
Table of Contents
What Are UEBA Tools?
For enterprises, UEBA (User and Entity Behavior Analytics) tools use machine learning and advanced analytics to detect anomalous user and entity activity that traditional security tools might miss. By establishing a baseline of “normal” behavior, UEBA solutions can identify potential threats like insider attacks, compromised accounts, and data exfiltration.
Enterprises should look for the following capabilities when evaluating UEBA solutions:
- Adaptive machine learning: Uses continuously evolving ML models to establish baseline behaviors and detect deviations that signify threats, including unknown or “zero-day” attacks.
- Data ingestion and integration: Collects and analyzes vast amounts of data from diverse sources, such as logs, network traffic, and identity information. It must integrate seamlessly with an enterprise’s existing security stack, including SIEMs, firewalls, and EDR.
- Real-time monitoring and alerting: Provides continuous analysis of user and entity behavior, allowing for rapid detection and response to potential threats. Advanced tools prioritize alerts based on risk.
- Behavioral profiling and risk scoring: Creates individual and peer-group profiles to identify anomalous behavior. The solution should assign risk scores to prioritize investigation of the most critical threats.
- Forensic investigation capabilities: Stores detailed user and entity activity records and provides automated incident timelines to help security teams investigate and understand the root cause of a security event.
- Automation and orchestration: Automates response actions, such as locking a compromised account or blocking a suspicious IP address. It can orchestrate responses across other security tools to simplify the incident response workflow.
Choosing the right UEBA solution depends on your organization’s specific security needs, budget, and existing technology stack:
- Identify use cases: Determine your primary goals, such as detecting insider threats, combating data exfiltration, or improving visibility into advanced persistent threats (APTs).
- Evaluate integrations: Select a solution that works well with your current security investments, especially if you already have a SIEM, EDR, or other core platforms.
- Consider cloud vs. on-premises: Decide on a deployment model based on your organization’s infrastructure. Many modern solutions offer cloud-native platforms, while others provide on-premises or hybrid options.
- Assess AI and analytics: Look for vendors with robust and accurate machine learning and AI capabilities. Some tools are more mature and effective at identifying subtle behavioral anomalies.
- Prioritize usability: For security teams that are often overwhelmed with alerts, features like automated incident timelines and risk scoring can be critical for improving efficiency and focusing on the most important threats.
Key Features of Enterprise UEBA Tools
Adaptive Machine Learning
Adaptive machine learning is central to UEBA tools, driving their ability to detect evolving threats without constant manual updates. These systems build dynamic behavioral profiles of users and entities based on continuous data input, adjusting to shifting baselines and new patterns over time. Unlike static, rule-based systems, adaptive models can recognize nuanced deviations from normal behavior, identifying sophisticated attacks such as credential misuse or privilege escalation more rapidly.
Frequent retraining ensures that the analytics engine stays accurate as user roles, workflows, and business processes change. This learning agility allows organizations to maintain high detection rates while minimizing false positives.
Data Ingestion and Integration
Efficient data ingestion and integration with existing data sources are vital for UEBA effectiveness. These tools pull activity logs and telemetry from a diverse array of systems, including identity and access management platforms, network devices, endpoints, cloud services, and applications. Comprehensive data collection ensures that the UEBA platform has the context necessary to accurately model behaviors across the enterprise.
Integrations can be achieved through APIs, connectors, log forwarding, and support for common standards such as Syslog or JSON. The more seamless and wide-reaching the integrations, the better the system can correlate events and detect subtle indicators of compromise.
Real-Time Monitoring and Alerting
UEBA platforms deliver real-time monitoring by continuously analyzing activity data as it is generated across the network. As soon as a behavioral deviation is identified, the tool can trigger notifications and incident response workflows.
These alerts are typically prioritized according to risk, enabling analysts to focus on the most critical threats. Customizable alert rules, adaptive thresholds, and integration with security incident and event management (SIEM) systems ensure that organizations can align notification practices with their operational requirements.
Behavioral Profiling and Risk Scoring
Behavioral profiling is the method by which UEBA tools establish baselines for normal user and entity actions over time. Profiles are generated from ongoing analysis of login patterns, resource access, data movement, and other activity indicators. Each entity’s typical behavior is mapped, making it possible to flag actions that fall outside the expected range and warrant closer scrutiny.
Risk scoring mechanisms assign quantitative threat levels to activities based on severity and deviation from the baseline. This risk-based prioritization helps security teams focus their efforts on the most suspicious events. Scoring typically incorporates contextual information, such as time, location, and device type, to distinguish between benign anomalies and genuine threats.
Forensic Investigation Capabilities
UEBA tools bolster forensic investigations by maintaining detailed records of user and entity activities, contextualized with behavioral analytics. When a security incident occurs, analysts can use the historical data and behavioral context to reconstruct attack timelines, trace lateral movement, and identify the root cause of a breach.
The ability to perform rapid searches, generate intuitive visualizations, and drill down into the specifics of anomalous events is crucial for supporting both proactive threat hunting and retrospective investigations. Detailed forensic evidence aids in compliance reporting, legal response, and the refinement of detection strategies based on observed attacker techniques.
Automation and Orchestration
UEBA solutions automate repetitive tasks such as anomaly triage, case creation, and alert escalation. Through orchestration, they integrate with broader security ecosystems to trigger predefined response actions, such as user lockouts, privilege reductions, or integration with security orchestration, automation, and response (SOAR) platforms, when high risk is detected.
Automation reduces response times and lightens analyst workloads, ensuring that threats are addressed as soon as they emerge. Orchestration capabilities further improve this effect by creating unified workflows across disparate systems, improving collaboration between security tools and ensuring a consistent, repeatable response to security incidents.
Notable UEBA Tools for Enterprises
1. Exabeam

Exabeam Nova functions as a New-Scale Security Operations Platform that integrates agentic AI to enhance detection, investigation, and response workflows. It operates as a coordinated system of AI agents embedded within the platform, designed to provide a unified experience for security teams.
Enterprise features include:
- Unified security operations platform: Integrates agentic AI for detection, investigation, and response within a single console, aiming to eliminate the need for separate tools and reduce disjointed workflows.
- Accelerated security workflows: Automates tasks such as evidence collection, triage, and case creation, with the goal of reducing mean time to detect (MTTD) and mean time to respond (MTTR).
- Posture insights and framework alignment: Offers daily posture insights through an Advisor Agent, mapping detections to established security frameworks such as MITRE ATT&CK and providing recommendations for improvement over time.
- Enhanced program visibility: Provides quantifiable outcomes and posture reporting, aiming to offer security leaders clearer oversight and understanding of their security programs.
- Increased analyst efficiency: Seeks to improve analyst productivity by automating repetitive tasks and offering guided workflows, thereby assisting analysts at various skill levels.
Behavioral analytics capabilities within Exabeam Nova include:
- Risk-based prioritization: Aims to reduce the volume of irrelevant alerts through risk-based prioritization, allowing security teams to focus on incidents with higher severity.
- Behavioral baselining and anomaly detection: Establishes behavioral baselines across users, entities, and AI agents to identify subtle deviations that may indicate compromise.
- Adaptive risk scoring: Applies dynamic risk scoring to events, correlating them into threat timelines to prioritize significant alerts for investigation.
- Comprehensive behavioral analysis: Detects subtle deviations from normal behavior, encompassing activities across users, entities, and AI agents.
Splunk UBA

Splunk user behavior analytics (UBA) strengthens enterprise defenses by applying unsupervised machine learning to detect anomalous behavior that indicates insider threats, account compromise, or attacks. Instead of relying on static rules, it establishes baselines of normal user, device, and application activity, then highlights deviations that suggest malicious intent.
Enterprise features include:
- Native integration with enterprise security: UEBA is built into Splunk Enterprise Security, aligning behavioral analytics with SIEM, SOAR, and agentic AI in one console.
- Unified detection and response workflows: Integration centralizes investigation views and connects UEBA insights with correlation rules to streamline triage and incident handling.
- Automated risk-based prioritization: Dynamic scoring ranks entities and events by risk, reducing alert fatigue and focusing analyst effort on higher-severity behaviors.
- Correlated visibility across systems: Aggregates behavioral signals from users, devices, endpoints, and cloud applications to reveal patterns that span multiple environments.
- Context-rich analyst views: Enriches alerts with peer comparisons, history, timelines, and heat maps to support faster decisions during investigations.
UEBA features include:
- Behavioral baselining and learning: Continuously models normal user and entity activity, surfacing subtle deviations that indicate insider misuse or advanced attack techniques.
- Per-entity risk scoring: Aggregates heterogeneous indicators into dynamic risk scores for users and devices to prioritize investigations and reduce low-value alerts.
- Multi-entity attack correlation: Connects related behaviors across systems to expose lateral movement, privilege abuse, and coordinated activity chains.
- Automated anomaly detection: Uses multiple machine learning models to monitor for emerging threats and automatically rank detections by risk severity.
- Contextualized threat insights: Provides enriched metadata and peer group comparisons to explain why activity deviates from baseline during alert review.

Source: Splunk
Microsoft Sentinel

Microsoft Sentinel integrates user and entity behavior analytics to detect anomalous behavior by building dynamic baselines of users, devices, and applications across the enterprise. Instead of only collecting logs, it applies machine learning to identify deviations from normal patterns, comparing individuals to their own history, to peer groups, and to the wider organization.
Enterprise features include:
- Unified Defender portal operations: Sentinel is available in the Microsoft Defender portal, consolidating security operations without requiring Defender XDR or E5 licensing.
- Entity context synchronization: Synchronizes Microsoft Entra ID and optional on-premises Active Directory (preview) to populate user profiles in the IdentityInfo table.
- Behavior analytics data access: Exposes BehaviorAnalytics and UserPeerAnalytics tables for KQL queries and advanced hunting across entities and anomalies.
- Built-in investigation content: Includes hunting queries, exploration queries, and a UEBA workbook to visualize anomalies and support investigations.
- Security-driven analytics alignment: Prioritizes use cases aligned with MITRE ATT&CK and selects data sources accordingly to focus on relevant attack vectors.
UEBA features include:
- Dynamic behavioral baselines: Learns normal activity for users, hosts, IPs, and applications over time, comparing entities to themselves, peers, and the organization.
- Investigation priority scoring: Assigns 0–10 scores to activities based on abnormality relative to user and peer behavior to prioritize analysis.
- Contextual anomaly evaluation: Flags deviations across geography, device, environment, time, and frequency with clear artifacts explaining why actions differ from baseline patterns.
- Peer group analytics: Calculates and ranks peers using signals like security group and mailing list membership, normalizing weights with TF-IDF.
- Asset sensitivity and blast radius: Estimates asset sensitivity and potential impact to help prioritize investigations and incident handling decisions more effectively.

Source: Microsoft
Varonis

Varonis delivers data-centric UEBA that focuses on protecting sensitive information from insider threats, ransomware, and persistent attacks. By continuously monitoring data activity across platforms, Varonis establishes behavioral baselines for users and devices, detecting anomalies such as unusual file access, privilege escalation, or geo-hopping.
Enterprise features include:
- Continuous data monitoring: Continuously observes data, activity, and events to surface threats like APTs, malicious insiders, and public exposures before escalation.
- Managed detection and response: Offers 24x7x365 Managed Data Detection and Response with a defined ransomware service-level target and incident response expertise.
- SIEM and SOAR integrations: Connects via native connectors to Splunk, QRadar, Cortex XSOAR, and Google Chronicle, as well as syslog and SNMP.
- Cross-platform risk coverage: Monitors data across environments to track abnormal access, lateral movement, and privilege escalation affecting sensitive information.
- Data detection and response workflows: Combines threat models with incident responder analysis to identify and contain stealth and insider threats.
UEBA features include:
- Per-user and device baselining: Builds behavior profiles for every user and device to detect unusual file access, email activity, and permission changes.
- Threat model breadth: Applies hundreds of machine learning threat models to identify ransomware behaviors, insider misuse, and advanced persistent techniques.
- Anomaly indicators and telemetry: Flags geo-hopping, abnormal access patterns, and privilege escalation using data-centric signals across platforms and services.
- Data exfiltration detection: Detects uploads, downloads, link sharing, and indicators of command-and-control in DNS, proxy, and VPN traffic.
- Focused data-centric analytics: Emphasizes telemetry tied to sensitive data rather than endpoint- or network-centric signals to surface relevant risks.
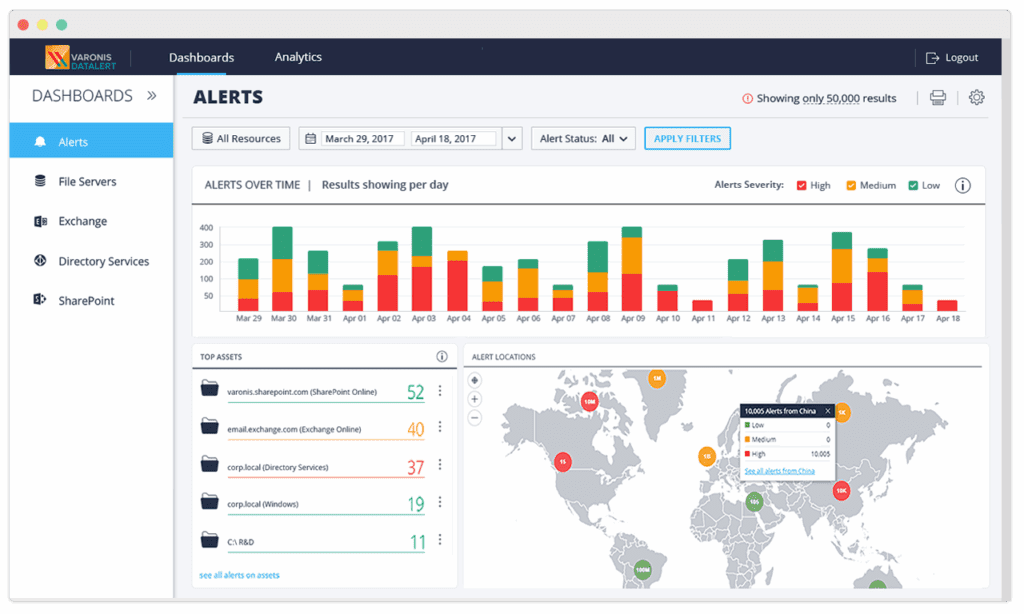
Source: Varonis
Securonix

Securonix delivers UEBA solutions that use machine learning and behavior analytics to detect insider threats, account takeovers, and unknown attacks with minimal noise. By analyzing both real-time events and historical behavior, Securonix distinguishes between legitimate user actions and malicious activity, providing security teams with alerts.
Enterprise features include:
- Cloud-native deployment model: Delivers UEBA as a cloud service with zero infrastructure to manage and rapid rollout across environments.
- Extensible to existing SIEM: Integrates on top of legacy SIEM deployments, avoiding rip-and-replace while enhancing detection and investigation workflows.
- Cloud coverage via built-in APIs: Extends monitoring to major cloud infrastructure and application platforms using built-in native connectors and APIs.
- Operational accelerators: Provides pre-built use cases, turnkey analytics, connectors, and case management workflows to support investigations and response.
- Pre-built use case content: Ships with one-click content for insider threats, IP theft, fraud, and additional scenarios to enable immediate access and use.
UEBA features include:
- Advanced behavior analytics: Uses machine learning and behavior analytics to distinguish legitimate operations from threats by combining real-time signals with historical behavior context.
- Peer group analysis: Automates anomaly detection by baselining user activities against peers to reduce noise from expected role-based differences.
- Threat chain modeling: Maps detections to MITRE ATT&CK and US-CERT frameworks to identify low-and-slow, multi-stage attack progression patterns.
- Noise reduction focus: Emphasizes pre-built analytics and risk profiling to lower false positives while maintaining coverage of user and entity threats.
- Cloud-focused monitoring: Extends behavior analytics into cloud environments using APIs for major cloud infrastructure and applications directly.
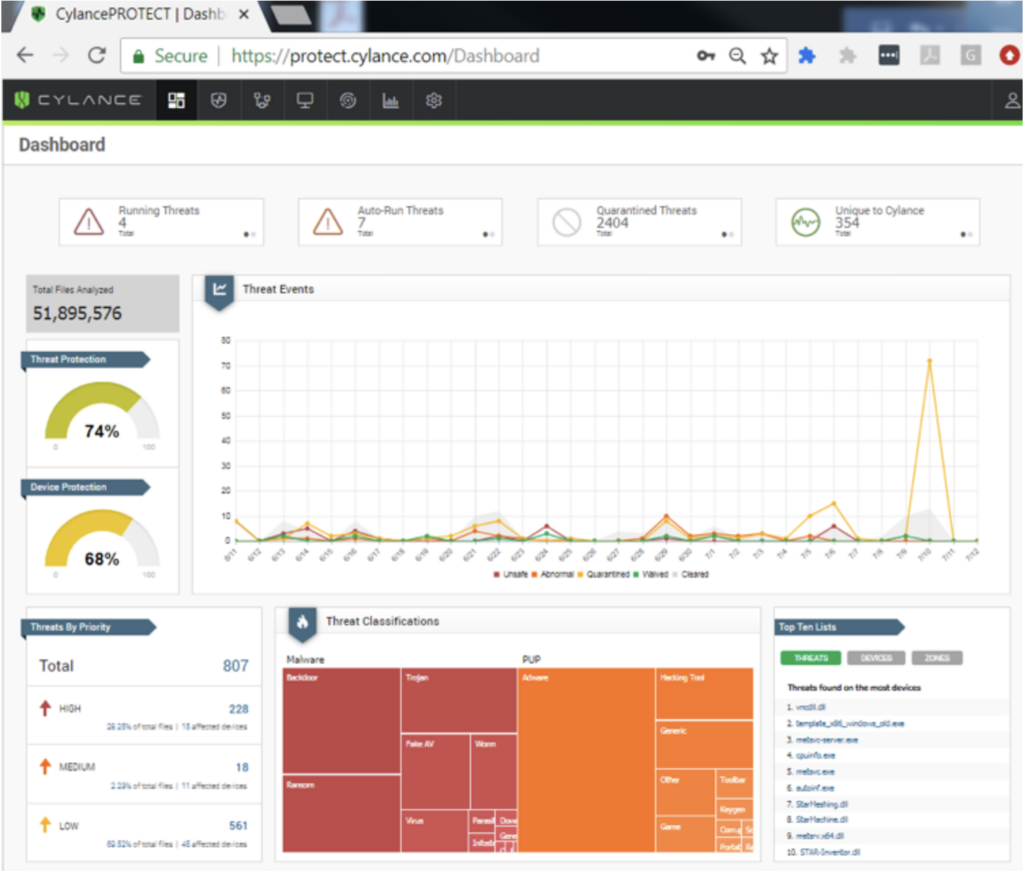
Source: Securonix
How to Select a UEBA Tool for Your Enterprise
Organizations should consider the following when evaluating UEBA tools.
1. Identify Use Cases
Clearly defining primary use cases is the first step in selecting an appropriate UEBA tool. Organizations should determine whether they need to focus on insider threat detection, account compromise prevention, privileged user monitoring, or regulatory compliance. Each use case involves different data sources, analytics requirements, and integration points, shaping the feature set required from the UEBA platform.
Understanding the specific problems to solve will guide investment decisions and ensure that the selected tool delivers measurable security value. Involving stakeholders from security operations, compliance, and business units ensures all critical risk scenarios and operational needs are accounted for.
2. Evaluate Integrations
Effective UEBA tools must support broad and seamless integration with existing enterprise IT and security ecosystems. Before making a selection, organizations should verify that candidate platforms can ingest data from directory services, SIEM systems, network and endpoint monitoring tools, cloud applications, and identity providers. The depth and flexibility of integration capabilities will determine how complete and actionable behavioral analytics will be.
Pilot projects or proof-of-concept integrations are useful for confirming real-world compatibility, data enrichment, and interoperability with other security technologies. Compatibility with APIs and event standards, as well as vendor support for custom connectors, should be closely evaluated.
3. Consider Cloud vs. On-Premises
The deployment model is a critical decision when choosing a UEBA tool. Organizations need to assess whether a cloud-based solution, on-premises deployment, or hybrid approach aligns best with their security requirements, regulatory constraints, and IT infrastructure. Cloud solutions offer scalability and reduced maintenance burden, while on-premises installations may be required where stringent data residency or privacy regulations apply.
Cost, speed of deployment, update cycles, and integration with other cloud or on-premises resources also influence the optimal deployment choice. Enterprises with highly distributed environments or rapid business growth often favor SaaS models for their flexibility and easy scalability. Organizations with mature, tightly controlled environments may opt for on-premises solutions to maintain maximum oversight and control.
4. Assess AI and Analytics
The depth and quality of a UEBA tool’s analytics engine directly affect its threat detection capabilities. Enterprises should evaluate the sophistication of machine learning models, the ability to adapt to unique organizational environments, and the transparency of anomaly detection results. Tools should support contextual risk analysis, weighing behavioral anomalies against business context to reduce false positives and highlight real threats.
Vendor claims about AI capabilities should be validated through testing and by reviewing documented detection methodologies. Support for custom analytics and ongoing tuning also plays a role, as each environment’s threat landscape evolves.
5. Prioritize Usability
User experience is often overlooked but essential for maximizing the value of a UEBA implementation. Tools should offer intuitive dashboards, straightforward workflows, and actionable alerts that do not require steep learning curves. Efficient case management, guided investigations, and clear reporting features allow analysts at all experience levels to identify and respond to threats efficiently.
Pilot programs, user feedback, and vendor demonstrations help evaluate the practical usability of a solution in daily operations. A tool that simplifies incident response and prioritizes relevant information accelerates threat resolution and allows security teams to focus on high-priority incidents. Usability should be balanced with feature depth, ensuring the tool remains accessible.
Conclusion
UEBA tools provide enterprises with a behavior-focused approach to security, helping detect threats that traditional systems miss. By combining machine learning, contextual analytics, and risk-based prioritization, they enable security teams to identify anomalies quickly, investigate incidents more effectively, and respond with greater confidence. This makes UEBA a critical layer in modern enterprise defense strategies.
Learn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
-
 Blog
Blog
Exabeam Agent Behavior Analytics: First-of-Its-Kind Behavioral Detections for AI Agents
- Show More

