The theme for this year’s National Cybersecurity Awareness Month (NCSAM) is “Own IT. Secure IT. Protect IT”. With that in mind, we look at an important aspect of cybersecurity: how to be one step ahead by preparing your incident response plan before it’s needed.
Every security breach that affects resources such as enterprise networks, computers, mobile devices, or IoT requires an incident response. This comprises how to identify an attack, contain its damage, and eliminate the incident’s root cause. In the (remote) likelihood that your organization comes under attack, what does your plan need to look like?
The six steps of incident response
SANS Institute’s Incident Handler’s Handbook defines six steps in the effective handling of security events. These are:
- Preparation – Create an incident response plan ahead of security events that may threaten your organization
- Identification – Security analysts detect IT infrastructure deviations and assess whether any represents a significant event that requires action
- Containment – Both short- and long-term containment steps are engaged to prevent further damage to the enterprise
- Eradication – Additional steps are undertaken to prevent future incidents. For example, a software component may require patching to close a vulnerability
- Recovery – Your incident response plan spells out all of the requisite steps—including testing—to restore full functionality to the organization
- Lessons Learned – Conducting a post-mortem after each security event helps refine and bolster your incident response plan
Read our post on The Three Elements of Incident Response: Plan, Team, and Tools to learn more about the objectives of an incident response plan.
Developing an incident response plan
An incident response plan is a crucial part of preparation. With a plan ready, your organization will be positioned to identify, respond to, and recover from a significant security breach. Robust planning can help prevent damages such as data loss or theft, a service outage, and unauthorized access to enterprise systems. Maintaining compliance is also of utmost importance (e.g., GDPR, HIPAA, PCI-DSS).
But don’t wait for a serious security event to happen before developing and testing an incident response plan; A modern security strategy adopts the mindset of “when” not “if” a breach will happen. Along with conducting post-mortems after facing a serious security event, your response plan can assist you in mapping out a set of best practices to improve your overall security posture and prevent further breaches from occurring.
To be effective, your incident response plan should include a well-defined incident response policy and designate a comprehensive incident response team.
See our post Incident Response Plan 101: How to Build One, Templates and Examples for more information.
Defining an incident response policy
Having an effective incident response policy in place helps ensure a timely, effective, and orderly response to a security event. Founded on best practices, it lays out the processes and procedures your incident response team will follow during a breach.
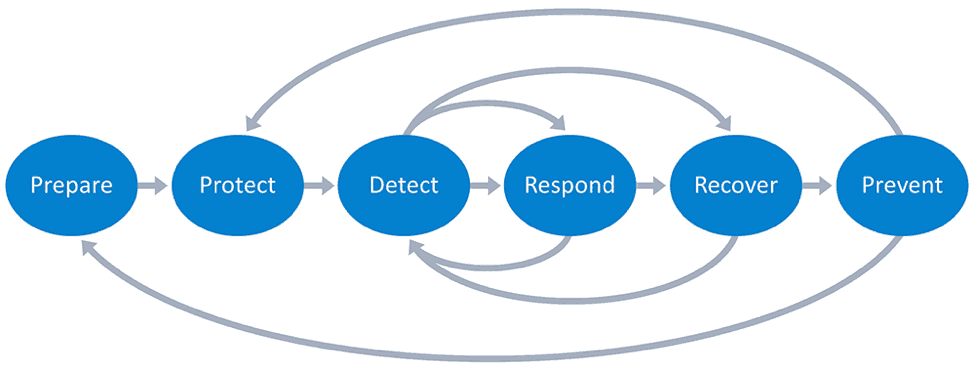
Figure 1: The phases of an incident response policy include preparation, protection, detection, response, recovery, and prevention.
Your policy guides the enterprise during these critical times and helps them refrain from being reactive when a security event occurs. A good policy spells out preventative measures and answers key questions for how to handle each security event effectively and appropriately. Who handles which aspect of any given response? And at what point do stakeholders, compliance regulators, and/or the public need to be notified?
See How to Quickly Deploy an Effective Incident Response Policy for additional details.
The incident response team
Your security operations center (SOC) team is responsible for the defense of your entire IT infrastructure. But they’re limited in their scope of responsibilities.
Your computer security incident response team (CSIRT) should include cross-functional members who are assigned specific tasks. Representing other departments within your organization, they can have the authority to recommend system changes, manage internal communications after a security event, interface with counsel, and other duties that extend beyond the purely technical actions taken to remediate an incident.
The incident response team coordinates all activities during a security event while also providing the following functions:
Analysis – Document the extent, priority, and impact of a security event to assess those assets that were affected and determine if the event requires further evaluation
Reporting – Inform team members of reporting procedures. Relevant trending data may be gathered to share with stakeholders and others
Response – Investigate root causes, record findings, implement recovery strategies, and communicate the CSIRT’s status within the organization
Our post 10 Best Practices for Creating an Effective Computer Security Incident Response Team recommends who should be on your incident security team and what duties each member should undertake.
Conclusion
Effective incident response enables organizations to detect, respond, repair, and review when confronted with cybersecurity breaches or attacks. Incident response teams use procedures and technology, such as automated playbooks, to respond quickly and adequately to such security events, limiting the damage done by attackers.
Similar Posts
Recent Posts
Stay Informed
Subscribe today and we'll send our latest blog posts right to your inbox, so you can stay ahead of the cybercriminals and defend your organization.
See a world-class SIEM solution in action
Most reported breaches involved lost or stolen credentials. How can you keep pace?
Exabeam delivers SOC teams industry-leading analytics, patented anomaly detection, and Smart Timelines to help teams pinpoint the actions that lead to exploits.
Whether you need a SIEM replacement, a legacy SIEM modernization with XDR, Exabeam offers advanced, modular, and cloud-delivered TDIR.
Get a demo today!













