In our first post in our two-part series on election security, we looked at vulnerabilities during political campaigns. In this post, we continue our discussion focusing on the voting system.
While there has been a lot of news coverage recently related to vulnerabilities with voting machines, these machines are just one piece of our complex American voting system. Our elaborate voting system alone comprises federal and state government agencies, vendors that supply the hardware and software for the voting machines, as well as national and local media. Security challenges exist throughout the entire system.
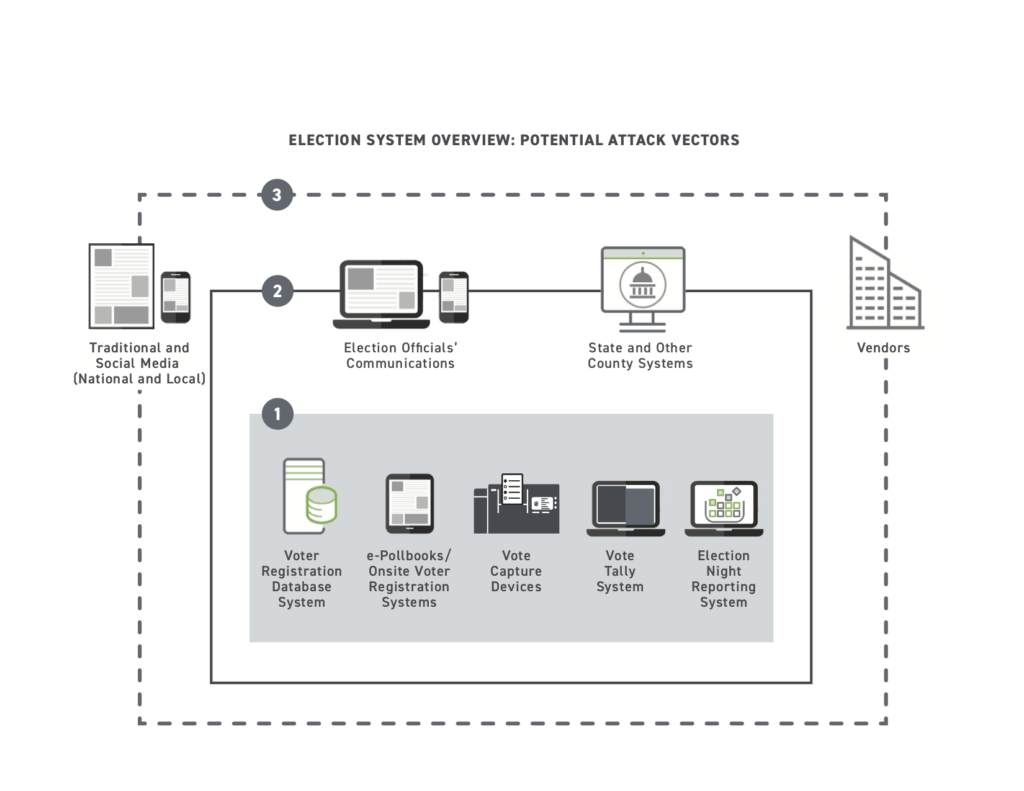
This overview of the election system captures the key devices and software vulnerable to exploitation including 1) the core systems that make elections run; 2) intermediary government systems that connect to other state/local systems and official communications; 3) external parties including social media from national and local media and vendors.
In the U.S., state and local governments are responsible for administering elections, which includes ensuring voting machines are not compromised. And while the federal government provides national-level security guidance, including testing standards for voting machines to verify that the systems have not been tampered with, state and local governments have the option to adopt these security standards, use their own, or a hybrid. They also have the option to have tests completed by private companies or local universities, as there are is no single federal test certification program.
In addition, there is no mandatory audit at any level to verify the integrity of the machines and testing procedures. While post-election audits can check both the voting equipment and procedures, state legislatures decide whether to require the audits. Currently, only 38 states plus the District of Columbia have post-election audits as defined by the National Conference of State Legislatures (NCSL). Opponents to the audits argue that they are time-consuming and error-prone since there is an element of hand counting paper records. Also, they note that newer systems have the ability to automatically provide an audit with a paper trail after someone has voted.
State and local governments are also responsible for managing the voter registration database system which contains the records of voters in their jurisdiction. Unfortunately, many of these database systems are outdated and ill-equipped to handle today’s cybersecurity threats, making it easier for adversaries to potentially delete or add voters. In addition, internet access to database systems, such as through public portals, increases security risks. In 2016, Russians were able to steal over 76,000 voters’ information after they successfully hacked into the State of Illinois election database by exploiting a vulnerability in the state’s online voter registration application website.
On the flip side, the decentralization of our election system, which includes over 10,000 different voting jurisdictions across our 50 states and 8,000 election offices on distributed networks, makes it difficult for attackers to launch a large-scale, coordinated attack. The number of voters served within each jurisdiction varies significantly. In some areas, the number of registered voters is below 100, whereas in larger metropolitan areas such as Los Angeles County, the numbers are in the millions, resulting in differences in the size of IT resources dedicated to each jurisdiction to prevent attacks.
The makeup of the voting machine market is a huge risk
Only three companies account for 92 percent of the voting machine market. Election Systems & Software has 50 percent, followed by Dominion Voting Systems and Hart InterCivic. Given only three companies serve the majority of U.S. voters, a compromise of just one of these three companies could have a significant impact on any election. Manipulation is not a formidable task given many of these machines are running outdated software with existing vulnerabilities. Some machines that have been distributed to various jurisdictions are still running Windows 7, which Microsoft stopped supporting on Jan. 14, 2020, and some were discovered to be running Windows 2000, which Microsoft stopped supporting in 2010. As transitioning to machines running newer Windows operating systems in time for the 2020 election may not be possible, Microsoft has committed to providing free updates for all certified voting machines in operation running on Windows 7. Additionally, with the support of federal funding in 2018 and potentially new funds in 2020, state and local counties have been upgrading their systems.
These machines also use a software-only security approach that offers less protection than a combination of software and hardware security. With a software-only approach, someone could enter a voting booth and slip a malicious memory card into the system and trick the system into recording a false number of votes cast.
“Machine learning-based behavioral analytics solutions can identify unusual behavior across a wide range of devices, including voting machines,” said Trevor Daughney, VP, Product Marketing at Exabeam. “Adding this layer of security can help improve the confidence in election outcomes by voters and politicians alike. Behavioral analytics could identify if a particular machine is producing more votes faster than others for example (like a bot is doing the voting instead of a human).”
Internet-connected devices increase risk
Our U.S. voting system is comprised of many different types of devices that serve different functions. It includes voting machines, electronic poll books that simplify the check-in procedure for voters, devices that tally the votes, systems that report the votes, plus all the systems managed by the various national and regional campaign teams as discussed earlier. Security experts note that web-based systems such as election-reporting websites, candidate websites and voter roll websites are easier to attack compared to a voting machine.
Many of these systems are IoT devices that have their unique security challenges. Often inexpensive IoT devices are shipped with factory-set, hardcoded passwords; they’re unable to be patched or updated; they have outdated protocols and lack encryption. IoT devices are also susceptible to botnets that can exploit large numbers of devices in a short period. This was the case with the Mirai botnet, which launched a massive distributed denial of service (DDoS) attack that exploited an estimated 100,000 unsecured IoT devices. A DDoS attack occurs when multiple machines operate together to attack one target, causing the system to crash and prevent legitimate users from accessing the system, potentially making digital election systems unavailable to voters. IoT attacks could also compromise a user’s browser to manipulate votes and cut power to polling stations.
Mobile voting, regarded by some as the future of voting despite the cautionary comments by security experts such as Ron Rivest, may be gaining traction because voting remotely can accommodate overseas voters, voters with disabilities and social distancing. The recent success in a pilot program in a board of supervisors election outside of Seattle suggests the convenience of e-voting likely contributed to an improvement in voter turnout. Yet the concern for cybersecurity breaches in mobile voting remains high with the main threat being that a breach would sow distrust in the election results and the system as a whole.
To put it in perspective, Steve Grewal who is on the Exabeam Federal Advisory Board says, “With mobile voting and paperless machines all interacting digitally, strong identity management will be absolutely critical in terms of attribution and traceability around the voting process. There will be a need for backend evidence and traceability to confirm that remote votes can be validated at the local and state level.
“Preparedness and readiness will be critical. The public sector has a series of security mandates and technical controls like 2FA, encryption, but not all agencies or their employees are equipped with the appropriate set of tools to do so. We are starting to see some activity where agencies are expanding in real time their infrastructure and corresponding security. Some tradeoffs taking place are: security may be deprioritized for the sake of functionality and corporate access to systems and services needs to be done in a secure fashion.”
Addressing vulnerabilities in our election system starts with voter fraud detection and behavior analytics
Despite these huge challenges, some measures can be taken to minimize the impact of attacks on our voting system — starting with detecting voter fraud. Early in the voting process, baselines for normal activity across all the systems mentioned earlier should be established. User and entity behavior analysis (UEBA) solutions in modern security information and event management (SIEM) platforms can detect anomalous behavior that would point to voter fraud.
For example, UEBA could flag large-scale changes in voter status occurring in voter registration database systems. It can also detect if a particular machine is producing more votes faster than others as a result of a malicious bot. “Entity analytics can also identify threats that older and outdated voting machines are susceptible to,” Nate Labadie, manager, Sales Engineering at Exabeam pointed out. “While some voting machines are appliances, which means log monitoring tools cannot be installed to detect anomalies, a UEBA tool can analyze appliance metadata such as firewall logs that can identify suspicious connections.”
UEBA solutions can also detect ransomware early as these attacks take several stages to execute. As a result, campaigns can take measures such as locking down systems and conducting frequent backups to prevent data loss and avoid having to pay extortion fees or face regulatory fines if voter PII is stolen.
Proactive response with SOAR helps understaffed election IT teams
For understaffed security teams, machine-based learning systems enable limited teams to operate 50 percent more efficiently through automation – which is essential given the scale and number of elections. Security orchestration, automation and response (SOAR), as part of a modern SIEM, can also orchestrate remediation in response to an identified anomaly through playbooks. SOAR also automatically identifies and prioritizes cybersecurity risks and responds to low-level security events, which is extremely useful for state and local government agencies that operate with small cybersecurity teams.
Republicans and Democrats unite to offer a helping hand
In late 2019, recognizing the seriousness of election attacks and the lack of security resources, former campaign managers for Hillary Clinton and Mitt Romney launched a non-profit organization, Defending Digital Campaigns (DDC), which offers free to low-cost security technology and services to federal election campaigns. Security services include email security services, anti-phishing, managed security services and more. Initial DDC efforts will be focused on helping the network of teams running campaigns.
Some experts predict that the 2020 election will be one of the most anticipated digital security event in U.S. history. Given the complexity of our election process and voting system, security automation and behavior analytics and security education can be a part of the solution for managing a secure voting process. But in acknowledging the effort required to secure these digital methods, voting by mail may now be considered more broadly for the November ballot.
Further Reading
Are Vulnerabilities in our U.S. Elections Insurmountable? Part 1
2020 U.S. Elections: Vulnerable to Cyberattacks? [infographic]
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!