
- Home >
- Explainers >
- Zero Trust
ZTNA Solutions: Key Capabilities and 9 Options to Know in 2026
- 11 minutes to read
Table of Contents
What Are Zero Trust Network Access (ZTNA) Solutions?
ZTNA solutions provide secure remote access to enterprise applications by enforcing the “never trust, always verify” principle of zero trust, allowing only authorized users and devices to connect to specific resources based on identity and context. Key benefits include a reduced attack surface, prevention of lateral movement by attackers, and protection for hybrid workforces.
What ZTNA solutions do:
- Enforce zero trust: They apply the principle of Zero Trust, which assumes no user or device is inherently trustworthy, even those on the network.
- Per-session, per-application access: Instead of granting broad network access like a traditional VPN, ZTNA creates secure, encrypted tunnels to individual applications, allowing access only to the specific resources a user needs.
- Context-based verification: Access is granted based on dynamic, real-time evaluation of user identity, device health, location, and other contextual data.
- Hide network resources: ZTNA solutions make applications invisible to unauthorized users, significantly reducing the network’s attack surface.
What ZTNA Solutions Do
Enforce Zero Trust
Zero trust enforcement is the foundation of ZTNA solutions. These systems dismantle the traditional idea of a trusted internal network by replacing blanket trust with continuous verification. Every connection request, whether originating from within or outside the organization, is subjected to strict identity and risk validation checks. This process relies on technologies such as identity providers, multi-factor authentication, and device compliance checks to confirm each user’s legitimacy before access is allowed.
By enforcing zero trust, ZTNA solutions make it significantly harder for attackers to exploit compromised credentials or devices. Even if an attacker gains access to one system, they cannot move laterally through the network without undergoing the same rigorous checks for each new resource they attempt to reach.
Per-Session, Per-Application Access
ZTNA solutions grant access based on individual sessions and specific applications rather than network-wide permissions. Each time a user initiates a connection, the system evaluates that request independently, validating identity, device posture, and risk factors. Access to one application does not imply the right to access others, even during the same user session. This approach ensures that permissions are tightly aligned with actual needs and reduces the risk associated with overly broad access rights.
This per-session, per-application model also enhances visibility and auditing capabilities. Each access attempt is logged, making it easier to detect unusual activity or policy violations. Security teams can review granular logs to determine exactly who accessed what, when, and from where.
Context-Based Verification
ZTNA solutions go beyond static credentials by using context-based verification to assess each access request. Context includes factors such as user identity, device health, geolocation, time of access, and even behavioral analytics. For example, if a user attempts to log in from an unfamiliar location or from an unsecured device, the request may be challenged or denied based on predefined risk policies. This dynamic assessment helps prevent unauthorized access using compromised accounts or stolen devices.
Context-based controls are adaptive, automatically adjusting access requirements as environmental factors change. If the risk profile increases, such as during high-privilege actions or sensitive data access, ZTNA solutions can enforce additional security measures, like step-up authentication.
Hide Network Resources
A core function of ZTNA is to make network resources invisible to unauthorized users. Unlike traditional architectures where applications or servers may appear on the network scan, ZTNA shields these assets until successful authentication and authorization. Users can only see and connect to applications they have explicit permission to access, which significantly reduces the attack surface and prevents reconnaissance by would-be attackers.
Hiding network resources also helps prevent exploits against vulnerable services. Since resources are not exposed to the public internet or even to internal users without proper clearance, the risk of attacks like port scanning or lateral movement is minimized.
Related content: Read our guide to zero trust architecture
Notable ZTNA Solutions
1. Microsoft Entra Private Access

Microsoft Entra Private Access is an identity-centric ZTNA solution intended to replace traditional VPNs by enabling secure, conditional access to private applications, regardless of whether they’re hosted on-premises or in any cloud environment. Built on Microsoft’s global private network and zero trust principles, it ensures users can connect to resources securely from any location or device without exposing applications to the internet.
Key features include:
- VPN replacement: Enables identity-based access to private apps without relying on legacy VPNs, reducing complexity and improving security.
- Adaptive conditional access: Applies granular policies such as MFA, location-based rules, and least-privilege access, all without modifying existing apps.
- Per-app access control: Grants access on a per-application basis, limiting lateral movement and minimizing attack surfaces.
- Seamless user experience: Delivers fast, global connectivity and single sign-on (SSO) across all private resources using Microsoft’s global edge network.
- Simple configuration: Supports configuration of broad private IP ranges and FQDNs for rapid deployment and policy enforcement.
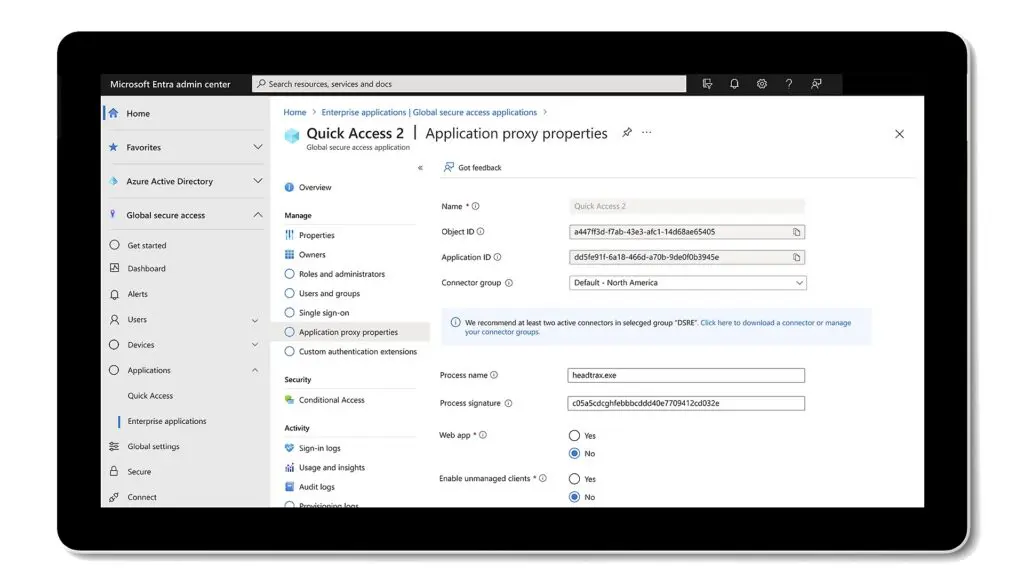
Source: Microsoft
2. FortiClient

FortiClient is a unified endpoint agent from Fortinet that combines zero trust network access (ZTNA), secure remote connectivity, and endpoint protection into a single lightweight client. Acting as a Fabric Agent, FortiClient integrates with the Fortinet Security Fabric to deliver visibility and centralized control over endpoint activity.
Key features include:
- Zero trust and VPN access: Supports universal ZTNA and encrypted VPN tunnels, applying consistent access policies for remote users across devices and networks.
- AI-based endpoint protection: Provides next-generation antivirus (NGAV), behavior-based anti-exploit, ransomware protection, and cloud sandbox integration.
- Fabric integration: Acts as a Fabric Agent to share endpoint telemetry with Fortinet’s Security Fabric, enabling coordinated response and policy enforcement.
- Centralized management: Managed through FortiClient EMS for policy enforcement, software inventory, and vulnerability monitoring.
- Cloud access security: Includes built-in CASB to manage and monitor access to cloud applications, including shadow IT visibility.
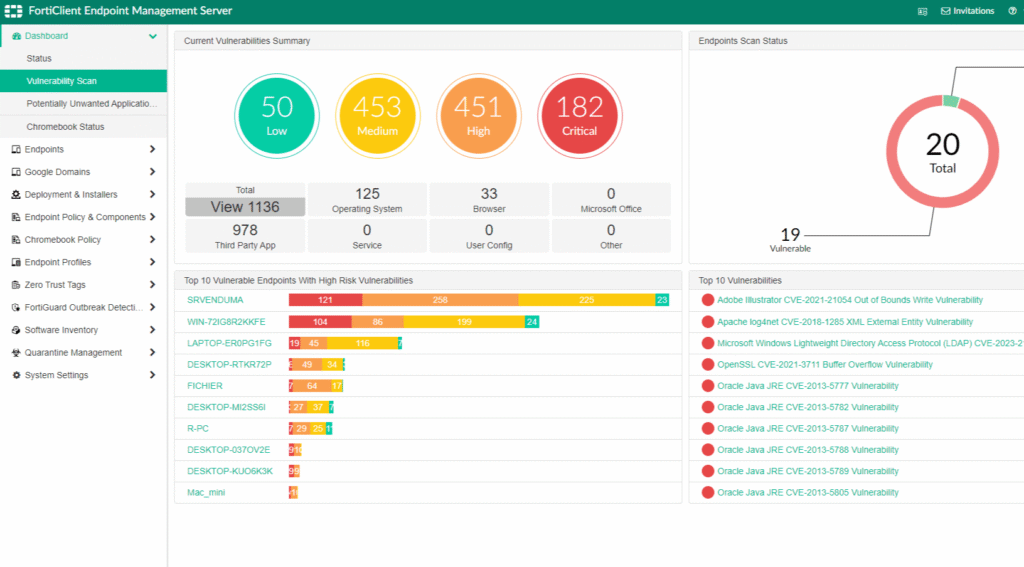
Source: Fortinet
3. Ivanti Neurons for Zero Trust Access

Ivanti Neurons for Zero Trust Access is a context-aware ZTNA solution that enforces secure, least-privilege access to private applications based on continuous evaluation of user identity, device posture, and risk level. It allows seamless access while maintaining security controls through dynamic policy enforcement.
Key features include:
- Context-aware access control: Grants application access based on real-time evaluation of device risk, user behavior, and application sensitivity.
- Dynamic risk assessment: Continuously scores device and user risk, enabling automated actions such as step-up authentication or endpoint quarantine.
- Least-privilege connectivity: Limits access to only the necessary applications, reducing lateral movement and exposure to internal resources.
- Unified client and management: Provides centralized visibility and control over VPN and ZTNA users, with a single interface for deployment, configuration, and policy management.
- Low friction user experience: Enables secure access to business-critical applications from any location or device, with minimal user disruption.
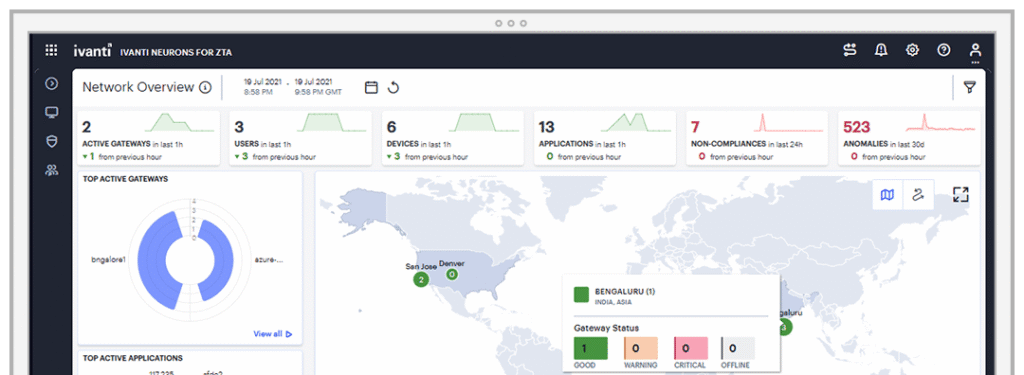
Source: Ivanti
4. Cloudflare Access

Cloudflare Access is a cloud-native ZTNA solution that enables least-privilege access to internal applications, infrastructure, and third-party tools without relying on traditional VPNs. Built on Cloudflare’s global edge network, it enforces identity- and context-based policies for each request, delivering fast, reliable access.
Key features include:
- Least-privilege access: Enforces fine-grained policies based on identity, device posture, and context for every request to internal or cloud-based applications.
- VPN replacement: Eliminates the need for legacy VPNs, providing direct, secure access to internal apps through a browser or native client.
- Simplified policy management: Uses unified zero trust policies and one-time integrations with identity providers and device management platforms to reduce setup time and complexity.
- Developer and infrastructure access: Grants secure, low-latency access to servers, APIs, and dev environments, optimized for performance-sensitive users.
- Third-party access support: Enables clientless access for contractors and partners through flexible identity options, including social identity providers.
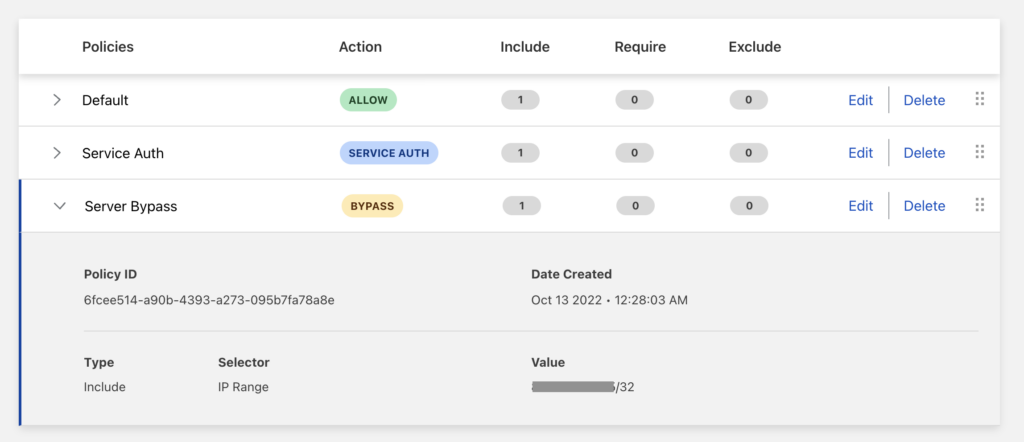
Source: Cloudflare
5. Zscaler Private Access

Zscaler Private Access (ZPA) is a cloud-native ZTNA solution that replaces legacy VPNs by delivering secure, seamless access to private applications without placing users on the network. Built on the Zscaler Zero Trust Exchange™, ZPA enforces user-to-app segmentation with context-aware policies and AI-powered app discovery.
Key features include:
- User-to-app segmentation: Grants access to individual apps, not the network, using dynamic, least-privilege policies to stop lateral movement.
- AI-powered app discovery: Uses AI to automatically identify apps and recommend segmentation policies, simplifying setup and reducing risk.
- Clientless remote access: Enables secure, browser-based access to critical systems (RDP, SSH, VNC) for remote workers and third parties without agents.
- Inline data protection: Inspects private app traffic in real time and enforces DLP policies to prevent data exfiltration and app compromise.
- Workload segmentation: Secures workload-to-workload communications across hybrid and multicloud environments, including AWS and Azure.
Source: Zscaler
6. Prisma Access

Prisma Access is a cloud-delivered ZTNA solution from Palo Alto Networks that combines secure access, user experience optimization, and threat prevention. It enforces least-privilege access to all apps and data while eliminating the need for traditional VPNs.
Key features include:
- Zero trust network access (ZTNA): Enforces secure, least-privileged access to applications while eliminating implicit trust and reducing the attack surface.
- Best-in-class threat prevention: Blocks sophisticated threats inline across users and traffic types using AI-driven analysis and real-time inspection.
- Cloud-native firewall as a service (FWaaS): Secures network traffic with integrated firewall capabilities, application control, and zero trust policies.
- Secure web gateway (SWG): Protects users from web-based threats with real-time URL filtering, content inspection, and policy enforcement.
- Cloud access security broker (CASB): Provides deep visibility and control over SaaS usage with inline and API-based protections and posture management.
Source: Palo Alto Networks
7. Cisco Universal ZTNA

Cisco Universal ZTNA delivers a unified, identity-aware approach to secure application access across environments. Built on Cisco’s networking and security convergence strategy, it provides a single client experience for ZTNA and VPNaaS. It applies continuous, context-aware verification of users, devices, and applications.
Key features include:
- Single client for all access: Combines ZTNA, VPNaaS, and application access in one client to simplify user experience and support all app types: SaaS, cloud-native, or legacy.
- Context-aware least-privilege access: Enforces precise, dynamic access policies based on user identity, device posture, application type, and inferred intent.
- Identity intelligence and threat detection: Continuously verifies behavior post-authentication to detect impostors, block threats, and adapt trust levels in real time.
- AI and IoT visibility and control: Monitors thousands of apps for AI usage and provides granular control over IoT device access using a unified policy engine.
- Built-in resilience and performance: Leverages Cisco SD-WAN, MASQUE, and QUIC protocols to maintain seamless user experience, even across lossy or changing network conditions.
Source: Cisco
8. Twingate ZTNA

Twingate ZTNA is an identity-centric remote access solution that enables secure connectivity to private resources without relying on traditional VPNs. Designed around zero trust principles, it eliminates open inbound ports, lateral movement, and network-level exposure by enforcing per-user, per-device, and per-resource authentication.
Key features include:
- Identity-first access control: Integrates directly with leading identity providers (IdPs) and supports SCIM provisioning for centralized user management and authentication.
- Context-aware policies: Applies access rules dynamically based on user identity, device posture, and contextual risk factors to enforce least-privilege access.
- Device posture enforcement: Validates endpoint compliance using native posture checks and integrations with MDM and EDR solutions before granting access.
- Universal MFA: Extends MFA, including TOTP, biometrics, and hardware security keys, to all resources, including SSH and RDP, for consistent protection.
- Elimination of network exposure: Establishes direct, peer-to-peer connections without open inbound ports, preventing unauthorized scanning and lateral movement.
Source: Twingate
9. NordLayer ZTNA

NordLayer’s zero trust network access (ZTNA) solution provides identity- and context-driven access to private applications and cloud resources from any device or location. Its ZTNA approach establishes strict access boundaries around critical assets, enforcing least-privilege access policies and continuously verifying users before granting connectivity.
Key features include:
- Identity and context-based access: Uses role-based access policies and contextual parameters like user identity, device status, and location to control access to apps and resources.
- Cloud access control: Restricts access to cloud environments by assigning specific permissions to users and applications, ensuring only verified entities reach sensitive data.
- Internal application protection: Conceals private applications from public exposure, reducing the risk of unauthorized access and targeted attacks.
- Network segmentation: Separates critical systems and user groups to prevent lateral movement within the network in the event of a breach.
- Insider threat mitigation: Limits access based on user roles and behaviors, helping to prevent misuse by internal actors or compromised accounts.
Source: NordLayer
Related content: Read our guide to zero trust solutions (coming soon)
Key Considerations When Choosing a ZTNA Solution
Organizations should look for the following factors when evaluating ZTNA solutions.
1. Support for All Users and Devices
When selecting a ZTNA solution, it is essential to ensure support for all user types (employees, contractors, partners, and guests) across both managed and unmanaged devices. Users may access company resources from corporate-issued laptops, personal smartphones, or shared workstations. A ZTNA solution provides consistent security policy enforcement, regardless of device ownership or user profile, and should accommodate bring-your-own-device (BYOD) environments without sacrificing control or monitoring.
Scalability is also key; the chosen solution should grow with your organization and maintain reliable access for a distributed workforce. This includes users working remotely, in branch offices, or traveling internationally. Device diversity and user mobility should not compromise security posture, so look for solutions offering broad compatibility, flexible policy options, and seamless onboarding for new endpoints.
2. Support for All Application Types
ZTNA should provide secure access to the full spectrum of organizational applications, whether they are web-based, legacy, SaaS, or hosted in private data centers. Enterprises often rely on a mix of modern and legacy software, and a solution that cannot support all application types risks leaving security gaps or creating complexity through parallel access methods. Ensure that your ZTNA choice is agnostic to application architecture and can integrate with diverse software environments.
Visibility and control over all application access is crucial for compliance and security management. Solutions that support granular policy enforcement and detailed logging at the application layer will help maintain compliance with industry standards and enable quick response to incidents. The ability to segment access and restrict which applications are visible to different user groups enhances both security and operational efficiency.
3. Deployment Flexibility
Deployment flexibility is a critical factor for ZTNA adoption, as organizations often operate in hybrid environments combining on-premises data centers and multiple cloud platforms. Some solutions are cloud-native, others are appliance-based, and many offer hybrid architectures. Assess whether a prospective solution can adapt to your current infrastructure and support planned changes, such as cloud migration or new remote work initiatives.
Ease of deployment affects the speed at which you can realize security benefits. Look for solutions with straightforward setup, minimal hardware requirements, and strong automation capabilities. Flexible deployment options also make it easier to pilot ZTNA in small teams or select offices before expanding organization-wide, which reduces risk and administrative burden.
4. High Performance and Low Latency
ZTNA solutions act as gatekeepers for all resource access, so any delays in authentication or data transfer can impact productivity. High performance and low latency are particularly important for organizations with real-time or high-availability requirements, such as financial services or healthcare. Prioritize solutions with optimized routing, global presence, and robust infrastructure to minimize user disruption.
Evaluate the provider’s network footprint and availability guarantees. Solutions with distributed points of presence are better equipped to deliver consistent low-latency access regardless of where users are located. Performance monitoring tools and service-level agreements (SLAs) will also help you hold vendors accountable and proactively address any issues as they arise.
5. Integration with Existing Infrastructure
Seamless integration with your existing identity, security, and network infrastructure simplifies ZTNA deployment and management. Solutions that natively support common identity providers, endpoint management platforms, and SIEM systems can reduce implementation time, lower training requirements, and avoid siloed security data. Tight integration also enables more effective enforcement of consistent policies and rapid adaptation to changing security requirements.
Consider how a ZTNA solution will interoperate with your broader security ecosystem. The best options enhance, rather than replace, current investments in areas like endpoint security, CASB, or network monitoring. API support and pre-built connectors for popular platforms can greatly simplify deployment and future-proof your access management strategy as your organization evolves.
How Exabeam Combines Zero Trust Telemetry with Behavioral Analytics to Provide a Complete View
ZTNA solutions generate detailed telemetry about application access, including user identity, device posture, access timing, and policy decisions. While this data explains how access was granted, it does not on its own explain user intent, behavioral risk, or what happened after access. Exabeam focuses on ingesting ZTNA telemetry and correlating it with broader security data to support higher-fidelity detection, investigation, and response.
Exabeam New-Scale Analytics ingests logs and events from ZTNA providers alongside identity activity, endpoint telemetry, cloud workload data, SaaS audit logs, and network signals. The UEBA engine analyzes this combined dataset to establish behavioral baselines for users, service accounts, and entities. ZTNA access events are evaluated against historical behavior, peer group norms, and current risk signals rather than being treated as isolated authentication records.
By applying behavioral analytics, Exabeam can surface access activity that technically complies with zero trust policy but is operationally suspicious. Examples include users accessing applications at atypical times, connecting from devices that show subtle risk changes, or exhibiting access patterns that deviate from established role behavior. These deviations are scored and prioritized to help analysts focus on activity that warrants investigation.
During investigations, ZTNA telemetry becomes part of an evidence-backed timeline generated by New-Scale Analytics. Access events are correlated with downstream actions such as abnormal data access, privilege use, cloud configuration changes, or endpoint activity. This provides a clear view of how a session evolved after access was granted and whether the behavior aligns with normal usage or potential misuse.
New-Scale Analytics also improves operational efficiency by reducing alert noise and contextualizing ZTNA signals within broader workflows. Rather than triggering investigations based solely on access events, the UEBA engine helps distinguish expected remote access from higher-risk behavior that spans multiple control layers. This supports more consistent triage, faster root cause analysis, and better prioritization across large volumes of access activity.
Exabeam does not replace ZTNA controls or enforce access decisions. Instead, it functions as an analytics and correlation layer that helps organizations assess the effectiveness of zero trust policies over time. By combining ZTNA telemetry with behavioral analytics and other security signals, Exabeam enables a more complete understanding of user and entity activity across identity, access, and application environments.
Learn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
-
 Blog
Blog
Exabeam Agent Behavior Analytics: First-of-Its-Kind Behavioral Detections for AI Agents
- Show More

