Security operations centers (SOC) are the frontline of defense against cyber threats. So, whether your SOC is in-house or outsourced, it’s essential to gauge the effectiveness of your SOC given the importance it plays in your overall cybersecurity program.
Exabeam’s 2020 State of the SOC Report allows you to compare your company’s security operations center to your peers. With our report, you’ll gain valuable insights, including:
- What your peers consider are their top SOC priorities and challenges
- Successful tactics your peers are using to retain employees
- Technologies that are necessary to address the latest threats
This report is our third annual comprehensive survey of cybersecurity professionals like yourself who manage and operate SOCs. Respondents include CISOs, CIOs, frontline security analysts, and security managers from the U.S., U.K., Canada, Germany, and Australia. The report covers a wide range of topics including:
- Basic SOC operations
- Hiring and staffing
- Operational processes
- Technology
- Finance and budget
Here are just a few key findings from our report:
SOC leaders and analysts are confident in their ability to detect common security threats but do not agree on the threats
SOC leaders and frontline analysts do not agree on the most common threats facing the organization. SOC leaders believe that phishing and supply chain vulnerabilities are more important issues, while analysts see DDoS attacks and ransomware as greater threats.
Yet threat hunting and the ability to remediate threats effectively stands out as a critical skill that SOC personnel feel they lack. This gap may indicate that SOCs are overconfident in their ability to detect a full range of security threats.
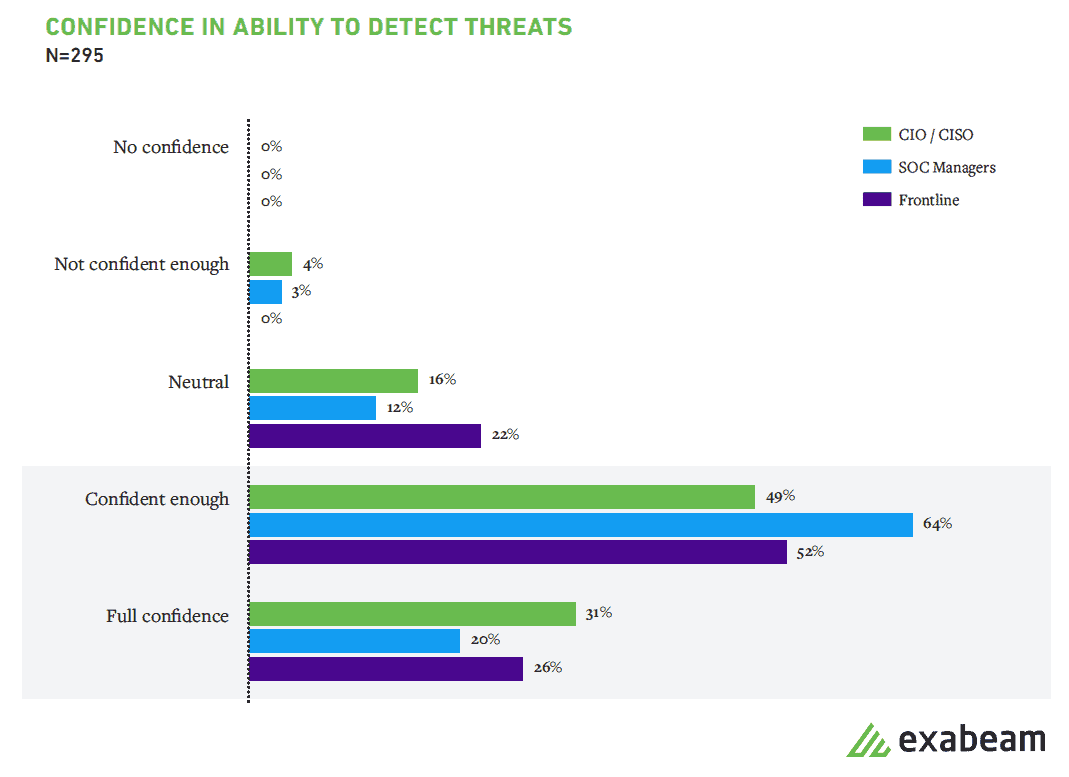
Figure 1: Eighty-two percent of SOC professionals are confident in their ability to detect threats.
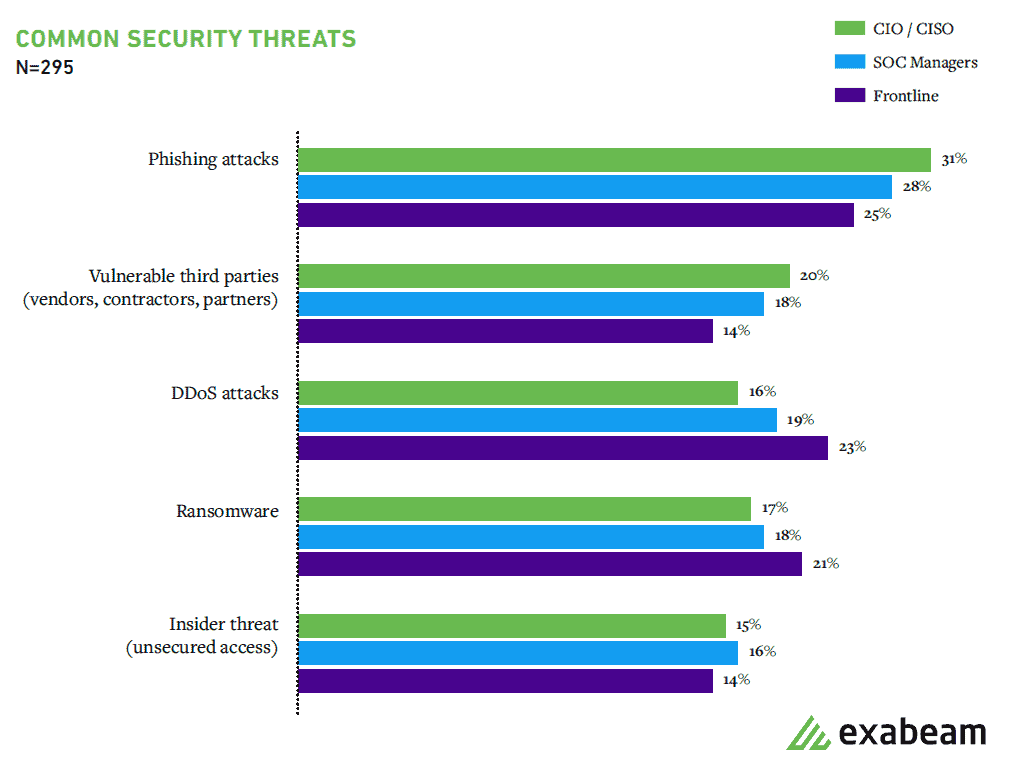
Figure 2: SOC leaders believe that phishing and supply chain vulnerabilities are more important issues, while analysts see DDoS attacks and ransomware as greater threats.
Working in teams is this year’s most important soft skill
In last year’s report, respondents cited personal and social skills as the most critical soft skill for SOC employees. This year, however, 62% of respondents noted the ability to work in teams as the most important soft skill.
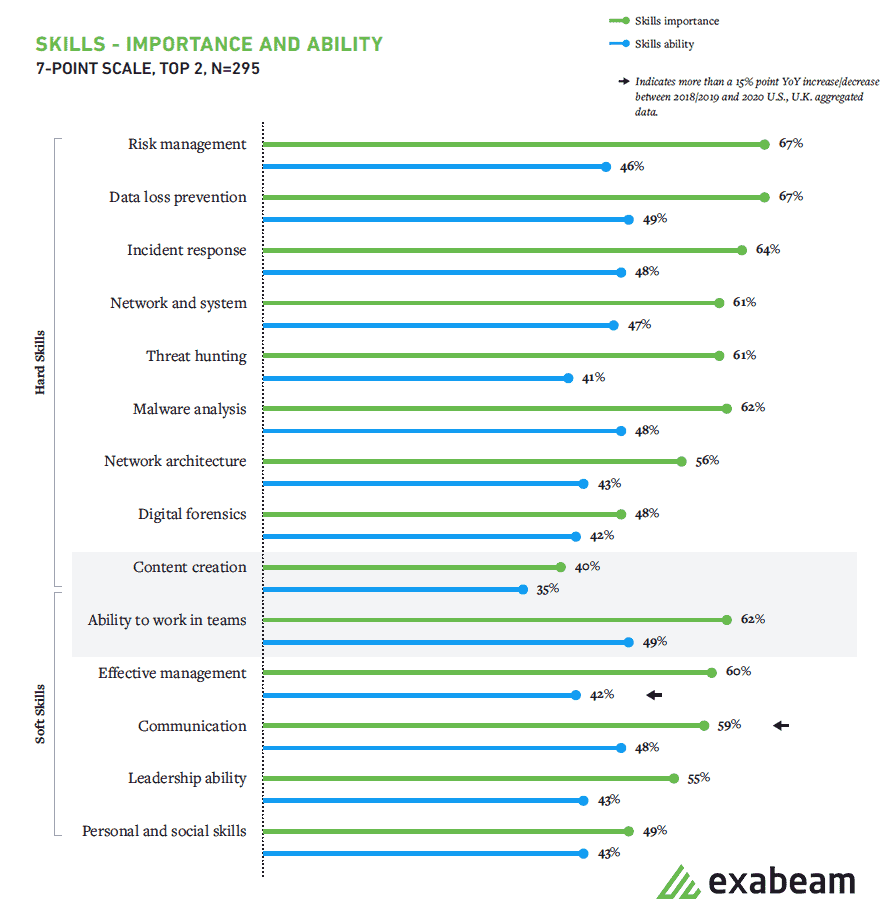
Figure 3: While hard skills remain critical, SOCs place emphasis on soft skills with the ability to work in teams taking precedence over formerly reported social ability.
The importance placed on teaming is an indication that SOC staff need to work in cohesive teams and often with staff from other teams. SOC members that work as a team are more apt to document processes to standardize tasks and train new employees which is helpful both as teams grow or are reassigned.
Members of a SOC should not only improve teaming among their group, but also proactively strengthen their working relationship with other functional groups, including IT operations, NOC staff, and increasingly DevOps. Working with these other groups helps to improve response time. More important, it will create a team that is responsive and able to adapt as the work environment shifts like the challenge of working with a distributed workforce, and ensuring the right collaboration and communications tools and culture are in place.
Threat modeling, incident analysis abilities and budget/resource allocation show year-over-year decline
Our report reveals a significant decline in the ability to do threat modeling in both the U.S. and U.K. SOCs. Threat modeling is the systematic approach to identifying and prioritizing potential security threats and designing countermeasures to prevent them. The data suggests threat modeling doesn’t have an agreed upon standard and most analysts perform it infrequently or not at all.
Additionally the ability to conduct incident analysis and budget and resource allocation for both countries have declined from the previous year.
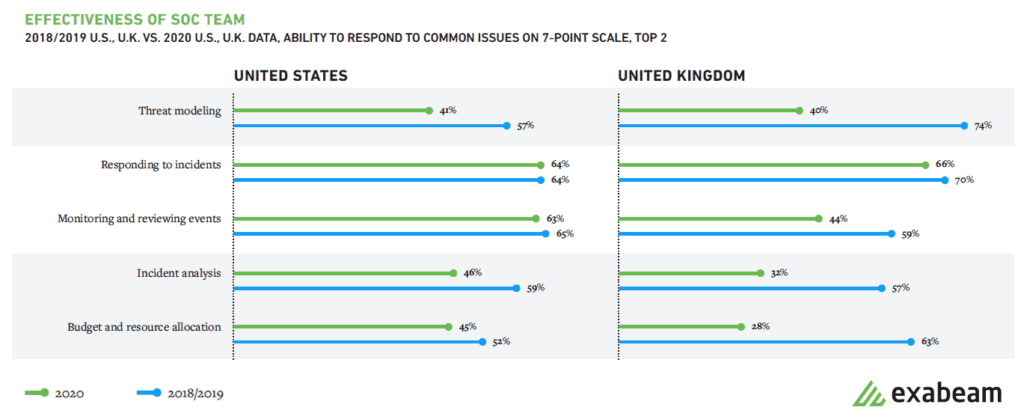
Figure 4: U.S. and U.K. SOCs reported significant declines in their ability to do threat modeling, incident analysis, and budget/resource allocation in YoY change.
Managers and analysts don’t agree with CIOs/CISOs on inexperienced staff and time spent on reporting and documentation
When asked to rate pain points, inexperienced staff and time spent on reporting/documentation were common pain points for managers and frontline employees but not for executives.
Lending credence again to the statement, “you can’t protect what you can’t see,” senior leaders noted that the lack of visibility and not having a good list of assets were their most significant pain points.
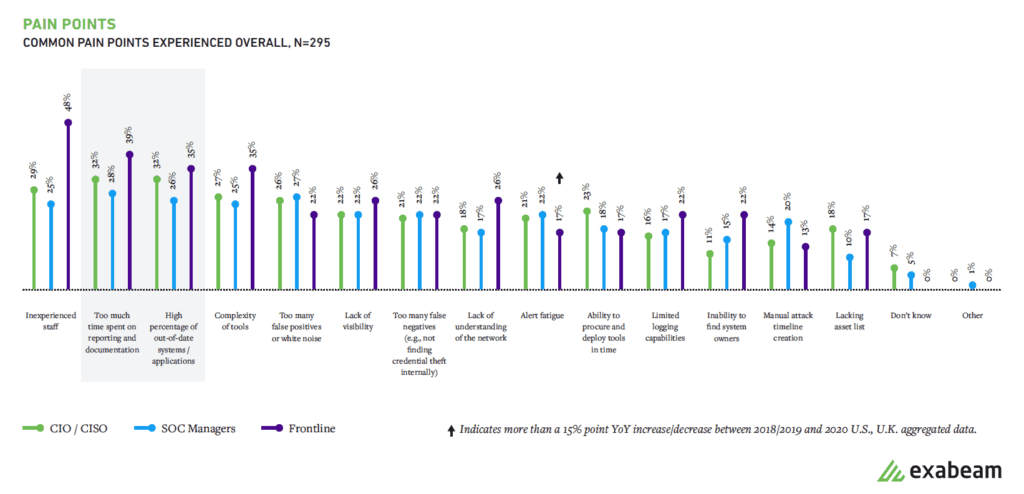
Figure 5: Inexperienced staff and too much time spent on reporting and documentation continue to be pain points for SOCs in 2020.
Shared responsibilities across all levels with some variances
Traditionally SOC teams have generally been responsible for two primary responsibilities — investigating suspicious activities and maintaining security tools. But over the years, the responsibilities of the SOC has increased to include other duties such as defining security metrics and incident response. Our report finds that staff at all levels share these responsibilities. However, there are a couple of differences.
We found that CIOs and CISOs rank their responsibility for operations management as well as policy and procedure development highest, they also share other responsibilities with managers and frontline employees including defining security objectives and metrics, and incident response. Not surprisingly, maintaining security monitoring tools was noted as a critical responsibility for frontline employees.
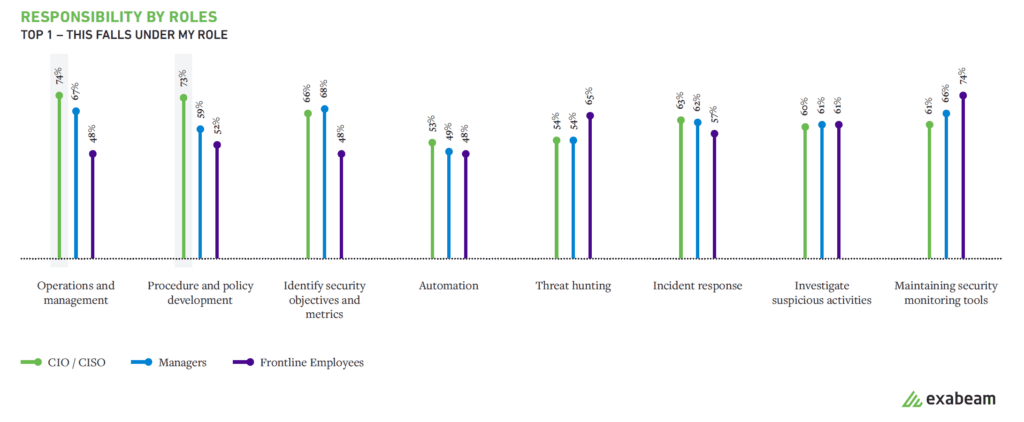
Figure 6: SOC managers drive metrics specifically in operations and management and procedure and policy development.
We invite you to download your copy of the complete report to learn other points of interest that can help measure the effectiveness of your SOC and support you in your ongoing efforts to protect your organization.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












