of the problem
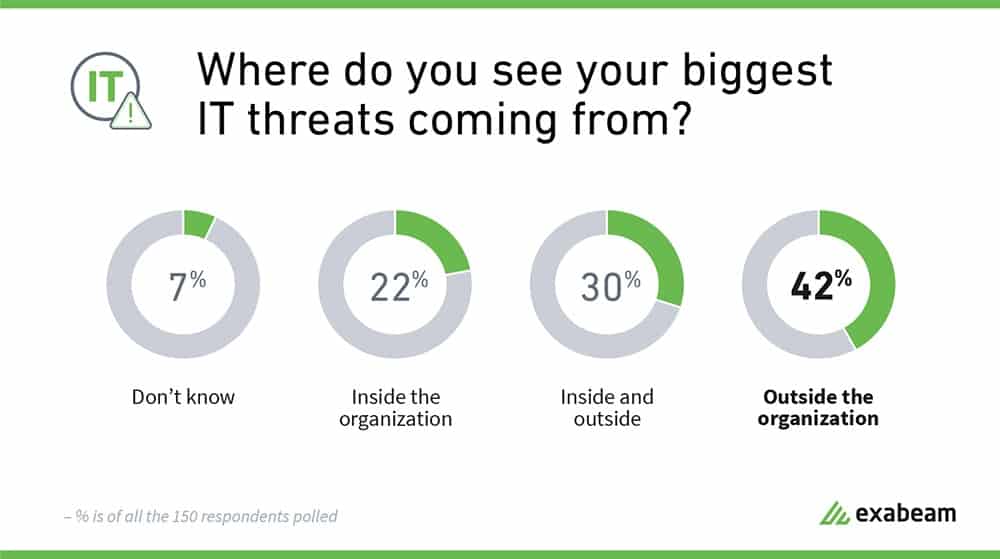
During the survey, when asked where IT threats are coming from, 42 percent of businesses believe that the biggest IT threats come from outside, with only 22 percent seeing the dangers that come from inside their own networks.
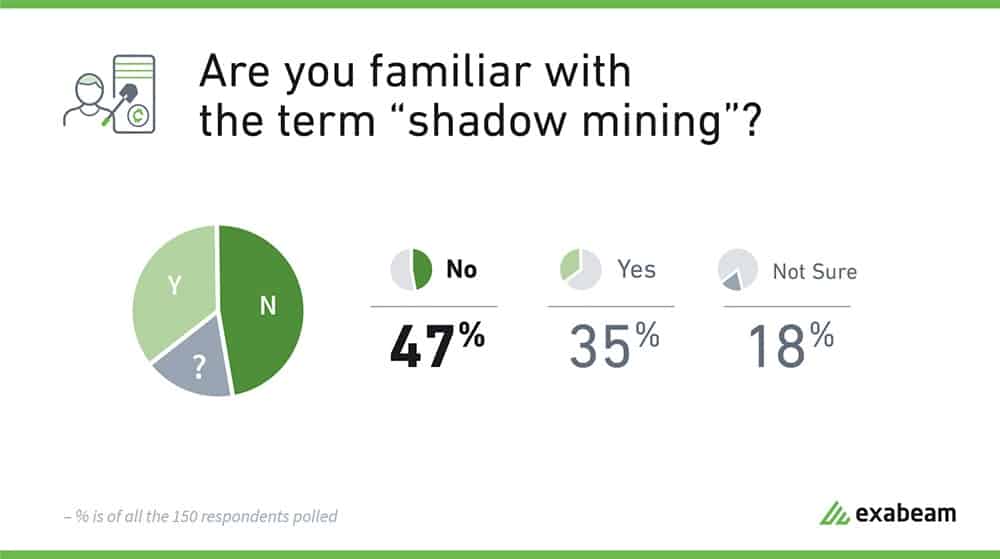
Only 35% of those surveyed were familiar with the term shadow mining.
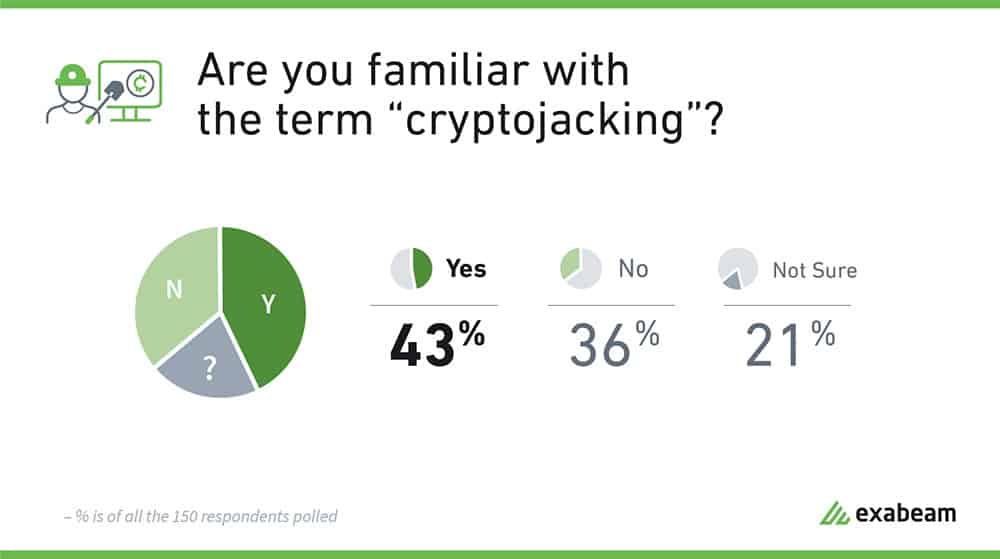
As for cryptojacking, less than half of the respondents were aware of the term.
When asked about their organization’s ability to detect these two types of attacks, six percent of respondents admitted they weren’t equipped to detect or prevent cryptocurrency mining activity, while another 13 percent weren’t confident at all that they could. In total, almost half of the respondents (47 percent) were not very confident that the tools they had in place could detect illegal crypto mining activities on their corporate networks.

Crypto mining threats
The first step to securing your network is understanding the threats you face. According to the survey, security professionals are aware of some threats but may underestimate shadow mining and cryptojacking. The respondents listed the following as top cybersecurity threats:
- Ransomware (40 percent)
- Bring your own device (28 percent)
- IoT botnet and DDoS attacks (13%)
- Shadow mining (10 percent)
- Cryptojacking (9 percent)

How to protect your business
Both shadow mining and cryptojacking can be undetected by some security solutions. For example, it’s a barely noticeable slowdown in your network that indicates your resources may be involved in illegal crypto mining. The bigger issue is that the security of your organization’s entire IT infrastructure may be compromised.
The right security platform can make all the difference, but it’s also important to understand how cryptocurrency mining works. Criminals use borrowed IT resources to mine cryptocurrency, making money without investing in bandwidth of their own. Hackers may make their way into your network through your own employees. One place to start is by educating your employees on the dangers of phishing and other social engineering schemes. Setting strict security requirements at the server level can also help prevent common irresponsible employee behaviors, such as poor password habits and using business resources on public Wi-Fi. Over time, you’ll be able to reduce your risk in addition to detecting and preventing attempts to drain network resources.
For more on the risks posed by crypto mining, read our recent report on shadow mining.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











