Recently a new vulnerability named PrintNightmare CVE 2021-1675/34527 surfaced which scored 8.2/10 on the Common Vulnerability Scoring System. PrintNightmare allows an attacker to execute remote commands to gain full access to a domain controller and take over the whole domain — with user-level access. The vulnerability takes advantage of the Windows-native service called Print Spooler that is enabled by default on all Windows machines (servers and endpoints).
They are two distinct vulnerabilities.
It was initially released as a minor elevation of privilege vulnerability (CVE 2021-1675) and Microsoft released a patch for it. However, it was later exploited as a remote code execution (CVE 2021-34527) by researchers from Tencent & NSFOCUS Security Lab. Fortunately and unfortunately, both the vulnerabilities are similar but they are distinct. For CVE 1675, the attacker needs to have direct access to the machine to use a malicious DLL file to escalate privileges. While with CVE 34527, the attacker can remotely inject DLLs.
What is a Print Spooler service?
Print Spooler is a native Microsoft service that manages printing processes. The spooler accepts print jobs from computers/users and makes sure that printer resources are available. The spooler also schedules the order in which print jobs are sent to the print queue for printing. Every Microsoft machine (servers and endpoints) has this feature enabled by default. This is not the first exploit of this service. Over the past couple of years, there have been several exploits (CVE 2020-1048, CVE 2019-0759) and attackers have always found ways to exploit the vulnerability to get more details about the system, execute a remote code or to escalate the current privileges.
What Windows versions are impacted?
- Windows Server Version 2004
- Windows Server Version 2008
- Windows Server Version 2008R2
- Windows Server Version 2012
- Windows Server Version 2012R2
- Windows Server 2016
- Windows Server 2019
- Windows Server 20H2
- Windows 7
- Windows 8.1
- Windows 10
A significant impact: How attackers can exploit this vulnerability
- Domain administrator access: With domain administrator access, an attacker can get full control of the network.
- Credential stuffing: Attackers can use the domain password to use brute force against other sensitive accounts like social media, bank accounts, etc.
- Deploy malware/keylogger: Attackers can use keylogger, or any other malware to harm any user on your network.
MITRE ATT&CK mapping for PrintNightmare
MITRE ATT&CK techniques mapped to the PrintNightmare vulnerability:
- T1569.002 – System Services: Service Execution
- T1574.002 – Hijack Execution Flow: DLL Side Loading
- T1068 – Exploitation for Privilege Escalation
PrintNightmare detection by Exabeam
As there are multiple ways to exploit the vulnerability, there are multiple ways to detect PrintNightmare. Before proceeding, please make sure to enable these logs:
- 4688/1(Sysmon) – Process Creation logs
- 808 – Microsoft Windows PrintService/Admin
- 11 (Sysmon) – File Creation Logs
- 7 (Sysmon) – Image Load Logs
Into action: Detecting the exploit with Exabeam
You can find the exploit on any Github repository but please make sure to run it under a controlled environment (and only if you must run the exploit).
Detection case 1
Abnormal parent-child relationship for the processes:
- Event Code – 4688/1
- Process Name – PowerShell.exe or cmd.exe or werfault.exe
- Parent Process Name – spoolsv.exe
Detection case 2
Detecting remote print spooler driver load using file share logs:
- Event Code – 5145
- ShareName – \\*\IPC$
- AccessMask – 0x3
- RelativeTargetName – spoolss
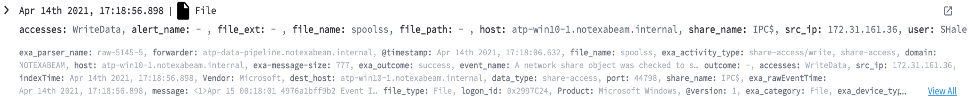
Caption : Detecting remote print spooler driver load using 5145
Detection case 3
Detecting abnormal DLL load via sysmon:
- Event Code – 11 or 7
- Image Name – spoolsv.exe
- Target File Name – \System32\spool\drivers\x64\3\* (Check for new DLLs added here)
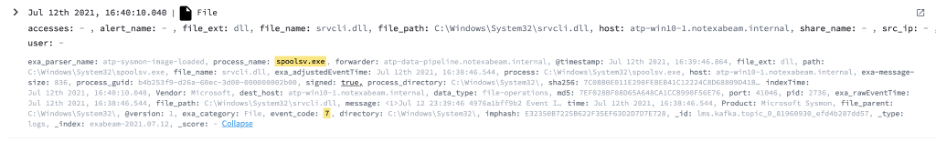
Caption: Detecting DLL load for spoolsv.exe using Sysmon
Detection case 4
Detecting failed spooler logs:
- Event Code – 808
- Image Name – C:\Windows\System32\spool\drivers\*
- Module Name – myexploit.dll or evil.dll or addcube.dll or rev.dll or rev2.dll or main64.dll or mimilib.dll
Detection case 5
Detecting unsigned DLL loading (NOTE: this could trigger some some false positives as it differs environment-to-environment ):
- Event Code – 7
- Image Name – spoolsv.exe
- Signed – False
Detection case 6
Detecting spoolsv registry changes:
- Event Code – 13
- TargetObject – HKLM\System\CurrentControlSet\Control\Print\Environments\Windows x64\Drivers\Version-*\<new dll file>
In addition to Data Lake queries, with Exabeam’s behavioral analytics-based detection, you can hunt for any abnormal process spawned by spoolsv which is abnormal for the user or any asset. You can easily search for the right set of rules in Exabeam’s Threat Hunter that will help you stitch the whole attack timeline together.
How do you patch this?
Microsoft released a patch for the Windows versions impacted Security Update Guide – Microsoft Security Response Center but we have seen reports that attackers can still exploit the vulnerability.
Alternatively, if you don’t require printspooler on your domain controllers, it is advisable to disable it. You can disable the printspooler server altogether, or alternatively, disable it until the Microsoft patch is verified.
- You can disable it via GPO if you configured printspooler via GPO.
- If you don’t have it enabled in the GPO, check to see if it is running as a service under services.
You can check your exposure for this vulnerability by reviewing this flow chart:
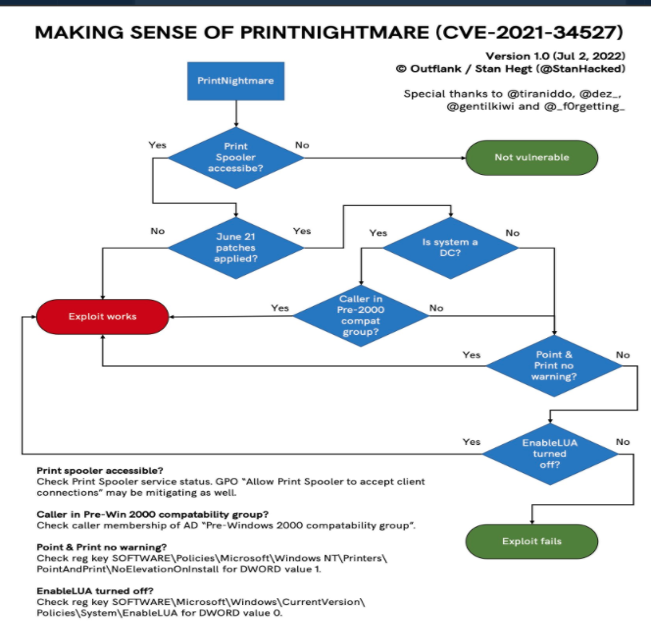
Caption: The flow chart demonstrates the exposure to PrintNightmare1
Conclusion
PrintNightmare is a critical vulnerability that can have a dramatic impact on a company’s operations if exploited by attackers. It is recommended to monitor the print spooler service closely and disable the print spooler service if not necessary. With this exploit an adversary gains the ability to escalate privileges and execute remote code injection.
References
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












