The banking industry faces numerous challenges, with insider threats ranking at the top. Contrary to popular belief, insider threats play a significant role in cyberattacks, not just involving malicious employees. In this blog post, we’ll explore the different types of insider threats, why banks are attractive targets, and how the right technology can help protect against them.
In this article:
- Understanding insider threats in the banking industry
- Factors making banks vulnerable to cyberattacks
- The need for solid detection solutions
- Identifying insider threats using behavior analytics
- Assessing the scope and consequences of an insider attack
- Conclusion
Understanding insider threats in the banking industry
Unpopular opinion: every banking breach making headlines is a result of insider threats. Let’s discuss.
The term “insider threat” might evoke images of malicious employees, but it’s not always that straightforward. Let’s look at how these threats might look.
Insider threats generally fall into three categories:
- Malicious insiders — These individuals harbor ill intentions and purposefully misuse their access rights to exfiltrate sensitive data, disrupt operations, or inflict damage on the organization. Malicious insiders may be disgruntled employees, corporate spies, or those manipulated by external adversaries.
- Negligent insiders — Negligent insiders inadvertently cause security incidents due to their recklessness or lack of awareness. Instances of negligent insider behavior include succumbing to phishing attacks, disclosing sensitive information on public platforms, or using weak passwords.
- Compromised insiders — These are employees, interns, and third parties with legitimate access whose credentials or devices have been seized by external attackers. These attackers use the compromised insider’s access to infiltrate the organization and execute malicious activities while posing as authorized users.
As stated in the 2022 Verizon Data Breach Investigations Report, 26% of incidents are attributed to malicious insiders, 56% to negligent insiders, and 18% to compromised insiders. Cyberattacks in the banking industry have reached staggering levels, with an estimated cost of $5.97 million per breach, according to the 2022 Cost of a Data Breach report — more than a million dollars above the overall average.
In every major breach, including those affecting banks, the common denominator continues to be compromised access to systems, allowing attackers to move freely within the victim’s environment. This technique is far from new. In the early 1990s, dumpster divers were able to find sticky notes containing passwords to legacy systems. So why do attackers still use this technique today? The answer is simple. Because it still works, and there are few solutions on the market designed to detect compromised credentials.
Factors making banks vulnerable to cyberattacks
There are a variety of things that make banks such attractive targets for cybercriminals:
- Rapid digitization — As banks embrace digital technology to offer convenience and accessibility to customers, they inadvertently create more vulnerabilities. The growth of these applications opens up new opportunities for attackers to manipulate these tools.
- Adoption of cloud technology — The shift towards cloud technology could potentially expose banks to additional risks, especially if they haven’t implemented proper security measures.
- Rise of remote and hybrid workers — The increase in remote and hybrid work environments expands the surface area for attackers to access systems, making breaches more likely. This also increases the use of personal devices, which may not have the necessary levels of protection.
- Ineffective cybersecurity solutions platforms — Traditional security solutions struggle to keep up with modern, constantly evolving threats. Understaffed security teams need new cloud-native solutions that consistently and repeatedly generate attack resolutions.
The need for solid detection solutions
With these factors making banks attractive targets, the need for solid solutions is even greater. The cybersecurity industry has focused on preventing breaches, but has often neglected to invest in detection technology for when prevention fails.
For example, the hacking gang Lapsus$ has successfully compromised major companies like Microsoft, Samsung, and Okta by socially engineering employees’ credentials. The group recruits employees via social media and secure messaging apps, allowing them to move freely within networks as seemingly legitimate users.
Identifying insider threats using behavior analytics
Detecting these types of insider threats effectively requires a deep understanding of the normal access patterns for each user within an organization. This knowledge is essential for identifying abnormalities and potential breaches. A behavior-based approach is key to detecting and thwarting insider threats.
The illustration below shows the progression of a Lapsus$ attack experienced by an Exabeam customer. By utilizing the Exabeam Security Operation Platform’s Advanced Analytics app, the system was able to detect several notable events. For example, a user logging in from South America and Europe simultaneously or accessing an unusually large number of assets triggered a Notable User alert just three hours into the attack.
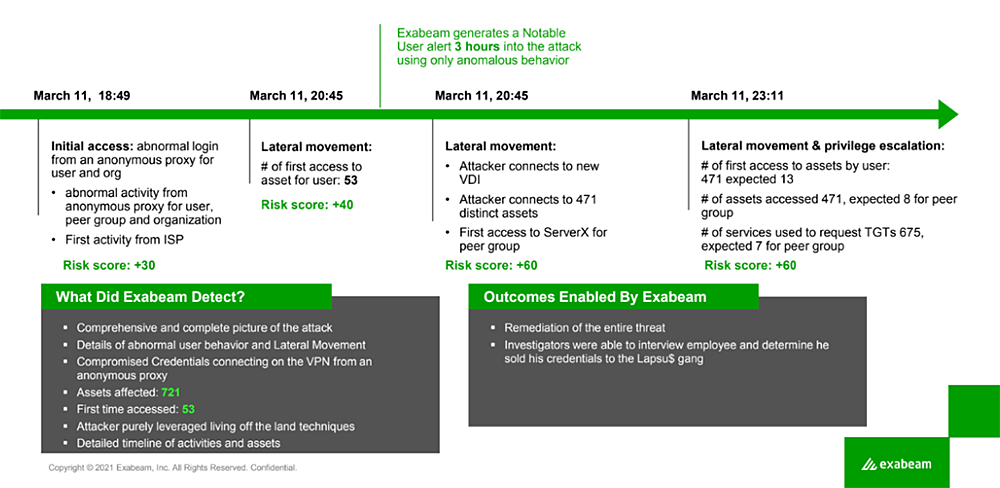
The ability to detect these anomalies was possible because we had a comprehensive understanding of the customer’s normal access patterns. As a result, we were able to highlight the abnormal behavior. The key to effective detection is being able to differentiate between ordinary and unusual behavior. To achieve this, it’s elemental to establish a normal behavioral baseline for each user. Without this foundation, detecting abnormal credential usage becomes nearly impossible.
Assessing the scope and consequences of an insider attack
Every attack follows a progression consisting of a beginning, middle, and end. In many cases, by the time a security team receives an alert, the attack has already reached its midpoint. To accurately determine the extent and impact of an attack, it’s necessary to uncover the entire scope of the breach, rather than focusing on isolated incidents.
Exabeam Smart TimelinesTM offer a comprehensive view of events, enabling security teams to answer crucial questions, such as:
- How did the attacker gain entry?
- Which locations and assets were accessed during the incident?
- How many assets were accessed?
Smart Timelines revolutionize the quest to track lateral movement within an organization, providing a much-needed alternative to legacy security information and event management (SIEM) solutions. This automated approach eliminates the need for highly skilled security operations staff to manually correlate events, often derived from obscure raw log data gathered from multiple sources.
By visually representing the sequence of user and device activity, Smart Timelines drastically reduce the time and effort required for manual correlation. This allows security operations teams to rapidly pinpoint anomalous behavior and assess potential risks, facilitating the discovery of a complete narrative of an attack and its overall impact. Figure 2 below offers another example of how this technology can reveal critical insights that might otherwise go unnoticed.
User behaviors — especially with service accounts — often provide critical warnings that enable organizations to mitigate and prevent security threats. To manage insider threats based on behaviors, it’s essential to establish a normal behavior baseline for each user. By doing so, security teams can effectively detect and respond to insider threats, minimizing the risk and potential damage of cyberattacks.
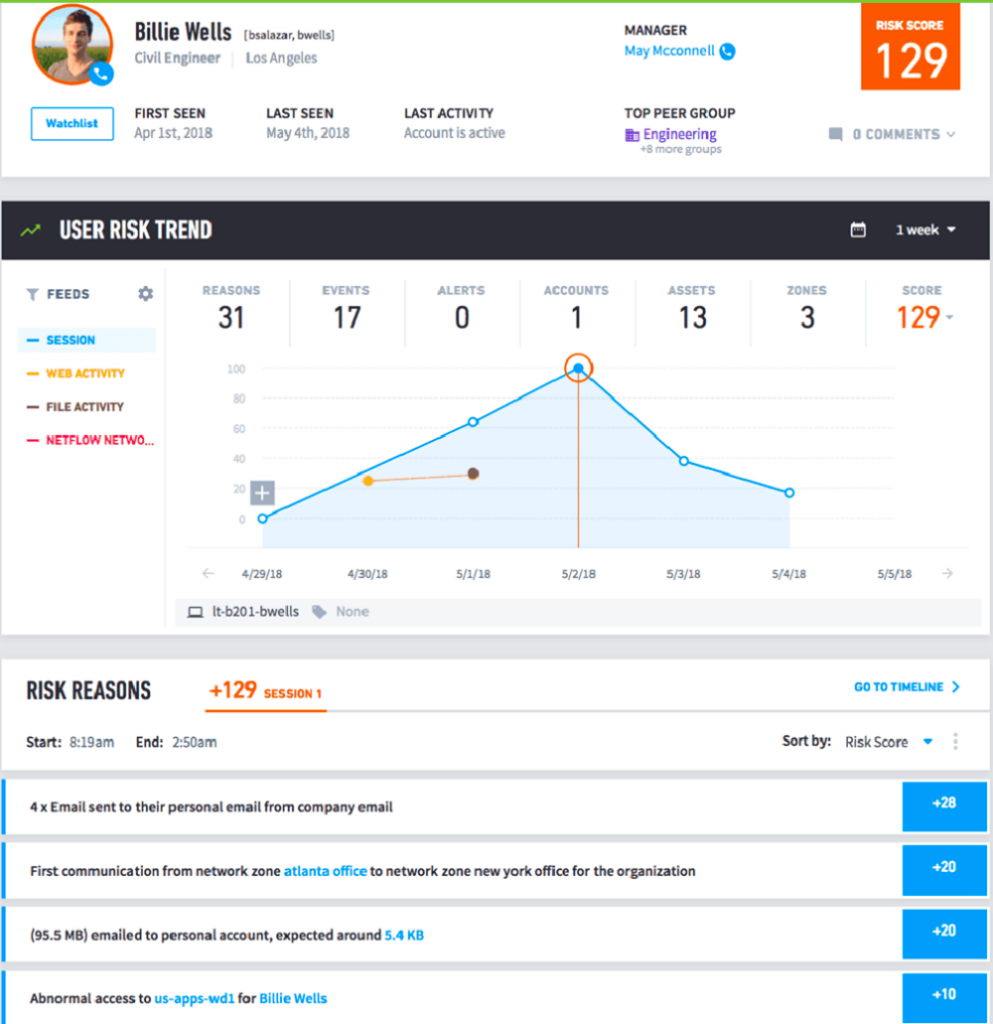
Conclusion
Insider threats aren’t something any bank can afford to ignore, as they continue to be a primary attack type. Implementing the right security solutions can help you:
- Distinguish normal from abnormal behavior
- Process and analyze vast amounts of data from various systems
- Minimize the number of alerts that consume security teams’ time and resources with investigations
- Thoroughly evaluate and address the ramifications of an attack
By proactively tackling insider threats, banks can significantly reduce the likelihood of devastating cyberattacks, safeguarding their customers and assets in the process.
Want to learn more about defending against insider threats?
Do you know what the biggest threat is to your organization? The answer may surprise you. It’s your own employees, contractors, and other insiders. These trusted insiders have authorized access to sensitive information and can cause significant harm to your organization, whether they mean to or not.
Insider threats are a growing concern for organizations worldwide, and it’s essential to understand the risks they pose and how to defend against them. That’s why we’ve created this comprehensive guide to help you better understand what insider threats are and how to protect your organization from them.
Read this eBook to learn about:
- What insider threats are and why they’re a growing concern
- The importance of simulation and security training for defending against insider threats
- A modern approach to insider threat detection, including real-world examples and case studies
- Advanced best practices for insider threat programs, including data science, data feed detection points, and use cases.
With this guide, you’ll know how to improve your organization’s overall security posture with faster, easier, and more accurate insider threat detection, investigation, and response. Download now!

Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













