If you operate a SIEM, you probably deeply sympathize with what I’m about to say. SIEMs are over priced. More accurately, SIEMs are overpriced compared to the value they actually provide to their customers. Not only are these systems responsible for draining security budgets, they aren’t effective in helping customers to effectively manage security incidents.
The Economics of SIEMs (and Razors)
All legacy SIEMs have at least one thing in common, some form of data volume based pricing. This pricing model leads to large, unpredictable bills and in some ways parallels another unpopular pricing model; that of razors.

To illustrate my point let’s consider the following:
- Both are expensive, although orders of magnitudes different in how expensive. A Mach3 starter kit might run you $8 and it includes a handle and a single blade, which is just enough to get you started. In the world of SIEMs the initial deployment can easily cost many organizations over $1 million dollars.
- For both products the starter pack won’t get you far. A million dollars into your SIEM project you’re good to go right? Nope. In the same way that with your Mach3 will constantly need expensive razor blades in order for you to have semi-decent user experience, SIEMs will need data to be useful. The more data you put into your SIEM the more it’s going to cost you. Did you just change firewalls? Oops! That extra log data the new firewall creates is going to increase your SIEM bill. Did you just invest in some cool new detection technology you want to include in your SIEM correlation rules? Well, that’s another “razor blade”. In a recent report by Eric Ogren at 451 Research, he comments about this situation, remarking “if a SIEM cost $1m to buy, it is not uncommon to see $3-4m in operating costs.”
- This creates a situation not unlike that of razors where the more you use your SIEM, the more it costs you. (For everyone’s sake and also to bring us more rapidly to the actual point of this article, this is where we part ways with my razor blade analogy.) In fact, for SIEMs this volume based pricing is actually prohibitive to the goal of getting all of your data into one place so you can analyze it for threats. It incentivizes security teams to keep the bare minimum amount of data as opposed to the data they might actually need.
The Stages of Security Management
With near ubiquitous deployment among corporations large and small, SIEMs have become the de facto security management tool. They were designed to help customers effectively detect and respond to security incidents. To do that, three things need to happen:
- Collection – The appropriate data must be collected so that it can be used for analysis, or detection of threats.
- Detection – Threats need to be detected. This could be with good old static correlation or with newer technologies like behavioral analytics.
- Response – Once a threat has been detected, it will need to be responded to. This response can vary widely but typically will include investigation, containment, mitigation, or remediation.
15 Years of Practice and Still Stuck on Collection
Most solutions in the SIEM market have been around for 10 to 15 years. With all this time in market, one would assume that these de facto kings of security management would have these three items covered, right? Let’s have a look:
- Collection – Yes. SIEMs can get all of the required data in one place, however the volume based pricing models legacy SIEMs use is counterproductive to that goal. Lack of budget or willingness to shell it out for log management creates a situation where many organizations simply do not collect all of the information they would like to, and suffer from security blind spots as a result.
- Detection – Legacy SIEMs by and large rely on static correlation for detection which is unable to detect unknown attacks or complex attacks that involve lateral movement. This is inadequate for dealing with today’s threats.
- Response – Most legacy SIEMs only offer case management. While it’s important, it doesn’t actually help Security teams keep up with the massive workloads they face.
In summary, you have an expensive security tool that collects data, but not all of it because that would be cost prohibitive; can’t detect complex modern threats, and doesn’t reduce response times.
A Staggering Value Mismatch

Legacy SIEMs are charging the most for the easiest task (getting data into one place), while offering little to no value in other areas that would really be impactful to security organizations such as finding threats and efficiently responding to them.
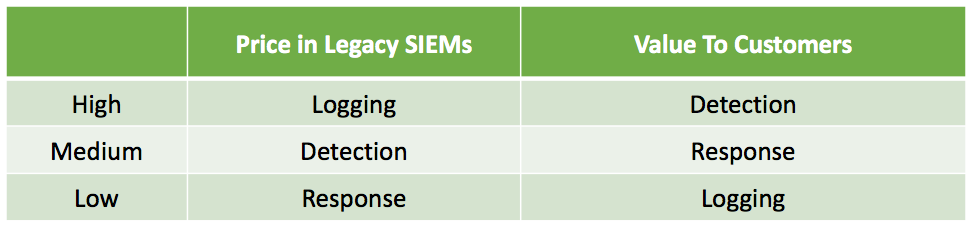
Exabeam’s Security Management Platform does just that, it breaks free from volume based pricing models by offering unlimited logging using a cost effective and highly predictable user-based pricing model, detects threats with its market leading User and Entity Behavior Analytics (UEBA) solution, and makes use of API based security orchestration and workflow automation to greatly improve the productivity of Security Operations Centers.What this all boils down to is a mismatch between price and value which will eventually need to be addressed by SIEM vendors as their customers become increasingly dissatisfied with the arrangement. SIEM vendors need to adopt pricing models that reflect the values of their customers.
Learn more about the Exabeam Security Management Platform.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












