With the demand to improve sales and efficiency, more retailers have been moving to online methods to expand their capabilities. The pandemic has also fueled this shift as many organizations started trading online for the first time, while others have seen an abundant increase in web traffic and transactions within their e-commerce platforms. The migration of point of sale (POS) management systems to the cloud has also expanded the POS security threat landscape and provided cybercriminals with a very popular vector for exploitation.
It is a well-known fact that retailers are holding vast databases of Personally Identifiable Information (PII) and credit card data, which allows opportunists, and especially threat groups, to take advantage of the many possible areas of vulnerability — from system intrusion and social engineering to the “dishonorable mention” of denial of service attacks. These risks also include the human element; a high employee turnaround is also common due to temporary or seasonal contracts, as is the daily engagement with third-party distributors and vendors. These, in effect, give rise to insider threats due to incongruent or inconsistent security practices.
In this article:
Finding a way in
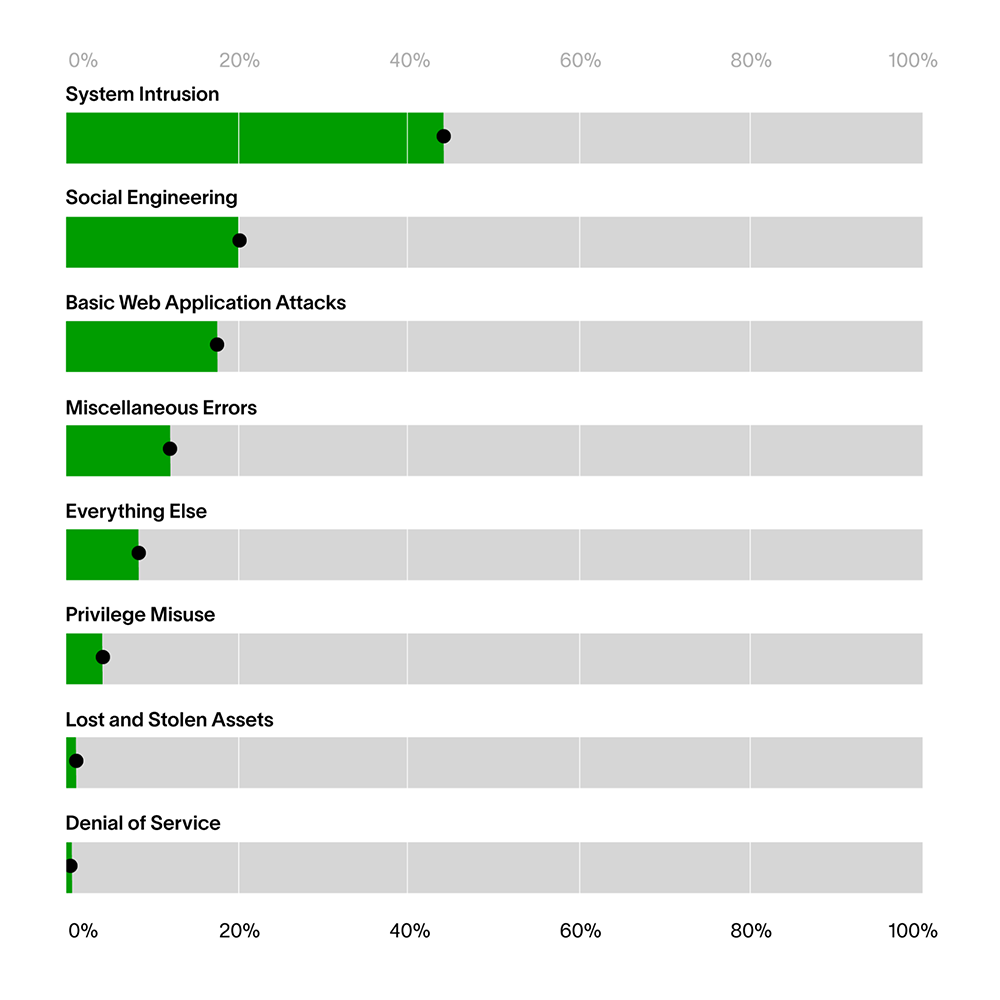
Cybercriminals — even malicious insiders — are becoming increasingly sophisticated and elusive in their tactics, techniques, and procedures (TTPs) even with simple tools downloaded from the internet. The majority of attacks often begin with a well-crafted social engineering campaign. This may involve a duration of pretexting (47%) while information is gathered from various individuals and affiliates, which is then usually followed by a convincing (and in most cases, spoofed) email(53%) sent to employees, which directs them to download a file or click a malicious link.
Most cybercriminals often follow the rule to remain as stealthy as possible to evade detection or trigger security alerts. The idea is to establish persistence, use remote access tools and credential dumpers to gain initial access, start to move laterally (aka. island hopping or leapfrogging), and deploy payloads throughout the POS environment. Ultimately, the campaigns intend to exfiltrate PII data or deploy ransomware.
Retail facts from the 2021 Verizon DBIR:
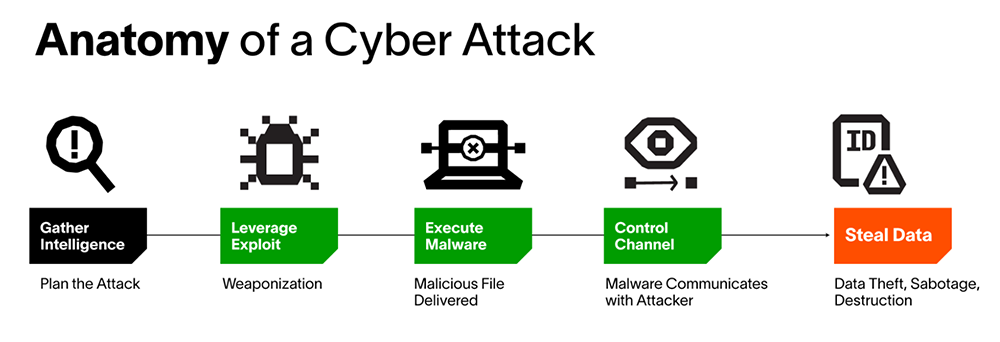
Thinking like a cybercriminal
Let’s assume the position of a cybercriminal and expose some of the possible paths they may take during a POS attack. For this section, I will think like an attacker and walk you through my malicious processes.
Mission Statement: I am part of an organized criminal group that is set on stealing credit cards and personal customer information (PII) for financial gain.
My Targets: The employees of Retail, Inc. — specifically, their POS Management Systems and their card processing systems. This contains both PII and CC information.
Scope: Numerous locations around the UK and the EU.
STAGE 1 – Reconnaissance
Through various methods of social engineering, I have profiled my targets over a period of time.
I have gained some knowledge of their environment; their operations; some of their 3rd parties and affiliates. Additionally, I have identified some members of staff and their roles.
STAGES 2 & 3 — Weaponization and Delivery
I use spear phishing to send one or more controlled emails to targeted victims either at Retail, Inc. and/or its third parties or partners. The sender will be a number of spoofed email addresses.
I shall vary the content in these emails, either directing the victim to a doppelganger domain via a malicious link, or to download a weaponized file.
Once clicked, the victim will unknowingly have their system infected.
STAGE 4 – Exploitation via Control Channel
Once the payload is activated, the system is infected and I can now start to establish further persistence.
Things I may decide to do:
- Use a credential dumper, trigger a password hash attack or perhaps install a root-kit which will run at boot-up to steal as many system and user credentials as possible.
- Build a profile of the system I am on; understand environment variables (for example, network connections; registry values; running processes and applications)
- Attempt to disable local security measures such as AV or a local firewall.
Once I have obtained user credentials, I can impersonate any acquired user account.
I can now use my user privileges to:
- Execute a new process if I wish, or migrate into the memory of a normal process/application, so there is no suspicion of any of these activities.
- Use an MD5 collision to impersonate any process and possibly even evade Application Whitelisting tools with customer installers/malware (akin to Flame malware).
PROGRESS: This is my base machine, and will be used for exfiltration later.
My investigations allow me to understand where this machine connects. I discover the server network and also the POS network as well as the legitimate network connections through which data is transmitted.
- I can use the user credential to laterally move across the environment gathering information but essentially to steal more user credentials and infect more machines on this network.
I will now attempt to hop onto the POS network and infect a machine using the user privileges I obtained.
- I have customized malware which will take a memory dump of the POS system that I will use to steal credit card data.
PROGRESS: I have successfully pivoted to a POS network and a POS system.
STAGE 5 – Installation
- I will upload a memory dumping tool which is masquerading as a legitimate MD5 executable to evade local security. (MD5 collision)
This tool provides a list of all the current running processes on the POS system, including the credit card software.
PROGRESS: I have successfully deployed customized malware that is masquerading as a legitimate MD5 process. This malware is gathering information on the POS system, specifically the POS application (POS.exe).
STAGE 6 – Action
- With the process ID for POS.exe obtained. I will use my malware to locally dump the process memory of POS.exe which has details of all the credit cards that have been processed since the POS application has been running.
- I have dumped the memory in a local folder on the POS system.
- With my legitimate open network connection, I can move the memory dump to the base machine.
PROGRESS: PII and CC data has been offloaded locally. Ready for exfiltration.
Note: This is very similar to how the BlackPOS attack exfiltrated data from Target and Home Depot.
Clean Up and Exfiltration:
- I use a zipping tool and batch file, which compresses the memory dumps.
- I download the dumps to a share on the base machine (I can set up cron jobs to do this low and slow to evade detection).
- I remove the share and delete the dump folder.
- I also delete any audit logs.
PROGRESS: Data exfiltration complete. Tracks removed.
Food for thought
Many organizations have various security investments to try and reduce their risk. An investigation should be focused on asking the right questions pre- or post-breach. With security tooling in mind, these are the types of key attack identifiers we should be looking to clearly visualize in our armory. And remember, the first time ANY activity occurs for a user, endpoint, server, or service account should be recorded and called out as interesting by the system.
| Network Traffic | Abnormal User Agents | Cryptominers | Endpoint Activity | Retail Security Stack alerts |
|---|---|---|---|---|
| New/abnormal connections TO a new country or ISP | More than two new user agents used by the user in the same session | Process ending with ‘miner.exe’ has been run on this asset | Base64 string in command line execution on this asset | First security alert name on the asset |
| New/abnormal connections FROM a new country | First Multipurpose Internet Mail Extensions (MIME) type for organization or user | Connection to IP associated with cryptocurrency mining | A ping command used a hex decoded IP address on this asset | First security alert (by name) in the organization |
| TOR source/ destination IPs | First user agent string for user | Host has browsed to a known coinmining/ shadowmining domain | Base64 string in command line | First security alert (by name) in the zone |
| New traffic on a new Port | First activity using this mobile web browser/app for this user to a new domain | User has browsed to a known coinmining/ shadowmining domain | Possible Meterpeter/ Cobalt Strike usage | First security alert (by name) in the asset |
| Asset visited an IP instead of a Domain | New user account creation or elevated permissions on an existing system | User has connected to a known coinmining/ shadowmining IP | Malicious PowerShell script used via get cmdlets on the asset | First security alert for this asset in the organization |
When decisions are made on inconsistent or inaccurate data, it limits the ability to implement an effective security strategy. In order to understand the broadening attack surface, organizations require a comprehensive level of visibility across users, devices, and networks. Security analytics can enhance the existing security stack and data repository covering dozens of key technologies like endpoint, identity security, network, cloud, and more. To understand normal and detect anomalies even as normal keeps changing, all user and device activities need a baseline. Analytics then help identify risk-based prioritization to automatically assign risk scores to all events, calling out first-time and other new events to prioritize triage, investigation, and response. This will provide a means to detect and respond to cyber threats more effectively.
A multi-layered strategy that encompasses both machine learning and automation is vital here. Using analytics to understand the nuances of the various parts of an organization, understand normal and thus flag anomalous activity. Because of this, it is vital that all departments, locations, and affiliates understand the risk of any new tooling and workflows and how they fit into a consistent and continuously reviewed security policy.
Want to learn more about threat detection, investigation, and response?

When incidents happen, security teams are under tremendous pressure. In such a hectic environment, they might not follow proper incident response procedures to limit the damage. Lacking the right information or a formal plan, many overreact, shutting down or patching too many systems and interrupting operations in a way that magnifies the business risk. In some cases, a rush to respond may eliminate valuable forensic information needed to isolate and eradicate an attack.
This eBook is our take on why an incident response plan should be a critical piece of your cybersecurity strategy. It provides some valuable guidelines and tips to help CISOs and incident responders succeed.
Read our eBook, Why You Need an Incident Response Plan.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












