Most security analysts start their day with a common question: “What should I be working on today?” The answer can have serious ramifications. On a daily basis, analysts typically must confront an overwhelming number of security alerts, with no actual means to prioritize them. The unfortunate fact is that too often the massive number of security alerts lack the context that’s needed to quickly investigate and remediate so that they don’t become a major breach.
One of the reasons is that security teams often use generic service management tools to automate their operations with ticketing and workflow capabilities that have been borrowed from other IT departments. Or, perhaps their tools have been poorly implemented. Or, maybe they’re relying on a legacy SIEM tool that lacks comprehensive threat detection, automation and context enrichment capabilities, which leads to time-intensive manual investigations. Because all of these approaches aren’t designed to tackle today’s complex cyber threats, many organizations struggle to keep up with threat detection, investigation, and response.
Empowering analysts: Exabeam Case Manager with built-in intelligence and end-to-end incident oversight
Exabeam Case Manager makes it easy for analysts to prioritize security incidents and mitigate them quickly. Case Manager allows analysts to consolidate security alerts and automatically enrich cases with context, investigative artifacts, and risk reasons so analysts can better understand their security posture and focus on high risk alerts.
Case Manager shares a common user interface with Exabeam Advanced Analytics, Exabeam Entity Analytics, and Exabeam Incident Responder (IR). Advanced Analytics and Entity Analytics are Exabeam’s user and entity behavior analytics (UEBA) offerings. Notable events from Advanced Analytics and Entity Analytics are automatically created as incidents in Case Manager. Analysts can then gather artifacts for their investigations or quarantine affected users and assets through playbooks provided by Incident Responder.
A single place to store, view, and collaboratively prioritize security incidents
Case Manager’s shared dashboard lets administrators view queued incidents and assign them to analysts. Incidents include all the needed context, including users and assets, event timelines, and risk indicators so analysts can get the critical details to pinpoint anomalous events and mitigate them quickly.
How it looks from the analyst’s hot seat
Let’s take a look at how Case Manager gives analysts greater efficiency as they manage and respond to security incidents. Analysts can see their assigned tickets with all the users and entities associated with the incident and its type—from malware to phishing to DLP (see Figure 1).
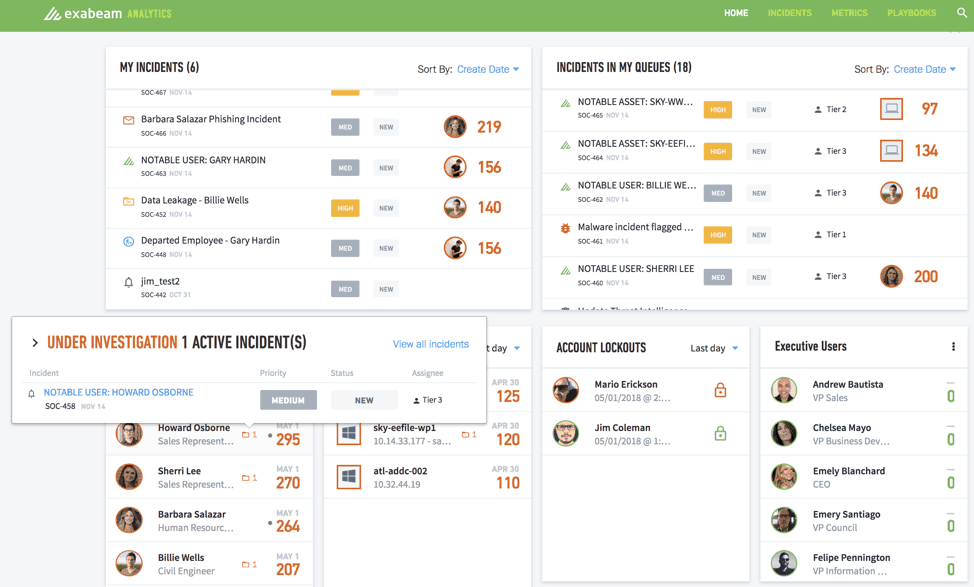
Figure 1 – Case Manager shows all queued incidents, assigned incidents, and notable users and assets on a single dashboard
Analysts can immediately access user profiles to look for contextual information including a user’s host, login IDs, department, location and their associated peer groups. Additional context includes the user’s normal and anomalous behavior with all risk reasons and artifacts involved (see Figure 2).
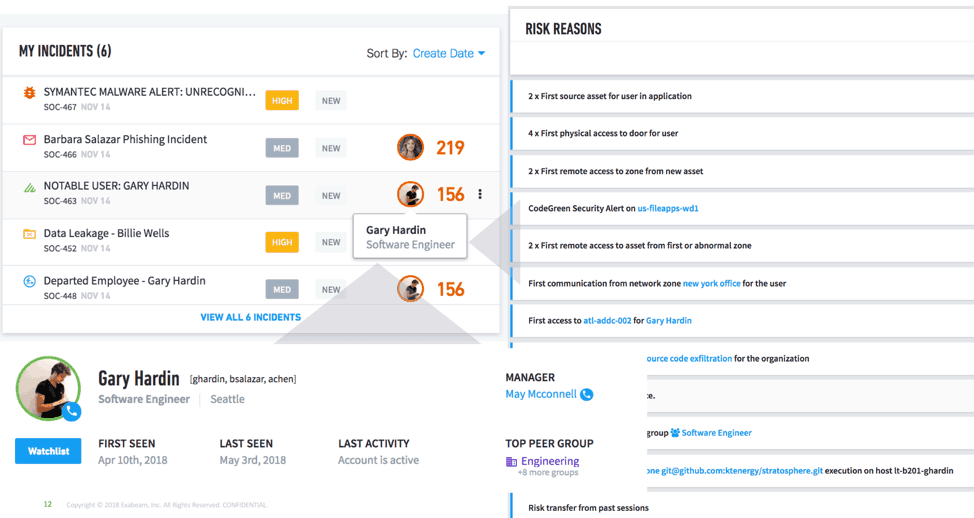
Figure 2 – Every Exabeam case or created incident is contextually enriched—with user login, department, peer groups, and associated risk reasons
How it works—from notable event to incident
Consider a new WannaCry ransomware incident (see Figure 3). It is instantly escalated to a Tier 3 analyst. Clicking on the preview, a more detailed view provides all the ticket information. Even a junior analyst can quickly assess what’s going on. They can see all the risk reasons attached to the ticket, and all impacted entities such as the assets, files, devices, and users. The attached Exabeam Smart Timeline shows all related events pertaining to impacted users and assets, stitched together in one timeline.
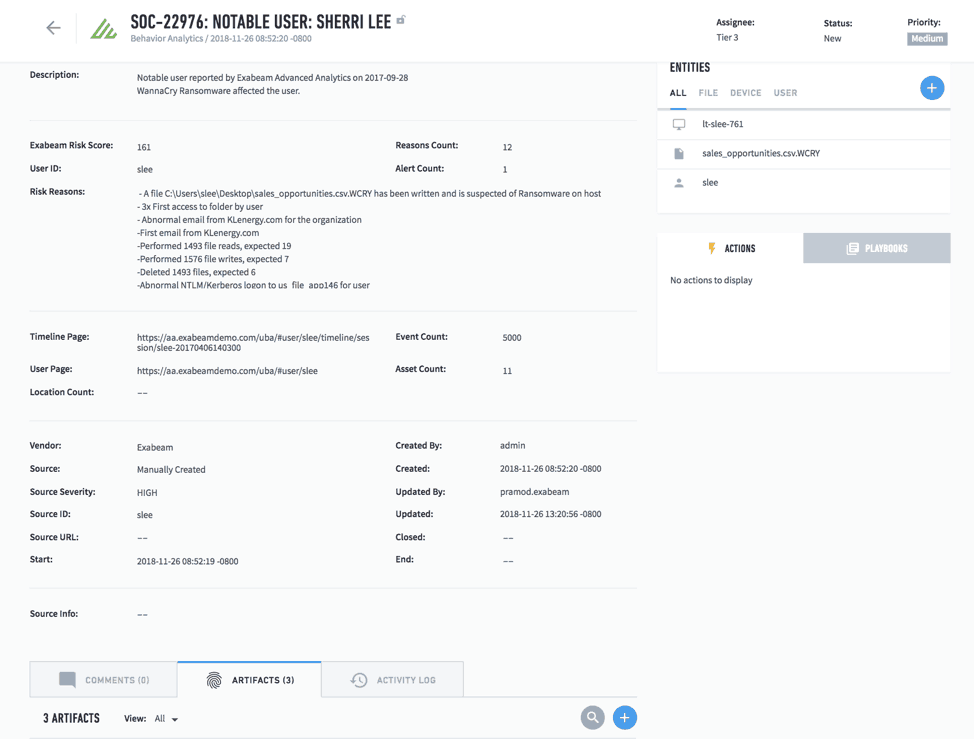
Figure 3 – Detailed incident view shows all risk reasons, impacted users and entities, artifacts, and attached Smart Timeline (as shown in Figure 4)
Analysts can take further action by using prebuilt playbooks in Incident Responder. These can be automatically triggered to gather additional artifacts to help with investigations, and to quarantine affected users and assets until remediation is completed.
Exabeam Smart Timelines, a key artifact of a security incident
One of the key steps in intelligent incident response is automatically weeding out the false positives and stitching together the event timeline so that the investigation is faster and more accurate. Exabeam provides pre-built Smart Timelines that automatically combine both normal and abnormal behaviors into a timeline, so investigators can accurately pinpoint the series of anomalous events, along with associated assets, users, and risk reasons. The relevant Smart Timeline gets attached to the ticket within Case Manager automatically as an artifact. This makes it faster and easier for investigators to mitigate security incidents, lowering the mean time to respond (MTTR).
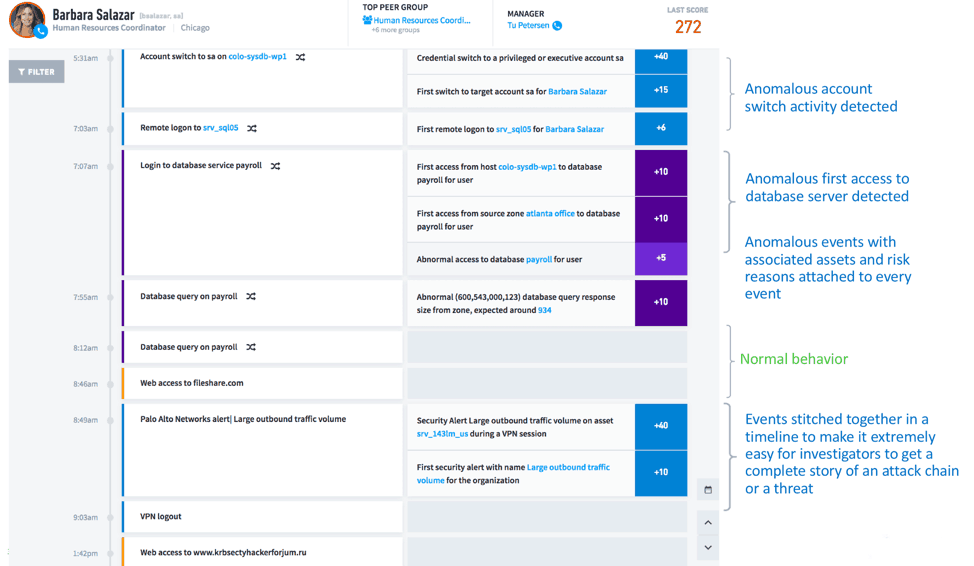
Figure 4 – Smart Timelines provide the complete user behavior story; investigators can pinpoint anomalous behavior and respond to security incidents faster (lower MTTR)
Coupling investigation and response in automated workflows empowers analysts to effectively address incidents and improve SOC efficiency.
For more information on best practices on advanced analytics and incident response, see:
How UEBA Overcomes 5 Hurdles to Achieving Effective Security and Incident Response
Improving Cybersecurity with Orchestration and Automation
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












