SECURING YOUR CLOUD OPERATIONS IN TODAY’S DISTRIBUTED ENVIRONMENT
You might have a good handle on your on-premise network security, but what do you know about cloud security and threats to your cloud operations? Do you even have a list of all of the deployed cloud assets within your organization, and who is responsible for each? Most organizations don’t have a handle on their cloud security.
Organizations are moving to the cloud
Many enterprises are embracing cloud operations as an effective replacement for some or all of their on-premise data center resources. If you haven’t yet moved any operations to the cloud, it’s likely that you’ll be doing so in the near future. But before you do, you’re going to want to make sure you have a grasp of the security and regulatory issues involved.
There are two main categories of cloud hosting:
- Infrastructure as a service (IaaS) – These services host all or part of your data center. Examples include Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform.
- Software as a service (SaaS) – These are complete applications that are typically delivered through a web browser. Examples include Salesforce, Microsoft Office 365, and Google G Suite.
Cloud security landscape
As you move to the cloud, you’ll discover that your principle application platform is no longer a hard disk drive, but a web browser. Even if your company hasn’t yet embraced the cloud, it’s already evident that cloud applications have transformed how we all do business. They have also transformed the security landscape.
Cloud services have become critical to operations
Entities that have moved at least some of their applications have found that cloud services are critical to running their operations. According to a recent survey by our partner Skyhigh Networks, the average enterprise is using 1500 cloud services, with a minimum 10% year-on-year increase.
As trust builds, cloud data becomes more sensitive
The sensitive nature of certain data is not stopping many organizations from moving it to the cloud. The Skyhigh Networks survey states there’s a good chance that if your organization has data in the cloud, some form of it is sensitive. Sensitive documents comprise nearly 20% of all documents in cloud sharing and collaboration applications (Figure 1).
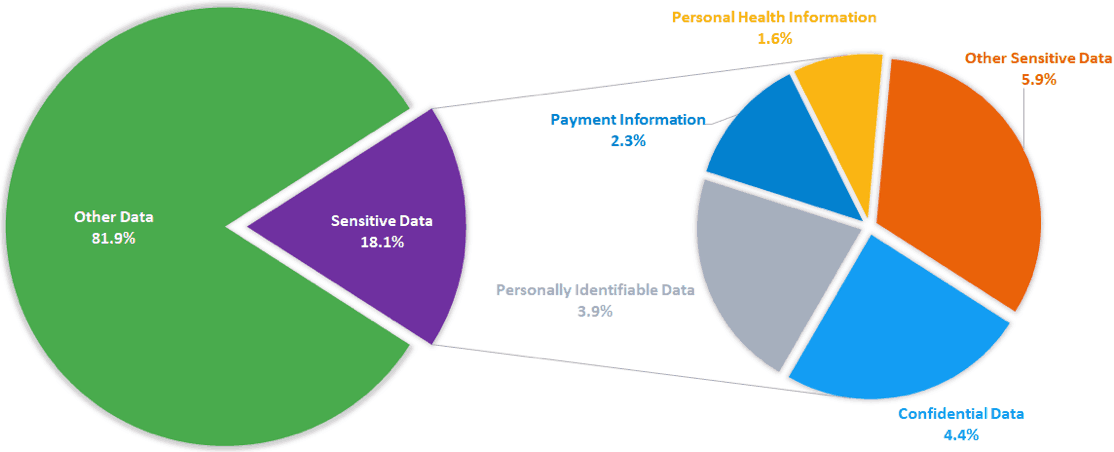
Figure 1 – Percentage of documents in cloud-based file sharing and collaboration applications
Some cloud data never crosses your network
It’s possible that at least some of your data never interacts with your organization’s local network. Indeed, this is true for as much as one quarter of enterprise data.
Let’s say you use Google Sheets to create a new spreadsheet, then post that on a Salesforce application. There is no need for that document to ever be present on your local computer or LAN. It exists solely in the cloud and users only see it within the scope of their web browser. Can your current security solution deal with this kind of exposure?
Cloud-related threats are at an all-time high
Not surprisingly, cloud-related threats have proliferated, and there is no reason to believe this will change. Once again looking at Skyhigh Networks’ study, organizations having cloud operations experienced an average of nearly two related incidents per month in 2017. These include:
- Insider threats (both accidental and malicious)
- Privileged user threats
- Compromised accounts
- Data exfiltration
These are the same threat scenarios most organizations contend with in their on-premise operations, which shows that your data is exposed no matter where you store it. Plus, in the realm of accidental insider threats, you might have users spinning up cloud-based environments, like AWS workloads, without having received proper training in how to make them secure.
Most organizations are not adequately staffed
Surveys of security professionals reveal that most organizations aren’t dedicating sufficient resources to cloud security operations. In The Exabeam 2018 State of the SOC Report, we noted that only one percent of the pros list cloud security as their primary job responsibility. The better news is that cloud security is at least part of the responsibility for 28.5 percent of security pros. Still, it’s no surprise that Gartner’s 2017 Magic Quadrant for Cloud Access Security Brokers report states that “…through 2020, at least 99 percent of cloud security failures will be the customer’s fault.”
What are the biggest threats to cloud security?
Many cloud services users might think that their respective providers are responsible for all aspects of their platform security—that their security problems are inherently solved by choosing a platform that enjoys a good reputation. But in fact, several cloud security aspects are relegated to your hands. For example, AWS states that it’s responsible for the security of the cloud, but its customer—you—remain responsible for security within the cloud.
The 2018 Cloud Security Report published by Netskope, another Exabeam partner, along with Cybersecurity Insiders and Crowd Research Partners cites that the biggest threats to cloud security are:
- Misconfiguration of cloud platforms (62 percent)
- Unauthorized access (55 percent)
- Insecure interfaces/APIs (50 percent)
The second post in our series reviews how to improve cloud cybersecurity.
For more information, click here for Exabeam’s webinar on Cloud Security Monitoring and Analytics.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












