Prepare for Your Future With AI-Driven Security Operations
Industry-leading AI and automation optimized for TDIR
Experience the world’s most advanced cloud-native security operations platform, powered by AI to deliver superior threat detection, investigation, and response (TDIR).
Leading the Way with AI-Driven
Security Operations
Pinpoint the Highest-Risk Threats
AI detections fill the gaps of point solutions and legacy SIEM tools by learning normal behavior, correlating alerts, scoring risks, and dynamically prioritizing threats for analyst review.
Enable Faster, More Accurate Investigation and Response
Persona-based workflows apply AI to deliver automated threat timelines, impact analysis, and natural language search to arrive at answers and decisions faster.
Improve Threat Coverage
A guided process maps data to prepackaged use cases and MITRE ATT&CK® content, and provides recommendations to improve threat coverage and meet strategic outcomes.
Detect. Defend. Defeat.™
Over 90% of breaches are rooted in compromised credentials1 and most security tools can’t help. Exabeam® offers a breakthrough combination of capabilities that security teams needs in products they will want to use. Advance your security operations: detect threats, defend against cyberattacks, and defeat adversaries with Exabeam.
1 2022 Verizon DBIR
The Leading Platform for TDIR
Realize the full potential of security operations with the cloud-native Exabeam Security Operations Platform:
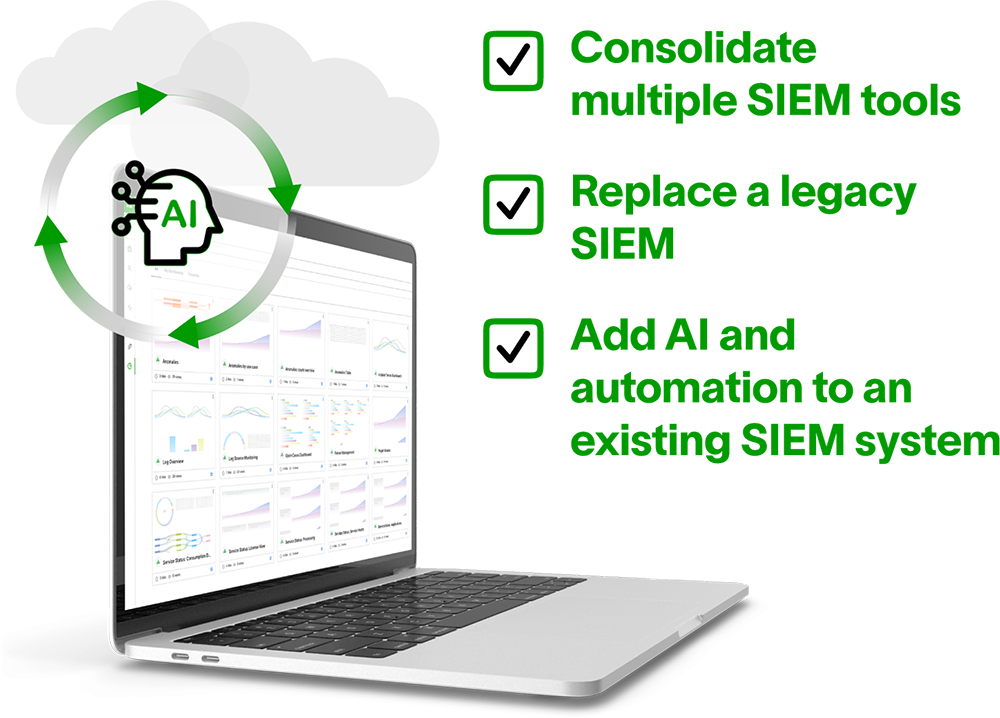
Get Started
Replace a SIEM
Exabeam Fusion >
Augment a SIEM with AI
Exabeam Security Investigation >
pre-built parsers
As it is ingested, data is parsed using over 9,500 pre-built log parsers and enriched using context sources from open source and commercial threat intelligence feeds.
anomaly rules
Over 1,800 anomaly rules, including cloud infrastructure security, with over 795 behavioral models that automatically baseline normal behavior of users and devices.
events per second
Rapid log ingestion processing at a sustained rate of over 2M EPS.
CLOUD-NATIVE ARCHITECTURE
Speed and scale without limits
Cloud-native architecture for rapid data ingestion and lightning-fast query performance securely ingests, parses, stores, and searches data at scale while continuously processing 2M+ EPS.

THE LEADING AI-DRIVEN PLATFORM
Powerful behavioral analytics and automation
10+ years experience delivering AI to the SOC. The only solution that learns normal behavior to detect advanced threats, including lateral movement and changes in devices, IP addresses, or credentials.

AN OPEN PLATFORM FOR TDIR
Complements best-of-breed security investments
Supports 300+ on-prem, 30+ cloud security, and 20+ cloud infrastructure products, including 10+ SaaS apps. Transport options: APIs, agents, syslog, and log aggregators. 9,500+ pre-built parsers from 674 products. Gain 576 SOAR actions with 65 vendor integrations.
CONTEXT ENRICHMENT
Deeper insights added to your data
Threat intelligence enhances detection through IoC, file/domain/IP/URL reputation, and TOR endpoint ID enrichment. Geolocation refines accuracy with location context. User-host-IP mapping adds details to logs, critical for building behavioral models.
What outcomes are you looking to achieve?
The Exabeam Security Operations Platform supports TDIR best practices with a use case approach for external and insider threats. Pre-built content streamlines workflows and Outcomes Navigator maps logs to use cases and ATT&CK, identifying coverage gaps and providing actionable recommendations.
Trusted by organizations
around the world





















“Since we’ve had Exabeam on board, the visibility, detection, and rich feature set has given us a different lens with a huge amount of context around an incident, which has informed our decision making and led to faster response times.”
Lindbergh Caldeira
Security Operations Manager | SA Power Networks

Learn more about the Exabeam Security Operations Platform
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.

DATA SHEET
The Exabeam Security Operations Platform
Whether you replace a legacy product with a New-Scale SIEM, or complement an ineffective SIEM solution by adding the industry’s most powerful user and entity behavior analytics (UEBA) and automation to it, the Exabeam Security Operations Platform can help you achieve security operations success.

GUIDE
How Exabeam Solves for TDIR Challenges
Exabeam redefines the approach to TDIR with an innovative workflow designed to improve SOC efficiency and efficacy. By integrating rapid data ingestion, a cloud-native data lake, lightning-fast query performance, powerful behavioral analytics, and AI-driven automation, Exabeam shifts cybersecurity from reactive to proactive.
REPORT
Gartner®️ Report: Hype Cycle™️ for Security Operations, 2023
The Hype Cycle for Security Operations, 2023, is research that aids in evaluating the risks and rewards of investing in specific Security Operations features. It provides graphic representation of the maturity and adoption of technologies and applications, and how they are potentially relevant to solving real business problems and exploiting new opportunities.
See the Exabeam Security Operations Platform in action.
Request a demo of the industry’s most powerful platform for threat detection, investigation, and response (TDIR). See how to:
• Ingest and monitor data at cloud-scale
• Determine abnormal user and device behavior
• Automatically score and profile user activity
• View pre-built incident timelines
• Use playbooks to make the next right decision













