Security information and event management (SIEM) is a mature but aging technology; the term SIEM was coined in 2005 by Mark Nicolett and Amrit Williams, in Gartner’s SIEM report, “Improve IT Security with Vulnerability Management.” In the time since, vendors have developed “modern” SIEMs that promise new capabilities to provide unparalleled visibility and automation to security teams. And while companies crave these new capabilities to improve threat detection, enhance analyst productivity, and decrease logging costs, many hesitate to replace their legacy SIEM. In this post, we’ll discuss why SOC leaders may be dragging their feet on performing a SIEM tech refresh and what can be done about it.
A brief history of SIEM
The first generation of SIEMs included in the Gartner report was created over 10 years ago — before the first iPhone! Originally, these SIEMs were built out for compliance and threat detection use cases, performing much better at the former rather than the latter. With legacy solutions, security teams poured hours into maintaining static correlation rules, identifying new threats as they arose. Investigation proved similarly painful, requiring querying and pivoting until analysts gathered enough evidence to manually create a timeline of events. Once analysts figured out what happened, they could contain and respond to the incident.
Modern threats require modern solutions
A lot has changed since then. In recent years, SIEMs have evolved to keep up with increasingly frequent and sophisticated threats. Today, Gartner identifies both user and entity behavior analytics (UEBA) and security orchestration and automation response (SOAR) as integral features of a “modern” SIEM. UEBA improves threat detection by identifying anomalous behavior relative to a normal baseline of activity, while SOAR automates incident response through integrations with other enterprise systems via APIs, for instance, endpoint detection response and response playbooks.
Meanwhile, data sources for ingestion continue to expand. Companies seeking modern solutions are looking to leverage big data architecture while managing ballooning logging costs. Further, as companies continue to migrate to cloud-based applications such as Office 365 or Salesforce, they must extend their security to the cloud. For more detail on the history and evolution of SIEM, see our blog post SIEM Security Primer.
Roadblocks to change?
With the changes in the SIEM landscape over the last decade, companies are eager to adopt new technologies. Many companies are considering a “tech refresh” for their legacy SIEMs. However, replacing an existing SIEM can be a daunting process. In particular, security teams may face organizational and operational constraints, preventing them from a complete tech overhaul.
From an organizational perspective, log management systems and SIEMs are frequently shared resources which may be used for use cases outside of security, for example IT operations. Politics may influence the ability to replace an existing SIEM if other teams are still receiving value. Security teams may choose not to pursue a tech refresh to avoid a political battle over the tool in use.
From a user perspective, “ninjas” and other specialists can become attached to an existing SIEM, wanting to stick with familiar tools they’ve used for years. Combined with the fact that security teams often lack the budget or time to undertake an immediate overhaul, it may be easiest to simply rely on the tools and technologies already in place.
Modular SIEMs: augment instead of replace
Many SIEMs force customers to use a single vendor to provide all their security management needs. But with all the advantages that newer technologies provide, should customers have to choose between their existing SIEM and a more modern one? Instead, companies may consider using a modular solution to avoid the pain of a complete replacement project. A modular solution leverages a company’s existing SIEM while concurrently investing in a newer, more modern tech stack. The beauty of this approach is that it allows security teams to take an incremental approach to modernization. By completing a tech-refresh in phases, companies can spread out upgrade costs over multiple budgetary cycles while augmenting their SIEM with complementary technologies.
BYOS: bring your own SIEM (and enhance it with Exabeam)
The Exabeam Security Management Platform is modular, allowing customers to “mix and match” products to obtain new technology without needing to rip out their existing SIEM. You can opt to either replace your existing SIEM or augment it with Exabeam products to build custom solutions tailored to meet your security teams’ specific needs:
- Improve threat detection — Static correlation rules often miss unknown attacks, lateral movement, and create an enormous amount of false positives, while also requiring huge amounts of maintenance. Exabeam’s Advanced Analytics and Entity Analytics detect threats based on identifying abnormal, high-risk user and machine activity, regardless of whether it’s been seen before, improving accuracy without the need to create and maintain correlation rules.
- Enhance analyst productivity — Move beyond manual incident investigation and save analysts from days or weeks of querying [link to Ponemon report: Ponemon Study Reveals Analysts Tasks Take 50% Less Time When Using Exabeam] and pivoting to perform each investigation. Exabeam Smart Timelines automates this process, allowing analysts to focus on high-value work instead of tedious tasks.
- Enable faster response times — Avoid the work of using dozens of tools to manually respond to an incident and reduce inconsistencies from analysts of varying skill level. Exabeam’s Incident Responder includes pre-built, out-of-the-box playbooks that automate and standardize incident response actions.
- Decrease logging costs — Don’t be forced to choose between anticipating which data will be most useful in the event of an attack or deal with unpredictable logging bills from the increased collection. Deploy Exabeam’s Data Lake alongside an existing SIEM for unlimited log storage and search with flat, user-based pricing.
- Extend security to the cloud — Easily ingest logs from popular cloud-based services like SalesForce, O365, AWS, Google Apps for work, and dozens more. Exabeam Cloud Connectors provide pre-built connectors that can be added to any existing SIEM.
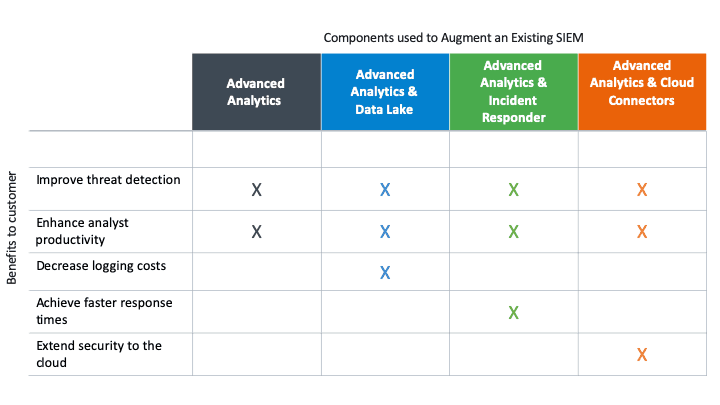
Figure 1: Exabeam’s modular nature can augment an existing SIEM to solve a variety of customer needs.
Conclusion
Each company has a different environment, making its progress on adopting newer SIEM technologies a unique case. Regardless of where you are in your journey towards modernization, you don’t have to choose between the old ways and modern solutions. You can opt for a modular platform that works with existing tech to avoid the headaches of a full replacement project.
Want to learn how Exabeam can work alongside your existing SIEM? Sign up for a free demo here!
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













