
A Four-Layered Approach to Malware
- Apr 12, 2022
- Tim Lowe
- 6 minutes to read
Table of Contents
The best way to detect and respond to malware is to create a layered approach within your network and among your workforce. According to the MIT Technology Review, the number of zero-day exploits discovered in 2021 more than doubled the number discovered in 2020. The exponential increase in zero-days in 2021 was not attributable to better detection capabilities, according to the publication, but rather it was greater access to purchased zero-days by international hacking groups. Consultants and security vendors might assure you that your network is locked down against malware and ransomware threats, but no environment is completely secured against the unknown unknowns that zero-day attacks represent. There are a great many security solutions that protect against malware in many different ways. In this article, we’ll explore a multi-layered approach that allows us to use all the tools in our security toolkit to thwart the tools in a hacker’s toolkit. When it comes to malware events, security practitioners “gotta catch ’em all”, while hackers just have to get lucky once.
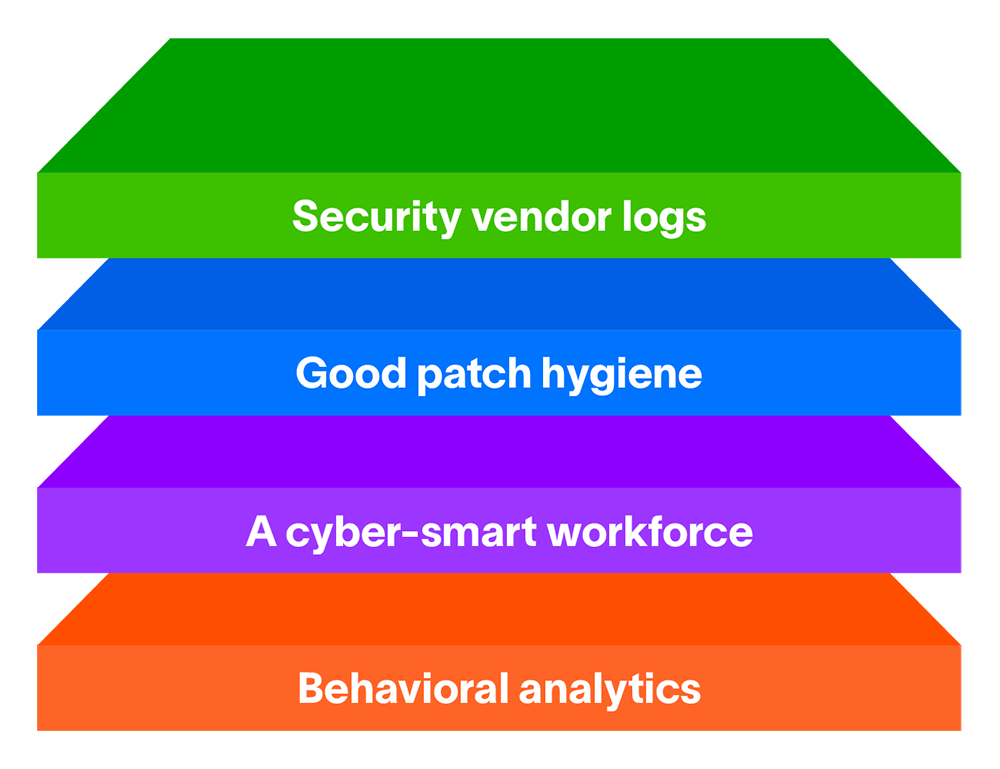
Layer 1: Security vendor logs
Building a layered approach requires using all the tools in your security toolbox. It means throwing all the security logs and alerts at detecting malware. Some vendor log types that can show malware known to security researchers are:
| Anti-virus software | CASB | Email gateways | Endpoint detection and response tools |
| Intrusion detection/protection systems | Phishing solutions | Smart firewalls | User and Entity Behavior Analytics |
Each one of these vendor solutions defends against malware in a slightly different way. These elements form the strata of your security stack. They are all working individually to protect the network. Each provides a small aperture through which to view threats to your network. The aggregation and presentation of these logs in a single, chronological view creates a comprehensive view of the alerts your security logs.
Layer 2: Good patch hygiene
With the exception of User and Entity Behavior Analytics (UEBA), the solutions in Figure 1 rely heavily on signatures of attack. In most cases, this means hashes of malicious files previously discovered in the wild and their respective hashes compiled in threat intelligence databases. When the security solution detects a matching hash or filename, it takes some action against it. This could mean blocking the known file from entering the network or the spawning of a process to detonate and isolate the file in a sandbox. Other known signatures of hacker toolkits might be included in the software as well. This could include processes known to deploy or disseminate malware or ransomware. Layering multiple solutions with varied threat intel feeds is a robust layer of defense against malware.
Threat intelligence match alerting should also include a current feed of known malicious IP addresses and domains. Threat intelligence feeds usually contain a listing of IPs and domains that have been discovered as command and control nodes for malware and ransomware. These should also be incorporated into a layered defense. Additionally, threat intel feeds usually contain web categories for URLs with low rankings that represent a risk of malicious behavior that can be incorporated into rule content for alerting. Lastly, sites hosted using dynamic DNS is an indication that some shadiness might be involved in the site and it should be monitored.
Layer 3: A cyber-smart workforce
Not all defensive layers in your malware defense posture are dependent on having intelligent software installed and running. There are human elements involved as well. Most malware achieves its goal via human error. Phishing campaigns, social engineering and drive-by downloads by visiting unsafe sites are three of the most common ways malware is delivered. The human layer in your security stack should also include:
- Security awareness training: Most organizations have mandatory security training that is due annually. Many times this training is repetitive and the same for years. It’s important to find a training program that is varied and engaging. It’s critical to inform employees of common tricks and techniques bad actors use on the web and in emails.
- Phishing simulation campaigns: Keeping the dos and don’ts at the forefront of the workforce’s mind is critical to preventing malware during a phishing, spearphishing, or whaling campaign. Teaching the workforce how to identify common phishing tricks used by attackers is important, but more important is to keep that phishing possibility in the minds of the workforce when they’re in a hurry or multi-tasking. Fortunately, the author of this article has never been tricked by a pseudo-miscreant faking a phish attempt. It has not happened… twice. Ahem. Some of them are very good. It can happen to anyone, right?
- Timely patches and updates: Anyone who knows anything about cybersecurity knows that machines going unpatched is a very serious vulnerability. Most IT professionals also can tell you stories about the horrors some egregious lack of patching caused their organization or their home servers,— lots of trouble due to vulnerabilities in the software of which they were unaware. Microsoft released the patch to Server Message Block v1.0 in 2017, and people are still getting pwned by WannaCry ransomware five years later. Information security team members are not usually responsible for system patching, but it’s worth having a talk with InfoSec leadership about the organization-wide posture when it comes to patching systems. InfoSec knows better than most that when you fail to patch and protect, InfoSec gets hammered and rekt. (This writer just made up that catchy rhyme, so feel free to use it for your about-to-be-scheduled meeting with your CISO to discuss the dangers of not pushing patches and updates.)
Layer 4: Behavioral analytics
Hackers will never breach a network to do the work of the person they’ve exploited. They have their own goals on the network. This means that their behavior will be different than the person whose credentials or machine they’ve compromised. This change in behavior is detectable with a User and Entity Behavior Analytics platform. Using established baselines of user and asset activity, deviations from the modeled norms could be an indication of a bad actor deploying malware or positioning themselves to do so. The added layer of protection against an attacker running roughshod through your network is that unauthorized access to your network is likely to be detected before an attack in many cases. The goal of many types of malware is to increase and expand its presence on the network to achieve its aim. That goal might be to dump credentials and exploit more users. It could be to specifically target an individual or database to get valuable information out of the network. These types of activity show up as the malware carries out activity that the user or asset would not typically display. This anomalous behavior is surfaced by behavioral analytics in most cases, and could highlight malware on your system before it is deployed.
Evidence of some of the following activity types may surface via abnormal behavior for a user or asset, such as:
| Compromise of credentials | Moving laterally | Escalating privileges | Abusing system privileges | Attempts to evade detection |
| Manipulating accounts | Tampering or deleting audit logs, journals, or disabling recovery mode | Destroying data | Abnormal authentication and access | Exfiltrating data |
Earlier I mentioned signature-based detection and fact-based rules, and the security benefits they bestow. If no signature exists, we have what is referred to as a low observable characteristic attack. Unknown unknowns, including but not limited to zero-days, can’t be caught via this method of detection. It requires the establishment of a baseline of “normal” for a user or asset.
Other types of behavior that might be a clue to detect malware on your network are abnormalities related to activity in memory. In the absence of a file that can be identified via its hash or file name, there is no detection, no matter how sophisticated the threat intel, without some sort of anomaly analytics. Some tools identify types of behavior occurring at the operating system for alerting. Known actions can throw alerts. These types of alerts are typically the types of activity a systems administrator would carry out and, in many cases, lead to lots of false positives. Behavioral analytics can detect abnormal actions that are transparent to most end users.
Most system users are not conscious of services, spawning executions, scheduled tasks, and other processes running on their machine unless they are causing problems. Hackers don’t want their malware to cause problems for the user and become noticeable, in most cases. The notable exception here is ransomware, which is intended to be unavoidable to the end user. Some activity that behavioral analytics can model and alert on when there are anomalies on the system are:
| Processes | Services | Command line arguments | DLL injection and side-loading abuse |
| Powershell commands | Scheduled tasks | Programs | Executions |
Alerts based on these types of events could be the difference between detecting an unknown type of malware or a novel process and letting that malware achieve its goal.
There are lots of ways for malware to enter an environment. Awareness of these vectors is crucial for information security teams and the workforce at large. Not all attacks can be prevented, but with the proper layering of security vendor logs, good patch hygiene, a cyber-smart workforce, and behavioral analytics your team will come much closer to catching them all.
Explore these resources:

Tim Lowe
Senior Community Content Developer | Exabeam | Tim Lowe is the Senior Content Creator for the Exabeam Community, principally involved in multi-media product creation in support of Exabeam Use Case methodology. He was an Exabeam user as a Cybersecurity Engineer at a Fortune 500 company prior to coming to Exabeam. He served 14 years as a Cryptologic Technician and Intelligence Analyst for the US Navy and National Security Agency, where he was involved in technical development for a wide array of national security interests. His background, prior to migrating to the field of cybersecurity, is in linguistics. He did his Bachelor’s and Master’s degree in French Literature before studying Arabic at the Defense Language Institute in Monterey, California. He has worked in nine different countries in the security and cyber fields and lived in Europe for five years. He currently lives outside of Birmingham, Alabama with his wife and three daughters. He’s an avid mountain biker, musician, and obsessive audiophile.
More posts by Tim LoweLearn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
-
 Blog
Blog
What’s New with New-Scale in October 2025: Measurable, Automated, Everywhere Security Operations
- Show More




