What is threat hunting?
Threat hunting takes a proactive approach to cybersecurity. A threat hunting workflow starts with a hypothesis or strange occurrence, and requires asking questions of your data repository to detect and isolate advanced threats. These can stem from events that have appeared in the news, or even curiosity about a MITRE ATT&CK® tactic if you want to understand your security posture.
Threat hunting involves continuously searching security data for patterns and anomalies in an attempt to discover threats that have evaded existing security tools. Many analysts run manual, query-based searches within a security information and event management (SIEM) solution to find adversaries. However, these searches require a deep understanding of the specific threats being searched for and often a knowledge of a specific query language or even Snort rules, thus relegating the activity to seasoned analysts. Once a threat is discovered, they often must perform tedious and inefficient investigation processes, which makes it difficult to quickly understand the scope of the threat and identify users or entities that may have been compromised.
Protecting your business from security threats on an ongoing basis requires threat hunting. By threat hunting, you can reduce the time between intrusion and discovery to minimize the damage from an attacker. Exabeam offers two starting points for threat hunting: Anomaly Search and Advanced Analytics.
- Anomaly Search offers an interface to search for Exabeam-triggered events across the data repository. Through a drop-down menu, a threat hunter can construct queries across a variety of different objects such as sessions, rules, users, assets, ATT&CK TTPs, and anomaly identification.
- Threat Hunter offers a drop-down menu to search for abnormal behaviors in an environment, which may be indicative of threat. Threat hunters can string together conditions from contextually enriched menus like peer groups, and labels, as well as activity type, vendor, and anomalous tactics, techniques, and procedures (TTPs), without needing to learn a complicated search query language. While Anomaly Search returns raw logs, Threat Hunter in Advanced Analytics return pre-built incident timelines that outline both normal and anomalous activity that happened before and after the threat.
Threat hunt with Anomaly Search
Anomaly Search is our newest capability: a single interface that allows analysts to search for Exabeam-triggered events across their data repository. Anomaly Search offers a drop-down menu of the relevant fields available, which streamlines the query construction process. Anomaly Search pairs behavior-based detection of tactics, techniques, and procedures (TTP) with known indicators of compromise (IoC) to enhance an analyst’s threat-hunting capability, providing a flexible search capability across a variety of different objects such as sessions, rules, users, assets, ATT&CK TTPs, and anomaly identification.
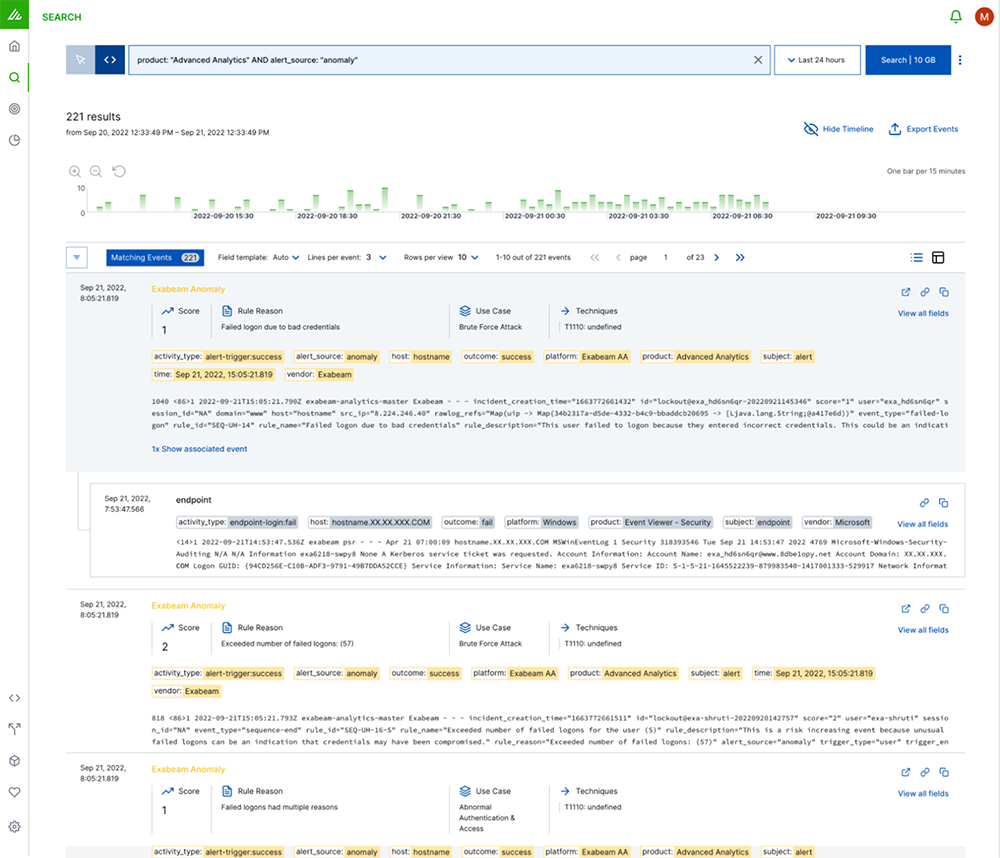
How it works
Start with a hypothesis. A large financial institution has publicly disclosed that they have been successfully breached through a phishing attack. Tina, a threat hunter at a credit union, wonders if this was a single attack, or if the attacker might have attempted to breach additional institutions like hers. She decides to investigate if her system has been compromised. Her hypothesis is based on the public report of the first bank: An attacker that tries to gain initial access via phishing, may drop malware that initiates a connection to a command and control server.
Now that she has her hypothesis, Tina uses Anomaly Search to build a query with the ATT&CK label, command and control, and the destination IP address, 23.224.232.73.
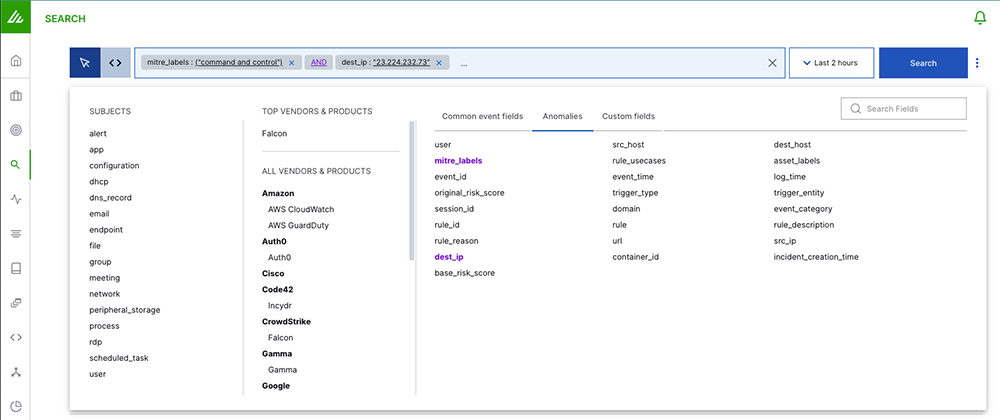
Query building is the key to Anomaly Search. In Tina’s search she can include Subjects or Vendors and Products, along with fields associated with anomalies: dest_host, src_ip, or mitre_labels. If she has a specific timeframe, she can use the time filter to modify the time range of her search. She can run the query above looking for AND or OR options – finding any associated credentials or devices.
From the search results, each anomaly provides the raw log, but it also provides additional context like score, rule reason, associated use cases and techniques. If she is ready to dig deeper into the anomaly, she can pivot to Advanced Analytics, to see the Smart Timeline™ associated with the anomaly. A Smart Timeline™ is a machine-built incident timeline that stitches together both the normal and abnormal behavior for users and machines. These timelines include all information an analyst needs to perform a rapid investigation, including: normal and abnormal behavior, as well as the surrounding context, like what happened before and after an alert, or if this alert maps to an ATT&CK TTP.
Threat hunt with Advanced Analytics
In Advanced Analytics, threat hunting pairs behavioral analytics and a point-and-click interface to position you well ahead of adversaries when it comes to protecting your organization’s assets. While user and entity behavior analytics (UEBA) notifies an analyst about users and assets who deserve attention, Threat Hunter completes the picture by giving an analyst the ability to query, pivot, and drill down into user sessions that match any combination of attributes and activities. In short, while UEBA is about the machine telling the analyst what to watch, Threat Hunter is about the analyst telling the machine what to find.
How it works
Chris, a threat hunter at a software company, is concerned that a recent malware attack in the sales department might not be completely removed. They begin by using Threat Hunter to query every sales user who recently tried to perform account management (account creation, privilege escalation) who also had failed logons or an account lockout. Whereas Anomaly Search returns raw logs, Threat Hunter quickly returns all user and asset sessions that fit the criteria, and pre-orders the sessions based on risk. Chris sees not only what they searched for, but any other anomaly or alert that occurred in the same session, saving them time on the investigation. There’s no learning curve; analysts aren’t required to learn a proprietary query language.
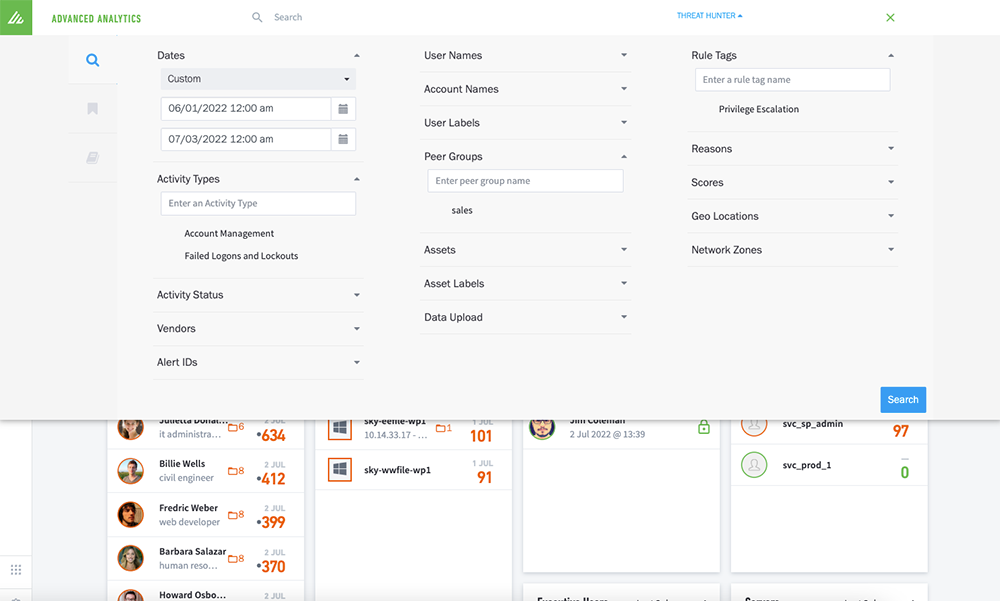
Threat Hunter allows Chris to search for abnormal behaviors in their environment that may be indicative of threat. They can filter the result set further by also asking for sessions where the password was recently changed. If they note a suspicious user — maybe a web developer in the sales group with many recent failed logins, account management activity, and password changes — they can click on the session to see the activities within this employee’s session, the reasons behind the risk elevation, and the employee’s baseline behavior. Seeing a user who is normally in the office and working, working instead remotely at a distance and at odd hours, coupled with the strange behavior noted above, Chris can deduce that this is a user whose account has likely been compromised and is being used for data exfiltration or in preparation of some other attack.
Exabeam Drives Threat Hunting
Whether it’s Anomaly Search or Threat Hunter, Exabeam puts advanced search tools in the hands of analysts who need them, enabling more effective detection of subtle attacks. Paired with Advanced Analytics, threat hunting with Exabeam improves threat detection and security operations center (SOC) efficiency, making analyst and insider threat teams much more productive.
Want to learn more about threat detection, investigation and response?
Get our white paper: Using the MITRE ATT&CK Knowledge Base to Improve Threat Hunting and Incident Response
Threat hunting and incident response are critical roles of SOC analysts. This paper is useful for analysts who need to stay ahead of adversaries in the face of ever-rising sophistication of new and emerging attacks.

Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!











