New-Scale SIEM Brings Powerful Behavioral Analytics and Automated Investigation to Threat Detection, Investigation, and Response

Co-authored with Sanjay Chaudhary
Exabeam built New-Scale SIEM to solve the numerous challenges and limitations of legacy security information and event management (SIEM) and to provide security operations teams breakthrough capabilities to detect and respond to a wide range of threats.
The three pillars of New-Scale SIEM are:
- Cloud-scale security log management
- Powerful behavioral analytics
- Automated investigation.
This blog post will focus on the last two pillars and how Exabeam can bring analytics and automation to the security operations center (SOC) to scale the threat detection, investigation, and response (TDIR) capabilities of any organization — whether they are looking for a new SIEM, or a way to get more value out of their existing SIEM.
Analytics and automation go hand in hand, and there are many cases where analytics can provide powerful automation and save SOC analysts precious time. An excellent example is the ability Exabeam has to learn what is normal and display this information for every user and device in an organization’s environment. Without these powerful analytics, it is up to an analyst to determine this normal behavior across a wide array of behaviors and logs every time they start an investigation. Exabeam believes that automation is not just the last mile of the TDIR process but should be provided throughout the entire TDIR lifecycle. Automation is not just about taking a response action. Still, it can be vital in providing the proper decision support at the right time for an analyst to be able to do their job as effectively and efficiently as possible.
In this blog post:
- Threat detection analytics and automation
- Triage analytics and automation
- Investigation analytics and automation
- Response analytics and automation
Threat detection analytics and automation
Exabeam provides a tremendous amount of integrated security content to help customers automate their threat detection capabilities. Exabeam ships with more than 1,900 pre-built detection rules to cover the most common threats, including external threats, compromised insiders, and malicious insiders. This also includes the latest content pack, TDIR for Public Cloud. This content is heavily focused on identifying anomalous behavior after establishing a baseline. In most organizations, threat detection is highly manual and requires content engineers to predict how they will be attacked and author correlation rules with static thresholds that apply to the entire organization. Exabeam takes a different approach by leveraging more than 750 pre-built data models to learn what is normal for every user and device in the environment. This is equivalent to writing 750 unique correlation rules for every user and device in an organization. If we do some quick math for an organization with 5,000 users and 10,000 devices, that would be like authoring and maintaining more than 11 million correlation rules set with unique thresholds.
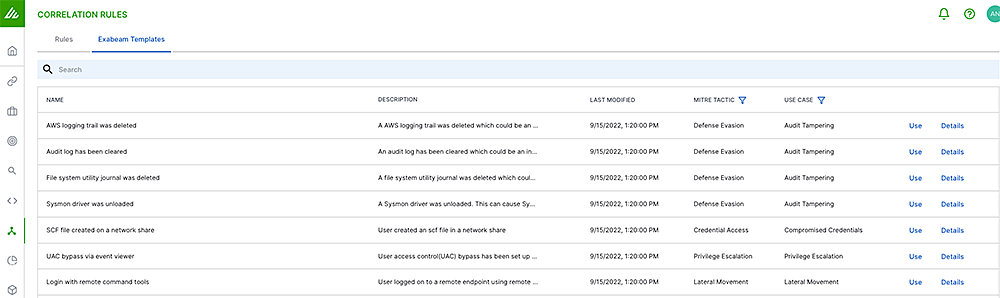
New-Scale SIEM offers a powerful Correlation Rules application for those times when you know exactly what you are looking for. Organizations can create logic or leverage Exabeam Pre-built Correlation Rules. Exabeam can help automate the triage and investigation workflows by providing content engineers with the ability to set multiple outcomes for a single rule — whether they want a case to be created for the most critical alerts, or to simply add risk into a Smart TimelineTM and let the analytics automatically correlate and evaluate this rule alongside other third-party alerts and anomalous behavior. This gives organizations more control over the triage, investigation, and response process for the rules they define.
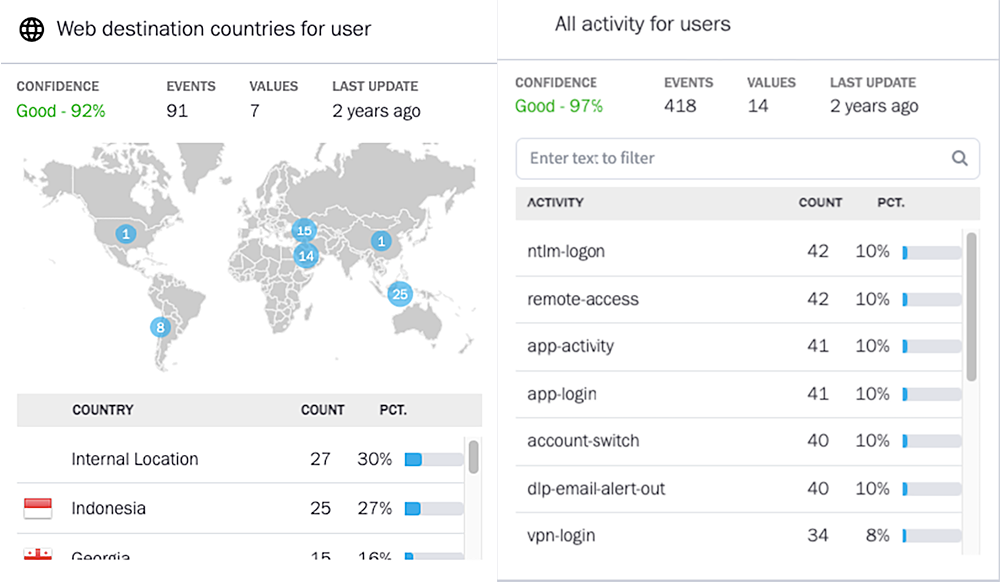
Threat hunting is another key threat detection capability offered by New-Scale SIEM. The threat hunting process often starts with a hypothesis regarding a known threat or the validation of controls and coverage of existing threat detection content. Many threat hunters leverage a SIEM to query their data to look for outliers and anomalies that might indicate something suspicious is occurring. Take, for example, trying to identify if a server is infected with malware and communicating to a C2 domain/IP. If the domain is static and known, it is simple for the threat hunter to search for that domain name in the new Search feature and find the infected server. However, if the domain is dynamic, the hunter might need to first find machines communicating with new domains or IP addresses that it has never communicated with before. Locating first-time IP connections is something the hunter could do by running queries against raw log data and doing their own analysis, or they could leverage the power of Exabeam Advanced Analytics to help automate the time-consuming part of this task. Now a hunter can leverage Exabeam Anomaly Search to query for “Abnormal access to an internet IP address in this country” OR “First access to this domain through a network which has been identified as DGA”. Anomaly Search automates the steps of first identifying these anomalous behaviors and provides the hunter the ability to spot these threats much more rapidly.
Lastly, context enrichment automation is critical for threat detection, but also for the rest of TDIR. Exabeam offers the ability to enrich data with both static and dynamic context to power threat detection. A simple example of static context enrichment would be how Exabeam automatically enriches all data ingested with Exabeam Threat Intelligence Service to make it fast and easy to detect known indicators of compromise (IOCs) and hunt for them. Exabeam also provides a ton of enrichment to each log through the Exabeam Common Information Model (CIM) and event-building process. The CIM enriches every log with new data like subject, platform, and landscape, which identifies and categorizes data fields that can be used to quickly build correlation rules that span multiple security products and logs. Static context enrichment is a great place to start, but Exabeam takes this a step further by leveraging analytics to derive new context about an environment and keep this context up to date. A good example of this would be our personal email address machine-learning algorithm, which will learn and identify which personal email addresses are tied to employees. This is context that would be difficult to obtain otherwise and is used to power pre-built content to detect malicious insiders.
Triage analytics and automation
Triaging alerts is one of the most common workflows in any SOC. The challenges today are the sheer number of alerts generated from the multiple security tools most organizations have deployed, and the lack of context provided by a single alert. New-Scale SIEM can address these challenges by providing automation and analytics via Exabeam Alert Triage. The first major challenge with the triage process is the lack of context from a single alert. Alert Triage solves this by providing real-time, dynamic context related to entities involved in an alert, including the user and host(s) involved. Contextual alerts help the analysts to quickly understand if there are critical users or devices related to an alert, or if the users or devices have a high amount of risk associated with them. The second step in triage is typically to understand if there were other alerts or signals around the alert being investigated. Alert Triage will automatically provide insights into the nearby anomalies and alerts so that an analyst doesn’t need to hunt for this information. This kind of context automation and enrichment is critical for an analyst to be able to make fast decisions to escalate or dismiss an alert.
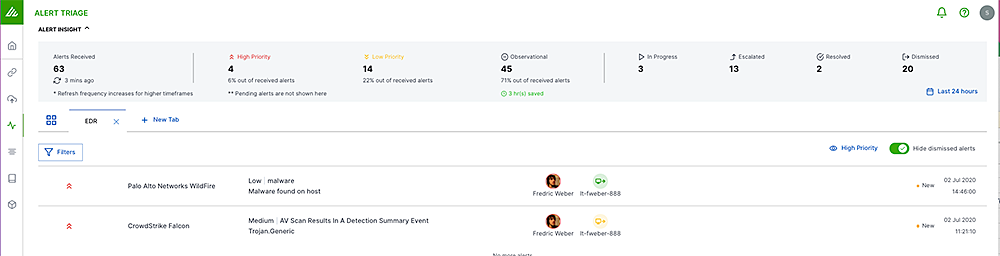
In some cases, context enrichment and automation are not enough, and critical alerts are still slipping through the cracks due to the overall volume. Many organizations are forced to focus on the “high” or “critical” alerts based on the way the vendor classifies them. However, we have all seen breaches where attackers were able to maintain persistence in environments while tripping detections because they were classified as “low.” Exabeam built the Dynamic Alert Prioritization engine to solve this specific problem. Dynamic Alert Prioritization analyzes each third-party alert and uses machine learning to increase the alerts’ priority based on the rarity of that alert, or decrease its priority. This helps organizations surface low or medium alerts as critical that would have otherwise not been looked at.
Investigation analytics and automation
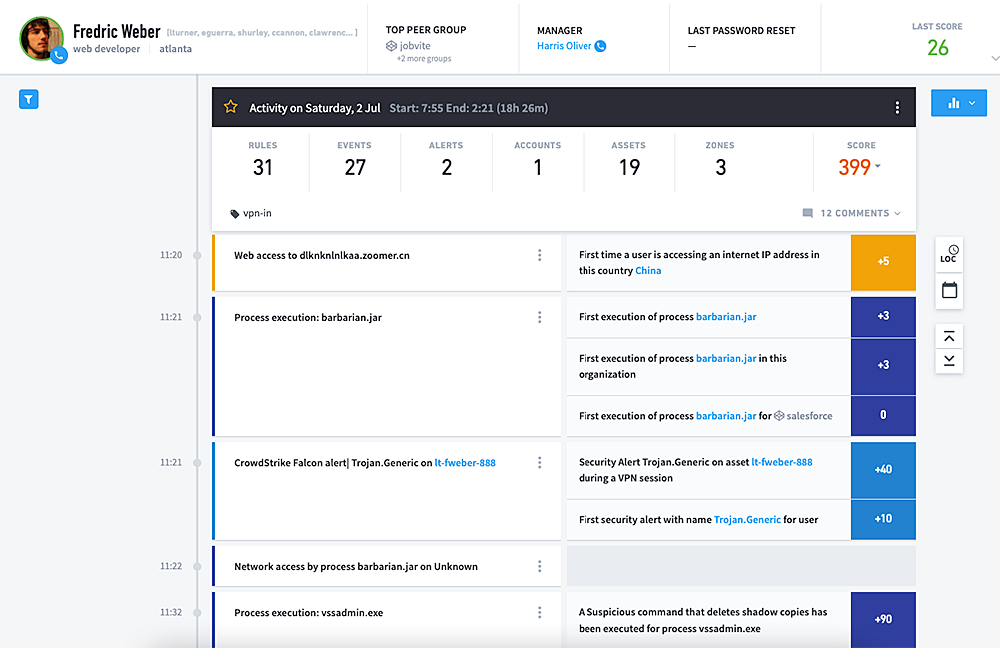
One of the most critical and time-consuming parts of the TDIR workflow is the investigation. If an analyst cannot perform a comprehensive investigation and understand the complete picture of a threat, this will lead to incomplete response and remediation. Too often, I see organizations respond to a malware alert by simply re-imaging the infected host without understanding how the machine got infected and what happened after the infection occurred. This is like playing Whac-A-Mole with these alerts, since a full investigation and the proper response was not performed. Exabeam Smart Timelines were designed to automate the investigation process by stitching together all the behavior of a user or device into a chronological timeline and identifying any third-party alerts or anomalies within the timeline. This gives an analyst the full story of what happened throughout an entire threat, not just a piece of it. These Timelines can save analysts hours investigating in other tools or writing several hundreds of queries to recreate the scene of the crime and understand the full picture to perform the right response actions.
Response analytics and automation
The final phase of the TDIR workflow is response, which is key to closing the risk of security threats to an organization. Many organizations make the mistake of only focusing their automation efforts on response. As I explained above, it is important to understand and leverage analytics and automation across threat detection, triage, and investigation to provide the right information about a threat so that the response automation can be comprehensive and more targeted. Once a threat is found, Exabeam response automation will automatically classify incidents based on the anomalies and rules found for a given entity. Once classified, Exabeam Turnkey Playbooks can automatically get executed to perform actions against third-party tools to gather more evidence and context or take response actions. A good example of this is to automatically run the Malware Playbook to sandbox malware to validate the threat, then automatically block that hash or file from running on all other hosts.
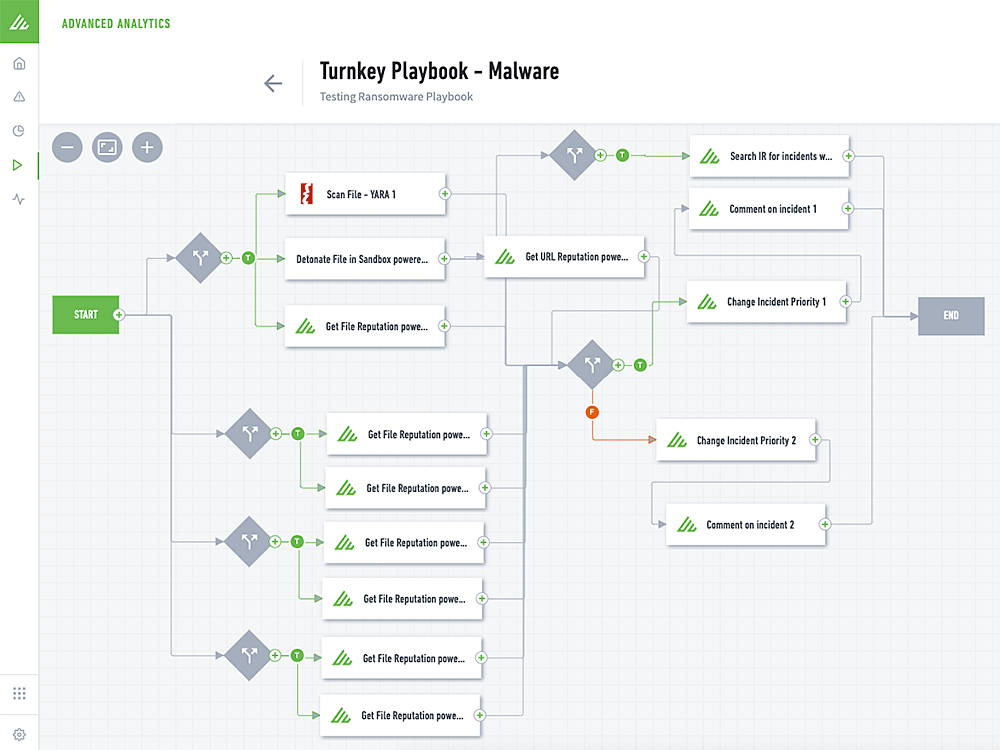
Analytics and automation are all about providing analysts with the right information at the right time throughout the TDIR workflow. New-Scale SIEM offers many unique capabilities leveraging analytics, machine learning, and a robust service and action library to deliver the most comprehensive automation to help scale the capabilities of any SOC.
Learn more: Discover New-Scale SIEM.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!










