The data breach at Capital One that exploited a vulnerability in the cloud reported a few weeks ago was one of the largest-ever bank data thefts. A former employee at Amazon’s cloud-computing division is allegedly responsible for the theft of 106 million Capital One Financial Corp. records.
This technical analysis of the Capital One data breach is based on the wealth of publicly-available information. The 11 techniques used to launch the attack provided 11 opportunities for detection. These techniques are mapped to the MITRE ATT&CK framework. We then look at how it could have been prevented using Exabeam UEBA technology.
The information provided below is based on the legal document that was presented before the court during the suspect Paige Thompson’s hearing.
Impact of the data breach
An estimated 100 million U.S customers were affected by the breach with another 6 million impacted in Canada. Other key details on the impact include:
- Personally identifiable information (PII) including social security numbers, bank account details and credit card numbers, phone numbers, and dates of birth were stolen.
- The attacker was also able to gain credit history information on some customers, including credit scores and credit limits.
Background of the breach
The attacker took advantage of a misconfiguration in the open-source web application firewall Capital One was using and exfiltrated data from an Amazon S3 instance.
- What was taken: credit card applications from 2015 – 2019
- Type of information in the records: names, addresses, zip codes/postal codes, phone numbers, email addresses, dates of birth and self-reported income, 140,000 Social Security numbers and 80,000 linked bank account numbers
- Other data: Some transaction data from a total of 23 days during 2016, 2017 and 2018.
Summary
The breach on Capital One conducted by the attacker exploited a firewall vulnerability. All major cloud services have their own web application firewall (WAF). Amazon S3 instances such as the one used by Capital One include the AWS WAF.
The attacker first executed a command in the WAF to gain credentials to an admin account. Once the attacker gained access, she executed a series of commands on the server to list the folders and directories from Amazon’s metadata service. Next the attacker wrote commands to extract the data and exfiltrated it to a local 32TB drive. Finally, all the stolen data was uploaded to the attacker’s GitHub profile. All of the activities were recorded and reported to Capital One by a security researcher.
An analysis of how the attack unfolded
According to the document, a firewall misconfiguration permitted commands to reach and be executed by the affected server, which gave the attacker access to folders or buckets of data in Capital One’s cloud storage. The following is a detailed account of the attack timeline and analysis of the different techniques used in the attack:
- The attacker obtained security credentials for an account (ISRM-WAF-Role) that in turn, enabled access to certain folders in Capital One’s AWS instance.
- Next the attacker used the ISRM-WAF-Role account to list the names of the folders or buckets of data. Capital One confirmed that data from more than 700 folders were listed.
- Data from these folders were extracted using requisite permissions from the ISRM-WAF-Role account. According to the document, Capital One’s logs show a number of connections or attempted connections to its servers from TOR exit nodes. There were also a number of connections from IP addresses beginning 46.246.**.** all of which were related to activity conducted by the same individual. This attack spanned multiple months with a related activity occurring a month prior to the attack.
One of the files copied from Capital One’s folder has a specific file name that was accessed for the first time by the ISRM-WAF-Role.
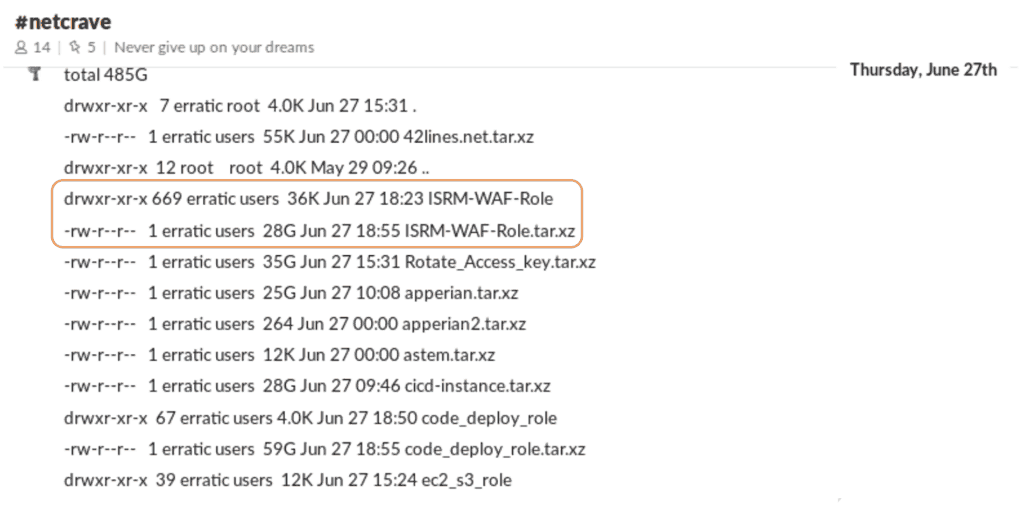
Figure 1: According to the attacker’s posts on Slack, the two items in the list above beginning with “ISRM-WAF” belong to Capital One. (Source: https://krebsonsecurity.com/2019/07/capital-one-data-theft-impacts-106m-people/#more-48393)
Mapping the attack to the MITRE ATT&CK framework
Several stages of an attack kill chain outlined in the MITRE ATT&CK framework were seen in the Capital One data breach – initial access, persistence, discovery, exfiltration and command & control. In fact, for some tactics, the attack leveraged multiple techniques to accomplish that phase of the kill chain which is explained below.
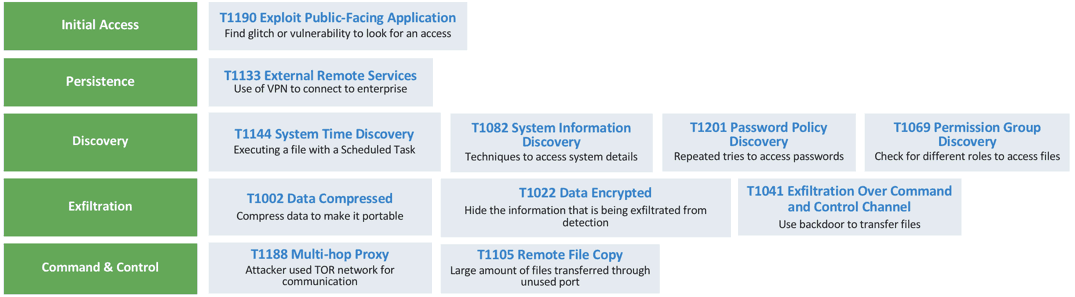
Figure 2: How the tactics and techniques used in the Capital One attack map to the MITRE ATT&CK framework.
Initial Access
- Exploit Public-Facing Application (T1190) – The attacker leveraged a glitch or a vulnerability in the application to get an initial access to the server.
Persistence
- External Remote Services (T1133) – The attacker used remote services such as VPN to connect to internal enterprise network resources from an external location.
Discovery
- System Time Discovery (T1124) – An adversary can find out the system time and/or time zone from a local or remote system. This information can be used to schedule tasks to execute programs at system startup or on a scheduled basis, to conduct remote execution, to gain system privileges, or to run a process under the context of a specified account.
- System Information Discovery (T1082) – The attacker used enumeration techniques to access the system details such as version, patches, hotfixes, service packs, and architecture.
- Password Policy Discovery (T1201) – The attacker may try to find the policy enforced in the organization to make a list of passwords to attempt a brute force or any other type of attack.
- Permission Group Discovery (T1069)– The attacker used discovery to check for local level group and permission settings.
Command-and-Control
- Multi-hop proxy (T1188) – The attacker used a TOR network for communication.
- Remote File Copy (T1105)– Large amounts of files were downloaded and transferred through an unused port.
Exfiltration
- Data Compressed (T1002) or/and Data Encrypted (T1022) – It’s not clear from the report the kind of commands used to compress the files but the attacker did compress the data to make it easier to transfer the files.
- Exfiltration Over Command and Control Channel (T1041) – The attacker used a backdoor to transfer files to their local system before uploading to her GitHub account. However the legal document doesn’t name the exact command and control or the IP, but she would have queried an unknown DNS server to get the data.
Armed with the knowledge of the tactics and techniques, the question remains: How can a breach like this be prevented?
The attacker uncovered several loopholes in the attack chain such as a misconfigured WAF, lenient access policies, undetected command & control activities and command executions. Many of these activities are undetectable using legacy security tools. They require a behavioral approach to threat detection.
The following section of this post looks at how enterprises today can achieve a stronger security posture using Exabeam user and entity behavior analytics (UEBA) technology. We’ll look at a selection of the tactics and techniques used in the Capital One attack chain and show how it can be detected using Exabeam.
Detecting the attack using Exabeam Advanced Analytics
Exabeam Advanced Analytics is part of the Exabeam Security Management Platform which is designed to perform user and entity behavior analytics (UEBA) for threat detection. Advanced Analytics preprocesses all logs and combines them with other data sources to baseline normal user and asset activities. In this way, the system can easily identify any anomalous behavior, such as those associated with attacks.
Advanced Analytics ties all the events both normal and abnormal and presents them in a chronological timeline to make it extremely easy for analysts to pinpoint anomalous behavior. Exabeam Smart Timelines provides analysts with the new method of incident investigation and response—one in which they don’t need prior knowledge of an attacker’s tactics and techniques.
Detecting initial access
Adversaries use various techniques to gain access to an environment. Techniques may include targeted spearphishing or exploiting weaknesses on public-facing web servers. If security tools are able to effectively detect and enable security teams to respond to these techniques, the attack will be less successful in developing into a data breach. Exabeam uses UEBA to model normal behavior for users and machines, and then identify the anomalous activity associated with these specific techniques.
Here is one such example:
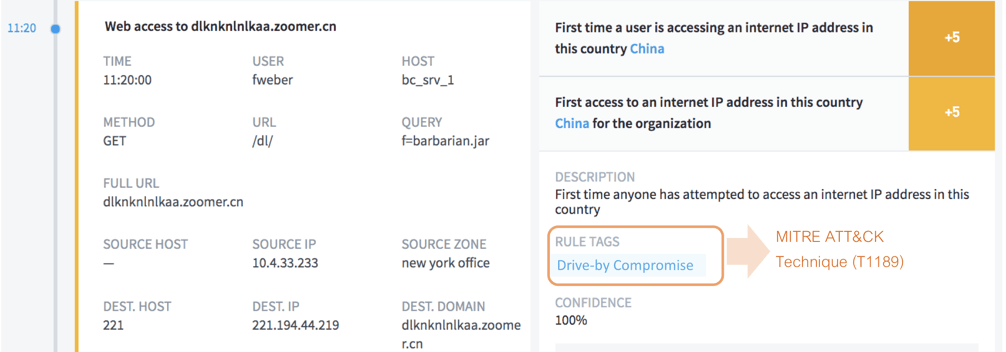
Figure 3: Exabeam detects a “Drive-by Compromise” technique where an adversary gains access to a system after the victim visits a weaponized website.
Detecting first-time access and external remote services
Advanced Analytics has preconfigured rules and models to detect any first-time access and external remote services. This activity is shown as part of the timeline and assigned a risk score. Risks are scored based on machine-learning algorithms and the impact the event can have on the organization.
Exabeam processes various data sources like authentication logs, file and process monitoring, email gateway, web logs, firewall logs, application logs, and cloud access, to correlate and build behavioral models to detect first-time access to an asset, connection from external IP, user access to various public-facing applications or websites and login to public cloud providers like AWS, Azure or GCP. Here are a few examples of how Exabeam uses machine learning models to help detect anomalous behaviors and tag them to the techniques outlined in the ATT&CK framework.
In Figure 4, Exabeam tags the activity to the ATT&CK technique, External Remote Services as it is the access mechanism to connect to internal enterprise network resources from external locations.
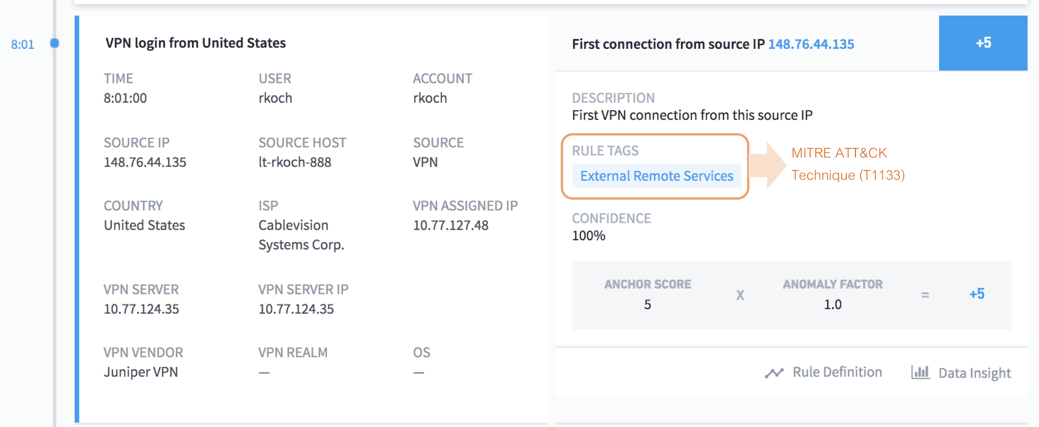
Figure 4: VPN activity is identified as anomalous and given a risk score because it’s the first time the user is accessing the network from an unknown IP address.
Figure 5 shows how Exabeam detects a technique known as Valid Accounts that is used by adversaries to gain initial access to the system through social engineering. Typically this entails stealing specific user or service account credentials. In this example, the user is using a Salesforce account which is configured by an organization for remote or external services in order to gain initial access.
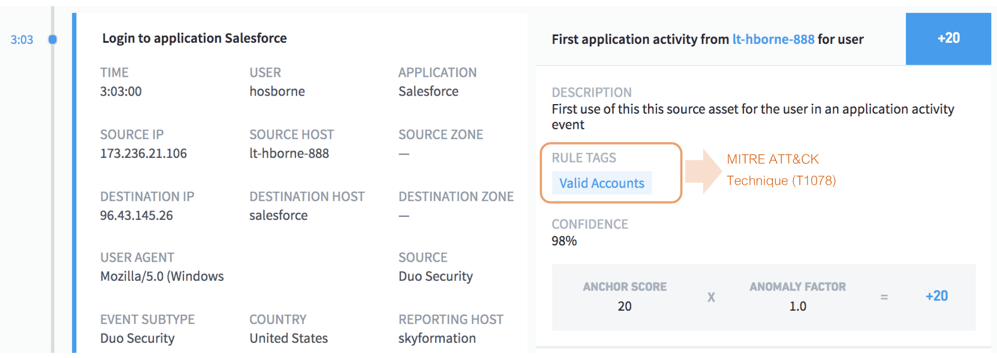
Figure 5: Exabeam flags risky behavior when the user is trying to get into the Salesforce application for the first time (the Valid Accounts technique is being used to gain initial access to the system).
Detecting discovery
An adversary may use many techniques during the discovery phase to gain enough information about internal systems and network before accessing them. The techniques in this tactic help adversaries observe the environment and orient themselves before deciding how to act and explore what they can control.
Exabeam ingests many data sources like process and command-line monitoring, file monitoring, API monitoring, powershell logs, network logs to detect adversaries attempting to enumerate files/directories on a host, list local system or domain accounts, get information on registered services or running processes, or learn about network configuration and settings. Here is an example of how Exabeam detects these techniques.
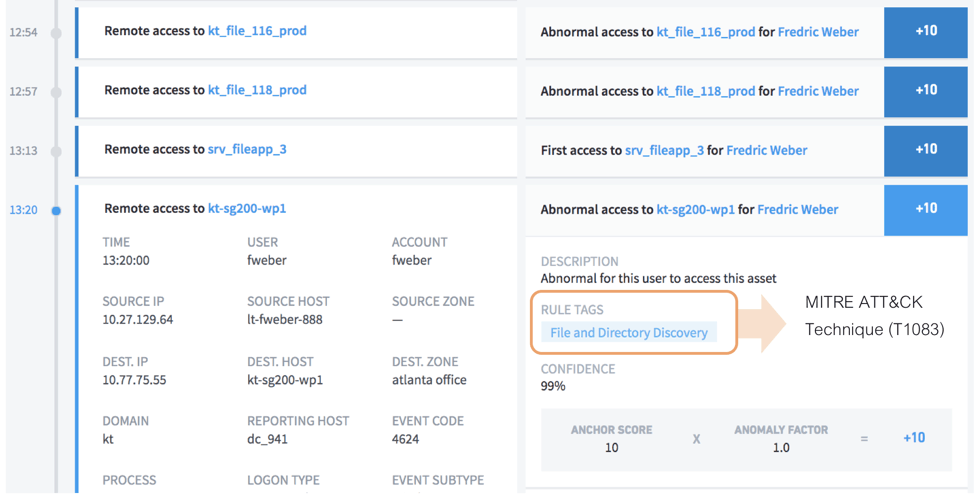
Figure 6: The file and directory discovery technique shows the attacker searching for files.
Detecting exfiltration activities
Data exfiltration occurs when data is illicitly transferred outside an organization. It can happen when a user transfers data over the internet, which often is the result of malware infecting local systems.
Exabeam monitors files, processes, network, cloud access and also integrates with several DLP vendors including Symantec, Forcepoint, Palo Alto Networks, and Zscaler, to detect data exfiltration and identify infected systems that transmit data to unauthorized parties. Exabeam behavioral models also detect unusual amounts of network traffic over protocols that facilitate large data transfer compared to the baseline of a user or machine transferring the data.
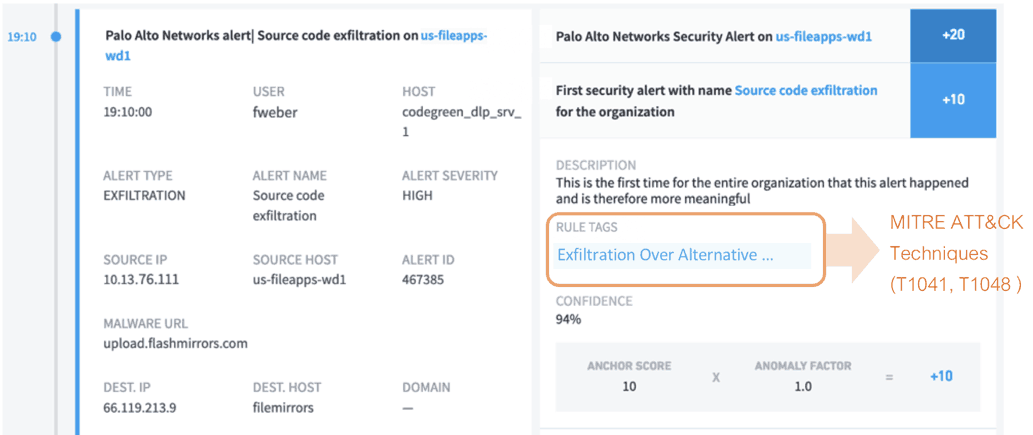
Figure 7: Example of a data exfiltration technique detected by Exabeam.
Data is usually compressed and/or encrypted to hide the information that is being exfiltrated and to make it less conspicuous when inspected by an investigator. Exabeam has file modification rules that trigger alerts if files are encrypted or compressed.
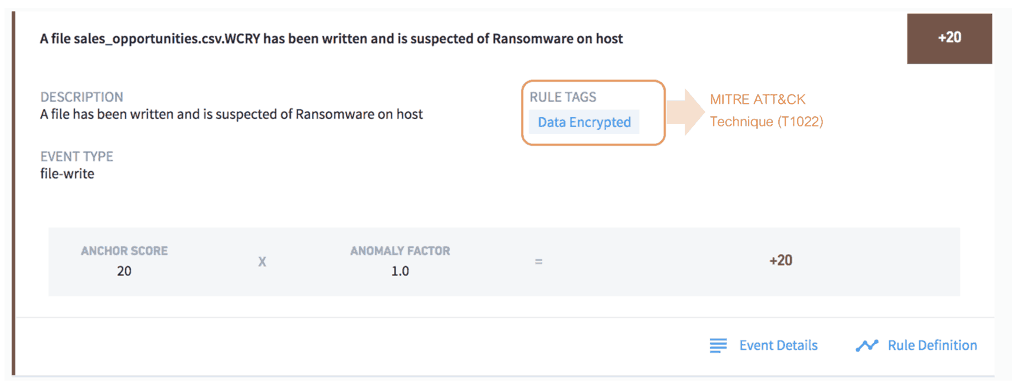
Figure 8: Exabeam UEBA showing detection of an encrypted file that is suspected of being ransomware.
Monitoring user activities on AWS and other IaaS providers
Exabeam has visibility into file downloads and uploads in AWS through the AWS Cloud Connector. Exabeam Cloud Connectors allow enterprises to easily collect logs from cloud services (like AWS CloudTrail, CloudWatch, Redshift) into Advanced Analytics. These can be combined with data from on-premises applications to improve detection of an attacker’s tactics, techniques and procedures using behavior-based threat detection.
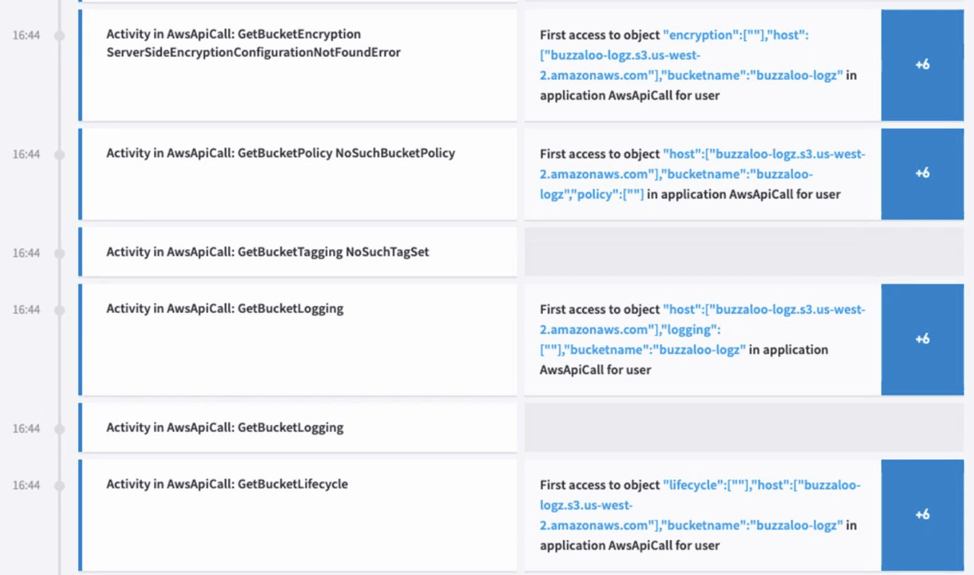
Figure 9: First time access to AWS objects are detected and shown in a Smart Timeline on the right of the screen.
Additional ways to improve security on an AWS instance
The following practices can also be applied to AWS instances to improve an organization’s security:
- Monitor CloudTrail logs for any malicious activity and enable log file integrity monitoring.
- Restrict access to the S3 buckets containing highly sensitive information to known IP ranges.
- Configure your S3 bucket policy to access files only within the VPC, so that even if the credential leak occurs, the attacker cannot get direct access to the files.
- Apply KMS encryption on the bucket objects.
- Restrict IAM profile so that an externally available instance does not have full access to the data warehouse.
Conclusion
Capital One’s well-documented attack shows the many tactics and techniques that are used by an attacker. Time is of the essence to quickly decipher techniques used and detect anomalous behavior. Resolving the attack sequences requires SOC analysts to see the complete picture. Smart Timelines provides just that. By tying together the behaviors identified as anomalous and risky in Exabeam, with the techniques identified in the ATT&CK framework, SOC analysts can trace the steps an attacker has used and uncover where they may be heading next. Smart Timelines show all the events in a chronological timeline so analysts can pinpoint the anomalous activities and respond quickly before it becomes a threat to their organization.
Editor’s Note: The screenshots above are from a forthcoming release of the Exabeam Security Management Platform.
Further reading
Mitigating Security Threats with MITRE ATT&CK
Smart Timelines: Nine Benefits for Detecting and Investigating Security Incidents
Why Understanding the Entire Attack Chain Before Responding is Critical
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













