January 2026 Updates
The January New-Scale Launch introduces powerful capabilities to secure the modern, agentic enterprise. This release provides a layered approach to securing your AI workforce, offers new strategic insights for security leaders, and enhances the platform experience for every analyst.
クラウドネイティブ・プラットフォームの新機能
New-Scale Security Operations Platform
脅威の検出、調査、対応を自動化し、SOCの生産性を向上させ、セキュリティの価値を実証するクラウドネイティブなプラットフォーム。

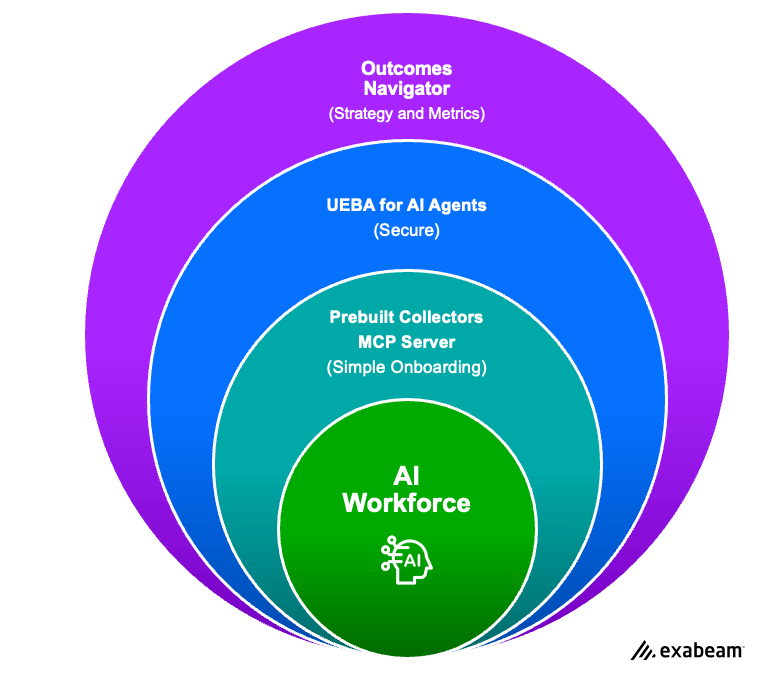
A SECURITY FRAMEWORK FOR AI
Securing AI and Agents
The January New-Scale launch delivers a complete security framework for AI. This release provides the tools to secure AI and agent activity through real-time monitoring, strategic risk management, and compliance oversight.
FACTOR IN AGENT BEHAVIOR
Agent Behavior Analytics
Exabeam Agent Behavior Analytics (ABA) is an industry-first security capability designed for the new digital workforce. Inspired by over a decade of user and entity behavior analytics (UEBA) leadership, ABA provides deep monitoring and an automated forensic timeline for every agent-related investigation, giving you unmatched visibility into this emerging threat vector.

STRATEGIC RISK MANAGEMENT
Outcomes Navigator: Agentic AI Security Use Case
This new use case provides a dedicated, board-ready dashboard to determine your AI security readiness. It gives leaders a single, clear view of their AI risk posture, helps them assess coverage, identify gaps, and simplifies reporting on program maturity to stakeholders.

COMPLIANCE MANAGEMENT
Outcomes Navigator: Compliance Posture Assessment
For the first time, get a quantitative score for your coverage of top compliance frameworks like NIST and GDPR. The Compliance Posture Assessment provides an immediate view of your posture and uses the integrated Exabeam Nova Advisor Agent to deliver a prescriptive, AI-driven plan for improvement.

OTHER PLATFORM ENHANCEMENTS
A More Powerful and Intuitive Platform Experience
This launch delivers platform-wide enhancements, including a fully redesigned and more customizable Dashboard 2.0 for a faster, more intuitive Timeline UX for investigations, new Cloud Collectors for expanded data coverage, and hardened security controls like Universal Logout for Okta.
セルフホスティング・プラットフォームの新機能
LogRhythm SIEM
A scalable, intuitive, cost effective, self-hosted SIEM that delivers comprehensive visibility, protection, and threat detection across all environments, systems, and assets.
AEI Events on Data Indexer Dashboards
Analysts can now pivot from a high-fidelity, AI-driven alert to the underlying raw data with a single click. By embedding AI Engine events directly into dashboards, this feature directly connects detection to investigation, eliminating context switching and reducing mean time to respond (MTTR).
Refreshed Threat Map
The Threat Map features a significant redesign, offering a more intuitive, real-time visualization of threat activity. The updated interface provides a clearer insight into the geographic source and targets of attacks, enabling better analysis of attack patterns and business risk.
AIE API
This release introduces a new API for the AI Engine (AIE), allowing security teams to programmatically create, read, update, and delete AIE rules. This allows organizations, especially MSSPs and large enterprises, to automate rule management and maintain consistency across multiple deployments.
Improved Salesforce Log Collection
Gain deeper visibility into critical SaaS applications with improved log collection for Salesforce. This provides enhanced insight into user activity, permission changes, and potential data exfiltration, allowing teams to apply advanced analytics to detect threats within Salesforce.
JSON Policy Builder
To simplify and accelerate the use of administrative APIs, the new JSON Policy Builder provides an intuitive, wizard-driven web tool to generate properly formatted policy files. This eliminates manual JSON coding, making automation more accessible and reducing errors.
Platform Enhancements
This release strengthens the LogRhythm SIEM platform with expanded compatibility and core functionality. Key updates include official support for Windows Server 2025 and Rocky 10, a new Linux System Monitor Agent with near-feature-parity to the Windows agent, and ongoing security and performance optimizations.

Exabeamのデモを見る
脅威の検知、調査、対応(TDIR)のための業界最強のプラットフォームに関する詳細情報の請求やデモのご依頼はこちらから。
詳細はこちら:
- セルフホスト型SIEMとクラウドネイティブ型SIEMのどちらが適しているか
- クラウドスケールでデータを取り込み、監視する方法
- AIや自動エージェントの行動を監視・分析することで、人間以外の危険な行動を発見する方法
- ユーザーの活動を自動的にスコア化し、プロファイリングする方法
- インシデント・タイムラインを使って全体像を見る
- プレーブックが次の正しい決断に役立つ理由
- コンプライアンスの義務化
受賞歴のあるセキュリティ界のリーダー









