
-
- Home
>
-
- Blog
>
-
- InfoSec Trends
Leverage MITRE ATT&CK to Gain Iranian Cyberattack Insights
- Feb 06, 2020
- Pramod Borkar
- 5 minutes to read
Table of Contents
Continued tension between the US and Iran—along with attacks originating from Iranian groups—suggest that such cyberattacks from Iran-affiliated actors will continue. The MITRE ATT&CK framework is a knowledge base of global adversary behavior across attack lifecycles, including Iran.
Nine Iranian adversarial groups have been identified within MITRE ATT&CK. We’ll take a deep dive into one such cyber espionage group, APT39, as well as show techniques and tools used by others (as listed in the framework). You’ll learn how Exabeam helps detect disparate adversarial techniques used by such threat groups and how you can leverage the ATT&CK framework to protect your organization.
APT39 Iranian Espionage Group
Active since 2014, APT39 is aligned with Iran’s national priorities. It has typically targeted telecommunications, tech, travel, government, and entertainment industries. Its focus—especially regarding travel and telecommunications—suggests its intent to monitor and track specific people or groups to collect proprietary data. Targeting government bodies indicates an intent to collect geopolitical data that may benefit future activities.
Let’s look at how APT39 has used custom or publicly available tools at various stages of its attack lifecycle—these being an initial compromise, discovery, credential access and privilege escalation, lateral movement, and exfiltration.
Initial Compromise – Adversaries use various techniques to gain access to an environment. APT39 leverages spearphishing emails to lure users to click on a malicious attachment or link. And it routinely exploits vulnerable web servers of targeted organizations to install tools such Antak, an ASP.Net webshell that leverages PowerShell. It lets an attacker upload executables through a web browser and execute them, and uses stolen credentials to compromise externally facing Outlook Web Access (OWA) resources. MITRE ATT&CK shows that APT39 also uses ASPXSpy, another tool providing control over a compromised web server.
Discovery – An adversary typically observes a given system and its network infrastructure before deciding how to act. MITRE ATT&CK reveals that APT39 often uses Remexi to collect system usernames, nbtscan to discover vulnerable systems, and a custom port scanner known as BLUETORCH.
Credential Access and Privilege Escalation – APT39 leverages tools such as Mimikatz, Ncrack, Windows Credential Editor, and ProcDump to obtain account credentials—normally in the form of a hash or a clear text password—from a given operating system and ancillary software. Attackers use so-called “dumped credentials” to and access restricted and/or proprietary information that requires privileged access.
Lateral Movement – Adversaries use tools such as secure shell (SSH) and PsExec to enter, freely roam, and even control network systems. Like APT39, they might install a tool such as Remote Desktop Protocol (RDP) to facilitate their lateral movement and persistence.
Exfiltration – Like many adversaries, APT39 compresses data it collects to minimize the number of packets sent over a network. Performed separately from the exfiltration channel, it either uses a custom program or algorithm, or a more common tool such as RAR, ZIP, or zlib. It’s also known tohave used WinRAR and 7-Zip to archive stolen data.
Notable Techniques of other Iranian Espionage Groups
APT39 isn’t the only Iranian threat group. MITRE ATT&CK lists some of the notable techniques and tools used by several of them during the attack chain.
| Name | Notable Techniques | Tools |
| APT33 |
|
|
| APT39 |
|
|
| Charming Kitten |
| DownPaper |
| Cleaver |
|
|
| CopyKittens |
|
|
| Group5 |
|
|
| Leafminer |
|
|
| Magic Hound |
|
|
| OilRig |
|
|
Using Exabeam to Detect Adversarial Iranian Techniques
Since adversaries frequently change their methods, many of these techniques and tools cannot be detected using traditional correlation or static rules. But by tracking individual user behavior and their interactions with network assets, they can be detected using a behavior-based approach.
Part of the Exabeam Security Management Platform, Exabeam Advanced Analytics is a user and entity behavior analytics (UEBA) solution for threat detection. Advanced Analytics preprocesses all logs and ties together all events—both normal and abnormal. As presented in Exabeam Smart Timelines (a chronological timeline), this makes it extremely easy for your analysts to pinpoint anomalous behavior (Figure 1).
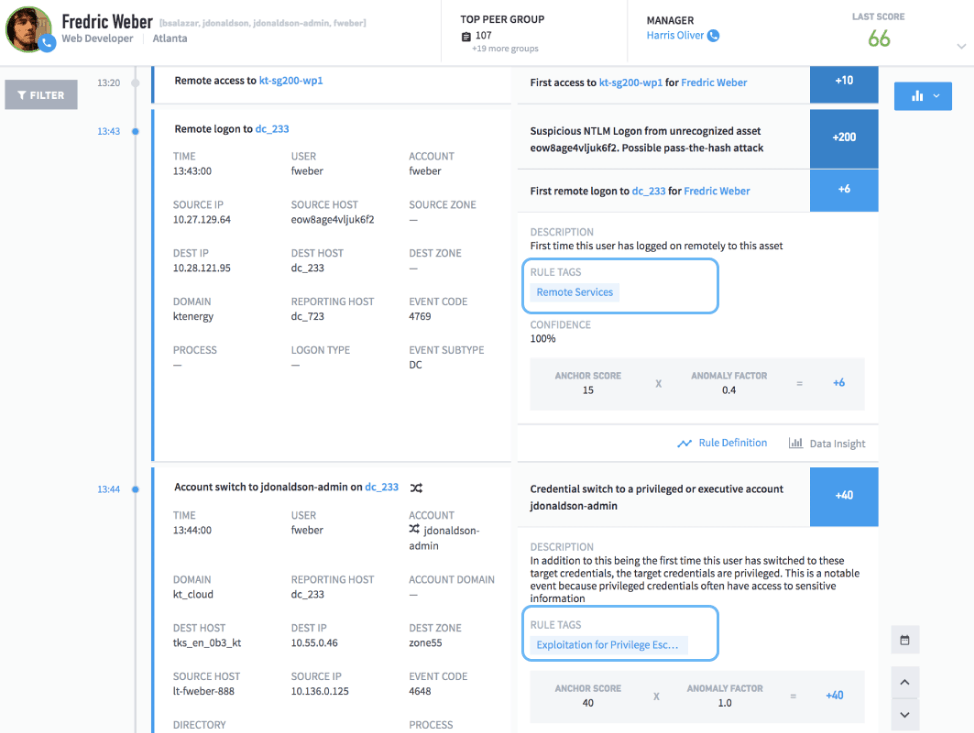
Figure 1: An Exabeam Smart Timeline makes it easy for analysts to hunt for anomalous behavior
Exabeam behavior models track users and assets to establish a normal behavior baseline; they also enable machine learning algorithms to easily detect baseline deviations. They can detect adversarial tactics that include initial access, discovery, user execution, lateral movement, privilege escalation, exfiltration, and others—as laid out in the MITRE ATT&CK framework.
A user model shown in Figure 2 aggregates all assets a given user remotely logs into. The model detects it’s the first time this user has remotely logged to a particular SQL server.
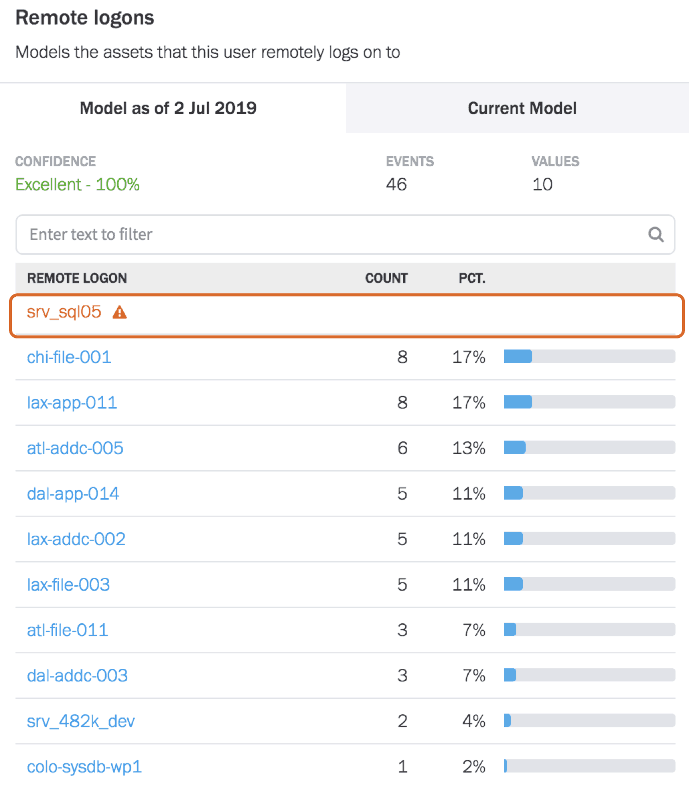
Figure 2: Being a deviation from this user’s normal behavior, their activity is flagged as a risk.
Exabeam Smart Timelines provide your analysts with a far more robust method for incident investigation and response—one in which they don’t need prior knowledge of an attacker’s tactics and techniques. Smart Timelines automatically tags techniques, along with corresponding risk reasons, to assist them in pinpointing anomalous behavior. This greatly reduces your SOC’s mean time in detecting and responding to incidents.
Along with the dynamically constructed context regarding the user and assets in question, Figure 3 shows the prior alert along with its risk score and the corresponding MITRE ATT&CK technique used. Your security investigators have complete information—including the risk reasons and relevant alert evidence.
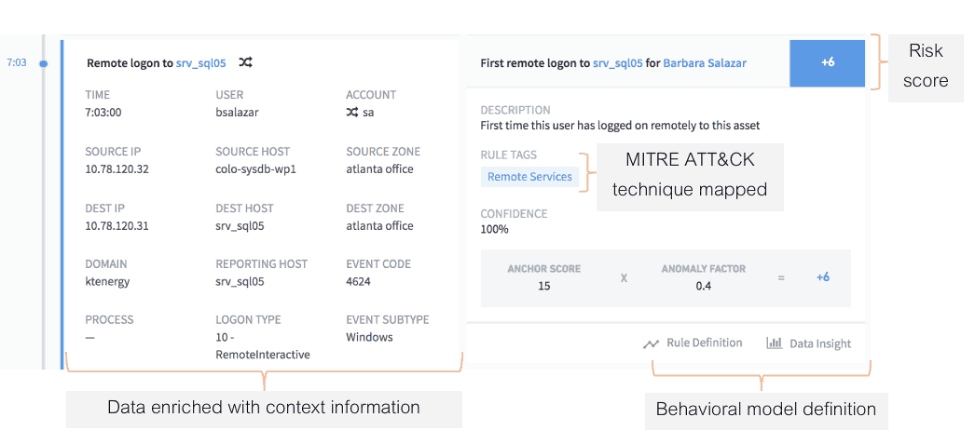
Figure 3: The anomalous server login is tagged to a MITRE technique used by Iranian espionage groups.
To ease the burden of your security team, Exabeam UEBA does not flood your SOC dashboard with individual alerts. In of itself, an alert initiated by a given user technique doesn’t offer proof that it’s a threat. But by leveraging machine learning, Exabeam Smart Timelines make it easy for investigators to not only see all the techniques used in an attack chain, but also corresponding risk reasons, enriched context data, and associated event scores.
Conclusion
During an attack, time is of the essence to quickly decipher techniques used and detect anomalous behavior. But resolving attack sequences requires SOC analysts to understand the complete picture. With Exabeam Smart Timelines tying together behaviors identified as anomalous and risky—along with techniques identified in the MITRE ATT&CK framework—your SOC analysts can trace an attacker’s steps to uncover where they may be heading next, then quickly respond before they become a threat to your organization.
- Tags
- MITRE ATT&CK
Learn More About Exabeam
Learn about the Exabeam platform and expand your knowledge of information security with our collection of white papers, podcasts, webinars, and more.
-
 Blog
Blog
Exabeam Agent Behavior Analytics: First-of-Its-Kind Behavioral Detections for AI Agents
- Show More


