It is evident that ransomware attacks are still apparent and on the rise. In 2021 ransomware attacks increased by 13 percent year over year — more than the past five years combined. Organizations are understandably concerned about their ability to not only prevent attacks, but to recover should they be targeted. Addressing the problem in its entirety is a common defensive oversight — specially, for example, at the point where ransomware performs reconnaissance on systems before initiating.
Empowering oneself with the correct knowledge can help one to begin to understand the likelihood of an emerging threat, and thus allow an organization to take necessary precautionary measures.
In this article:
The ransomware landscape
Ransomware is still a go-to tactic in 2022. It has been, and still is, a highly successful and lucrative form of extortion. As we know, the first attack was identified in 1989, and you may also recall the infamous CryptoLocker variant of 2013 which demanded a ransom of $300 to decrypt files — an amount that seems abundantly small compared to the incident volumes and demands for payments today.
Attacks have also diversified with the recent variant of GoodWill, a Robin Hood-esque group that requests that its victims help vulnerable people by performing a sequence of tasks, such as feeding the homeless, donating clothes, or providing financial assistance to hospitals. While we also see well-organized and multifaceted groups such as Conti, which have had a heavy impact on government agencies by causing disruption of critical services like customs, export, and payment systems.
Ransomware as a service (RaaS) is also not to be ignored. These offer any opportunist the ability to purchase pre-built kits to launch attacks with little to no knowledge. The kits are offered at a minimal cost on the dark web, and offer full subscription and support models.
The human element
What has been identified is that most, if not all ransomware attacks involve the human element, i.e., the exploit of a user and user credentials. Additional credentials may also be stolen and leveraged for future exploits, while the majority of attacks can last only minutes. They are often part of a more integrated process. Attackers frequently employ a distribution campaign, using techniques like social engineering and phishing to provide links to weaponized websites to force victims to download a dropper to initiate the infection process.
This malicious process then downloads an executable file that installs the ransomware, enabling it to embed itself onto the target system. The ransomware then scans the infected machine and wider accessible network resources for content to encrypt. It’s after that point when the ransom demand is presented to the victim, along with instructions on how to pay.
Addressing the emerging ransomware threat
Time is of the essence. There are some key points where organizations can start to understand and start to disrupt active ransomware attacks.
In the early phases of detecting a ransomware incident, one can attempt to identify the Indicators of Compromise (IOC). The only problem is that these IOCs usually only exist after attacks have been effective and reported back to a vendor. Additionally, many ransomware attacks now use new or zero-day exploits to circumvent defenses. As a result, the gap between the publication of a new vulnerability and its use in a ransomware attack can be very short.
There are only a few phases where an organization can disrupt an active ransomware. This is described in the table below.
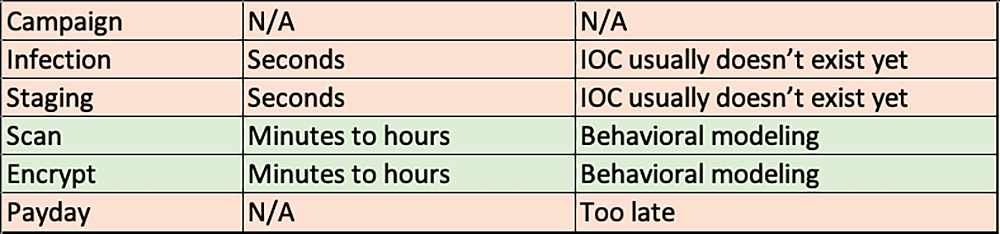
There is hope during the “Encypt” phase where endpoint security vendors can disrupt the attack for known variants, or where customized signatures may have been developed for specific activity. But to defend completely against zero-day ransomware would mean disrupting users from their normal operation, as well as adding huge overhead to managing the various systems within an environment.
The real opportunity to detect an emerging ransomware attack arises during the “Scan” phase. At this time systems on the network are being accessed, using the stolen user credentials, for files/locations to encrypt and also checking that endpoints can connect to the cybercriminal’s command-and-control center. These behaviors cannot be identified using simple correlation rules, due to the complexity and volume. Using a cross-layered detection mechanism like User and Entity Behavior Analytics (UEBA) can help identify key behavioral patterns such as this throughout an environment. This helps to paint a more holistic picture of an emerging threat and possible attack scenarios.
- Some examples are:To quickly identify a compromised user performing actions outside the realms of their norm
- Never-before-seen file executions or abnormal network connections on an endpoint
While mapping these seamlessly into a timeline of events, analytics can be leveraged to understand what is normal versus what is abnormal, subsequently identifying key risk indicators.
The use of security tools such as firewalls, intrusion detection systems (IDS)/intrusion prevention systems (IPS), or endpoint security can be extremely helpful in preventing the initial infection. However, once these defenses are penetrated, security teams are often left to scramble to manage disparate products. Planning for such an event is imperative, so implementing focused playbook actions for triage and attack prevention is essential — for example, orchestrating specific actions to collect endpoint telemetry using an endpoint detection and response (EDR) tool, isolating a host, or blocking an IP address.
With ransomware on the rise, we must accept that it is no longer if, but when an attack will occur. By identifying the principal areas where detection can be improved while being prepared to employ an effective response policy, one can start on the journey to seize the breach and defeat ransomware attackers before it’s too late.
Learn more about ransomware detection and response
Read our white paper, Using a Layered Approach to Improve Ransomware Detection and Response.

Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













