
-
- Home
>
-
- Blog
>
-
- InfoSec Trends
Securing Your Remote Workforce, Part 5: Helping Your End Users Stay Protected
- Apr 17, 2020
- Cynthia Gonzalez
- 6 minutes to read
Table of Contents
Over the last few weeks we have shared the first four parts of a five-part blog series to support IT and security teams working to enable and secure remote workers; this is part five of that series. Previous posts covered topics such as detecting phishing scams, unusual VPN access, malware, and fraudulent log-ins.
Regardless of the size of your organization or cybersecurity team, there are a number of actions you can take to help secure your now remote employees. I (virtually) sat down with Alexander Koshlich (Alex), Director of InfoSec at Exabeam to discuss some of the challenges that come with a fully remote workforce. Alex has been working in the cybersecurity space for nearly a decade in both the public and private sectors. Alex comes from a technical background, specializing in red/blue team initiatives, and more recently building out security programs for organizations.
In this post, Alex will describe some of the challenges his team is facing and offer suggestions to help secure your workforce and ensure your employees stay protected.
What security measures helped you prepare for a 100 percent remote workforce?
At Exabeam, we have always had a laid-back work from home culture. We can expect that 60 percent of our employees are working remotely on any given day, whether it is at a café, customer site, conference, hotel room or home. We took this into account when first designing our security strategy. It was important that we build a structure that would enable remote workers and would allow for the ability to provide real-time response remotely. We followed the zero trust model when designing our strategy, which focused on device verification and endpoint visibility. Furthermore, multi-factor authentication, role-based access control, and single sign-on has been a mandatory strategy for all employee services we provision.
What is the zero trust security model?
The zero trust security model believes that no user, whether inside or outside of the network, should be trusted by default. This stems from the idea that organizations that are too trusting of individuals and outsiders are prone to vulnerabilities. Some of the principles to implementing a zero trust security model include verifying all users and devices, implementing least-privileged access, microsegmentation of security perimeters, and risk management analytics for all network traffic.
Have you adapted your security structure to support a 100 percent remote workforce?
At the moment, endpoint visibility is key. As we move to a work from home model, our corporate security perimeter has expanded. Because we do not manage the internet connections from which our employees are connecting to their laptops, we are now focusing more on endpoint security than we did before. This includes endpoint hygiene – making sure that the endpoint security stack is running and operating as expected: updating browser software, installing security patches and managing application versions. Ultimately, we want to protect the devices from exploitation or unauthorized access.
We’ve made some changes to allow a little bit more flexibility, so our employees feel productive at home, for example accommodating for local-network screen sharing technologies like Apple AirPlay and Google Cast. We have also increased our incident response readiness testing. We are retesting playbooks for remote malware remediation to ensure our tools and capabilities function as expected. Given that from a SOC perspective, 60 percent of our employees were already remote, we continue using real time response in security incident situations.
Why is it important for organizations to secure their end users?
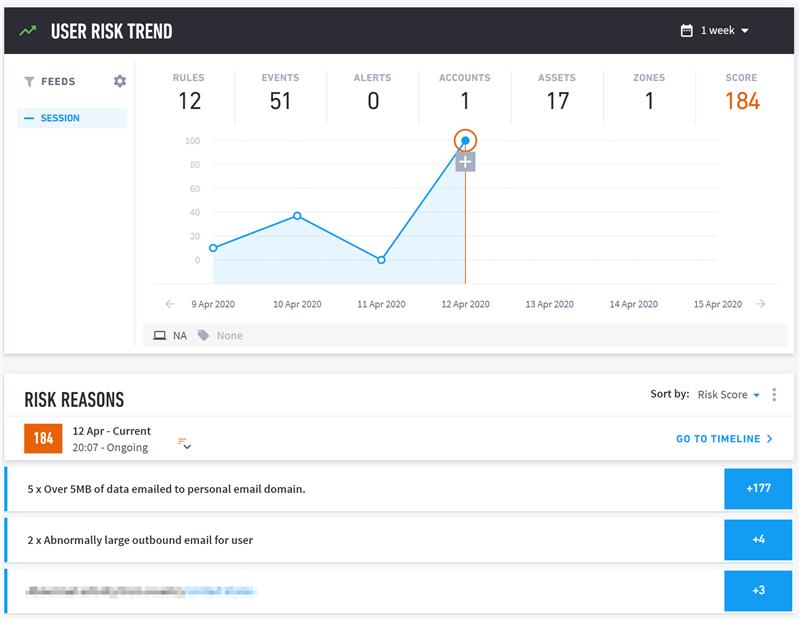
Figure 1: End users have access to a variety of internal corporate assets that can be exploited in the event of a security breach.
Your employees have connectivity access to various internal corporate resources, a compromised account can potentially result in major security breach if not detected and stopped early on in the attack chain.
Has employee behavior changed since “shelter in place” went into effect?
We have started to see an uptick in non-business-related activity on corporate assets. Employees are browsing the web more, streaming videos and using social media throughout their work day. Our security strategy is flexible, so we do not block this type of activity on all corporate endpoints, but some organizations rely on web filtering to block browsing and social media channels. Often, these web filters are installed as part of internal proxy servers and firewalls. This makes it difficult to block browsing, since your employees are remote, and outside of the corporate network.
We continue to monitor for abnormal user activity, which we believe is a strong indicator of a threat. Below, you can see how activity such as emailing data to a personal email account, forwarding executive emails outside of the company, or file exfiltration attempt gets a risk score and flagged as suspicious. These are activities that we will then review to identify whether or not they are malicious.
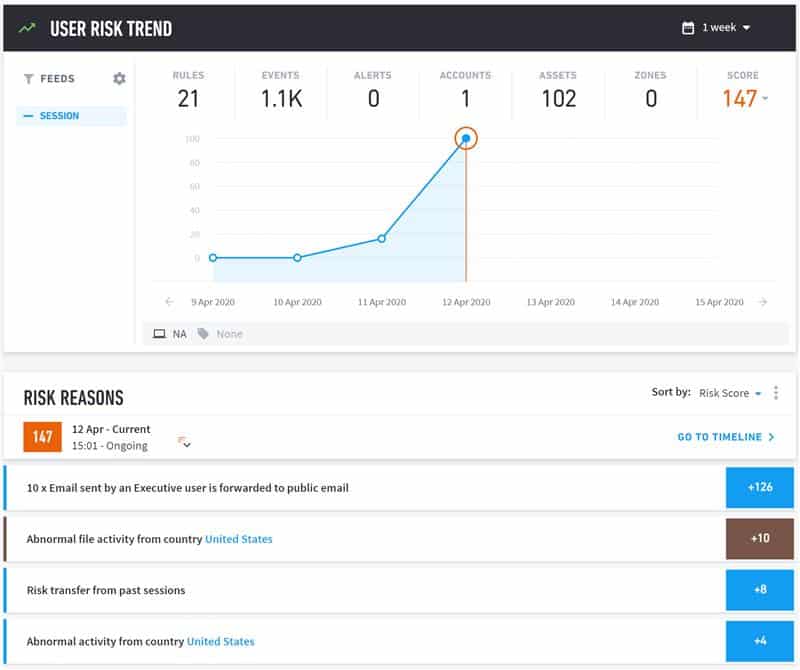
Figure 2: Unusual user activity such as excessive forwarding of executive emails to external emails are given a risk score to evaluate if they are malicious.
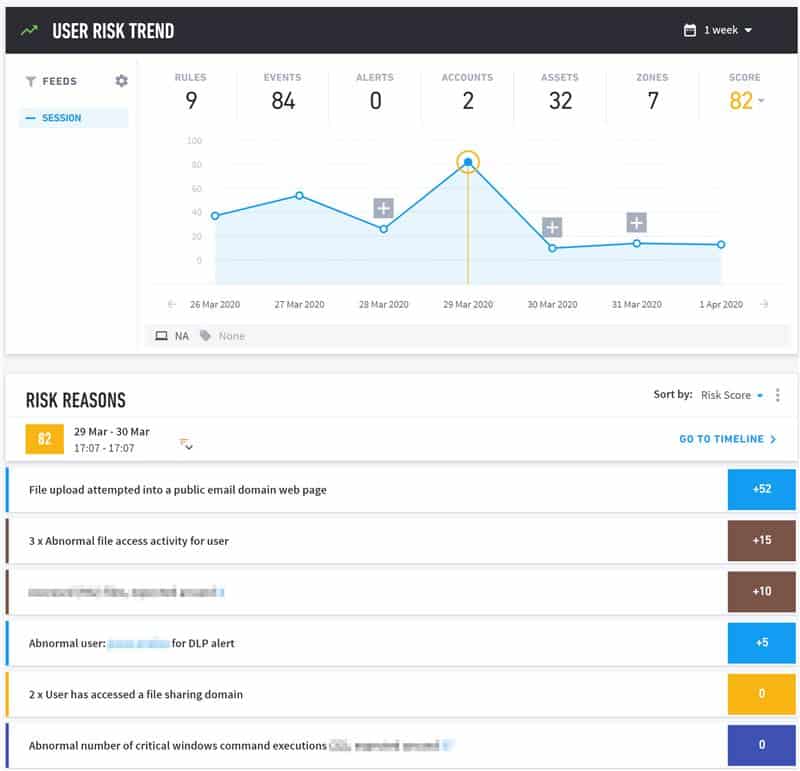
Figure 3: In this instance the user attempted to upload a file into a public email domain web page, a file exfiltration activity that received a higher risk score.
What about cyberattacks, has there been a change in the types of attacks you see?
We’ve seen an uptick in phishing attacks against individual employees. The attacks we’ve been seeing exploit public fears about COVID 19 for their attacks. Unfortunately, some of the technical infrastructure controls we had on-prem are no longer applicable to the same extent, so the endpoint has become part of our perimeter. This means we are focusing our detection and activity on the endpoint more so than we did before. Along with typical anti-virus protection, we deploy EDR and DLP tools to support detection on the endpoint.
Recently, we have seen some news about web conferences being “hijacked” by external actors. What steps can security teams take to help secure teleconferencing?
Attacks can happen on any teleconference or communication platform, all remote conferencing solutions experienced security issues at some point in time. Logins and passwords are often dumped online when a website or service is compromised. Adversaries can purchase these username and password combinations for less than a penny each, and sometimes even get them for free. As users have a tendency to use the same passwords, adversaries take advantage of this tendency to log into teleconference platforms using accounts leaked in older data breaches, a technique known as credential stuffing. Mandatory passwords, good middleware patching practices, and advanced anti-malware prevention tools will mitigate most of the common attacks against web conferencing platforms.
Given recent news reports of attackers “hijacking” teleconferences, we reviewed and updated our existing configurations and communicated best practices guidelines to our employee base.
There are a lot of people with IoT devices at home: smart light bulbs, personal assistants, thermostats, doorbells. Given that most people do not invest in security for these devices, can compromised IoT devices pose a risk for the enterprise?
Definitely, it all comes down to good security controls at the endpoint level – firewall configuration, regular patching schedule, and mandatory encryption can help address the potential attack vectors posed by IoT devices. We designed our security layers so remote connectivity is treated the same whether an employee is working from home or somewhere public like an airport or a cafe. We assume the Wi-Fi network from which the employee is connecting remotely is compromised, and follow industry best practices for endpoint configuration profiles:
- To limit eavesdropping, restrict unencrypted communication for any business related function or service
- To help prevent man-in-the-middle attacks, enforce encryption on all corporate services and test that endpoints are prepared against such an attack
- Firewall enforcement and regular patch scheduling addresses network level attack vectors against the devices
- Conduct red team/blue team exercises against a corporate device in a “coffee shop scenario”
Have colleagues from other companies shared any issues they are facing?
Some colleagues experienced challenges scaling their VPN infrastructure while maintaining the same level of network monitoring and security controls. Ability to scale remote workforce directly correlates to hardware and bandwidth limitations. Initial rollout does not typically scope 100 percent employee capacity right out of the gate, whether it’s due to administrative or technical resource limitations.
What are measures that companies can take to help secure their end users, especially if they are unable to address their VPN capacity?
Some suggestions would be to:
- Two-factor authentication: Enforce two-factor authentication for all corporate connectivity, including cloud services. If hardware tokens are not an option, consider a soft token. Make sure to to disable any support for legacy authentication protocols.
- Monitor user activity: Collect and monitor logs for endpoints, user and file activity. This provides visibility into abnormal user or endpoint activity.
- Test response readiness: What is your ability to detect and remediate a malware attack remotely? If an attack happens you might not have the ability to remote wipe in real time. Test your response readiness to be prepared when a malware attack happens and avoid scrambling for a solution.
As a security expert and now, a remote worker, what are measures that employees can take while working from home, to maintain a secure home network?
I try to enable auto-updates on all devices that support it or keep an eye out for security advisories for any other devices or software I use at home. I also enable multi-factor authentication for internet services that support it, especially personal banking, personal email, and social media. These are simple tips and practices for good cyber hygiene that anyone can incorporate to improve their online security and ensure your software or devices are up to date.
Want to learn more?
This is the last of a five-part series on common issues security teams face with remote workers. If you missed any of the earlier posts make sure to check them out:
- Part 1: Detecting Phishing Scams Disguised as Updates
- Part 2: Detecting Unusual VPN Access and Best Practices to Secure VPN Services
- Part 3: How to Detect Malware in the Guise of Productivity Tools
- Part 4: How to Detect Fraudulent Logins and Policy Violations Using UEBA
- Part 5: Best Practices for Personal and Corporate Device Usage

Cynthia Gonzalez
Senior Product Marketing Manager | Exabeam | Cynthia Gonzalez is a Senior Product Marketing Manager at Exabeam. An advocate for customers, she’s focused on their use of technology to enable and simplify day-to-day work activities. She is at her best when bridging the gap between sophisticated software products and the benefits customers can expect. She received a BA with majors in Economics and Spanish from the University of California, Berkeley.
More posts by Cynthia GonzalezLearn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.