Information security practitioners know there are real operational risks that result from unpreparedness. There are known unknowns that we do our best to protect against, but there are also unknown unknowns that, when they surface, often result in 2:30 am calls from our CISOs or information security leadership. These alarms create stress and lead to burnout among security analysts and managers. Ideally, awareness and preparation can mitigate many of these risks, but situations on the ground in a security operations center (SOC) are not always ideal. Correlation rules can detect and respond to known threats, but having a system that automates the process of discovering what is odd and abnormal on a network goes a long way toward covering gaps for threats that are unknown or difficult to detect.
This blog post will highlight some of the lesser-known benefits of user and entity behavior analytics (UEBA), along with chronologically correlated security vendor events in a timeline. Specifically, we’ll be exploring the following topics:
- How Exabeam serves as a force multiplier to your SOC staff with its wide range of pre-built security coverage
- How Exabeam use-case methodology helps prioritize and validate risk mitigation in a systematic manner
- How looking at various vendor solution events and alerts collated in a single timeline reveals gaps and misconfigurations in other vendor solutions
- How behavior analytics highlighting initial and subsequent anomalous activity reduces alert fatigue for analysts and incident stress for managers
There is a great benefit to deploying a combination of correlation rules and behavior analytics in tandem. The former detects known threats specific to your environment as prescribed by your organization. The latter identifies first and anomalous activity that might not have been something analysts were specifically looking for, but which reveals risks on the network. Pairing these two modes of detection creates a powerful security combo. A well-tuned system will return some false positives. However, the goals are to surface positives that reveal risky activity and show risks of which you were unaware.
Learning to maximize prepackaged content
Exabeam Advanced Analytics contains more than 1,700 pre-built rules and models. These cover a wide range of potential threats to your network. Most of the rules have a model dependency which compares current behavior to historical norms for a user or entity. The quantity and diversity of rules allow analysts to focus on threat hunting and alert triage, rather than building rules that could prove fallible due to imperfect rule formation.
The time to create a response plan for how your organization will respond to specific types of threats is not while you’re investigating an incident, but beforehand. To address this, Exabeam developed a use-case methodology that allows for the systematic prioritization and validation of the most critical threats according to your organization’s risk matrix. A response plan for specific types of attacks should be created before the incident occurs to reduce time to respond to the attack. Then, analysis and validation should be performed on the threats of highest criticality to your information security group and its stakeholders. Exabeam use cases are a helpful way to prioritize and validate use cases to detect specific types of threats. They also help SOC analysts and management sleep more soundly at night, knowing they have prepared for these eventualities.
There are three use case categories:
- Compromised Insider
- Malicious Insider
- External Threat
Compromised Insider use cases relate to activities that would typically be carried out by a bad actor who has compromised the credentials of one or more accounts on the system. Malicious Insider use cases represent detection capabilities against actions that might be taken in an insider threat scenario. External Threat contains activities carried out specifically by malicious actors seeking to harm or infiltrate your network via hacking behavior.
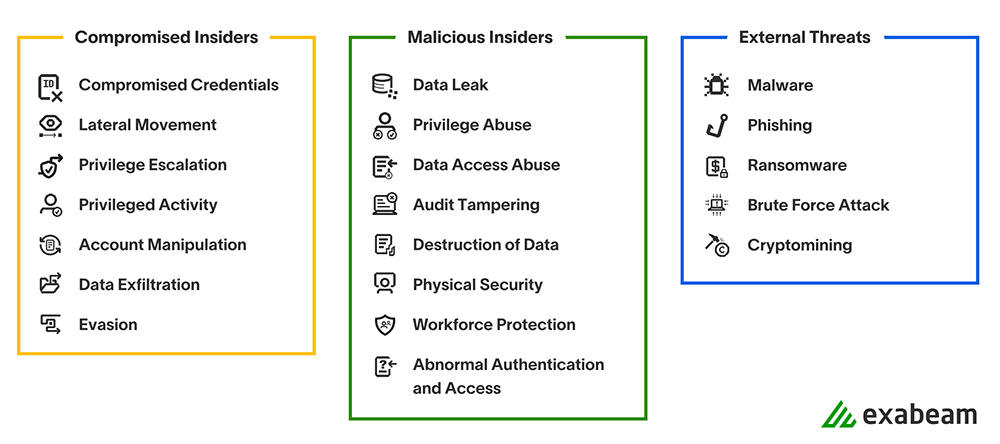
Most use cases are broken down into scenarios, which serve as a subset of use cases that group Advanced Analytics content into attack modalities. These serve as even more granular sets of content to identify specific types of activity. Understanding what rules exist, then validating the rule sets in which your organization is most interested greatly enhances assurance that the activity will be detected if it occurs.
Avoid viewing your network through a coffee straw
In larger organizations, the information security group may be divided into subgroups. It often occurs that there are groups that use their own security solutions to detect threats within their vendor’s user interface. In this case, independent groups don’t necessarily interact with their peers when they investigate a threat. The Windows security team may not be involved when the Data Loss Protection team discovers nefarious activity. Likewise, the Firewall team, the Endpoint Protection team, the Unix security team and the Purple team may all handle vulnerabilities without sharing the nature of the threat with other teams.
Exabeam provides unique insight into the nature of the occurrence by aggregating all logs for a user into one unified view. In a Smart Timeline™ all events for a user or asset appear. The Timeline is filterable to show only certain types of events, alerts, and anomalies. Since compromised users will display aberrant behavior from their norms, malicious users will be seeking to carry out some abnormal behavior, and because external threats are always bad, this activity will show clear patterns in the user or asset’s timeline.
Malicious activity doesn’t often happen in a vacuum, and often one bad behavior is followed by another. Smart Timelines save analysts a great deal of time tracking an event and evolving a narrative around the nature of an attack. For example, compromised credentials often lead to lateral movement. Lateral movement often involves privilege escalation and privilege abuse. Following the timeline allows for a more comprehensive investigation and turns up clues that wouldn’t have otherwise been noticed when viewing the network in security vendor silos.
Become a cybersecurity superhero
Viewing all security logs in Exabeam also has the collateral effect of turning the analysts who perform triage and investigation with it into subject matter experts on the network. Exabeam generates context around network events that allow analysts working in it to gain an understanding of multiple security vendor log formats. Being an effective and efficient analyst requires understanding these logs to determine the severity of the incident. It spurs interaction with other teams and generates greater understanding of multiple security solutions. An abnormal VPN logon, a couple of dodgy emails, and an odd print job might all be dismissed as anomalous but benign by their respective security monitors. However, when correlated in a Timeline, it becomes apparent that this behavior warrants a closer look.
In addition to providing a more holistic view of activity on the network, Exabeam behavioral analytics often highlight activity that wouldn’t raise the eyebrows of InfoSec analysts. This comes in the form of first or anomalous alerts that require investigation revealing some flaw in logic or misconfiguration of other security vendor platforms. When anomalous behavior occurs because of model-based rule triggers, it is common to reach out to the team that owns security for that behavior. Typically, when those alerts are brought to another team misconfigurations are discovered. Also, alerts derived from behavior analytics often show threats on the network for which there was no mitigation at all.
Relieve alert fatigue
Let’s be honest; sometimes working in a SOC is boring. Sifting through piles of security alerts day in and day out creates real fatigue among security analysts. This fatigue leads to lax alert triage and response when analysts find themselves reviewing the same types of alerts every day. Eventually that can lead to burnout, and analysts dismissing alerts that show up in the queue — not because they are benign — but because it is the 99th time they’ve seen that type of alert.
Likewise, the intent behind a correlation rule is not always immediately evident to an analyst. They may see an event in their queue and not be aware of the context that makes it dangerous. An analyst might see a service account scanning ports with an account name that looks like it should perform that activity, and dismiss it. If they knew that this account had recently been created by a user that had no business creating it, it would warrant an urgent response.
Advanced Analytics helps to solve both of these issues. Smart Timelines are capable of showing all events for a user or asset in a session, but it usually just shows the first and anomalous events for a user. This way an analyst is not searching through meaningless alerts all day, but rather looking at things that get surfaced because they signify potential threats. A hacker that has compromised an account will never act precisely as the rightful owner of the account. They are not hacking the network to do work for free. They are after some goal and will behave in a manner toward achieving that goal.
Additionally, the first and anomalous rules add context by the name of the alert and its respective description. This avoids the situation where a content creator activated a correlation rule but didn’t describe it adequately. Without the critical context of an event, risky behavior can be observed but not acted upon. A well-tuned Advanced Analytics instance with rule scores that highlight the threats most critical to an organization is a powerful vessel of detecting threats and gaining a better understanding of the network.
Conclusion
Exabeam Advanced Analytics gives you the power to understand normal user and device behavior and detect anomalies, even as normal keeps changing. Risk-based prioritization uses machine learning to automatically assign risk scores to all events, prioritizing triage, investigation, and response for key incidents and automatically visualizing these events within Smart Timelines that show full event flows and activities to inform the next right action.
Timelines convey the complete history of an incident and score the risk associated with each event, saving analysts from writing hundreds of queries. They also help detect lateral movement by organizing incidents to follow attack activity, credentials use, or permission changes within your environment. This enables you to find and address the threats others tools miss, uplevel your security team speed and performance, and stay ahead of your adversaries.
Want to learn more about UEBA?
Get The Ultimate Guide to Behavioral Analytics
This comprehensive guide was created to help organizations evaluating UEBA solutions better understand it and how it can be adopted to improve your overall security posture with faster, easier, and more accurate threat detection, investigation, and response (TDIR).
Read this eBook to gain clarity on confusion about the growing UEBA market, and learn about:
- What UEBA is and why it is needed
- How UEBA is different from other security tools
- The different types of UEBA solutions
- Factors to consider when evaluating UEBA solutions
- Threat-centric use cases

Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













