The infamous SolarWinds supply chain cyberattack in December was devastating not only because of its reach — extending to at least nine federal agencies, critical infrastructure entities, and more than 100 private sector organizations. Its sophisticated strategy made it virtually invisible until it was discovered by FireEye, and promises to change federal agencies’ approaches to security.
An article on Federal News Network, CISA: ‘Identity is everything’ for cyber defense post SolarWinds, highlights a number of takeaways from the breach, not the least of which is in the title: Identity is everything. According to Cybersecurity and Infrastructure Security Agency (CISA) strategist Jay Gazlay, the hacker’s exploitation of verified credentials highlights the critical importance of identity controls in stopping security breaches, particularly with the increasing use of cloud applications. Gazlay makes several other sobering observations.
- Those who had the best shot at detection were agencies with behavior analysis techniques built into their identity management that could flag anomalous activity, particularly “impossible logins.” More on that below.
- If Federal agencies are not set up to detect such anomalous activity, they’ll never be able to detect similar user impersonation attacks, which are becoming de rigueur for adversaries.
- Security should be automated as much as possible. Asking people to sort through individual [indicators of compromise] is a really hard ask.
We provide a more detailed discussion of how the SolarWinds breach unfolded and advice for countering each step here.
Enter UEBA
All of this highlights the importance of user and entity behavior analytics (UEBA), as part of every agency’s foundational security arsenal. What exactly is UEBA? We’ve described it in depth in posts including What is UEBA and Why it Should Be an Essential part of your Incident Response and How UEBA and SOAR Can Improve your Security Team’s Productivity Without Additional Staff.
Essentially UEBA is the opposite of the rules-based approach to security typically used by legacy firewalls, antimalware, intrusion prevention, and SIEMs. A rules-based approach creates individual correlation rules from thousands of different attack scenarios, such as “Send an alert whenever a user sends and an email attachment larger than 4MB.”
Rules like these are based on previously known attack patterns and so require a lot of work to keep up to date in the face of constantly shifting strategies. They often lack user context, such as those in the graphics department who routinely send attachments of 4MB or more. This means devising more rules to whitelist such users. In general, the rules-based approach requires a lot of time and resources, is prone to false positives, and is always chasing the last attack rather than the next one.
Instead of all that manual rule creation and maintenance, UEBA uses machine learning and advanced analytics to track and analyze normal user activity over time, comparing it with that of other users in the peer group, such as graphic artists. Gartner added the “entity” part of UEBA, which tracks the behavior of servers, routers, IoT devices, and other non-humans that access resources and data. Once UEBA establishes a normal expected behavior baseline, it flags any activity that is abnormal automatically. However, instead of sending alerts for every single abnormal behavior, UEBA:
- Ingests data from multiple log sources
- Analyzes and stitches together all user activity into one timeline
- Assigns risk scores to these abnormal behaviors
- Alerts the user only when the overall risk level across all these behaviors exceeds a certain threshold.
UEBA and impossible logins
A perfect example is the abnormal behavior of the SolarWinds attack that the Federal News Network article calls “impossible logins” — a scenario where the same set of credentials is used to log in at multiple places across the globe.
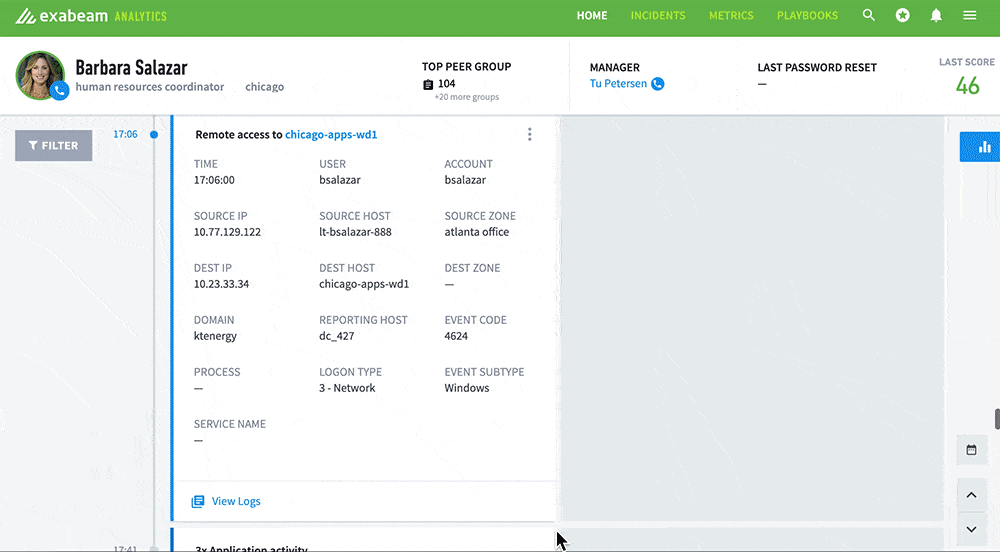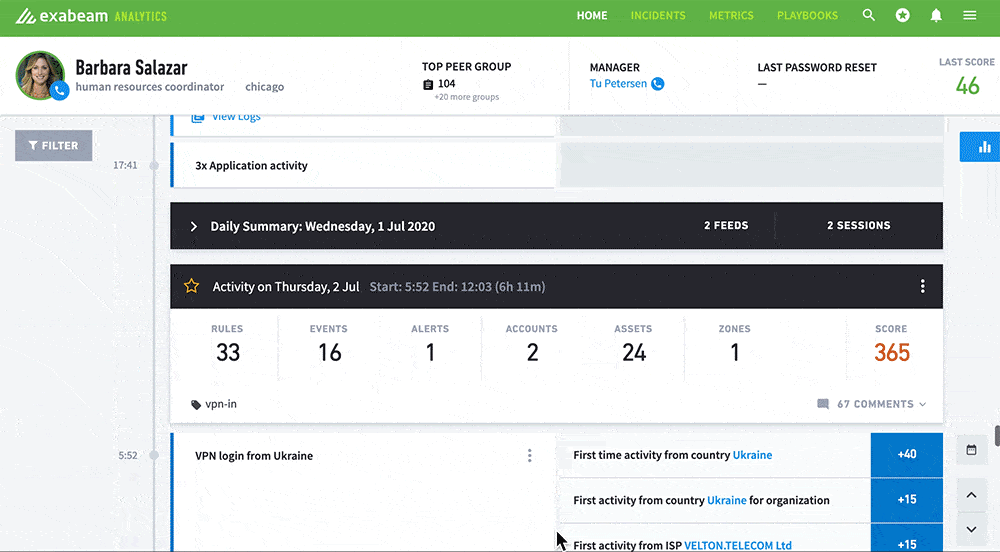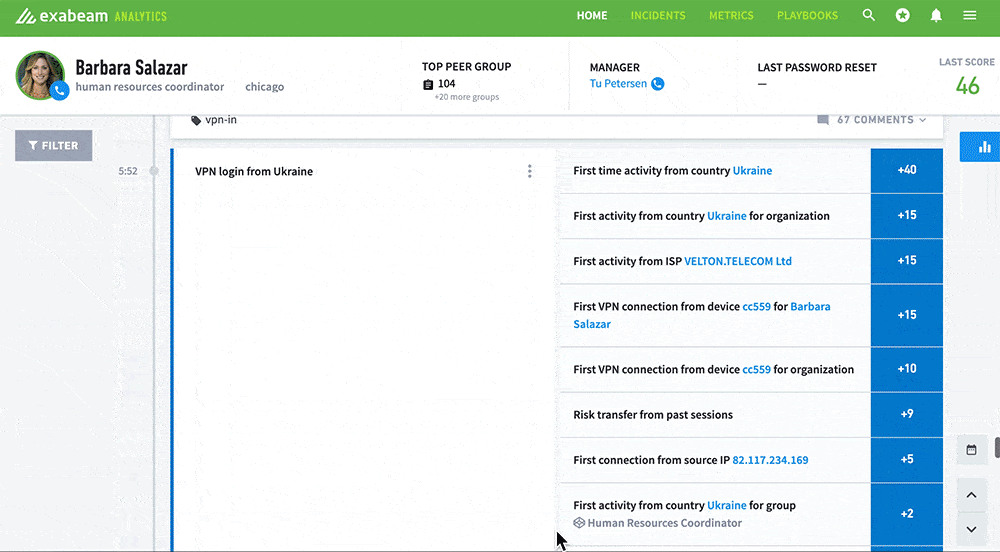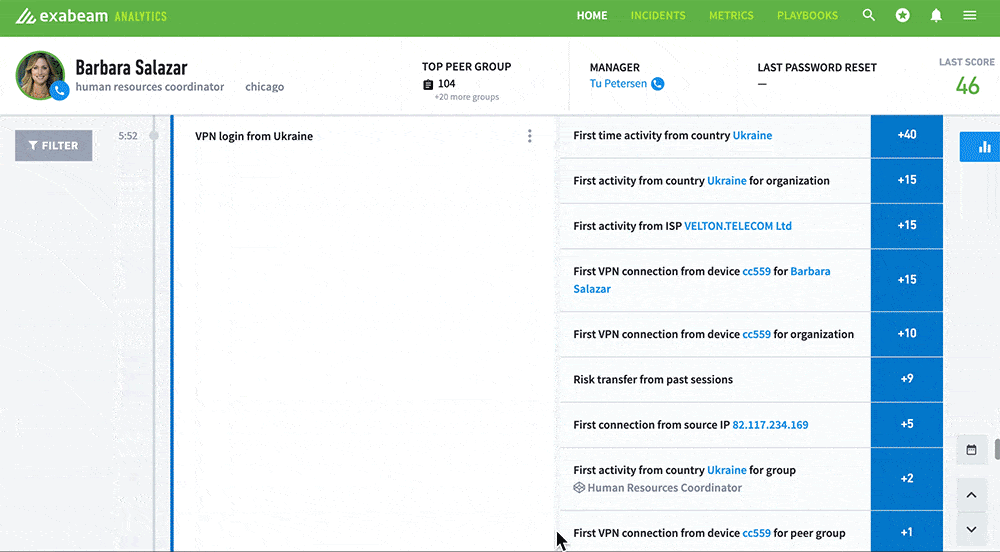
Once you know this attack strategy you could create scores of individual rules to flag it. The beauty of UEBA, however, is that it doesn’t need all those rules, it simply detects that an impossible login is not typical behavior from this user or other users in their peer group. Or put simply, UEBA can detect unknown threats. A perfect example is shown in the Exabeam UEBA screenshot below.
- The user, Barbara Salazar, logs in from Chicago at 5:06 p.m., a perfectly normal login behavior for her.
- The following morning she then logs in from the Ukraine — pretty much an “impossible login,” given the distance and time.
- UEBA identifies the Ukraine login as a first, not only for this user, but for the device and entire organization. It’s also the first connection from the source IP address and ISP.
- UEBA assigns a risk score for each of these identified behaviors.
- The sum of the assigned risk scores gradually pushes the abnormal behavior over the alert threshold, and an alert is generated for a review of the significant anomalous activity.
UEBA is geared directly to detect identity-based attacks and is a perfect tool for discovering and stopping privileged account attacks and other zero-day strategies. As Gazlay says, in light of the SolarWinds and other similar attacks, federal organizations should look seriously at adding such behavioral analytics to their security arsenals.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!












