On April 27, 2021, MITRE released a significant update to the MITRE ATT&CK framework which included several new and updated techniques, including T1553.006, code signing policy modification. I had submitted this technique to MITRE and I will explain this in more detail and offer guidelines on how you can detect activity that indicates the use of this technique in your network.
Introduction to Code Signing Policy Modification T1553.006
Adversaries are developing new malware to obtain initial access and persist in the victim’s network. Advanced persistent threats (APTs) develop custom malware that endpoint protection solutions do not have coverage to prevent. In some instances, APTs modify drivers to obtain kernel-level access to the operating system to further their objective. However, Windows provides Driver Signature Enforcement (DSE) which requires a valid certificate to install a driver — System Integrity Protection (SIP) is the macOS equivalent of DSE. Adversaries can modify the policy to switch to developer mode which bypasses DSE.
Detection
The security operations center (SOC) can detect the modification of the code policy with the correct visibility. Solutions such as an endpoint detection and response (EDR) provide the granular level of logging to identify when the DSE is modified.
For organizations without an EDR, sysmon is likely an alternative option to provide visibility on endpoints. Another option is to leverage native Windows logging to enable process creations and registry key modifications. The methods to identify this activity are the following:
- Command line monitoring for:
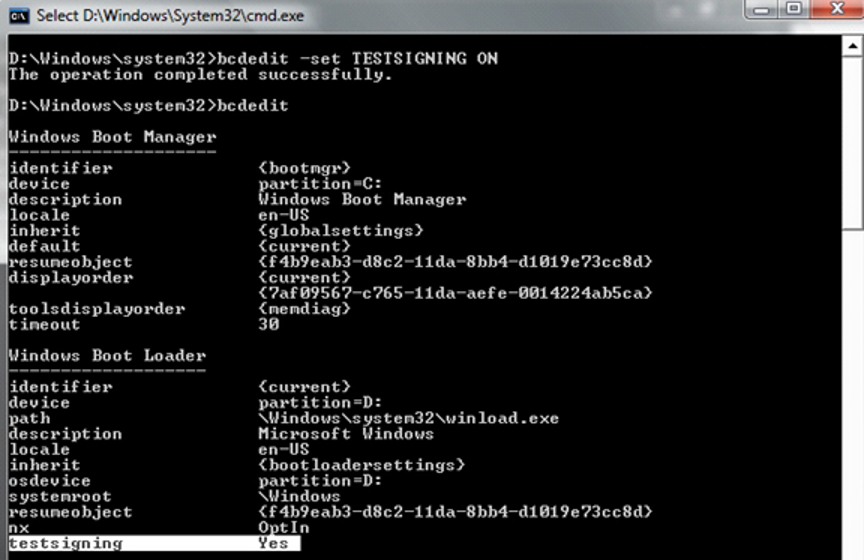
- Windows
bcdedit.exe -set TESTSIGNING ON
- Windows
- MacOS
csrutil disable

- Registry key modifications
Windows
HKCU\Software\Policies\Microsoft\Windows NT\Driver Signing
Modifications to the code signing policy isn’t likely to occur. However, if this is seen in an environment, it warrants an investigation. It is possible the credentials identified performing the activity are compromised. Therefore, it is important to have logs available for a minimum of 30 days to retroactively search for this activity.
Conclusion
Although APTs used this activity in the past, it is possible for an insider threat to leverage the same technique. Organizations need to implement a security in-depth strategy that focuses on multiple layers of protection and detection. Exabeam provides visibility into key techniques from the MITRE ATT&CK framework adversaries are leveraging to attack organizations. Exabeam customers will have coverage for T1553.006 in the latest content pack released this week.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












