SIEM Tools Explainers:
SIEM Tools: Top 6 SIEM Platforms, Features, Use Cases and TCO
A Security Information and Event Management system (SIEM) is a foundation of the modern Security Operations Center (SOC). It collects logs and events from security tools and IT systems across the enterprise, parses the data and uses threat intelligence, rules and analytics to identify security incidents.
What are Gartner’s Top SIEM Solutions?
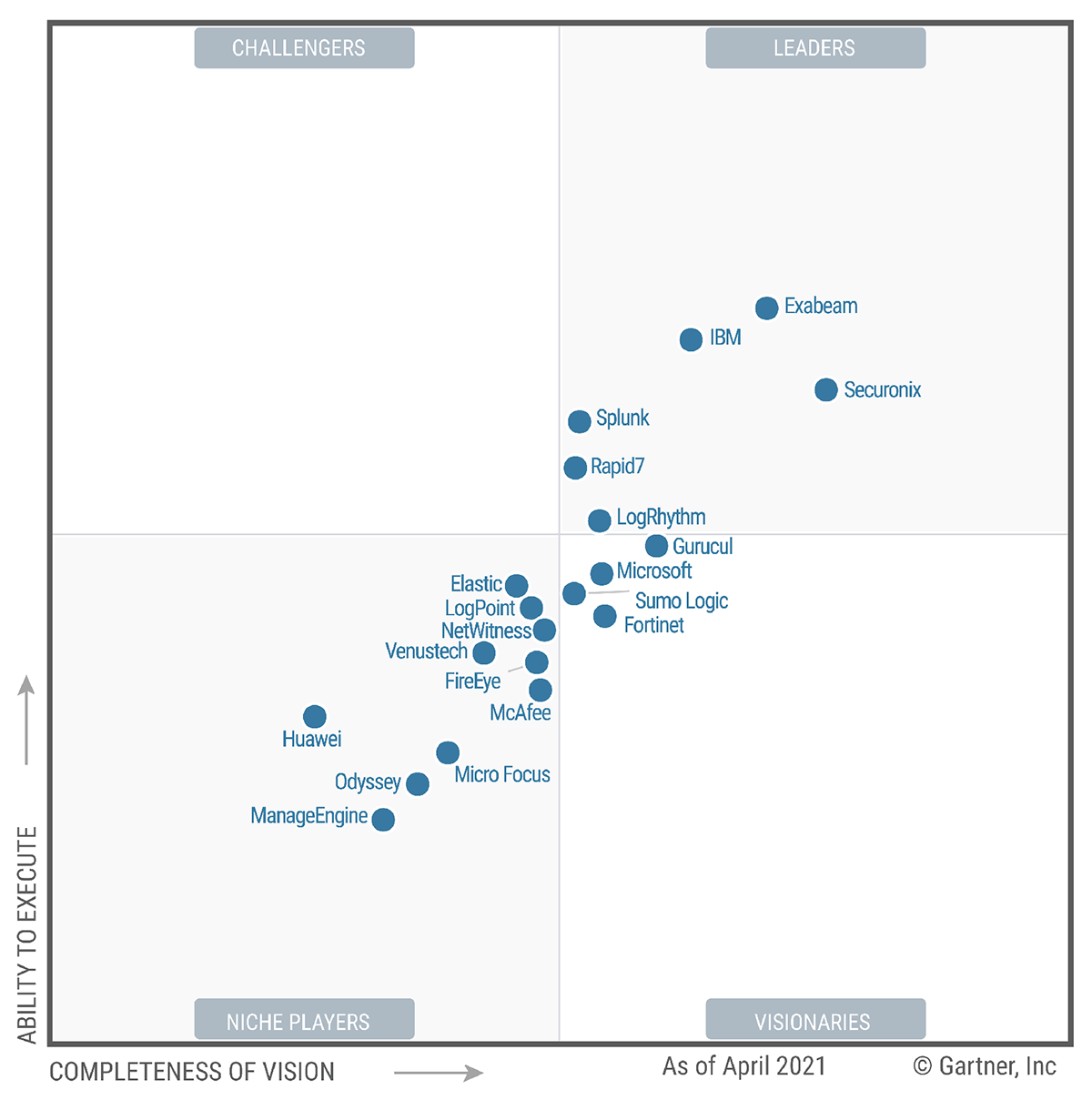
Gartner’s 2021 Magic Quadrant for SIEM report selected six solutions for the Leader’s Quadrant:
#1 – Exabeam
Exabeam Fusion SIEM, previously known as SaaS Cloud, is available as a SaaS in hybrid and local co-deployment. The solution includes components such as Advanced Analytics, Exabeam Data Lake, Threat Hunter, Case Manager, Incident Responder, Entity Analytics, Exabeam Cloud Connector, and Cloud Archive. These capabilities can be acquired separately to enhance existing SIEM products or bundled.
#2 – IBM
Offers QRadar SIEM solutions, as well as other security options such as Guardium, X-Force Threat Intelligence, Trusteer, Cloud Pak for Security, Privileged Identity Manager, Access Verification, WinCollect, QRadar Vulnerability Manager, and QRadar Network Insights.
#3 – LogRhythm
Provides a SIEM platform that includes behavior analysis for endpoints, networks, and users. The solution offers cloud-hosted deployment. However, the majority of customers deploy this platform locally.
#4 – Rapid7
InsightIDR runs on a cloud-based Insight platform. It provides additional products, including InsightVM (offers vulnerability management), InsightConnect (provides SOAR technology), InsightAppSec, Enhanced Network Traffic Analytics, and DivvyCloud (offers Cloud Security Posture Management).
#5 – Securonix
Offers next-generation SIEM, UEBA, security data lakes, SOAR, threat intelligence, NDR, and adversarial behavior analysis. It also offers use-case-specific features, such as protection for SAP and healthcare environments.
#6 – Splunk
Splunk SIEM provides products like Splunk Enterprise, Enterprise Security, Splunk Cloud, and Mission Control. High quality SOAR and UEBA capabilities are also available but cannot integrate locally with other products. You can deploy Splunk products as software or through Splunk Cloud.
About this explainer: This is part of an extensive series of guides about information security.
Key Features of Modern SIEM Systems
According to Gartner’s Critical Capabilities for SIEM report, modern SIEMs must incorporate additional technologies alongside the traditional log management, statistical analysis, alerting and reporting capabilities. New SIEMs must include:
User Event Behavioral Analytics (UEBA) – Technology that models standard behavior for users, endpoints and network devices, establishing a baseline and intelligently identifying anomalies, via advanced analytics and machine learning techniques.
Security Orchestration, Automation and Response (SOAR) – Yechnology that collects security data, prioritizes incidents, and encodes incident response in a digital workflow format, enabling automation of some or all incident response stages.
Key capabilities of modern SIEMs include:
Threat Intelligence
Combines internal data with third-party threat intelligence feeds on threats and vulnerabilities.
Data Aggregation
Collects and aggregates data from security systems and network devices.
Search, Data Exploration and Reporting
Search vast amounts of security data without reviewing raw data and without data science expertise, active explore data to discover patterns and hunt for threats, create and schedule reports on important data points.
Advanced Analytics
Uses statistical models and machine learning to identify anomalies and detect advanced threats, detect unknown threats, detect lateral movements within a network, and enrich the context of security alerts to make it easier to investigate and detect elusive threats.
Dashboards
Creates visualizations to let staff review event data, identify patterns and anomalies
Correlation, Security Monitoring and Alerts
Links events and related data into security incidents, threats or forensic findings, analyzes events and sends alerts to notify security staff of immediate issues.
Forensic Analysis
Enables exploration of log and event data to discover details of a security incident, with automated attachment of additional evidence organized in a situation timeline.
Retention
Stores long-term historical data, useful for compliance and forensic investigations. Built in data lake technology facilitate unlimited, low cost, long-term storage.
Compliance
Gathers log data for standards like HIPAA, PCI/DSS, HITECH, SOX and GDPR and generates compliance reports. Helps to meet compliance and security regulations requirements, for example by alerting about security conditions for protected data.
Threat Hunting
Enables security staff to run queries on log and event data, and freely explore data to proactively uncover threats. Once a threat is discovered, automatically pulls in relevant evidence for investigation.
Threat Intelligence
Combines internal data with third-party threat intelligence feeds on threats and vulnerabilities.
Data Aggregation
Collects and aggregates data from security systems and network devices.
Search, Data Exploration and Reporting
Search vast amounts of security data without reviewing raw data and without data science expertise, active explore data to discover patterns and hunt for threats, create and schedule reports on important data points.
Advanced Analytics
Uses statistical models and machine learning to identify anomalies and detect advanced threats, detect unknown threats, detect lateral movements within a network, and enrich the context of security alerts to make it easier to investigate and detect elusive threats.
Dashboards
Creates visualizations to let staff review event data, identify patterns and anomalies
Correlation, Security Monitoring and Alerts
Links events and related data into security incidents, threats or forensic findings, analyzes events and sends alerts to notify security staff of immediate issues.
Forensic Analysis
Enables exploration of log and event data to discover details of a security incident, with automated attachment of additional evidence organized in a situation timeline.
Retention
Stores long-term historical data, useful for compliance and forensic investigations. Built in data lake technology facilitate unlimited, low cost, long-term storage.
Compliance
Gathers log data for standards like HIPAA, PCI/DSS, HITECH, SOX and GDPR and generates compliance reports. Helps to meet compliance and security regulations requirements, for example by alerting about security conditions for protected data.
Threat Hunting
Enables security staff to run queries on log and event data, and freely explore data to proactively uncover threats. Once a threat is discovered, automatically pulls in relevant evidence for investigation.
Incident Response Support
Helps security teams identify and respond to security incidents automatically, bringing in all relevant data rapidly and providing decision support.
SOC Automation
Automatically responds to incidents but automating and orchestrating security systems, known as Security Orchestration and Response (SOAR).
SOC Pains and Required SIEM Capabilities
SIEMs have been a fundamental infrastructure of the Security Operations Center (SOC) for over two decades. However, SOC analysts experience several pains that traditional SIEMs can’t solve. Below we show how next-generation SIEM technology can solve these pains.
| Security Operations Center Pain | How a Next-Generation SIEM can Help |
|---|---|
| Alert fatigue – too many alerts to review and incidents to investigate | Next-generation SIEMs generate less alerts for security analysts to review [explain how facilitated by behavioral profiling] They can also categorize incidents based on risk reasons, incident type, and priority, enabling analysts to filter and prioritize based on risk scores and business impact. |
| Analyst fatigue due to mundane tasks | Next-generation SIEMs provide security automation via playbooks. They integrate with IT systems and security tools to automatically attach more evidence to incidents and aid investigators in closing incidents quickly. |
| Takes too long to investigate incidents | Next-generation SIEMs create a timeline that pulls together all the evidence related to a specific incident, across multiple users and organizational systems. This allows analysts to view the entire scope of an incident and its potential risks on one pane of glass. |
| Lack of skilled analysts – need to quickly train and on-board new staff | Next-generation SIEMs are easier to use and provide easy to interpret incidents packaged with ancillary information. They also allow easy ways to query and explore security data, without requiring analysts to become SQL experts or data scientists. This allows even junior analysts to assess risks, prioritize incidents, and push confirmed incidents to a next-tier analyst. |
Use Cases and Required SIEM Capabilities
SIEM technology can be employed in several use cases. Each use cases leverages different SIEM capabilities. The following table will help you understand if a SIEM tool is suitable for your organization’s use cases.
USER MONITORING
The Need:
Monitoring user activity within and outside the network
Capabilities:
- Monitoring user activity
- Privileged User Monitoring
- Baselining user activity and identifying anomalies
THREAT DETECTION
The Need:
Specialized tools to monitor, analyze and detect threats
Capabilities:
- Detecting known attack patterns, signatures, and correlations indicating an attack
- Detect unknown attack chains via machine learning and advanced analytics
SECURITY ANALYSIS
The Need:
Deriving more insights into security data from multiple sources
Capabilities:
- Statistical analysis and correlation rules
- Machine learning to establish baselines of normal activity and detect anomalies
INCEDENT MANAGEMENT
The Need:
An organized way to address and manage security incidents and alerts
Capabilities:
- Incident prioritization – understanding which incidents are particularly abnormal or dangerous
- Automated collection of evidence for investigators
- Automated response
COMPLIANCE AND SECURITY REPORTING
The Need:
Automatically verifying regulatory requirements and generating audit reports, managing data privacy and governance
Capabilities:
- PCI DSS compliance
- HIPAA compliance
- SOX compliance
- GDPR compliance
- Other standards and regulations
Evaluating SIEM Total Cost of Ownership
Procuring a SIEM involves several different costs, some of which are capital expenditures and some are operating expenditures.
A SIEM Costing Model
SIEM CAPEX Budget Items
- Licenses
- Development and integration
- Training
- Hardware and storage equipment (for on-premise SIEM)
- Periodic scaling up of hardware or storage equipment (for on-premise SIEM)
SIEM OPEX Budget Items
- Dedicated/outsourced security analysts
- IT maintenance and resource provisioning (for on-premise SIEM)
- Ongoing integration with new organizational systems
- Cloud storage and cloud-based compute resources (for hosted SIEM)
Hardware Costs and Sizing
Organizations adopting SIEM on-premise will have to provision hardware to run the SIEM. To determine how much hardware is needed, you should first estimate the number of events the SIEM needs to handle.
The number and type of servers needed is defined by event volume, as well as the storage format, your decision whether to store data locally on in the cloud, the ratio of log compression, encryption requirements, and quantity of short-term data vs. long-term data retention.
Related content: SIEM Architecture
Storage Costs and Sizing
The same calculation of Events Per Day can be used to determine the SIEM’s storage requirements. The cost of storage will depend on your SIEM deployment model:
On-premise SIEM
You will either need to setup storage infrastructure independently, and scale it up as data volumes grow. Or purchase an appliance from the SIEM vendor, but when you scale beyond the appliance’s capacity, you’ll have to manager storage yourself.
Cloud-based SIEM
There is typically a charge per data volume, to compensate the vendor for the cost of cloud storage. Check for how many days the SIEM permits you to retain data, and if there are additional retention costs.
Number of In-House Analysts
A SIEM is not valuable without security analysts who can receive and act upon its alerts. Security. Analysts are needed to:
- Review alerts and decide which are actual security incidents
- Investigate incidents by pulling together relevant information, and escalating to a higher-tier analyst for action
Analysts must be skilled and trained, preferably with a relevant security certification.
- If you use a Managed Security Service Provider (MSSP), analysts will be outsourced by the service provider, or work will be divided between in-house staff and external suppliers.
- If you use a SIEM with AI or machine learning capabilities, the tool’s intelligence is not a substitute for human analysts. You will still need analysts, but effective AI processing of security data can substantially reduce false positives, help security analysts get the data they need faster, substantially reducing analyst labor.
Compliance and Security Considerations
When purchasing a SIEM, consider which standards or regulations your organization as a whole needs to comply with (across all departments – because SIEM is a cross-organizational infrastructure.
Important to consider:
- Review the standard and map out sections which might be related to SIEM capabilities – for example, logging and reporting on failed login attempts.
- Ensure your SIEM deployment and customization makes it easy to fulfill these requirements.
- Check which compliance and audit reports you need to submit which the SIEM can generate automatically – and whether your SIEM solution of choice can generate them.
- What are the compliance requirements on the SIEM itself, e.g., which data can be saved according to GDPR?
- How will the SIEM be secured – different depending on deployment model – on-premise, cloud, MSSP.
Open Source SIEM and Build vs. Buy
There are three main options for procuring a SIEM platform. Following are some of their pros and cons.
Building an Open Source SIEM
Open source tools such as OSSIM, OSSEC and Apache Metron can provide many SIEM capabilities including event collection, processing, correlation and alerting. Some open source solutions also provide Intrusion Detection System (IDS) capabilities.
Pros
No upfront expense, simpler to implement an open source SIEM than traditional SIEM solutions.
Cons
Ongoing maintenance costs can outweigh the saving in license costs. Open Source SIEMs are not fully featured, mainly suitable for smaller deployments. No next-gen SIEM features.
Leveraging a Commercial SIEM Tool
Traditional SIEM tools from players like HPE, IBM and McAfee (now Intel Security) were the common choice of large organizations building a SOC to centralize security activity and incident response.
In recent years, new lightweight SIEM solutions have emerged, which are powerful, less expensive and much faster to implement. Three of these solutions have been featured in the Gartner SIEM Magic Quadrant 2018: Exabeam, Rapid7 and Securonix.
Pros
Enterprise grade, proven technology, most products have at least some next-gen SIEM capabilities.
Cons
License costs, SOC procedures are built around a specific solution’s processes, leading to vendor lock in.
Building a SIEM Platform In-house
The ELK stack – ElasticSearch, Logstash and Kibana – is a great starting point for building your own SIEM solution. In fact, most of the new contenders in the SIEM market are based on this stack. Can be suitable for very large organizations who need tailored capabilities, and want to integrate with previous investments in threat intelligence, monitoring or analytics.
Pros
Complete customization of all SIEM capabilities, easier integration with legacy systems and in-house security feeds. next-gen SIEM capabilities.
Cons
Very high upfront expense and an ongoing development cost to support changes and maintenance.
In-house vs. Managed SIEM
SIEMs provided and managed by Managed Security Service Providers (MSSP) are a growing trend. Managed SIEMs are making it possible for smaller organizations, which do not have sufficient full time security staff, to enter the SIEM game. There are four common SIEM hosting models:
- Self Hosted, Self Managed – A SIEM is purchased or build, then hosted in local data center and run by dedicated security staff.
- Self-Hosted, Hybrid-Managed – A SIEM is deployed in-house, typically a legacy investment, and run together by local security staff and MSSP experts.
- Self-Hosted, Hybrid-Managed – A SIEM is deployed in-house, typically a legacy investment, and run together by local security staff and MSSP experts.
- SIEM as a Service – The SIEM runs in the cloud, including data storage, with local security staff managing security processes leveraging SIEM data.
Related content: SIEM Architecture
Exabeam Fusion SIEM – with Unlimited Storage, Advanced Analytics and Automated Incident Response
Exabeam Fusine SIEM isa modern SIEM that combines end-to-end data collection, analysis, monitoring, threat detection and automated response in a single platform.
Exabeam Fusion SIEM Capabilities
Exabeam Fusion SIEM is a modern SIEM platform that provides all the next-gen SIEM capabilities defined in Gartner’s model:
- Centralized, Highly Scalable Data Storage – Inclusive visibility across your entire ecosystem ensuring no event or activity is missed.
- Guided Search and Enhanced Results – Search fields are auto-populated as you type, and enhanced view highlights key pieces of information for quick review.
- Rapid Search – Full indexing at the point of log ingestion means queries return results faster. Analyst productivity and efficiency is significantly improved as they aren’t left waiting for information indicative of a potential data breach or attack.
- Audit and Compliance Reporting – Hundreds of out-of-the-box compliance reports and dashboards eliminate the need for unwieldy spreadsheets when the auditors visit
- Flexible Integration – Pre-built connectors tightly integrate over 500 popular security and IT tools for threat detection, investigation, and response.
- Behavior-based detection – Market leading behavior analytics (UEBA) finds advanced threats like credential-based attacks, insider threats, and ransomware that are missed by other tools.
- Prescriptive, Threat-centric Use Cases – Prescriptive, end-to-end workflows and security content enable SOCs to see quick time to value and achieve successful TDIR outcomes.
- Automated Investigation – Machine-built Smart Timelines automatically gather evidence and assemble it into cohesive incident timelines that boost productivity and ensure nothing slips through the cracks.
- Response and Remediation – Guided checklists and automated response actions and playbooks reduce response times and enable consistent, repeatable workflows.
- Cloud-based Deployment – Cloud based delivery removes the operational overhead of implementing and maintaining another security program so your analysts can focus on security.
Addressing SOC Pain Points
Exabeam Fusion SIEM next-generation capabilities can help resolve the most common pain points in the modern SOC:
- Alert Fatigue – Fusion SIEM reduces fatigue by leveraging UEBA technology. It focuses analysts on alerts that represent anomalies, compared to behavioral baselines of users and network entities, and helps prioritize incidents based on organizational context.
- Analyst Fatigue Due to Mundane Tasks – Exabeam integrates with security tools and executes automated security playbooks when specific types of security incidents occur.
- Takes Too Long to Investigate Incidents – Exabeam automatically pulls in all evidence relevant to a security incident, and lays it out on an incident timeline. This provides an instant look of the incident, across multiple IT systems, users and credentials.
- Lack of Skilled Analysts – Exabeam automatically prioritizes incidents via behavioral analysis, and allows users to construct complex queries on security data using a simple drag-and-drop interface, with no need for data science or SQL expertise. This allows even junior analysts to identify important incidents and conduct in-depth investigation.
Exabeam SIEM Total Cost of Ownership
Traditional SIEM
Must replace existing log management platform.
Exabeam Fusion SIEM
Can replace existing log management platform or maintain your investment and augment it with analytics and other advanced features to improve detection, investigation and response.
Traditional SIEM
Server costs should be estimated based on estimated an Events Per Day model.
Exabeam Fusion SIEM
Exabeam Fusion SIEM is delivered from the cloud, dramatically reducing cost.
Traditional SIEM
Dedicated, expert-level in-house security staff needed to interpret and investigate SIEM alerts.
Exabeam Fusion SIEM
Prioritized, friendly risk-informed SIEM alerts with automated incident timelines – allows managing the SIEM with existing staff.
Related content: Exabeam Fusion SIEM
See Exabeam in action: Request a demo
See Additional Guides on Key Information Security Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of information security.
Security Operations Center
Authored by Exabeam
- SOC Analyst: Job Description, Skills, and Certifications
- What Is a Security Operations Center? Complete Guide
- 5 SecOps Functions and Best Practices for SecOps Success
Log Management
Authored by Exabeam
- What Is Log Management? Process & Tools
- Top 6 Log Management Tools and How to Choose
- Log Analytics: A Practical Guide
Disaster Recovery
Authored by Cloudian






