Exabeam Security Log Management — Because Security Operations Isn’t IT Operations
Enterprises of all sizes hire experienced security professionals to protect the company from motivated adversaries and don’t rely on IT admins and site reliability engineers to handle cybersecurity. Yet, for threat detection, investigation, and hunting, many security teams are asked to use IT log management tools designed to troubleshoot bugs and upload log bundles to support tickets. Security investigation is fundamentally different from IT troubleshooting. While developers leave “debug traces” in their code to trace the failures in the sequential execution of software code, security threat actors delete all traces of their actions to avoid detection and move laterally.
Many log management solutions are born as IT operations/observability tools, and vendors later window-dress them for security buyers. Exabeam has created a new category: Security Log Management, a cloud-native log management solution built from the ground up for cybersecurity professionals.
In this article:
- Quickly build patterns and trends across petabytes of data
- Log data is transformed into security subjects to be investigated, and their activities
- All the adventure of threat hunting, without the pain of queries and regex syntax
- Quickly pivot from search to detection rules
- Built-in threat intelligence
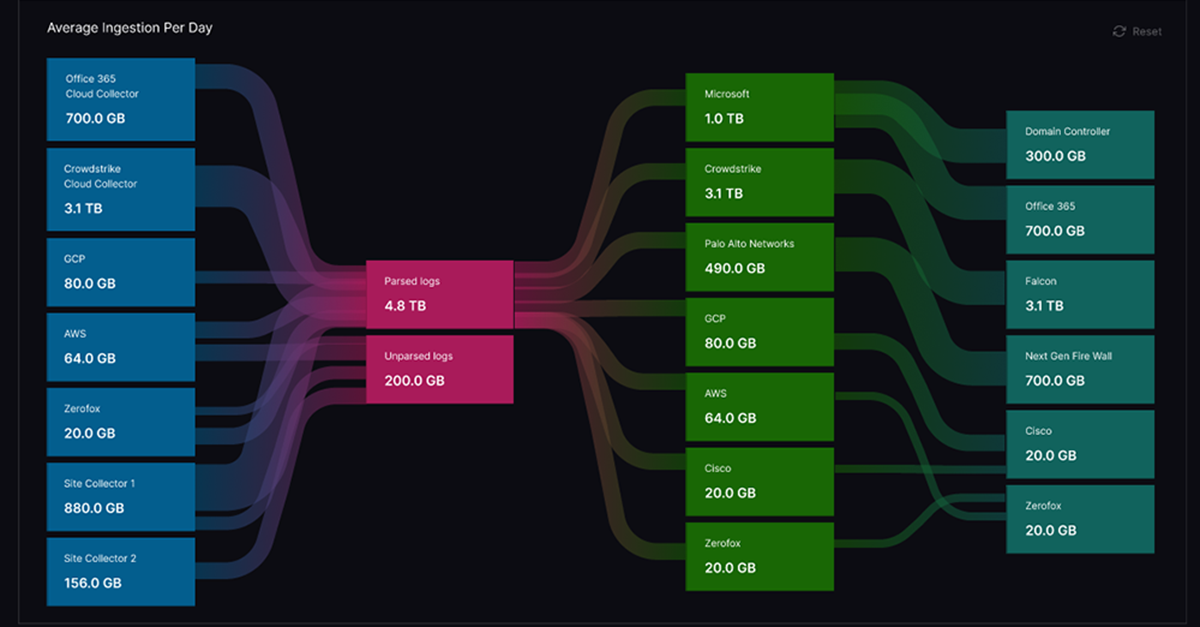
- Get granular consumption visibility
- Get guidance on your security coverage based on your data
- Avoid business risk — upgrade to Exabeam Security Log Management
Quickly build patterns and trends across petabytes of data
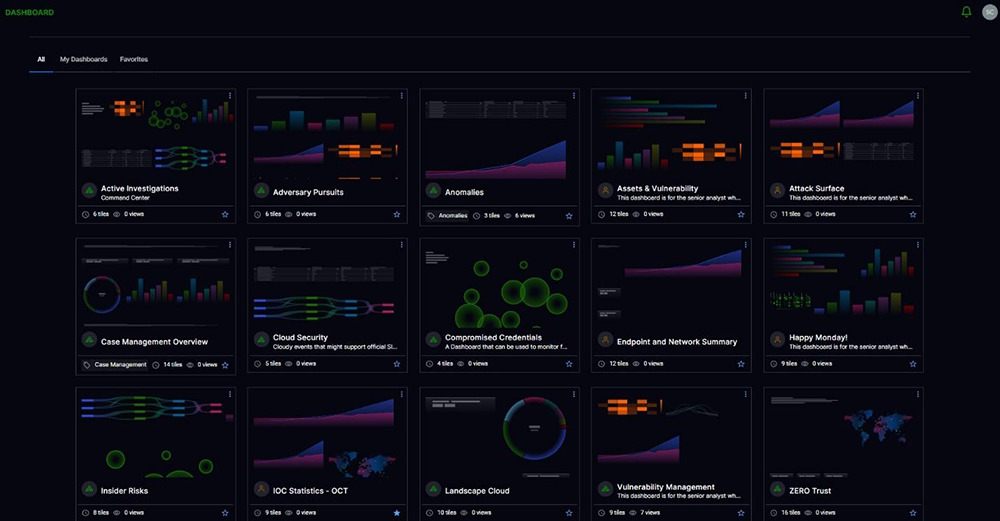
In my conversations with global CISOs, many have said that to get a summary of their organizations’ daily risk and security posture, they primarily use business intelligence (BI) tools like Tableau or PowerBI. While their IT log management tools have some dashboarding capabilities (with embedded open-source visualization tools like Grafana or Kibana), security teams must move all their data into SQL databases to render performance dashboards in BI tools.
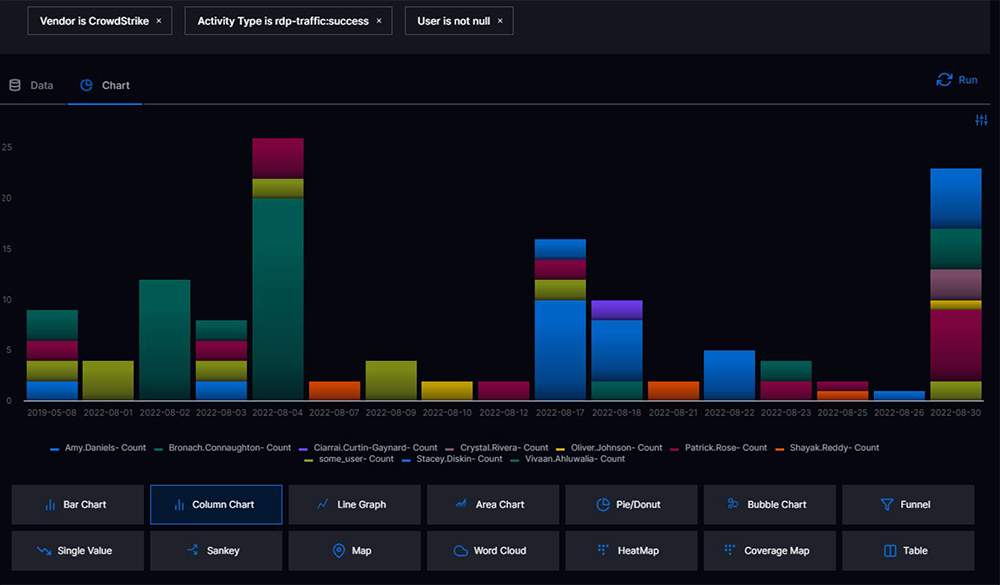
Exabeam Security Log Management is integrated with the Dashboards app, offering the ability to quickly create visualizations from parsed log data through pre-built compliance reports, or customized reports and dashboards. 14 different pre-built chart types, including a Coverage Map, allow you to build a dashboard in a minute with just a few clicks. Security analysts and CISOs alike will appreciate this capability.
Log data is transformed into security subjects to be investigated and their activities
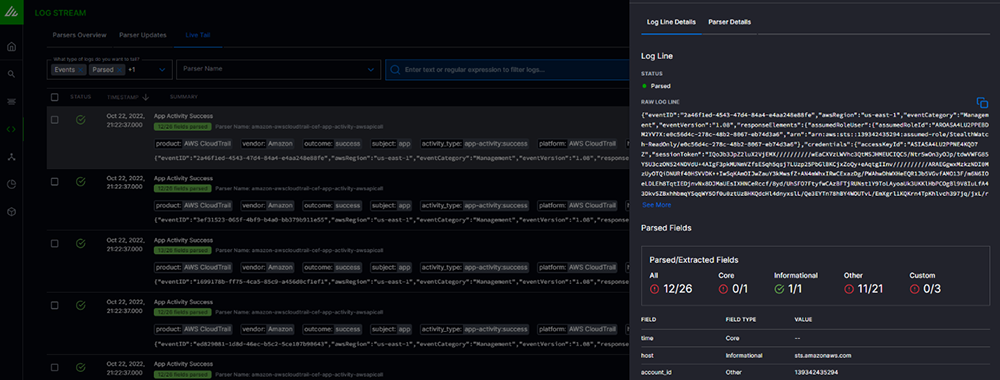
A significant shortcoming of IT log management tools is their limited parsing, enrichment, and event categorization capabilities. Most of these tools dump raw logs into a data lake and pass the burden of field extraction on to users to build parsers and schemas on reading — no security context, no cross-vendor normalization, and minimal security event schema.
Exabeam Security Log Management includes 8,000 parsers for 500 different IT and security products. All logs are parsed and enriched with security content — for example, threat intelligence — and required detection fields are identified and normalized regardless of the vendor.
All the adventure of threat hunting, without the pain of queries and regex syntax
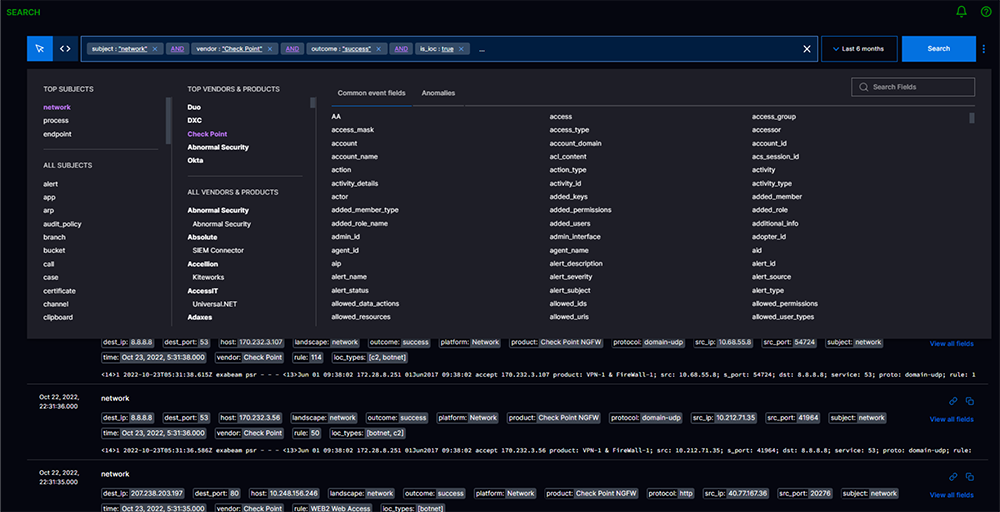
Even though they have dreaded syntaxes, proprietary languages, and poor UX, the users grind through the learning curve to do the job because IT log management tools are built for engineers writing Java and Python scripts all day long.
The Exabeam Search app is built to keep the excitement of threat hunting without the grind. Search automatically creates a search catalog based on logs in your environment. Security analysts can pick the critical security subjects, vendors, and fields they are interested in — a query is automatically built for them. Search allows analysts to search across multi-year data from one UI, removing the notion of hot and warm search created by IT log management tools due to their indexing limitations.
Quickly pivot from search to detection rules
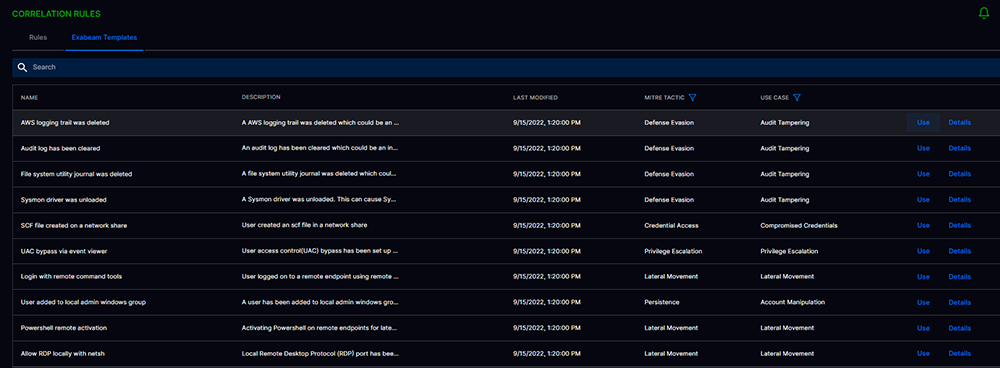
Most IT log management tools do not provide integrated threat-hunting and threat-detection workflows. Correlation Rules enable you to write, test, publish, and monitor custom correlation rules for your most critical business entities and assets; the best part is that the Search and Correlation Rules follow a bidirectional workflow to build detection at the end of your threat-hunting workflow. Correlation Rules provide analysts with an application to easily create custom correlation rules suited to their organization’s security and use case requirements. All Exabeam SIEM correlations can be enhanced with the most up-to-date indicators of compromise (IOCs) using the Threat Intelligence Service.
Built-in threat intelligence
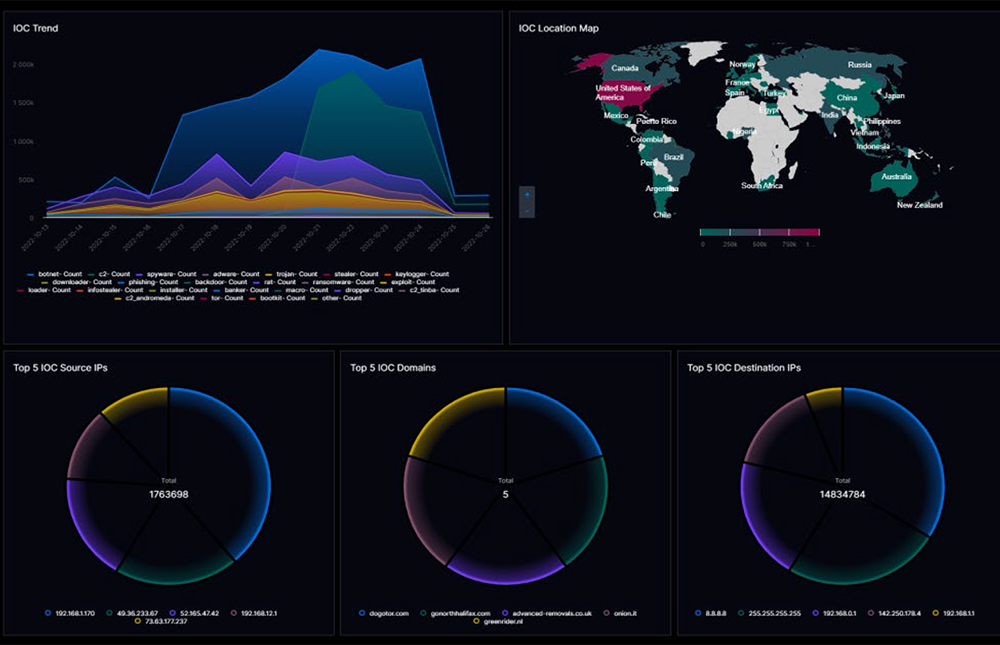
A common feature I see in IT log management tools is integration with Stack Overflow documents so that developers can quickly look up the error code in log messages and refer to the troubleshooting tips on Stack Overflow.
Security Log Management does things differently. It monitors the presence of IOCs in every incoming log message by monitoring IP, domain, email, etc. Security Log Management integrates with top commercial and open-source threat intelligence feeds so that security users can run a manual search with IOCs stored in CSV files to hunt for known threats.
Get granular consumption visibility
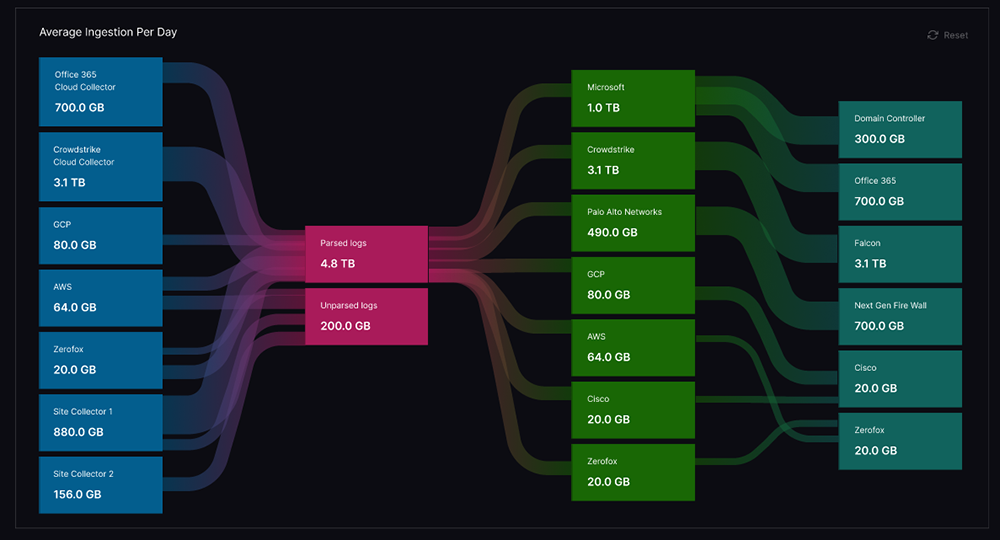
Service Health and Consumption provides complete visibility into log sources and their processing outcomes. This granular visibility not only helps you keep an eye on critical log source changes in the last 24 hours, but it also enables you to identify unimportant sources for optimization. Unlike IT log management tools, Security Log Management provides the backstory of log sources even if the logs don’t come from a source and instead come from staging storage, like S3 or GCS.
Get guidance on your security coverage based on your data
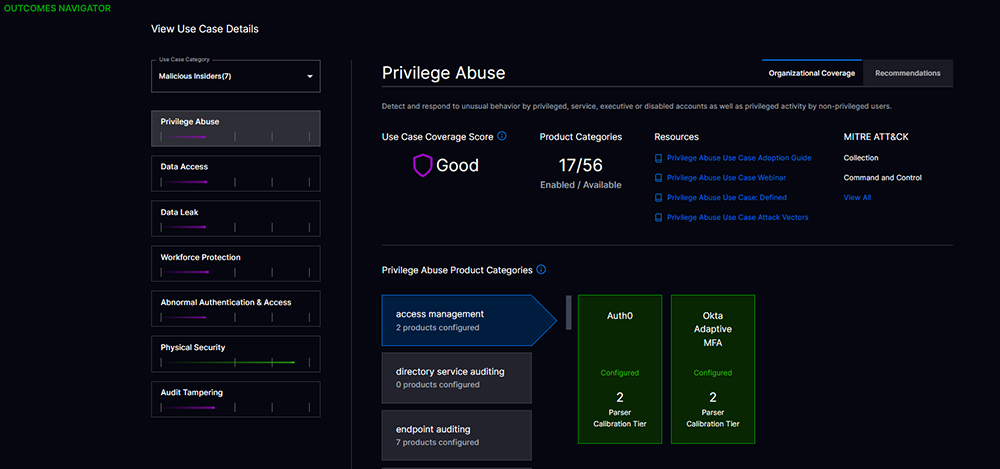
The biggest challenge with repurposed IT log management tools for security operations is their inability to guide you on what log sources can help you with what security outcome. Are all those logs adding to your cost or helping you improve your mean time to detect adversaries?
Outcomes Navigator enables you to understand your progress against the security outcomes you desire in your organization. It guides you on what vendors’ log sources can help improve your use-case coverage and overall security posture. Outcomes Navigator helps CISOs make informed decisions on the cost and benefits of bringing in new log sources to decrease risk and exposure to known attack tactics, techniques, and procedures (TTPs) for their industry and company.
Avoid business risk — upgrade to Exabeam Security Log Management
Exabeam Security Log Management combines hyper-quick Search, powerful detection, Reporting, Dashboards, and Outcomes Navigator, all on the cloud-native Exabeam Security Operations Platform. If you are still using legacy SIEM or IT log management as your security log management, it’s time to upgrade for better security outcomes.
Related content: Discover New-Scale SIEM
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!










